Firewall


A firewall (from English firewall [ ˈfaɪəwɔːl ], “ fire wall ” or “firewall”) is a security system that protects a computer network or an individual computer from unwanted network access. In a broader sense, a firewall is also a partial aspect of a security concept .
Every firewall security system is based on a software component . The firewall software is used to restrict network access based on the sender or destination and the services used . It monitors the data traffic flowing through the firewall and uses defined rules to decide whether certain network packets are allowed through or not. In this way it tries to prevent unauthorized network access.
Depending on where the firewall software is installed, a distinction is made between a personal firewall (also known as a desktop firewall ) and an external firewall (also known as a network or hardware firewall ). In contrast to the personal firewall, the software of an external firewall does not work on the system to be protected, but on a separate device that connects networks or network segments and, thanks to the firewall software, simultaneously restricts access between the networks. In this case, “Firewall” can also be used as a name for the entire system (a device with the function described). Due to the design, there are major conceptual differences between the two types .
The function of a firewall is not to detect attacks. It should only implement rules for network communication. So-called IDS modules are responsible for tracking down attacks , which can be placed on top of a firewall and can be part of the product. However, they do not belong to the firewall module.
general basics
The following basic knowledge is helpful in understanding how a firewall works. The respective main articles present the topics in detail.
How remote access to a computer system works
Access to a network service
A network service is a computer program that enables resources such as files and printers to be accessed over a network. For example, Internet pages are stored as files on a computer (server). Only a network service running on the server (in this case a web server software) makes it possible to access the pages from the Internet and thus load and display them on a remote device. So that network services can be reached from the network, they each bind to a port on the network interface. It is said that they “ open a port ”, which, conversely, means that an open port always belongs to a computer program that can receive network queries.
A security flaw in a network service can provide the basis for performing actions on the computer beyond the permitted access functions.
Note: A service (under Microsoft Windows English service ; under Unix English daemon ) is characterized by the fact that it is executed every time the system is started, regardless of whether a user logs on to the computer. There are programs with a functionality corresponding to the network service, which open a port, but are only started after the user has logged on. Although these programs are not strictly speaking services, for the sake of simplicity they are also referred to below as network services.
The way back from the remote network service to the client
The way back from the remote network service to the requesting PC (more precisely the client ), which accesses the service, can sometimes be used for comprehensive remote access. To stick with the above example, the user starts a browser that is supposed to display web pages from the Internet on his PC. If the browser contains a corresponding security hole, the contacted Internet server can now access this PC and carry out actions there that go beyond the normal display of Internet pages. In the worst case, simply calling up an appropriately prepared website is enough to even secretly install malware on the PC. In turn, malware can work as a network service on the PC and thus enable constant remote access to the PC.
Instead of installing a network service on the PC, the malware can also establish a connection to the Internet on its own and connect to a network service that is operated on the Internet. For example, a botnet mostly works this way. In such a case, the return path is used for permanent remote access to the PC.
The network implementation of the operating system
For communication in the network, the communication partners need knowledge of the basic protocols that are used for addressing and transporting data. Occasionally, an incorrectly implemented network connection of the operating system (including defective driver software ) can be used for network access that was not intended by the manufacturer in this form. An example of the exploitation of a formerly widespread error in the implementation of the IP protocol is Ping of Death , which systematically crashed the target system. Similar loopholes sometimes also make it possible to inject and execute program code on the target system.
Protection function and limits of a firewall
A firewall is used to prevent unwanted access to network services. It is based on the addresses of the communication partners (ie "who is allowed to access what"). As a rule, a firewall cannot prevent the exploitation of a security gap in the network service if the communication partner is allowed to access it.
When using the return route, a firewall cannot protect against access to security holes in the browser if the communication partner can access the endangered areas of the program. Programs that are intended for network access should therefore be kept up to date in order to close known security holes. Some firewalls offer filters that further restrict remote access to the network service being used, for example by filtering endangered ActiveX objects from websites. The browser can then no longer access such objects embedded in a website (it does not display them), which also means that it cannot be attacked via these objects. Alternatively, this behavior can also be achieved via the configuration of the browser used.
Depending on the type of firewall, a firewall can, in the best case scenario, draw attention to the network access of secretly installed malware and sometimes even prevent its network access. However, such success is heavily dependent on the skill of the respective malware (see the limits of the personal firewall and the external firewall ).
The exploitation of errors in the network implementation of the operating system can, in the best case, fend off a firewall.
The indicated limits of a firewall in comparison to the benefits can be compared with the seat belt of an automobile, for which there are also scenarios in which it is not able to protect the driver. It makes sense to put on the seat belt and at the same time drive carefully knowing your limits. An exception could be a belt that simultaneously endangers the driver (here with reference to the personal firewall ), which can lead to alternative solutions offering greater security.
The firewall as part of a security concept
Only when it is known against which scenarios a certain level of security is to be achieved can one start thinking about how this will be implemented. The creation of a security concept helps . In larger organizations, a separate security policy is usually used for this .
The firewall is part of the security concept. Just as “fire protection” is a bundle of measures (and not just the smoke detector in the stairwell), this partial aspect can be a bundle of several measures, depending on the security concept. The firewall can consist of several components, some of which serve, for example, a DMZ . Maintenance can also be an integral part of the partial aspect, as can the evaluation of the logging of firewall components.
Filter technologies
→ For a detailed description, see firewall technologies
Packet filter
The simple filtering of data packets based on the network addresses is the basic function of all firewalls (in a TCP / IP network this means more precisely the filtering of the port and the IP address of the source and target system).
Stateful packet inspection
This state-controlled filtering is an advanced form of packet filtering. This makes it possible to restrict access to an established connection more precisely and thus better protect the internal network from unwanted external access.
Proxy filter
A proxy filter establishes the connection with the target system on behalf of the requesting client and forwards the response from the target system to the actual client. Since he conducts the communication himself, he can not only see it, but also influence it at will. Specialized in a particular communication protocol, such as B. HTTP or FTP , he can analyze the data coherently, filter requests and make any adjustments if necessary, but also decide whether and in what form the target's response is passed on to the actual client. Sometimes it is used to temporarily store certain answers so that they can be accessed more quickly for recurring inquiries without having to request them again. Several such filters are often used in parallel on a single device in order to be able to serve different protocols.
Content filter
This content filter is a form of proxy filter that evaluates the user data of a connection and is intended, for example, to filter out ActiveX and / or JavaScript from requested websites or to block generally known malware when downloading . Blocking unwanted websites using keywords and the like are also included.
Deep packet inspection
Deep packet inspection can be used to analyze further, in particular protocol-specific information. This makes it possible to use rules based on URLs , file names, file contents ( virus scan or data loss prevention ) and the like. This is similar to the possibilities of a proxy or a content filter, but usually covers numerous protocols.
In order to be able to analyze encrypted connection data and content, SSL Deep Packet Inspection is used, which terminates an existing SSL encryption , examines the content and then re-encrypts it for the client. To do this, it is usually necessary to install a CA root certificate on the client that allows the firewall to generate suitable certificates itself during operation. Technically, this corresponds to a man-in-the-middle attack .
Visibility for users
In order to be able to filter network packets, the firewall must be between the communication partners. It can appear to the communication partners in different ways, whereby the first four manifestations can only occur on an external firewall:
Visible
The firewall acts as an intermediary between the source and target systems and is visible to both sides. Here the client asks the proxy firewall to take over communication with the target system on its behalf. For example, the web browser is configured in such a way that it does not send all Internet inquiries directly to the respective target address, but sends them as a request to the proxy. The proxy now connects to the target system. Only after the analysis has been carried out does the proxy forward the target system's response to the requesting client.
Transparent to one side
One of the two sides addresses the target directly and not the firewall. With an appropriately configured network infrastructure, the request in question is automatically routed over the ( NAT or proxy) firewall without the sender noticing or even being able to influence it. The connection to the other side is now established via the address of the firewall. Possible attacks from there are also directed at the firewall and do not hit the client directly. Because for this side the firewall represents the communication partner to be addressed, who is addressed on behalf of the actual communication partner. This form is the most common type of firewall devices for the home.
Transparent on both sides
The firewall lies transparently (almost invisibly) between the two networks, thus enabling a continuous connection between the communication partners so that the systems in front of and behind the firewall can see each other directly. The data stream simply flows through the firewall. At the level of IP addressing , the remote station does not see the firewall as a communication partner, but merely recognizes it as a link between the subnets ( router without NAT). Nevertheless, the firewall software running on the network device (router) can interrupt the data stream (filter out certain packets).
Invisible
Just as with the double-sided transparent mode, the data stream simply flows through the firewall. The device on which the firewall software is running now works like a bridge , which means that it is not visible to the communication partners either at the IP level or from the perspective of low-level addressing.
Local
A firewall software installed locally on the computer (personal firewall) monitors the data stream flowing through it on site (on the computer whose network packets it is to filter; in this paragraph referred to as the source system ). From the point of view of the target system, the firewall is therefore behind the network adapter of the source system. This changes neither the network address of the source system nor the communication path to the target system. This means that the personal firewall is practically invisible from the point of view of addressing. However, this only relates to the communication path and does not mean that it cannot be traced (due to the behavior of the source system) or that it cannot be directly attacked via the address of the source system (in contrast to the external bridge firewall, which has no network address).
Set of rules
The rules of a firewall determine what should happen to a network packet that fits into the pattern of a filter. The promotions can have different titles depending on the product. Either the request is not allowed and the packet is discarded locally (usually called DROP) or it is actively rejected (REJECT), for example by being answered with an ICMP packet. A permitted request is called ACCEPT, ALLOW, PASS or FORWARD, whereby FORWARD can also indicate a redirection of the request, depending on the product and configuration.
Verifiability of the source code
In the case of software products, free access to their source code is an aspect of computer security. Among other things, it is important to minimize the risk that a product may contain functionalities that the user should not be aware of. For example, there are some closed-source products from the field of personal firewalls that secretly send data to the manufacturer themselves, i.e. do exactly what some users are actually trying to prevent with the product. Open-source software can be checked by the public to this effect and, in addition, examined for weaknesses using legally unobjectionable means, which can then be closed more quickly. Open source license models are not to be equated with free software; Open source as well as free software also include commercial products ( free software is not the same as freeware ).
Firewall types in comparison
There are two types of firewalls, depending on where they are used. Personal firewalls are programs that run on the computer they are designed to protect. External firewalls are physically upstream of the computer or computer network to be protected.
Differences between personal firewalls and external firewalls
→ Main type section: Personal firewall (also desktop firewall) and external firewall (also network or hardware firewall)
Both types of firewall can be viewed as a complement to each other. It cannot be said across the board that one of the two can be replaced by the other, as there are major conceptual differences:
- An external firewall usually mediates between two networks, for example by controlling Internet access. In contrast to this, the personal firewall also filters the connections of the computer from and to the communication partners of the local network ( LAN ).
- In the case of higher security requirements , an external firewall can also filter connections within the local network by being physically connected directly upstream of the computer to be protected. The external firewall can also monitor a specially secured network (segment) within the local network, with which it filters at least part of the communication in the LAN. However, this is rarely found in a home network.
- The personal firewall exclusively implements an elementary function on mobile computers: It differentiates on which network the computer is currently being operated on and then switches over to the associated set of rules. For example, the file sharing of the mobile computer can be reached within the private network, whereas access to it is prevented within a public network (for example in an Internet café).
- An external firewall that establishes the connection to the Internet on behalf of the computer automatically prevents (due to its design) someone from the Internet from being able to access the network services of the protected computer. It thus also offers effective protection against network access to malware if it installs a network service that waits for someone to set up a connection to it from the Internet. In contrast to the personal firewall, there is no need to maintain a set of rules.
- On the other hand, simple external firewalls are not able to prevent malware from establishing a connection to the Internet, or only to a limited extent , because - unlike most personal firewalls - they were not designed for such a task. If the network communication from the malware is not prevented, unrestricted remote access to the computer is even possible despite the use of an external firewall.
- Exceptions are the external proxy firewall and the so-called next-generation firewall , which can support a possibility of only allowing network communication for certain applications.
A personal firewall is not generally better or worse than an external firewall, but above all different. The external firewall is more reliable in all the areas in which the functionalities are the same. This is because such a specialized device primarily offers a security-optimized system that is stable on the network side, which, thanks to its physical separation from the computer system to be protected, cannot be easily manipulated or even deactivated .
Personal firewall (also desktop firewall)
Firewall software installed locally on the computer is referred to as a personal firewall or desktop firewall . It is their job to prevent unwanted external access to network services on the computer. Depending on the product, it can also try to prevent applications from communicating with the outside world without the user's consent.
advantages
Computer worms that exploit a security flaw in a network service to spread can only infect the computer if the corresponding network service is available to the worm. Here a personal firewall can restrict remote access to the network service and thus make infection more difficult or even prevent it. The same applies to network access by a possible intruder.
Such filtering is required when a network service is started on the computer that is required for operation and access to it is to be restricted . Remote access to network services that are not required, on the other hand, can be prevented without a firewall by deactivating these services .
In addition, the rules of the personal firewall can, in the best case, prevent a service that has been secretly reactivated or installed by malware from being accessible from the network without hindrance. The use of the personal firewall has paid off if the (possible) message from the firewall software is used to immediately remove reactivated services along with malware.
Limits
Personal firewalls can protect against some computer worms that can spread over the network, but they also do not protect against the installation of any other malware.
Depending on the product and operating mode, a personal firewall can recognize newly added network services (and applications with the corresponding functionality ) and ask the user whether remote access should be permitted. In order for this part of the protective function to function reliably, the firewall software must run consistently and stably. This is a challenge even with a non- compromised system . On the other hand, the user has to know what he is doing.
In addition, some products try to prevent application programs from communicating with the outside world without the consent of the user, with the intention of restricting network access by malware. Such a success of the firewall software is, however, highly dependent on the skill of the malware in question (specialist articles from Microsoft's TechNet Magazine and the c't warn that the personal firewall can only prevent unwanted network access if the malware does not make a great effort there to hide their activities). This type of protective effect can be compared to a garden fence, which is an existing but not an insurmountable obstacle. In contrast to the garden fence, however, the firewall software can fail suddenly and unexpectedly, especially on a compromised system.
If malware is discovered on the PC to be protected, network access can be prevented efficiently by removing it instead of using a firewall, because this still has an effect if the firewall software fails. Within its limits, the personal firewall can sometimes help to recognize when such communication is taking place.
disadvantage
Programs that run on the same hardware as the personal firewall software have far more possibilities to manipulate and bypass them than with an external firewall. A crash or even permanent deactivation of the firewall software due to a software error or malware result in unrestricted access to the previously filtered network services, sometimes without the user noticing. Depending on the product and the user's level of knowledge, incorrect operation can also cause this state.
It is also a problem of the concept that the firewall software is positioned between the normal network implementation of the operating system and the outside world, which means that although the original network implementation is no longer partially open to attack, the much more complex firewall software is directly vulnerable. Experience shows that software contains more errors and points of attack the more complex it is. Personal firewalls can themselves contain security gaps which, for example, only offer a computer worm approaches for remote access.
Since the components of a personal firewall run (at least partially) with extended rights and kernel components are usually installed, programming and design errors have a particularly strong effect on the security, performance and stability of the computer system. Depending on the product, these components can also be used, for example, to secretly transmit data to the manufacturer and to create additional functions that the user does not specifically want and that would not exist without the installed firewall software.
In terms of security, the use of a personal firewall becomes questionable if it is switched off for smooth operation during a computer game, for example. The use of a personal firewall on such a system makes no sense, as the firewall software merely conceals the remaining risks and thus becomes a security risk itself (it gives the user a feeling of security during the rest of the time, which is without any basis on this system).
On systems in which a personal firewall is already an integral part of the operating system, it can be quite questionable to install additional firewall software. The parallel operation can lead to problems and is not necessarily associated with advantages.
Alternative solutions to prevent remote access
Deactivating all network services that are not required offers the best protection against unwanted remote access. Because even if the firewall software fails, nobody can access network services that have not been started. In addition, the start of each service slows down the startup speed of the operating system and they continue to need computer resources for their work. Depending on the operating system, there are sometimes easy-to-use tools that enable even inexperienced users to deactivate network services that are not required in a straightforward manner.
To prevent remaining network services from being accessed from the Internet, they should not be tied to the network adapter that is connected to the Internet. This task is not entirely trivial for an inexperienced user, which is why the use of an intermediary device, such as a DSL router , makes sense. This device automatically ensures that a network service is only accessible from the internal (private) network and not directly from the Internet (see also “ Advantages of using an external firewall ”).
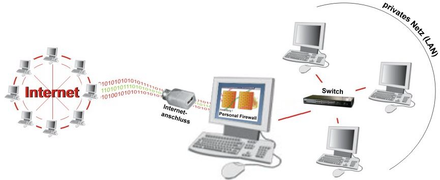
External firewall (also network or hardware firewall)
An external firewall (also known as a network or hardware firewall) restricts the connection between two networks. This could be a home network and the Internet, for example.
The external firewall is predestined to prevent unauthorized access from outside (the WAN in the figure ) to the internal system. In contrast to the personal firewall, the internal system here does not necessarily consist of a single computer, but can refer to a network of several computers that form the internal network (the LAN in the figure ).
Hardware firewall
In practice, there are no firewalls that are based exclusively on hardware . A firewall can run on its own operating system and access different network levels, but it does not become part of the hardware. A firewall always contains software as an essential component .
Rather, the term hardware firewall is used as a synonym for external firewalls . It is intended to express that this is a separate piece of hardware on which the firewall software runs. However, there is hardware that has been optimized for the use of the firewall software, for example in that a corresponding hardware design helps to accelerate parts of the decryption and encryption of certain protocols.
advantages
A direct connection of a computer to the Internet (more precisely to a corresponding modem) means that all computers from the Internet can access the computer's services linked to this network connection, which enables remote access to the computer .
In order to prevent remote access from the Internet, one solution would be to differentiate between the internal (private) network and the external network (Internet) and only bind the required services to the network interface of the internal network. An external firewall running in visible or one-sided transparent mode can take on this task: Instead of the PC, the external firewall is connected to the Internet, with the PCs from the internal network being networked with this device. The PCs now transmit their requests to the Internet to the firewall, which accesses the Internet on behalf of the PCs. The target system therefore only sees the firewall as the sender, which in turn forwards the response packets from the target system to the corresponding PC in the internal network. Depending on the type of firewall, this enables you to analyze and filter the network packets in both directions before they reach the actual communication partner.
Example configuration in the figure: The Internet connection could be a DSL connection including a DSL modem . The firewall could then be installed on a DSL router , which is addressed by the PCs in the private (self-contained) network as the default gateway . The device manages the network queries from the internal PCs and can differentiate between queries to the internal (private) and external networks (Internet) and forward them accordingly. The switch connects the PCs of the internal network with each other and is usually integrated in such a firewall, but is deliberately shown here as a separate device to make it clear that such a firewall only filters access between the internal and external network, but does not affect it has communication in the internal network.
Since the target system does not see the internal PC from the Internet, but only the firewall, possible attacks from the Internet are directed at the firewall that is predestined for this and do not directly affect the internal PC. Someone from the Internet who searches for a network service (such as file and printer sharing) on the network address of the firewall will not find it because the service runs on the PC and not on the firewall. At this level, the firewall cannot be attacked and the network services of the internal PCs cannot be accessed from the Internet.
Even malware that may secretly install a network service on the PC cannot change this state. The network service can only be accessed from the private network, but not from the Internet (after all, the malware cannot install a service on the firewall, only on the PC).
Note: For the described functionality it is necessary that the firewall device has been configured accordingly (the computer system to be protected must not be operated as a "standard server" or exposed host , or it should not be in a " DMZ ", depending on the The user interface of the firewall device can usually be easily checked and adapted if necessary without in-depth specialist knowledge).
Limits

In the private sector, packet filter firewalls that work on a DSL router are mostly used . You can only prevent individual programs from communicating with the outside world without the consent of the user to a very limited extent, because they were not designed for such a task: In order for such a device to work without permanent manual configuration, it must be able to set dynamic rules to create. Apart from requests for explicitly blocked addresses and blocked destination ports, it therefore automatically allows all communication connections that have been requested from the internal network (i.e. from the private PCs).
So if malware just installs a network service that waits for an external connection, the protection mechanism works quite well. However, if it establishes a connection to the Internet itself, the device will allow the connection because it was requested from the internal network. Such a device can only effectively prevent external connection requests.
A personal firewall offers more options here, but is not necessarily more secure and involves the risks mentioned above . A personal firewall is not an equal replacement for such devices, but under certain conditions it can serve as a corresponding supplement.
Accordingly, some DSL routers, which, in contradiction to this, apparently seem to implement network access control for PC applications, achieve this with a simple trick: According to the manual, the user should first install the administration software for the device on the PC. Together with the administration software, an in-house personal firewall can also reach the home PC. Even if the locally installed software reports with the logo and name of the external firewall, it has nothing to do with it. In terms of security, such a solution usually does not differ from other personal firewalls that are installed in addition to a DSL router.
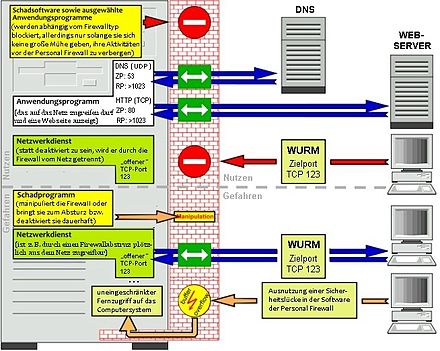
Another approach to preventing malware from communicating with the Internet is based on the idea that the firewall should block all access to the Internet by the local network that is not required, for example, to access websites. This is achieved by a filter rule blocking all requests to the Internet. Another rule now explicitly allows DNS requests to the DNS server of your choice and access to port 80 (HTTP) of any Internet server so that the network service running there can be reached for access to websites. The assumption is that malware installed on the PC to be protected, which independently establishes a connection to a network service from the Internet, is now blocked because the network request is no longer allowed to pass on its port.
This “protective effect” is very limited, however, because it cannot be ruled out with certainty that the malware to be blocked does not also use the released port for its communication. The more popular the port, the more likely such a scenario becomes . Since port 80 is enabled for communication with the Internet on almost every external firewall, numerous malicious programs now also use port 80 for their own communication with the Internet, as they can assume that the port will not be blocked. Companies tend to use such filters with the aim of restricting their employees' access to the Internet (for example, to ensure that HTML pages can be called up, but participation in the chat is prevented). In the private home network, such a set of rules usually makes no sense.
Beyond the port block, there are advanced methods on some devices to control internal connection requests using the external firewall. They usually use proxies and thus support the possibility that each application must authenticate itself to the external firewall before network communication before communication is allowed. A disadvantage of this method is that the application must know the authentication protocol (e.g. SOCKS ). In such an environment, only applications that have been expanded accordingly can be used, even though the support of these protocols is already widely used, so that in this regard one can almost speak of a standard configuration of the applications. This makes it more difficult, but not impossible, for malware to communicate with the external network unnoticed (see figure on the right).
In addition, special filters can be installed on professional firewalls that look for some known malware signatures in the network packets of a service and block the packets when they are identified.
The above-mentioned extended methods increase the damage-limiting effect of the external firewall also when communicating from the inside to the outside. However, since they are rarely found in devices for private use, they are at least an exception in this area.
External firewalls are only designed to limit network access between the internal and external network. So they do not offer any protection against unwanted access from the internal network, which according to a study by the Computer Security Institute in 2002 occurred at least twice as often as external hacking attempts. It also offers little protection against computer worms that spread over the network if they are brought into the internal network via CDs , USB sticks or floppy disks . The computer worms Sasser , W32.Blaster and Conficker have shown through outbreaks in large companies such as the German Postbank and Delta Air Lines that these routes of infection actually work despite an external firewall.
In addition, it has been known since 2013 at the latest that at least the US NSA has developed secret access options, so-called backdoors , which remove the access barriers to almost all devices from major manufacturers, including routers.
disadvantage
If your own computer does not operate any network services at the Internet interface and is otherwise operated professionally, the use of an external firewall is questionable, because the firewall may have to analyze the network packets separately for its work. It can delay the network communication to a greater or lesser extent depending on its own hardware speed, the load and the respective algorithm . However, modern devices usually cause delays below the perception threshold within normal parameters.
In addition, the use of a firewall can contribute to the fact that the user feels safe and is careless, for example by installing software from insecure sources recklessly, since the firewall supposedly protects him from remote access to possible malware. As a result, he not only loses security, but also endangers his system more than before; this also applies to the use of a personal firewall.
Further areas of application in corporate networks
In corporate networks, it is not just the transition from LAN to Internet that justifies the use of a firewall. A firewall can also be used between two or more internal organization networks in order to take account of the different protection requirements of the network zones, for example when the office network is separated from the network of the personnel department in which personal data is stored.
Firewall technologies
A firewall can use a number of methods to differentiate between desired and undesired network traffic, but not every product supports all of them.
Packet filter firewall
The task of a packet filter firewall is to block or allow network packets based on their network address. To do this, it evaluates the header information of the network packets.
The simple (stateless) packet filtering works on a firewall router with static rules and considers each network packet individually. So it does not establish any relationships with the previous network packets. In contrast, there is an extended form of (state-controlled) packet filtering that detects such relationships by using stateful inspection technology . This further restricts access to the source system that requested communication. A corresponding firewall is also classified as a pure packet filter firewall, at least as long as no (possible) proxy filters are installed on it.
Network addressing as the basis for packet filtering
Each network card has a unique serial number that can be called up, which is called the MAC address . It is composed of a manufacturer identification number and an adjacent serial number.
Since these numbers are unique, they can be used for a simple but generally valid type of addressing in a network. Simple because it can be used to address a computer in an unbranched network, for example, but it cannot be specified in the MAC address for which program on the computer the network packet is intended. Unbranched because the MAC address, due to its structure, is not suitable for being broken down into further sub-areas. It is therefore not possible to assign the addressee to a specific subnet using the MAC address. In other words, MAC addresses can be used like house numbers, but beyond that they cannot be assigned to a street or to a resident of the house.
The solution is offered by higher communication protocols that are placed over the MAC address. A network packet is thus figuratively packaged multiple times, with the MAC address representing the outer packet and the other packets being layer by layer in this packet. Within a TCP / IP network, the IP address forms the next higher protocol, i.e. the next packaging. It involves several blocks of digits, comparable to a house address, which contains a street number and a house number (which part of the IP address symbolically represents the street number, more precisely the network ID , and which part represents the house number, more precisely the computer ID , is defined by the subnet mask ). In such a network, the next higher protocol, i.e. the packaging according to the IP address, maps the port . The port is comparable to a room number or a name tag. He determines who exactly "in the house" the package is intended for (more precisely: which program should receive the package).
A firewall can evaluate all this “packaging” and filter the network packets accordingly by deciding on the basis of a “who is allowed to access what” set of rules which requests are permitted and which are not. As a rule, however, this only takes place from OSI layer 3, i.e. the IP address, since the MAC address information of the network packets changes when, for example, they pass a router on their way through the network.
Address filtering is the basic form of all other types of firewall. Filters that are used purely for filtering network addresses, i.e. packet filters , are therefore also used on all other firewalls.
Firewall router
A firewall router is classified as a packet filter firewall and is software that is installed on a router and restricts the network connection there. This type of firewall may be in one side transparent (router in NAT mode) or both sides of the transparent mode in appearance occur (router without NAT).
It is mainly associated with firewall devices that use static (stateless) packet filters, although, strictly speaking, a stateful inspection firewall can also be installed on a router. Other types of firewall differ from a firewall router in that they offer at least a more precise form of packet filtering (stateful inspection) or are based on a concept that deviates from the router and usually offer an extended form of filtering in addition to the packet filter (such as proxy Firewall and Personal Firewall ).
The firewall router is very fast compared to other types of firewall with the same hardware.
OSI layers
The OSI layer model describes the design basis of communication protocols in computer networks. According to this layer model, a packet filter accesses OSI layers 3 (IP address) and 4 (port) from the header information of a network packet.
Example of a set of rules
With the following exemplary filter rules, it should be noted that the content is not filtered according to the protocols mentioned, but rather the TCP or UDP ports belonging to the corresponding network service:
- Mail services ( SMTP - TCP port 25, POP3 - TCP port 110 and IMAP - TCP port 143) are permitted from the Internet to the mail server in the DMZ .
- The mail server can send mails from the DMZ to the Internet via SMTP and make DNS queries.
- Administration services ( SSH , remote desktop, backup - TCP port 22) to the mail server are permitted from the local network .
- All other packets in or from the DMZ are written to a log file and then discarded.
The filter decisions are made individually and independently for each packet. This type of filtering is implemented in numerous routers and layer 3 switches today .
Stateful inspection
In contrast to the static (stateless) packet filter, here the firewall rule is dynamically specified for each connection request in order to restrict access to an established connection more precisely. The firewall sets the return channel (target to source system) in direct relation to the previously established connection (source to target system) and restricts access accordingly so that only the communication partners involved can access the connection. This is the basic function that all stateful inspection firewalls can do.
Special filters from numerous stateful inspection firewalls can also view the useful data of a communication. This is useful, for example, for network protocols that negotiate a second connection between the communication partners via the user data (see active FTP ). The insight into the user data allows the filter to further refine the address filtering of the packets, but unlike a proxy filter, it is not able to influence the connection itself (it cannot change the data).
Depending on the product, the stateful inspection firewall can also detect after a connection has been established whether and when the PC to be protected (more precisely the client ) is communicating with the target system, whereby the firewall only allows responses to this. If the target system sends data that was not requested by the client, the firewall blocks the transfer even after the connection between the client and the target system has been established.
OSI layers
A packet filter based on stateful inspection technology accesses OSI layer 3 (IP address), 4 (port) and possibly 7 (user data) of a network packet.
Possible functions
Depending on the configuration of the device on which the firewall software was installed and the firewall product, a stateful inspection firewall can offer the following functions, among others:
- Protection against SYN flooding , e.g. B. through SYN cookies
- Discarding faulty packets (e.g. conflicting TCP flags such as SYN bits, ACK bits and sequence numbers)
- Protection against ping of death , smurf attacks , teardrop attacks or land attacks
Proxy firewall (also application layer firewall)
In addition to the pure traffic data such as source, destination and service, the filters of a proxy firewall (also called application layer firewall ) typically also consider the user data, i.e. the content of the network packets. In contrast to stateful inspection technology, which, depending on the product, sometimes also accesses the user data, the typical proxy filter does not simply pass the network request from the source system on to the target system. Rather, he himself establishes his own connection to the target system. Since it communicates with the target system on behalf of the requesting client, it can analyze the packets together and influence the connection. In this way, he is able to filter inquiries with regard to the communication flow of the user data and can decide which responses from the target system to pass on to the requesting client. He can change the contents of the package at will.
From a technical point of view, such a filter works as a communication partner who intervenes in the traffic and terminates the connections on both sides (there are two independent connections) instead of passing the network packets through. The filter itself is a service program for computer networks that mediates the data traffic and is therefore also called a proxy server : As an active mediator, it behaves like a server towards the requesting client, and like a client towards the other side, the target system. Since he has to know the communication protocol, there is a separate filter for each higher communication protocol ( HTTP , FTP , DNS , SMTP , POP3 , MS- RPC etc.) (one speaks therefore also of dedicated proxies ). You can u. a. unwanted protocol options prohibit by about a SMTP - Transaction no BDAT, VRFY or similar.. allow. There can even be several dedicated proxies for one and the same protocol , for example to filter different web services under HTTP; for example, one for each web application used in a company.
The generic proxy , also called circuit level proxy , is an exception . It is used as a protocol-independent filter on the proxy firewall, where it implements a port and address-based filter module that also supports (possible) authentication for establishing a connection. The filter is not able to see the communication, to manage and influence it itself, because it does not know the communication protocol.
OSI layers
A dedicated proxy as a filter, which is specialized in a certain protocol, works as an intermediary service program and therefore (like any service or application program) accesses the OSI layer 7 (application layer) . The Circuit Level Proxy as a generic (protocol-independent) filter, on the other hand, uses OSI layer 3 (IP address), 4 (port) and, if necessary, 5 (for authentication to establish a connection).
Note: Contrary to a popular misunderstanding, the basic task of an application layer firewall is not to grant or deny certain applications (programs) access to the network. The name Application was derived from the application layer of OSI layer 7, which means that a corresponding filter can look into the user data of the network packets. The task of restricting network access to applications that have authenticated themselves to the firewall usually falls (if at all) to the generic proxy filter, i.e. the filter that does not even use the application layer .
Limits: tunneling
In principle, any service can work on any port number. If TCP port 80 is enabled for HTTP in the rules, another protocol can still run on it. Only both communication partners (the client in the internal network and the service on the server from the external network) need to be configured accordingly. An attempt to prevent this using the firewall can be made with application layer firewalls. You can examine the structure of the user data and block all packets that do not correspond to the protocol of the released service. However, every protocol should transmit data, which is why the data only has to be converted accordingly in this case. If the software embeds the data to be transmitted in HTTP without violating the standard of the protocol, this firewall is also powerless against this (the remote station, i.e. the service on the server, must understand this type of conversion, however). A tunnel does such a conversion. Manipulated data can e.g. B. be packaged in image data streams.
Tunnels therefore provide a method of bypassing firewall control. Tunnels are also used to transport insecure network protocols in a tap-proof and tamper-proof manner using a secure and encrypted network protocol. This can be done, for example, through an SSH or VPN tunnel within a legitimately activated connection.
Both OpenVPN and many SSH clients (e.g. PuTTY ) are also able to set up a tunnel via an HTTP proxy, which should actually only forward websites. There is also special tunnel software for protocols such as DNS or ICMP .
Skype in particular is an example of how well most firewalls work from the inside out. As long as the users from the internal network are able to access websites, the firewall administrator hardly has a technical chance to prevent tunneling through the encryption. Thanks to whitelists, which restrict access to certain servers, firewalls can make tunneling very difficult. Organizations sometimes extend the technical measures with organizational security measures, e.g. B. a prohibition of the conscious use of tunnels in the safety guideline , which the employee has to sign.
A transparent penetration of a firewall is also known as firewall piercing.
Complementary technologies
Intrusion detection and intrusion prevention systems
"Intrusion Detection Systems" (IDS) and "Intrusion Prevention Systems" (IPS) recognize a break-in attempt based on communication patterns. The difference is that an IDS only recognizes the attack (detection) and an IPS (prevention) tries to block the attack. Although these systems do not belong to the firewall module, they can complement it and are therefore increasingly being included in a firewall solution as an additional function. Some firewall systems offer expansion options for retrofitting an IDS, including slots for expansion modules. These modules are sometimes independent processing units with CPU and main memory, as this function can require a computationally intensive performance depending on the task area. Sufficient CPU power is essential for low processing time (latency). The latency caused by IPS systems can be less than 100 microseconds, depending on the manufacturer.
The subject of recognizing attacks and reacting to them automatically is very complex. A careless concept, a poor implementation or an unfavorable configuration can possibly create the possibility for a denial-of-service attack. Some systems create a temporary firewall rule that blocks all further connection attempts from the alleged attacking IP address. However, if an attacker sends packets to the system with a fake sender address (see IP spoofing ), he can use this to prevent access to the fake address. If no exceptions have been defined for this, he can isolate all addresses from the attacked system one after the other that it needs for its work ( DNS server, etc.).
Other possible functions
The following functions can still be used on a firewall device:
- End point for VPN connections
- Consideration of Quality of Service in the processing priority
- Etherchannel (also known as link or port aggregation , bonding or trunking , depending on the manufacturer ) to combine several physical interfaces into one fast logical interface, for example two 100 Mbit interfaces of 200 Mbit
See also
literature
- Jacek Artymiak: Building Firewalls with OpenBSD and PF . 2nd edition. devGuide.net, Lublin 2003, ISBN 83-916651-1-9 .
- Wolfgang Barth: The Firewall Book. Basics, structure and operation of secure networks with Linux . 3rd updated and expanded edition. Millin-Verlag, Poing 2004, ISBN 3-89990-128-2 .
- Federal Office for Information Security: Design of security gateways. The right structure and the right modules for a secure network . Bundesanzeiger, Cologne 2005, ISBN 3-89817-525-1 .
- WR Cheswick, SM Bellovin, AD Rubin: Firewalls and internet security. Repelling the Wily Hacker . Addison-Wesley, Boston MA a. a. 2007, ISBN 978-0-201-63466-2 (Addison-Wesley Professional Computing Series) .
- Andreas Lessig: Linux Firewalls. A practical introduction . 2nd edition, O'Reilly, Beijing et al. a. 2006, ISBN 3-89721-446-6 ( download of the LaTeX sources)
- RFC 2979 Behavior of and Requirements for Internet Firewalls.
- Stefan Strobel: Firewalls and IT security. Basics and practice of secure networks: IP filters, content security, PKI, intrusion detection, application security . 3rd updated and expanded edition, dpunkt-Verlag, Heidelberg, 2003, ISBN 3-89864-152-X (iX edition)
Web links
- Checklist of the State Commissioner for Data Protection Lower Saxony from 1999 (PDF; 146 kB)
- BSI Firewall Study from 2001 ( Memento from January 25, 2012 in the Internet Archive )
- Article in the HaBo Wiki
Individual evidence
- ↑ duden.de , definition of “firewall”, as of May 26, 2012
- ↑ a b Michael Wächter, “Falsification and Progress in Data Protection”, ISBN 3-428-09780-7 , 1998, p. 92
- ↑ "HIPAA Training and Certification: Job-Role-Based Compliance", ISBN 978-1-4239-5899-4 , Axo Press, Supremus Group 2008, p. 18
- ↑ Erwin Erasim, Dimitris Karagiannis (ed.), "Security in Information Systems - SIS 2002", ISBN 3-7281-2864-3 , Hochschulverlag AG, 2002, p. 88
- ↑ Critical security gap in the Windows server service , heise Security, October 23, 2008
- ↑ Holger Schwichtenberg, Frank Eller: “Programming with the .NET class library”, ISBN 3-8273-2128-X , Addison-Wesley-Verlag, 2004, p. 434
- ↑ Newsletter Bürger CERT ( Memento from January 10, 2015 in the Internet Archive ), “Manipulated Websites”, January 21, 2010
- ↑ Harald Schumann: Attack from the Net , tagesspiegel.de , October 31, 2010
- ↑ Security gaps in Cisco's IOS , about the possibility of infiltrating program code with a prepared ping packet, Heise Security, January 25, 2007
- ↑ Andrew Lockhart: "Network Security Hacks", ISBN 978-3-89721-496-5 , O'Reilly Verlag, 2nd edition 2007, p. 130
- ^ Richard A. Deal: "Cisco Pix Firewalls", ISBN 0-07-222523-8 , 2002, p. 207
- ^ A b Deconstructing Common Security Myths , by Microsoft TechNet Magazine , Jesper Johansson and Steve Riley , May / June 2006 issue
- ↑ a b ZoneAlarm im Kreuzfeuer , The Spy Who Came From Inside , c't Issue 17 ( Memento of October 16, 2007 in the Internet Archive ), pp. 108–110, Jürgen Schmidt , August 7, 2006
- ↑ Protection against viruses under Windows Answers to the most frequently asked questions ( Memento of October 16, 2007 in the Internet Archive ) , c't issue 18, Daniel Bachfeld , p. 196
- ↑ BSI basic protection catalogs: Development of a concept for security gateways
- ↑ a b firewall calls home magazine com! , Edition 4/2006, p. 12
- ↑ a b c d G. Borges, J. Schwenk, C. Stuckenberg: "Identity theft and identity abuse on the Internet", ISBN 978-3-642-15832-2 , Springer Verlag 2011, p. 61
- ↑ Company perimeter . Palo Alto Networks. Retrieved July 7, 2016.
- ↑ Next Generation Intrusion Prevention System (NGIPS) ( Memento from July 6, 2016 in the web archive archive.today )
- ↑ a b W. R. Cheswick, SM Bellovin, AD Rubin: "Firewalls and security in the Internet", ISBN 3-8273-2117-4 , Addison-Wesley-Verlag, p. 159 ff.
- ↑ a b c Problem with BitDefender and the Windows Firewall settings on Windows 10 , bitdefender.com, July 31, 2015
- ↑ Personal Firewalls, Part 2 ( Memento from February 12, 2010 in the Internet Archive ) by copton.net, Alexander Bernauer
- ↑ a b Support from Microsoft on the subject of "Windows firewall does not start due to error 0x8007042c", based on Windows 7, accessed on July 5, 2016
- ↑ Disable bagle worms Windows Firewall , winfuture.de, message from October 31, 2004
- ↑ Note: A previously executed (ie installed on the system) malware can be reliably by the recording of the last "clean" image of the hard disk ( Image ) from the computer system removed (see also G4L , Clonezilla , Partimage ) whereas, for example, an antivirus software only conditionally is able to completely remove the malware and its manipulations on the computer system. See: Cleaning a Compromised System , Microsoft TechNet, Jesper M. Johansson, May 7, 2004
- ↑ Personal Firewalls (PDF), Author: Ralf Hildebrandt, lecture slides “Benefits and Dangers”, p. 6 Protection against “ Ping of Death ”
- ↑ Personal Firewalls, Part 1 ( Memento from April 15, 2011 in the Internet Archive ) by copton.net, Alexander Bernauer
- ↑ Critical security gaps in Symantec's desktop firewalls , Heise.de, May 13, 2004
- ↑ Software with errors and their consequences ( Memento from January 9, 2015 in the Internet Archive ) (PDF), Melanie Ulrich ; US Magazine Wired ; January 14, 2007
- ↑ Witty worm penetrates ISS security products through a hole , by heise.de, Daniel Bachfeld , March 22, 2004
- ↑ Deactivate network services on a Windows XP / 2000 system: win32sec from dingens.org (graphical), svc2kxp.cmd from ntsvcfg.de (batch)
- ^ "Security in Information Systems - SIS 2002", Erwin Erasim, Dimitris Karagiannis (Ed.), ISBN 3-7281-2864-3 , Hochschulverlag AG, 2002, p. 88
- ↑ Microsoft's data protection officer testifies in the Sasser trial , Heise.de, July 6, 2005
- ↑ Jacob Appelbaum, Judith Horchert and Christian Stöcker: Shopping for Spy Gear Catalog Advertises NSA Toolbox , in: Der Spiegel , English-language online edition of December 29, 2013, accessed October 31, 2017
- ↑ BSI basic protection catalogs: Security gateway (firewall)
- ↑ BSI basic protection catalog: Appropriate selection of an application level gateway
- ↑ Claudia Eckert: "IT security - concepts, procedures, protocols", ISBN 978-3-486-58999-3 , 2009, Oldenbourg Wissenschaftsverlag, 6th edition, p. 730
- ↑ Bypass a firewall with the help of a DNS tunnel
- ↑ Jürgen Schmidt: The Hole Trick, How Skype & Co. bypass Firewalls In: c't 17/06, p. 142
- ↑ Methods for bypassing a firewall
- ↑ https://www.trendmicro.de/cloud-content/us/pdfs/business/datasheets/ds_tps_440t.pdf