Defensive programming
Under defensive programming one is programming of computer systems understand the possible checked many conditions even before the actual end in itself is met. A programmer is faced with various known and unknown aspects of user input, various operating systems and versions. The defensively programmed applications are suspicious of all inputs and requirements and behave robustly against violations. By anticipating as many circumstances as possible, they continue or break off in an orderly process.
An alternative approach to defensive programming is design by contract . The component that uses the service of another component only ensures a series of preconditions on the basis of a contract and relies on subsequent conditions that were defined for the service in the contract. In the case of defensive programming, on the other hand, the preconditions would be unclear, while the postconditions would have to be checked by the claiming component.
A system does not have to be committed to a single concept. Basically, it can be divided up in such a way that external influences (user input, data import, API ) are to be handled defensively, while this is not necessary for internal processes.
Examples
- A printer entry is to be deleted. The defensively created program first checks whether the printer to be addressed is available at all. The program checks the return value of the delete function. If deletion cannot be performed due to lack of access rights, the program tries to grant itself the rights and tries to delete again.
- A file is to be copied from one directory to another directory. A defensive program checks whether the source directory exists and is readable. A check is then made as to whether the target directory exists and is writable. If it does not exist, the program creates the required directory itself and, if necessary, obtains the necessary rights beforehand. Ultimately, the file is then copied into the verified existing and accessible directories.
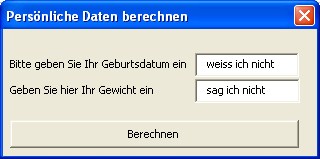
- The input of a user is completely contrary to expectations (see illustration). A far-sighted programmer recognizes such possible situations and checks the user input before the actual processing begins. In the example in the figure, the program would have to abort the process and output a message to the user that he would have to correct the entries.
Opposite of defensive programming
Depending on the programming language, the programmer has various other options for exception handling , the handling of exceptions. However, these possibilities are no longer summarized under the term defensive programming , but the aim is to intercept any unpredictable errors that occur at will. The instruction popular in Visual Basic (colloquially from an unknown source also called OERNy, in German “just go ahead”) , for example, behaves contrary to defensive programming . The advantage here is that the application does not crash, but with unforeseeable consequences, i.e. the result may be completely incorrect.
On Error Resume Next