Chord
Chord is a structured peer-to-peer system which, in contrast to most unstructured systems, enables an efficient search for content. Like Gnutella , Chord is not a concrete implementation, but a protocol system. It is being developed at MIT and the source code of the current version is available for free download and use under the MIT license .
Structured overlay network
Over the actual transport layer ( TCP / IP ), peer-to-peer systems form what is known as an overlay network . This overlay network describes the network topology of the individual peers that are connected via the peer-to-peer system. The central question arises when adding and removing new peers (network nodes): Who should the new node be connected to? The same applies to deletion: Was the node possibly a connection between two others, so that removing the node represents a deterioration in the quality of the overlay network?
At Gnutella these questions are not asked, new nodes connect randomly to the nodes that they can determine by flooding the network. With Chord, however, a so-called chord ring is set up: All network nodes are arranged in a ring structure, with each node having connections to its predecessor, successor and certain other nodes in the network. This ring structure enables a binary search (with the help of a distributed hash table ), which generally causes search costs when searching for content in the network. (In contrast to this, Gnutella causes immense search costs, for example - around 70% of the network load in Gnutella networks is caused by searching.) The disadvantage lies in the more complex handling of the ring structure - this must always be taken into account when adding and removing network nodes that the ring structure and cross-references are retained.
Content distribution
A binary search is not yet possible with the help of the ring structure alone: In the naive approach - to search for content - the ring would have to be run through once in ascending order of the GUIDs in order to achieve an "exact match", i.e. H. get a precise answer to a search query. Although this is better than searching in an unstructured network, it is still relatively "expensive".
A global hash function is required to correctly identify data, i.e. the actual content of the network to be distributed. This assigns a unique ID to each data record (e.g. files in the case of file sharing), which is created using the SHA-1 hash function (160-bit key). Each node now manages a certain part of the global hash table, which is represented by an interval of the key. Each node now knows for part of the data on which other nodes or intervals these are located.
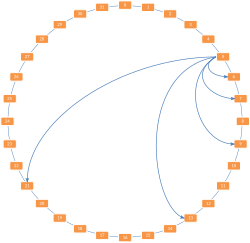
In the "Scalable Key Location" variant, the Chord network uses references to remote nodes, a so-called finger table, to search for and traverse the ring. The entries are created as follows: The -th finger ( ) of the node with the ID refers to the node that is responsible for the hash value , with the number of bits corresponding to a node. The modulo ensures that you stay on the ring structure. This ensures that you can get to the element you are looking for much faster than with a linear search.