Merkle's meta-procedure
Merkle's meta-method (also Merkle-Damgård construction ) is a method for the construction of cryptographic hash functions that goes back to the work of Ralph Merkle and Ivan Damgård .
There is a compression function that maps a bit long input to a bit long output. It is collision-proof , which means that it is not possible with realistic effort to find two different inputs that are mapped to the same output. The application of Merkle's meta-method results in a collision-proof hash function that maps messages of any length to a hash value of bits.
method
The message is first expanded with a padding process so that the length is a multiple of the block size . Then it is divided into blocks of length :
- with .
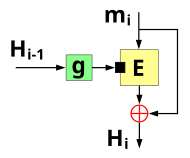
The compression function is iteratively applied to the bit long output of the previous iteration and the next block of the extended message until it is fully processed. In the first iteration, the input consists of a bit long initialization vector , often with the value 0, and the first message block .
- .
The hash value is then calculated from the last compression output by a finalize function: . The finalization function is often identity or truncation .
Block encryption is often used as the compression function, for which there are mainly two options: The Davies-Meyer compression function uses the message block as a key to encrypt the result of the previous compression . Then the cipher text calculated in this way is linked with the plain text (often by bit-wise XOR ). This removes the property of a block cipher to map the plaintext bijectively to the ciphertext, and the mapping from to is much more similar to a random function. Otherwise the compression function would not be collision-proof either, because an attacker could pretend and decrypt with various .
The Matyas – Meyer – Oseas compression function encrypts the message block with the previous compression output as the key. Here, too, plain text and key text are then linked. To adapt to the given key length, it may be necessary to expand or compress with a function .
Padding
In order for the collision security of the compression function to be verifiably transferred to the hash function, the padding process must meet certain conditions. The following conditions are sufficient for this:
- is an initial part of , d. That is, the messages are not changed, just expanded with a tail.
- Two messages of the same length are extended with end pieces of the same length.
- Two messages of different lengths are expanded differently, so that they differ in the last block, which is entered in the last compression level.
Typically, when padding, a coding of the bit length is appended to the message, and bits with the value 0 are inserted in between, so that it is a multiple of the block size :
weaknesses
A weakness is a possible extension attack ( extension Attack ): When the finalize function is reversible, then you can from the hash value of an unknown message the hash easily determine a message from the above enhanced message by adding an extension can be seen. So you can determine hash values for messages that start with, even if you don't know. Since a random oracle does not have this property, it can lead to attacks on processes that only have proof of security in the random oracle model. It also follows from this: once you have found a collision between two messages with the same number of blocks , you can easily determine further collisions by expanding them.
Finding multiple collisions, i.e. several messages that all have the same hash value, requires little more effort than determining a single collision.
A Herding attack , i.e. finding a suitable ending for a self-selected hash value z and a given beginning part of a message so that the entire message hash to z, i.e. That is, finding one with requires more effort than finding a collision, but much less than should be the case for a random oracle as a hash function .
An attack to determine a second pre- image attack , in which one searches for a second one with the same hash value for a given message , is possible with a message of the length of blocks with the expenditure of time , and thus considerably faster with long messages than with a systematic one Try (brute force), which requires some steps.
Improvements
In order to overcome these weaknesses, Stefan Lucks proposed the wide-pipe-hash construction: To calculate a hash value of bit length, one uses a compression function whose output is longer than , typically twice as long. thus compresses bits from the previous iteration and a bit-long message block into an output of bits. After the last iteration, the output is shortened from to bit by another compression function , if you do not simply discard half the output and use the other half as a hash value.
Nandi and Paul have shown that this construction can be done about twice as fast ( fast wide pipe hash ) by only entering bits from the previous compressions into the next compression, along with a bit long message block . The other half of the compression output is XORed with the following input:
In the last stage, the output of the penultimate is completely processed, and the message block is only bits wide (unless you use another compression function with a larger input):
and mean the first and second half of the bit string .
In addition to the wide pipe hash construction, the HAIFA construction is also considered a further development of the Merkle-Damgård method.
Individual evidence
- ↑ Goldwasser, S. and Bellare, M. "Lecture Notes on Cryptography" . Summer course on cryptography, MIT, 1996-2001.
- ^ Yevgeniy Dodis, Thomas Ristenpart, Thomas Shrimpton. Salvaging Merkle – Damgård for Practical Applications . Preliminary version in Advances in Cryptology - EUROCRYPT '09 Proceedings, Lecture Notes in Computer Science Vol. 5479, A. Joux, ed, Springer-Verlag, 2009, pp. 371-388.
- ↑ JS Coron, Y. Dodis, C. Malinaud, and P. Puniya. Merkle – Damgård Revisited: How to Construct a Hash Function. Advances in Cryptology - CRYPTO '05 Proceedings, Lecture Notes in Computer Science, Vol. 3621, Springer-Verlag, 2005, pp. 21-39.
- ↑ Antoine Joux. Multicollisions in iterated hash functions. Application to cascaded construction. In: Advances in Cryptology - CRYPTO '04 Proceedings, Lecture Notes in Computer Science, Vol. 3152, M. Franklin, ed, Springer-Verlag, 2004, pp. 306-316.
- ↑ John Kelsey and Tadayoshi Kohno. Herding Hash Functions and the Nostradamus Attack In Eurocrypt 2006, Lecture Notes in Computer Science, Vol. 4004, pp. 183-200.
- ↑ John Kelsey and Bruce Schneier. Second preimages on n-bit hash functions for much less than 2 n work. In Ronald Cramer, editor, EUROCRYPT, volume 3494 of LNCS, pages 474–490. Springer, 2005; [1] .
- ^ S. Lucks, Design Principles for Iterated Hash Functions. In: Cryptology ePrint Archive, Report 2004/253, 2004.
- ↑ Mridul Nandi and Souradyuti Paul. Speeding Up the Widepipe: Secure and Fast Hashing. In Guang Gong and Kishan Gupta, editor, Indocrypt 2010, Springer, 2010.
literature
- Hans Delfs, Helmut Knebl: Introduction to Cryptography. Springer 2002, ISBN 3-540-42278-1 , p. 40.