DNS amplification attack
The DNS Amplification Attack ( German DNS amplification attack ) is a denial of service attack , in which the abuse under the domain name system extremely large data streams are directed to the Internet connection of the victim. The aim is to overload this Internet connection so that it cannot be used, possibly with the intention of causing economic damage.
procedure
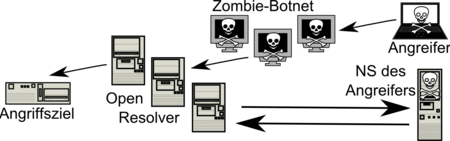
The DNS Amplification Attack takes advantage of the fact that in certain cases name servers respond to short request packets with very long packets. A 60-byte long request can in certain cases provoke a response that is more than 3000 bytes long. So there is a gain factor of more than 50. This response is directed to the victim's IP address by means of IP spoofing . For example, if an attacker sends a constant data stream of 100 megabits per second to various open name servers on the Internet, these generate a load of 5 gigabits per second for the victim with a gain factor of 50. If the target system has activated IP fragmentation , there is also a higher computational effort to assemble fragmented IP packets .
DNS amplification attacks have become much more effective thanks to the DNS extension Extended DNS , since the maximum length of a DNS packet was previously 512 bytes (which corresponds to an amplification factor of less than 10). In practice, such attacks are carried out as distributed denial-of-service attacks , in which numerous PCs controlled by the attacker send the DNS queries from a certain point in time. A possible additional effect is the overloading of the name servers involved.
Open resolvers that answer queries from any source address are suitable as reinforcing name servers . In the past, these were used very often as reinforcement systems because they were available in large numbers, among other things because the BIND name server was configured as an open resolver in its standard configuration. In the meantime, there are still open resolvers, but resolvers are increasingly being restricted to local address areas and can therefore not be used for amplification attacks.
Authoritative name servers are also suitable as reinforcement systems, provided that you can trigger a large response packet from them. With the introduction of DNSSEC and the associated long EDNS response packets, there is an increasing number of authoritative name servers that are becoming attractive reinforcement systems for the attacker. Since authoritative name servers are supposed to answer queries from all over the Internet, access cannot be restricted using IP address ranges. Instead, rate limiting is discussed and tested, with the conflict of objectives being to filter as many attack packets as possible without affecting legitimate requests.
The anonymization of the attack makes an effective defense more difficult. Only the IP addresses of the name servers are visible to the victim, but not those of the actual attacker. A widespread use of ingress filters would provide effective protection, because it would prevent spoofed IP packets from entering the Internet. A change to the Transmission Control Protocol as the transport protocol would also prevent IP spoofing and thus amplification attacks, but this solution is rejected with reference to performance losses.
example
A massive DNA amplification attack took place on February 15, 2006. The target was three of the 13 DNS root name servers over a period of 20 minutes, one of which was unavailable and the other two were slowed down.
Another attack took place on March 19, 2013 on the well-known anti-spam organization spamhaus.org. In this specific case, each request was about 36 bytes long. A DNS zone file of around 3000 characters in length was requested. So each request was amplified by the DNS servers almost by a factor of 100. Cloudflare registered at least 30,000 requesting DNS servers. Due to the distribution over many DNS servers, the load on the individual DNS server was low and hardly noticeable as a special event for its administrator. The attackers therefore only needed 750 Mbit / s outgoing bandwidth to generate an average traffic load of 75 Gbit / s on the victim.
Individual evidence
- ↑ SSAC Advisory SAC008 DNS Distributed Denial of Service (DDoS) attacks. (PDF; 986 kB) In: ICANN . May 2006, accessed April 3, 2012 .
- ^ The DDoS That Knocked Spamhaus Offline (And How We Mitigated It). March 20, 2013, accessed March 27, 2013 .