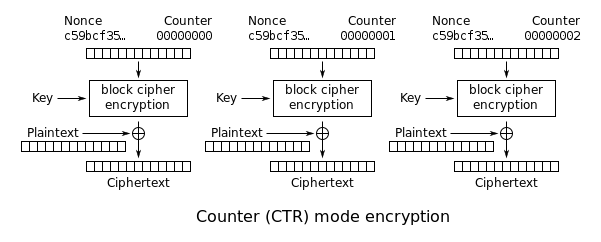
Counter mode
Counter Mode ( CTR ) is an operating mode in which block ciphers can be operated in order to generate a stream cipher . A generated ciphertext block is combined with the plaintext using an XOR operation.
General
The peculiarity of the counter mode compared to other operating modes is the fact that the initialization vector consists of a random number ( nonce ) to be selected for each cipher, linked to a counter that is incremented with every further block. The link can e.g. B. by concatenation (appending), addition or XOR .
Encryption
For encryption, an initialization vector is encrypted with the key and an intermediate key is thus produced. This is then combined with the plain text using an XOR operation. This is where the ciphertext arises.
Decryption
For decryption, the same meter is encrypted again with the key in order to obtain the same intermediate key . This is now applied to the ciphertext by means of an XOR operation, so that the plaintext is recovered.
advantages
Like Output Feedback Mode, counter mode is an operating mode that allows a block cipher to be operated as a stream cipher. The advantages of the OFB mode compared to cipher block chaining mode , cipher feedback mode and other modes which continue to use plain text-dependent data for the next block also come into play here:
- Bit errors during transmission result in errors in only the corresponding bits of the plain text (instead of making a whole block or possibly even another block unusable)
- Encryption and decryption are identical, so one-way functions can also be used here
- The keystream can be calculated in advance.
In contrast to the OFB mode, the key for a block does not depend on the key for the previous block, so:
- you have random access to every encrypted block and
- all encryption and decryption operations can be carried out in parallel.
application areas
- In ZIP archives in combination with AES .
- In TLS 1.2 in combination with AES (as part of the GCM operating mode ).
- In off-the-record messaging in combination with AES .
- Encryption in the Bluetooth Link Layer (AES-CTR) in the payload.
literature
- Claudia Eckert: IT security . 5th edition. 2008, ISBN 978-3-486-58270-3 .