Demilitarized zone (computer science)
A demilitarized zone ( DMZ , also demilitarized zone ) describes a computer network with security-controlled access options to the servers connected to it .
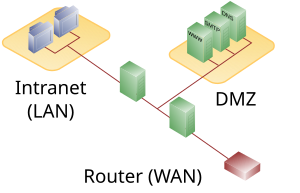
The systems installed in the DMZ are shielded from other networks (e.g. Internet , LAN ) by one or more firewalls . This separation allows access to publicly available services ( bastion hosts with e.g. e-mail , WWW , etc.) and at the same time protects the internal network (LAN) from unauthorized access from outside.
The point is to provide network services to both the WAN ( Internet ) and the LAN ( intranet ) on the most secure basis possible .
A DMZ develops its protective effect by isolating a system from two or more networks.
Security aspects
In Germany, the BSI recommends a two-stage firewall concept for the Internet in its IT-Grundschutz Catalogs . In this case, a firewall separates the Internet from the DMZ and another firewall separates the DMZ from the internal network. As a result, a single vulnerability does not immediately compromise the internal network. Ideally, the two firewalls are from different manufacturers, since otherwise a known vulnerability would be sufficient to overcome both firewalls.
The filter functions can, however, be taken over by a single device; in this case the filtering system requires at least three network connections: one each for the two network segments to be connected (e.g. WAN and LAN) and a third for the DMZ (see also dual homed host ).
Even if the firewall protects the internal network from attacks by a compromised server in the DMZ, the other servers in the DMZ can be attacked directly as long as further protective measures are not taken. This could e.g. B. segmentation in VLANs or software firewalls on the individual servers that discard all packets from the DMZ network.
A connection should always be established from the internal network into the DMZ, never from the DMZ into the internal network. A common exception to this is access from the DMZ to database servers in the internal network. As the last instance, the firewall administrator watches over this principle before the rule is activated. This largely reduces the risk potential of a compromised server in the DMZ to attacks:
- to the inner firewall directly
- to other servers in the same DMZ
- about security gaps in administration tools such as Telnet or SSH and
- on connections that were established regularly in the DMZ.
Other versions
Exposed host as "pseudo DMZ"
Some routers for home use incorrectly refer to the configuration of an exposed host as “DMZ”. You can specify the IP address of a computer in the internal network to which all packets from the Internet that cannot be assigned to another recipient via the NAT table are forwarded . This means that the host can be reached from the Internet (also for potential attackers). A port forwarding the ports actually used is the - if possible - preferable.
It depends on the specific configuration of the firewall whether port forwarding to other computers is taken into account first and only then the exposed host , or whether the exposed host makes the port forwarding to other computers ineffective.
Dirty DMZ
The network segment between the perimeter router and the firewall of the (internal) LAN is usually referred to as dirty DMZ or dirty net . From the outside, this zone has only the limited security of the perimeter router. This version of the DMZ is less of a hindrance to data transfer, as the incoming data only needs to be filtered (perimeter router).
Protected DMZ
A protected DMZ is a DMZ that is attached to a separate LAN interface of the firewall. This DMZ has the individual security of the firewall. Many firewalls have multiple LAN interfaces to set up multiple DMZs.
Web links
- DMZ built itself . hot networks
Individual evidence
- ↑ Telnet clients from several manufacturers are vulnerable Heise.de, March 29, 2005
- ↑ Two vulnerabilities in PuTTY Heise.de, February 21, 2005