WannaCry
| WannaCry | |
|---|---|
| Surname | WannaCry |
| Aliases | WannyCrypt |
| Known since | 2017 |
| Type | Network worm |
| Other classes | Ransomware |
| Authors | Unknown |
| Memory resident | Yes |
| distribution | Exploit |
| system | Windows XP, Vista, 7 etc. a. |
WannaCry , also known as Wcrypt , WCRY , WannaCrypt or Wana Decrypt0r 2.0 , is a malware program for Windows that was used for a serious cyber attack in May 2017 . WannaCry attacks Windows operating systems that have not been improved with a specific patch offered by Microsoft since March 2017 .
After attacking a computer , the malicious program encrypts certain user files on the computer and, as ransomware, asks the user to pay a certain amount in the crypto currency Bitcoin ; if a period is not used, the program threatens to lose data. In addition, the program tries to infect other Windows computers as a computer worm and installs the DoublePulsar backdoor , which has been known for a long time .
Cyber attack in May 2017
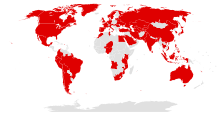
A major cyberattack with WannaCry started on May 12, 2017, infecting over 230,000 computers in 150 countries and demanding ransom payments . The attack was described by Europol as an unprecedented event in terms of its scale.
prehistory
WannaCry based on Eternal Blue , an exploit of the vulnerability MS17-010 in the SMB protocol (NetBIOS) from Microsoft. The US foreign secret service NSA used this loophole for more than five years without informing Microsoft about it, for its own purposes with an exploit that was named EternalBlue and was developed by hackers from what is believed to be the NSA-affiliated Equation Group . It was only after the NSA learned that the knowledge about EternalBlue had been stolen that they informed Microsoft of the vulnerability. The company then made a security patch available for the SMBv1 server on March 14, 2017, but at that time only for the Windows Vista , Windows 7 , Windows 8.1 and Windows 10 operating systems that were still supported by Microsoft and for Windows Server 2008 and later . One month after the updates from Microsoft, EternalBlue was made public by the hacking group The Shadow Brokers.
Affected companies and institutions
The cyber attack affected several global companies. These include the Spanish telecommunications group Telefónica and several other large companies in Spain , parts of the British National Health Service (NHS) with several hospitals, the US logistics company FedEx , the French car group Renault , the Japanese car manufacturer Nissan in Great Britain, Deutsche Bahn with the Logistics subsidiary Schenker , the Spanish Banco Bilbao Vizcaya Argentaria , the Brazilian telecommunications company Vivo , the Swedish company Sandvik , the Chinese oil company PetroChina . Other targets in at least 99 countries were also reported. In Romania, the Ministry of Foreign Affairs was affected. In Russia , more than 1,000 computers belonging to the Ministry of the Interior (MWD), the Ministry of Disaster Control and the telecommunications company MegaFon were affected.
Around 450 computers at Deutsche Bahn were infected and led, among other things, to the failure of display boards at many train stations, video surveillance systems and a regional control center in Hanover.
In China, customers could only pay in cash at more than 20,000 gas stations.
Inhibition of the spread
Already on May 12 discovered security researchers in their analyzes by chance a kind of " emergency stop " (kill switch) , which curbed further infection. The researchers found a reference to a domain that was not registered at the time in the malware's code . One of the researchers registered the domain because he hoped it would provide further information about the crypto trojan. He immediately recorded thousands of connection attempts on a server operated at this address . When the malware was able to access this domain, it stopped spreading. New variants of WannaCry that did not respond to this kill switch were much less widespread. This was attributed to the fact that many potentially affected computers had meanwhile been provided with the security updates provided.
State investigations and responses
In Germany, the Federal Ministry of the Interior considers the case to be particularly serious. The BKA took over the investigation. Government networks should not be affected. The President of the Federal Office for Information Security Arne Schönbohm expressed himself in a press release:
"[...] The current attacks show how vulnerable our digitized society is. They are another wake-up call for companies to finally take IT security seriously and to take sustainable protective measures. The current vulnerability has been known for months, and corresponding security updates are available. We urgently advise you to import these. "
Microsoft's President and Legal Director Brad Smith refers to repeated reports of exploits from stocks of the CIA and the NSA , which can be compared to the loss of cruise missiles from military facilities, and accuses "the governments of the world" of not being sufficiently aware of software vulnerabilities ( Exploits ) that their intelligence agencies discover:
"We need governments that are aware of the harm to civilians that arises from the accumulation and exploitation of such software security problems"
The older Windows versions XP , Windows 8 that had not been updated to Windows 8.1 and Windows Server 2003 did not receive any updates until the time of the attack, as these were outside the support period. Microsoft only responded on May 12, 2017 by publishing patches for these operating systems that were no longer supported. This limitation of security updates by Microsoft was criticized because, according to a survey, 52% of companies still used at least one computer with Windows XP. Analyzes later showed, however, that the exploitation of the security hole on Windows XP did not lead to success and that computers with Windows XP would therefore hardly have played a role. Rather, the large spread can be explained by the fact that existing security updates for operating systems that are still supported were not imported. 98% of the infections concerned the Windows 7 operating system, less than 0.1% of the infections concerned Windows XP.
Security firms Kaspersky Lab and Symantec announced on May 15, 2017 that they had assigned parts of the code used to write early versions of the malware to the Lazarus Group , a group believed to be on behalf of North Korea operated on. Both companies emphasize that their findings are merely circumstantial, far from being conclusive.
In a December 2017 article, a US government official attributed responsibility for "WannaCry" to North Korea. The attack was described by one of the President's security advisers as "cowardly", "expensive" and "ruthless".
Transmission routes
A computer is infected by other already infected computers: Without any further action on the part of the user, WannaCry searches for other unprotected computers in the local network due to its worm properties , infects them and sends numerous IP requests to the Internet in order to infect computers that are not protected . Contrary to what was initially assumed, WannaCry does not spread via email .
A weak point in the implementation of the SMB interface, which is required under many Windows versions for file and printer sharing , is responsible for the network infection . The security gap makes it possible that the respective Windows computer can be made to execute any other code from outside - in this case WannaCry with its various modules. The implementation of version 1 of the SMB protocol was affected, which for reasons of compatibility is still active by default even with newer Windows versions.
Harmful effect
During the initial expansion, WannaCry gives the currently active Windows account administrator rights , also shows files marked as hidden and encrypts around 100 different file types of document, image, video or audio formats that are on the internal hard drive , a network drive or another connected storage medium with drive letters can be found with a 2048-bit RSA key . The encrypted files are given the file extension .WNCRY . To prevent restoration with automatic backups, so-called shadow copies, WannaCry also deletes these with the Windows system tool vssadmin. Afterwards, the ransomware demands a certain amount in the crypto currency Bitcoin, which varies from case to case, which is to be paid within a period of a few days in order to decrypt the files. If the deadline is not used, the program also threatens to delete data. In addition, RDP connections (for remote control of the PC) can be misused.
Payment of ransom
The program code of WannaCry provides for the generation of an individual Bitcoin address for each infected computer. In this way, ransom money received can be assigned to the computer and the decryption codes transmitted to the victims. Due to a so-called " critical race error ", however, the generation of individual Bitcoin addresses fails; instead, one of three fixed Bitcoin addresses is used. It can then be assumed that the perpetrators cannot tell whether the ransom has been paid for a particular hijacked computer. The security company Symantec therefore assumes that ransom payments will not lead to success. However, according to other sources, some payments resulted in decryption after being negotiated manually. The program error has been fixed in later variants of the malware that achieved low levels of spread.
Protective measures
In addition to importing the latest security updates, the use of the latest anti-virus programs is recommended. However, some antivirus programs block access to the KillSwitch domain, which prevented the original variant of the malware from spreading because they consider the increased data traffic with it suspicious. This is counterproductive as the malicious program then spreads because the emergency stop button is not activated.
In addition, the firewall can be used to block the incoming signals for TCP ports 445/139/137 and UDP ports 137 and 138 (all five are used by SMB), as well as incoming and outgoing connections of TCP port 3389 (RDP) getting closed. This prevents the currently most common variant of the pest from penetrating. This permanently protects the services based on it from external attacks.
However, newly released variants of the malicious program as well as completely different attackers can use other gaps and ports to penetrate and spread. Therefore, according to the opinion of the trade press, a number of other measures make sense: SMB and file sharing can be completely deactivated. Files with unsuitable or multiple file extensions or any other suspicious file attachments in emails - even from known senders - should not be opened because their computer could already be compromised without the knowledge of the sender. Microsoft Office and similar programs should not be allowed to run macros , and programs that appear untrustworthy should not be started. In order to keep the damage as low as possible in the event of an infection, the authors also recommend carrying out regular data backups and disconnecting the backup media from the system after the backup so that they are not infected.
Trivia
Shortly after the appearance of WannaCry, security researchers discovered a new piece of malware called EternalRocks , which tried to pretend to be WannaCry in order to remain undetected by security researchers.
In May 2017 it became known that the Samba software , which provides Windows functions such as file and print services on various operating systems such as Linux , is affected by a vulnerability similar to Windows systems. This is referred to as SambaCry . The injected malicious programs run on affected systems such as NAS systems a Mining for cryptocurrency Monero out.
Web links
- Global cyber security incidents caused by ransomware. In: bsi.bund.de. Retrieved May 13, 2017 .
- Dusan Zivadinovic: WannaCry: BSI calls on those affected to report infections - heise online. In: heise.de. May 13, 2017. Retrieved May 13, 2017 .
- Msrc Team: Customer Guidance for WannaCrypt attacks. In: blogs.technet.microsoft.com. May 12, 2017, accessed May 13, 2017 .
- Ransomware: Win32 / WannaCrypt. In: microsoft.com. May 12, 2017, accessed May 13, 2017 .
- Microsoft Security Bulletin MS17-010 - Critical. In: technet.microsoft.com. March 14, 2017, accessed May 13, 2017 .
Individual evidence
- ↑ Code: GitHub - GregorSpagnolo / WannaCrypt: Known WannCrypt Bitcoin addresses. In: github.com. May 15, 2017, accessed May 15, 2017 .
- ↑ GitHubGist: Wannacryptor factsheet , accessed May 15, 2017
- ↑ BBC News: Ransomware cyber-attack threat escalating - Europol. In: BBC.co.uk. May 14, 2017. Retrieved May 14, 2017 .
- ↑ a b c Dusan Zivadinovic: WannaCry: Microsoft delivers security patches for outdated Windows versions. In: heise.de. May 13, 2017. Retrieved May 13, 2017 .
- ↑ Jenny Stern: Wanna Cry: attack tool from the NSA's gun cabinet, in: Tagesschau Fact Finder, online May 13, 2017
- ↑ Dennis Schirrmacher: Alleged NSA hacking weapons for sale , in: Heise.de, online August 16, 2016
- ↑ NSA officials worried about the day its potent hacking tool would get loose. Then it did. In: The Washington Post . May 16, 2017. Retrieved May 18, 2017 .
- ↑ Microsoft: Security update for Microsoft Windows SMB server (4013389) , online March 14, 2017
- ↑ Microsoft: Security update KB4012598 from March 12 and May 13, 2017
- ^ Dan Goodin: Mysterious Microsoft patch killed 0-days released by NSA-leaking Shadow Brokers. In: Ars Technica. April 15, 2017. Retrieved May 15, 2017 .
- ↑ a b c d Maik Baumgärtner, Frank Hornig, Fabian Reinbold, Marcel Rosenbach, Fidelius Schmid, Hilmar Schmundt, Wolf Wiedmann-Schmidt: "Ooops" . In: Der Spiegel . No. 21 , 2017, p. 10-17 ( online ).
- ↑ Volker Briegleb: WannaCry ransomware attacks Deutsche Bahn computers - heise online. In: heise.de. May 13, 2017. Retrieved May 13, 2017 .
- ^ How to Accidentally Stop a Global Cyber Attacks. In: MalwareTech. May 13, 2017. Retrieved May 15, 2017 .
- ↑ a b Player 3 Has Entered the Game: Say Hello to 'WannaCry'. In: Cisco's Talos Intelligence Group Blog. May 12, 2017. Retrieved May 15, 2017 .
- ↑ Michael Link: Ransomware WannaCry: Security expert finds "kill switch" - by accident. In: heise.de. May 13, 2017. Retrieved May 15, 2017 .
- ↑ Cyber attack - WannaCry 2.0 did less than feared . In: Deutschlandfunk . ( deutschlandfunk.de [accessed on May 30, 2017]).
- ↑ Volker Briegleb: WannaCry: BKA takes over investigations after global cyber attack - heise online. In: heise.de. May 13, 2017. Retrieved May 13, 2017 .
- ↑ BSI - Press releases from the BSI - Worldwide cyber security incidents caused by ransomware. In: bsi.bund.de. Retrieved May 15, 2017 .
- ↑ Brad Smith: The need for urgent collective action to keep people safe online: Lessons from last week's cyberattack , in: Microsoft on the issues, online May 14, 2017
- ↑ "WannaCry" attack Microsoft makes governments allegations. In: Spiegel Online . Retrieved May 15, 2017 .
- ↑ Chris Merriman: Microsoft, it's not just the NSA. If you want to kill WannaCry, fix broken Windows , in: The Inquirer, online May 15, 2017
- ↑ Windows XP computers were mostly immune to WannaCry. May 30, 2017. Retrieved May 30, 2017 .
- ↑ heise online: WannaCry: Almost only Windows 7 PCs are infected. Retrieved May 30, 2017 .
- ^ "NHS cyber attack: Everything you need to know about 'biggest ransomware' offensive in history" Daily Telegraph, May 17, 2017
- ↑ Phil Muncaster: "Lazarus Group Exposed with Major New North Korea Link" infosecurity-magazine.com of April 4, 2017
- ↑ heise online: WannaCry: Sony Pictures hackers from North Korea under suspicion. Retrieved May 17, 2017 .
- ↑ Justin McCurry: "WannaCry cyberattack: US says it has evidence North Korea was 'directly responsible'" The Guardian, December 19, 2017
- ↑ a b c msft-mmpc: WannaCrypt ransomware worm targets out-of-date systems , in: Microsoft Blog Technet / Windows Security, online May 13, 2017
- ↑ How did the WannaCry ransomworm spread? - Malwarebytes Labs | Malwarebytes Labs. Retrieved June 16, 2017 (American English).
- ↑ nakedsecurity blogger Bill Brenner: WannaCry: the ransomware worm that didn't arrive on a phishing hook .
- ↑ Vulnerability CVE-2017-0144 in SMB exploited by WannaCryptor ransomware to spread over LAN . ESET North America. Archived from the original on May 16, 2017. Retrieved May 16, 2017.
- ↑ US States Computer Readiness Emergency Team (US-CERT): Alert (TA17-132A) Indicators Associated With WannaCry Ransomware , in: US Department of Homeland Security, online access May 15, 2017
- ↑ heise online: WannaCry: What we know so far about the ransomware attack .
- ↑ Technical analysis of the "WannaCry" ransomware
- ↑ Zammis Clark: The worm spreads did WanaCrypt0r. May 12, 2017. Retrieved May 20, 2017 .
- ↑ a b What you need to know about the WannaCry Ransomware , May 15, 2017
- ↑ Teardown: WannaCry Ransomware , May 17, 2017
- ↑ How Much The Wanna Cry Hackers Earn , May 16, 2017.
- ↑ WannaCry: What we know so far about the ransomware attack. In: heise online. May 15, 2017. Retrieved May 31, 2017 .
- ↑ a b Mohit Kumar: WannaCry Ransomware: Everything You Need To Know Immediately. In: thehackernews. May 15, 2017. Retrieved May 18, 2017 .
- ↑ Martin Holland, Axel Kannenberg: WannaCry: Attack with ransomware paralyzes tens of thousands of computers worldwide. In: heise.de. May 12, 2017. Retrieved May 13, 2017 .
- ↑ heise Security: WannaCry & Co .: How to protect yourself. Retrieved May 15, 2017 .
- ↑ EternalRocks worm uses seven NSA exploits (WannaCry used two) . In: CNET . ( cnet.com [accessed June 1, 2017]).
- ↑ CVE-2017-7494 - Remote code execution from a writable share. Retrieved July 23, 2017 .
- ↑ SambaCry is coming