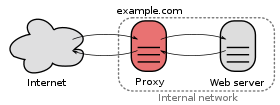
Proxy (computer network)
A proxy (from English proxy representative “representative”, from Latin proximus “the next”) is a communication interface in a network . He works as an intermediary who on the one hand accepts inquiries in order to then establish a connection to the other side via his own address.
If the proxy is used as a network component, on the one hand the actual address of a communication partner remains hidden from the other communication partner, which creates a certain anonymity. As a (possible) link between different networks, on the other hand, it can establish a connection between communication partners even if their addresses are incompatible with one another and a direct connection is not possible.
In contrast to simple address translation ( NAT ), a proxy server , also known as a dedicated proxy , can manage and influence the communication itself instead of passing the packets through unseen. Specialized in a particular communication protocol, such as B. HTTP or FTP , it can analyze the data coherently, filter requests and make any adjustments if necessary, but also decide whether and in what form the response of the target is passed on to the actual client . Sometimes it is used to temporarily store certain answers so that they can be retrieved more quickly for recurring requests without having to request them again from the target. Several dedicated proxies are often used in parallel on a single device in order to be able to operate different protocols.
A generic proxy , also known as a circuit level proxy , is used as a protocol-independent filter on a firewall . There it implements a port and address-based filter module, which also supports (possible) authentication for establishing a connection. In addition, it can be used for simple forwarding by listening on a port of a network adapter and passing the data on to another network adapter and port. He can neither see the communication nor conduct or influence it himself because he does not know the communication protocol.
Working method and demarcation
The difference to a NAT device
From a technical point of view, a typical proxy works as a communication partner intervening in the traffic on OSI layer 7, whereby the connections are terminated on both sides (there are therefore two independent connections) instead of simply passing the packets through like a NAT device. Such a dedicated proxy is a service program for computer networks that mediates data traffic and is therefore also called a proxy server : As an active mediator, it behaves like a server towards the requesting client and like a client towards the other side, the target system .
There are overlaps with NAT, however, with the generic Circuit Level Proxy operating on OSI layers 3 and 4 , which in certain circumstances makes use of the technology of simple address translation. Regardless of this, NAT plays a neglected role among proxies. Therefore, in the following, the first-described variant is assumed when a (typical) proxy is generally used.
overview
Visibilities
A conventional proxy acts as a communication partner for both sides. He is therefore consciously addressed (addressed) by them. Here the client asks the proxy to take over communication with the target system on its behalf. So z. B. the web browser is configured in such a way that it does not send all requests directly to the target address, but rather sends them to the proxy in form of a request.
In addition, there is the transparent proxy as a special network component that is transparent (almost invisible) to one of the two sides. This page addresses the target directly and not the proxy. With an appropriately configured network infrastructure, the relevant request is automatically routed there via the proxy without the sender noticing or even being able to influence it. For the other side, however, the proxy continues to represent the communication partner to be addressed, who is addressed on behalf of the actual communication partner.
Thus, a proxy generally appears as a supposed communication partner for at least one of the two sides.
location
A proxy as a separate network component is physically located between the source and target systems. Within an IP network, it converts the IP address as soon as the packets pass the proxy on their way to the destination. This means that the real IP address of the actual communication partner can be hidden and individual participants in a network or even entire networks can be connected to one another even if they are incompatible with one another in terms of addressing. The latter is made possible by a special port management system, which enables a proxy e.g. B. allows a private (self-contained) network to be connected to the Internet via a single official IP address. Since the target system does not see the client but only the proxy, possible attacks from there are directed at the proxy predestined for this and do not hit the client directly.
The local proxy , on the other hand, runs directly on the source or target system and is located in the logical arrangement between the network service to be contacted and the requesting client. It is mostly used as a filter or converter. Since it comes into action on site, i.e. before the packets are routed into the network (local proxy on the source system) or after the packets have reached the target system (local proxy on the target system), this proxy is not able to hide the real IP address of the communication system. This is what sets it apart from other proxies in an IP network. However, a local proxy on the source system can be of great help in automatically sending the network request via an external proxy, the local proxy then managing this type of redirection and thus contributing to the anonymization of its own IP address.
Possible functions of a proxy
- Protection of clients
- The proxy can form an interface between the private network and the public network. The clients of the private network access, for example, the web server of the public network via the proxy . Since the contacted target system from the public network does not send its response packets directly to the client, but sends it to the proxy, the proxy can actively control the connection. Unwanted remote access to the client (which goes beyond the response packets) is thus prevented or at least made more difficult. Appropriate security measures and their ongoing control are limited to a single or a few proxies instead of a large number of clients. They can also be implemented more easily and reliably in an upstream bastion network. In this way, your own servers are also better protected, which themselves do not require access to the Internet but are in the same segment as the clients shielded by the proxy. This means that the internal network remains initially protected even if the proxy is compromised, thus giving the IT department additional time for suitable reactions to any external attack.
- Protect the server
- A proxy server can generally be used to place the actual server in a protected network , so that it can only be reached from the external network through the proxy. In this way one tries to protect the server from attacks. The proxy software is less complex and therefore offers fewer points of attack. This solution is used, for example, in online shops : the web server and proxy are located on the Internet and access the database with customer data behind a firewall.
- Bandwidth control
- The proxy allocates different resources to different users and groups depending on the workload. The proxy server Squid masters this procedure, whereby it can also help protect the server and support methods for better availability.
- Availability
- Load distribution and availability can be achieved with relatively little effort via a proxy network .
- Preparation of data
- Proxy servers can also take over certain application functions, for example bring data into a standardized format.
- Content control of frequently used protocols
- A proxy specializing in a specific network protocol can analyze the packets of the respective protocol and act as a connection and command filter.
- Function expansion of a network service
- A reverse proxy can expand the usual range of functions of a service by, thanks to the analysis of the protocol, e.g. B. special statistics are created, which the service normally does not offer. Since he can answer queries himself, any further functional extensions are conceivable.
- Logging
- Many proxies allow connections that run through them to be logged. This enables statistical evaluations and the detection of unwanted connections.
- Open proxy
- As an open proxy or open proxy (English open proxy ) refers to a proxy that can be used by anyone without prior registration (open or public). On the one hand, they arise unknowingly through incorrect configuration or through Trojanized PCs (see also: botnet ), on the other hand, many open proxy servers are also set up on purpose to enable extensive anonymity - such as in the Freifunk network; such proxies are often provided with additional anonymization functions.
- Proxy as an anonymization service
- The anonymization proxy (e.g. anonymizer , Tor ) forwards the client's data to the server, which means that the server can no longer read the client's IP address directly (see also: Anonymity on the Internet ). They are used to disguise the origin of a client. Internet users can try to protect themselves from state or other persecution or control. In another scenario, proxies are offered - some of which are freely available - from which any website can be requested under the URL of the proxy. These proxies can be used, for example, to bypass the restrictions of company or school networks (although these are sometimes blocked if the operator notices it). They are anonymous in that the target server only sees the URL of the anonymization service.
- Access to blocked content
- Geo-blocking can be avoided by using a proxy server in another country .
- Translating proxy
- Some proxies translate one protocol into another. These are then called Gateway , Transport, Agent. For example, a Cern proxy communicates with the client via HTTP , while it connects to the server via FTP or Gopher . This concept is also based on XMPP transports .
The proxy as a network component
In order to understand how such a device can manage to hide the identity of the real communication partner, it can be helpful to imagine the proxy as an automated mailbox: a packet is sent through the proxy from the hidden (internal) address sent to the external network, the proxy connects itself to the target system and automatically assigns its own sender address to the outgoing packets.
The target system now sends its response packets back to the mailbox (proxy), which analyzes the received packets if necessary and then forwards them to the internal client. In this way, the proxy forwards all incoming reply packets from the external network to the actual recipient from the internal network without the sender knowing the actual (internal) address of the recipient.
The local proxy
Address conversion is also carried out internally with proxy software installed locally on the source or target system. This is part of their internal way of working and can be limited to redirecting the port, but often refers to a conversion to localhost (the so-called loopback interface 127.0.0.1).
On the source system
As an example, an application could no longer send its Internet requests directly to the target system, but to its own system to the port of the proxy software installed there. The application must be configured accordingly for this. The proxy software now determines the address of the desired target system and forwards the request there on behalf of the application. The address of the source system and the return port of the proxy software are specified as the sender so that the response packets reach the local proxy again, which can then pass them on to the original application. In this way, such a proxy can analyze (and, if necessary, filter) outgoing requests in the same way as the replies from the target system. Polipo is free proxy software for the Hypertext Transfer Protocol (HTTP) with caching and filter functionality , e.g. B. for the laptop or the netbook. Another example of a local proxy is Proxomitron , which, among other things, prevents JavaScripts from resolving the browser identity and its version number and from reading the operating system. The SpamPal spam filter is also installed with a local proxy, at least for certain mail clients such as Vivian Mail.
On the target system
The application on the source system sends its requests directly to the target system. Without the source system having to be aware of it, however, the coveted network service is not hidden behind the addressed port of the target system, but proxy software.
The proxy software thus accepts requests from the network and then establishes a connection to the actual network service of its own system on behalf of the source system. This answers the request and sends the answer back to the proxy software, which can now analyze it and change it as required or even evaluate it statistically before it forwards it to the actual client.
Proxy names
Dedicated proxy (proxy server)
A dedicated proxy is a service program that mediates the data traffic between the requesting client and the target system. It specializes in the communication protocol that the service uses and can therefore analyze the communication and, if necessary, manipulate its content. In addition, it can independently send requests to the communication partner and sometimes act as a buffer (i.e. respond to a request on its own without having to request it again from the actual target system).
Sometimes it is installed locally on the source or target system in order to carry out the corresponding task on site. In contrast, this can also be a filter module that actively intervenes in the communication and is placed on a proxy firewall . Among other things, dedicated proxies are used as (e.g. SMTP ) virus scanners or (e.g. FTP ) connection and command filters.
Several dedicated proxies can run in parallel on a single device in order to serve different protocols. Since he has to look into the packets, a dedicated proxy does its work on OSI layer 7.
Dedicated proxies are often used for the following protocols:
- HTTP / HTTPS
- Most providers offer their customers the use of such a proxy. It can fulfill the following functions:
- SSL termination
- An HTTPS connection can be broken (terminated) using a web proxy in order to also check its content for malware. Further encryption to the client (browser) then takes place with a certificate offered by the proxy. The problem here is that the browser user no longer gets to see the original certificate of the web server and has to trust the proxy server that it has taken over a validity check of the web server certificate.
- Temporary storage ( cache )
- The proxy can save queries or their results. If the same request is made again, it can be answered from the memory without first asking the web server . The proxy ensures that the information it delivers is not too out of date. Complete topicality is usually not guaranteed. Caching means that queries can be answered more quickly and the network load is reduced at the same time . For example, such a proxy for a company mediates all data traffic from employees' computers to the Internet .
- Censorship / Access Control
- Using a proxy, certain websites can be blocked for the user or access to them can be logged. The content can also be searched for harmful programs ( viruses , malware , scripts, etc.). A proxy is therefore usually part of a firewall concept. In this way, schools or public institutions in particular, but also companies, prevent access from their network to any website in order, for example, to prevent the downloading of music files because of the associated legal problems. In addition, those under protection can be protected from websites that are dangerous to them (pornography, racist websites or the like). User authentication can also be used to assign different web filters to individual users or user groups.
- Filtering out advertisements
- Advertising can generate significant amounts of data traffic - many advertising spaces are loaded, for example. B. regularly new. What is unproblematic for private users on a broadband line can, for example, become a problem for a network of several dozen users on this line.
- SMTP
- Some firewalls offer an SMTP proxy that monitors the mail traffic between the Internet and the mail server and filters out certain dangerous or undesired commands. The design of the SMTP protocol means that every SMTP server can also be used as an SMTP proxy.
- IMAP proxy
- Holt z. B. automatically e-mails from the central IMAP server to a local machine, from which the clients then pick up the e-mail.
- IRC proxy
- Such a proxy mediates IRC connections and can maintain them even if the client is switched off.
- NNTP proxy
- The proxy (e.g. Leafnode) can be used for news and allows e.g. B. Define filters for undesired groups.
- Exchange front-end server
- It provides a proxy function that tunnels the RPC protocol over HTTP (S) .
- Citrix Secure Gateway
- Here the ICA protocol is tunneled over HTTP (S).
Circuit Level Proxy (Generic Proxy)
A circuit level proxy (also known as generic proxy ) is a packet filter module that can be used to block or unblock any IP addresses and ports on a firewall, but without the possibility of analyzing the packet contents.
Such a proxy, which operates on OSI layers 3 and 4, sometimes simply passes the packets through without terminating the connections itself. The Circuit Level Proxy then implements the address translation using NAT on the OSI layer 3. While the address filtering is also located on the third OSI layer, it also implements port filtering on the fourth OSI layer.
There are also circuit level proxies that can implement authentication on OSI layer 5 thanks to a special protocol. The client gets such a connection authorization z. B. by entering an identifier and password. The client must know this special authentication protocol, which is why a Circuit Level Proxy enabled in this way is less generic (it only works with applications on the client that have been extended accordingly). SOCKS is an example of such an authentication protocol . Such an extended circuit level proxy does not necessarily use NAT. Some of them even make this dependent on the protocol; so z. B. the TCP connection is terminated, while a UDP connection is simply passed on.
A generic proxy can also be used for simple forwarding. The simplest possible proxy is the Linux program Redir , which listens on one interface and one port and forwards the data to another interface and port. This is also possible with the iptables command under Linux and is used, for example, to route the exit data traffic of a Tor server through several proxies in order to protect the Tor server.
Proxy firewall
A proxy firewall is a firewall that uses dedicated proxies or circuit level proxies as filter modules. These filter modules implement rules by deciding which data are forwarded to the actual communication partner and which are not. In this way, the proxy firewall tries to protect its own network (segment) from unauthorized access. It can also convert the data, buffer certain content and perform all other functions that are inherent in a proxy.
Dedicated proxies on a stateful inspection firewall
Some manufacturers also offer dedicated proxies for their Stateful Inspection Firewall (SIF) . In terms of definition, however, this is a little problematic: Since this type of firewall, according to the original Checkpoint concept, is only based on a generic packet filter and thus concentrates exclusively on packet filter rules, a SIF is clearly classified as a packet filter firewall . However, if a dedicated proxy is activated there, the SIF is actually no longer a packet filter firewall, but belongs to the proxy firewall category, which carries out a stateful packet inspection . This exact differentiation is rarely made by experts, which is why a firewall classified as SIF only partially meets the definition of a packet filter firewall in practice.
Transparent proxy
A transparent proxy basically consists of two components. First, the desired ports of the protocols are tapped on the router (for example via iptables using a redirect) and then forwarded to a proxy. For the user, the connection via a transparent proxy cannot be distinguished from a direct connection via the router. The presence of a transparent proxy has the advantage that the proxy settings on the individual PC cannot be configured (see section Visibilities ).
Reverse proxy
In the case of the reverse proxy, a proxy appears as an alleged target system, the address translation then being carried out in the opposite direction and the true address of the target system thus remaining hidden from the client. While a typical proxy can be used to grant multiple clients of an internal (private - self-contained) network access to an external network, a reverse proxy works exactly the other way around.
Direct the internet access of the browser via a proxy
There are several options for directing browser access through a proxy:
- Environment variable
- Some browsers, for example Lynx , evaluate an environment variable (in this case 'http_proxy =') and use the value entered there if it is not empty.
- Direct configuration
- The name (or the IP address) of the proxy server and the port on which it listens are entered directly in the browser. The disadvantage is that you have to do this manually for each client and that changes have to be made on each client individually.
- Transparent proxy
- Nothing is configured here on the clients; they direct their requests to the destination on ports 80 (HTTP) as if they had a direct connection to the internet. The network's infrastructure ensures that your requests are directed to the proxy.
- Automatic proxy configuration ( Proxy Auto-Config )
- The URL of a JavaScript file containing the address and port of the proxy server is entered here in the browser. If this work has been done once, further changes can be made centrally in the script. The script can also assign to a reverse proxy.
- Web Proxy Autodiscovery Protocol (WPAD)
- This is a protocol with which web clients, like a browser, can automatically find web proxies to be used within a computer network by saving a Proxy Auto-Config (PAC file) under a guessable URL, for example:
http://wpad.example.com/wpad.dat
Possible problems using a proxy
hazards
A poorly configured proxy can be dangerous as it allows third parties to act on the Internet via the proxy address. As an example, the proxy could be misused for an attack or - similar to an open mail relay - to send spam . In the event of misuse, the proxy is then determined as the source, which under certain circumstances can have unpleasant consequences for the operator.
Statistics for accesses
Commercial servers in particular, which rent out advertising space, justify their attractiveness for advertising with access numbers whose statistics are generated by the web server. Of course, proxy servers and filters have a negative impact on these numbers, since the content delivered from the cache does not appear there and some of the advertising is not even loaded. Some providers of websites therefore try to make their content poorly or not at all cache-capable.
Proxy log files can be evaluated on a user-specific basis. Statistics about users (or IP addresses), the websites they visit and the time they spend on the websites can be compiled.
Proxy as an anonymization service
In various Internet forums , including Wikipedia, the creation or modification of articles via open proxy servers is often prevented by blocking the relevant IP addresses in order to make anonymous participation more difficult. It makes sense to do this only for users who are not logged in.
It should be noted that the operator of an open proxy has almost full control over the session, recording data and falsifying any web content without the user noticing.
In order to limit the risk of the anonymization service being misused by the proxy operator, concepts such as F2F could offer a solution: With an F2F proxy, the data is passed through a “friend”; this increases security as no unknown proxy servers are used. The friend-to-friend network guarantees that only private and verified connections are used. Common encryption and certification methods such as SSL / TLS with the target system behind the proxy, for example by using an HTTPS connection, can also provide a remedy . In this case, the proxy cannot perform any manipulation, at least as long as the implementation of the method used is not defective and the method itself is not undermined.
Web links
- Link catalog on the topic of proxy software and scripts at curlie.org (formerly DMOZ )
- Link catalog on the subject of Free web-based proxy services at curlie.org (formerly DMOZ )
- Link catalog on the subject of Free http proxy servers at curlie.org (formerly DMOZ )
- Set up proxy under Chrome, Internet Explorer, Android and iOS
Individual evidence
- ↑ On May 13th, 2008 the Debian project announced that the OpenSSL package of the distributions since September 17th, 2006 (version 0.9.8c-1 to 0.9.8g-9) contained a security hole.
- Jump up ↑ SSL protection , Felix von Leitner , May 23, 2008.
- ↑ Methods for obtaining information , Felix von Leitner , January 15, 2010.