Anonymity on the internet
The internet enables different levels of anonymity . This is limited, for example, by the fact that an IP address is also transmitted with every communication on the Internet . Internet users also leave traces through careless behavior, and a lot of information about them can be gathered with technical tricks.
The use of nicknames allows pseudonymity on the Internet .
In Germany, service providers of telemedia are obliged in accordance with Section 13 VI TMG to enable their services to be used anonymously or under a pseudonym, provided this is technically possible and reasonable. However, at the beginning of 2020, a Federal Council initiative by the Lower Saxony government required a clear name to be compulsory through mandatory registration on the Internet platform used.
Identification by the IP address
The IP address enables the lowest level of identification. It identifies every participant on the Internet, mostly individual computers. Identification takes place via the IANA entry for the internet access provider and this can be used to identify the internet connection owner with the IP address sought. The access provider can be legally compelled to assign an IP address to a participant in his address range. This can be used to find the sender of the information transmitted over the Internet, unless special countermeasures have been taken.
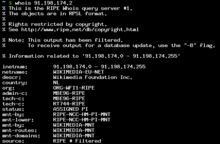
Each IP address is registered to an owner, who can also be queried at any time via the Whois service. Most IP addresses are Internet service providers ( English provider internet service , ISP ) associated with rare fixed IP numbers owners. In order to assign individual addresses to a subscriber, the provider must be asked. Since the providers allocate their address ranges according to regions, the approximate location of the subscriber using the IP address and the corresponding assignment tables is possible. However, this does not apply equally to cellular networks. When dynamic address assignment was introduced due to the scarcity of IPv4 addresses, which assigns a new address to the connections each time a connection is established, the privacy of the connection owner was strengthened as a side effect, since other Internet users could no longer reliably assign IP addresses to the same participants. Another method is "splitting" via so-called ports , with which the same IP address can be assigned to several users.
In Germany, a record of the assignment between the IP address and the subscriber was only required with the "Law on the New Regulation of Telecommunications Monitoring and Other Covert Investigative Measures and Implementation of Directive 2006/24 / EC ", whereby the new identification rules in the Telecommunications Act are an accessory and not an implementation of the EU directive. In Germany, before the German implementation of data retention, it was a decision by the Internet access provider to save the assignment or not. The storage was practiced by Deutsche Telekom , but mostly not by smaller providers. In an individual case with a DSL flat rate between Holger Voss and T-Online, the Internet access provider was even forbidden from saving the assignment by the Federal Court of Justice, because with a flat rate it was not necessary to save the connection data for operational purposes.
On March 2, 2010, the Federal Constitutional Court laid down some framework conditions for this. The assignment query is only permitted for “limiting criminal offenses or catalogs of legal interests”, “for the prosecution of criminal offenses, for hazard prevention and the performance of the tasks of the intelligence services on the basis of general legal intervention authorizations”. The query may also only be made on the basis of an “initial suspicion or a specific danger based on individual facts”. A judge's reservation is not necessary, but the person concerned must be notified. If the query is due to an administrative offense, this must be particularly important and explicitly listed by the legislature in the law.
In Germany, the competent authorities are permitted to request the data specified in Section 111 TKG (for example the address) from a connection identifier such as the IP address for the tasks specified in Section 113 TKG (for example, the prosecution of criminal offenses or administrative offenses). This restricts anonymity vis-à-vis the state, but not vis-à-vis other Internet users.
However, the Constitutional Court has complained that the provisions in the TKG do not sufficiently legitimize the identification of IP addresses. The quotation requirement was not observed, since the “assignment of dynamic IP addresses” constitutes an interference with Article 10 (1) of the Basic Law . It should also be clearly regulated whether it should be possible to identify “addresses that have their own weight”. For a transition period until June 30, 2013 at the latest, dynamic IP addresses should still be identifiable. Until then, the legislature is called upon to re-regulate the identifiability of IP addresses.
In order to determine the target person, the subscriber is usually not questioned in a court case, but ordered in the search and seizure order that all internet-enabled devices be taken. Above all, the browser cache, the cookies, the websites accessed, entered search terms and form data, but also other data from the file system, including data that has already been deleted, are evaluated. Target persons who have encrypted their hard drive have an advantage here, as the disclosure of a password must not be forced.
Examples in which the target person and the subscriber are not identical are Internet cafés, shared apartments and families, but also onion routers and open proxies . Since the introduction of data retention (like Internet access providers), operators of German anonymization services (e.g. proxies) have had to store the data already mentioned for their anonymized connection IDs and to provide the authorities mentioned with information about this data. This puts them on an equal footing with Internet access providers. In the case of shared apartments and families, on the other hand, which do not need to store data, the target person cannot always be determined.
The assignment of the IP address to the Internet connection owner is also made more difficult by the internationality. This is possible within the EU through cooperation, but not in all other countries. The authenticity of an IP packet from a specific IP address is currently not very secure either. The jurisprudence mostly assumes that the operators of an internet subnetwork do not manipulate data and route it correctly. Cryptological security such as IPsec is rarely given. In addition, other people can be identified at higher log levels . For example, a shared blog can indicate the authors of each article.
Measures to protect anonymity
Anonymizer
Anonymizers are used to hide your identity via another IP address while surfing. The most common and simplest variants are anonymizing proxy servers or virtual private networks (VPNs).
Operators of proxy may but log files create, represent the logs of IP address, time and transmitted data and publish them on request to competent bodies. In many countries, they would be obliged to do this within the framework of data retention . In Germany, the provisions on data retention have been unconstitutional and void since the judgment of the Federal Constitutional Court on March 2, 2010.
In order to be able to establish anonymity in spite of such recordings, certain utilities set up chains of proxies between which the traffic is encrypted. It is hoped that at least one of these proxies will not keep a record. This variant slows down the connections, but makes reconstructing the original transmitter practically impossible.
If several proxies are connected in a row that mix the packets of the incoming data streams, a mix network is created, such as JonDo .
Another technique is onion routing . An example of this is Tor , an anonymous overlay network for TCP developed by the Freehaven project . Connections based on TCP, such as web browsing, instant messaging, IRC, SSH, e-mail, P2P, can be anonymized. I2P uses garlic routing , which works in a similar way . Apart from "out proxies", the data traffic never leaves the I2P network, which is why all messages there are end-to-end encrypted. This enables anonymous surfing of anonymously hosted websites within the network, anonymous IRC, anonymous instant messaging , anonymous file sharing and anonymous e-mails. All connections based on TCP or UDP are supported within the network.
The Independent State Center for Data Protection Schleswig-Holstein (ULD) is driving further, in some cases even international, projects that enable security and data protection on the Internet . For example, when surfing the net, P3P can use data protection technology to identify which personal data is processed when you visit a website. Research is also carried out on anonymity and pseudonymity.
To send anonymous e-mails and anonymous posts for Usenet forums, so-called remailers are used, which work similar to an anonymizer . These servers react to e-mail in a similar way to an HTTP proxy to requests for web content: the message is forwarded by the remailer so that it acts as the sender itself. The servers currently found on the Internet use either the Cypherpunk or the Mixmaster protocol. While the former defines a pure forwarding service that must be additionally secured by encryption systems, Mixmasters only accept encrypted emails in a very specific format. Hybrid remailers are a hybrid of the two types of remailers . But I2P also offers the option of sending anonymous e-mails using mail programs or a browser.
Anonymous file sharing
Anonymous file sharing programs offer the possibility of anonymously exchanging data over the Internet. In most anonymous peer-to-peer networks, anonymity is achieved in that the data to be exchanged is encrypted and the "exchanging" clients do not maintain a direct IP connection to one another, but rather the data are stored using "IDs" via proxies (e.g. other clients) to the recipient. Anonymous file sharing programs are, for example, I2P (with i2psnark, iMule, I2Phex), Freenet or GNUnet .
Use of friend-to-friend networks
In friend-to-friend networks (F2F), connections are only maintained with verified and trusted friends. This contributes enormously to anonymity on the Internet. The peculiarity of F2F compared to Darknets is that friends do not know the IP addresses of the friend friends. Only the trusted friends themselves know each other's IP addresses. This makes it possible to forward a file from Alice via Bob to Carol, although Alice and Carol do not know each other's IP address. The best known friend-to-friend networks include RetroShare and GNUnet .
Friend-to-friend networks, in addition to the use of offshore anonymization servers, are the best way to establish anonymity and free communication despite a wide range of Internet monitoring instruments. The prerequisite for this, however, is that encrypted information can be transmitted. So far, no friend-to-friend networks have been developed that circumvent this prohibition through steganography in totalitarian states that forbid any encryption . However, it is planned for the use of Tor in China, for example, that HTML pages transmitted via HTTP can serve as a tunnel for the door data. Another very complex and comprehensive way of securing Internet monitoring can be provided by software installed on the computer to be monitored, which can discover, report and block the use of friend-to-friend networks. The Open Net Initiative reported that in China, for example, “Green Dam”, a censorship software that would have to be installed directly on the computer, was planned.
Offshore anonymization services
Internet offers that enable anonymous communication can be set up on so-called “offshore servers”, which are located in the Bahamas, Belize, Malaysia or Panama, for example.
Special Usenet providers
Another option for “anonymous” publishing, downloading or exchanging data on the Internet is offered by so-called Usenet providers. Access to the data is provided via the Usenet server of the provider who offers the “news groups”. The provider knows the identity of its users through payment information and IP address. If one of their customers would like to publish data on Usenet, some providers do this by specifying the provider's email address instead of the customer, so that the customer remains anonymous. The retrieval of information is just as anonymous as the retrieval of a website, since only the provider in question is aware of it. The person who published the data on Usenet does not know who is accessing their data. The provider is thus a proxy that must be trusted just like a web proxy.
Anonymous SIM card
Some telecommunications providers offer SIM cards that do not require identity verification or that do not verify false information. Anonymous mobile internet use is then also possible via this. The dial-up device is assigned an IP address by the mobile network operator for the Internet session, via which the device can be traced. For technical reasons alone, the mobile network operator has to know the mobile network cell used by every device logged into the mobile network and can thus limit and log the position of the dial-in device. However, the device can also be precisely located, which can be accurate to a few meters depending on the measurement method used and the environment (see GSM positioning ). It should also be noted that exchanging the SIM card does not change the serial number IMEI of the dial-up device. This is usually unique and is transmitted when dialing into the mobile network. If the required data is available, the mobile network operator has the option of determining all SIM cards that were used by the same dial-in device. The identity of the user can then be inferred from the data linked to the SIM cards.
ID has been required when purchasing a SIM card since July 2017.
Internet café and WiFi access points
The use of an Internet café or open or poorly secured WLAN access points also offers the possibility of anonymous Internet access, provided that no identity check is carried out by the system or operator. The IP address of an internet café or an access point can be resolved to a subscriber just like any other IP address. If the user transmits personal data unencrypted, they can be saved and used later for de-anonymization. In the Internet café, the transmission of encrypted data is also not secure, as the operator through z. B. installed monitoring software can see and record the screen and all activities on the computer. In WLANs it is possible for the operator as well as attackers within range or in the network to record and manipulate unencrypted data traffic between the access point and the device. Every active WLAN user can also be located within range. According to the last decision of the Wuppertal District Court, anyone who uses an open, third-party WLAN without authorization does not commit a crime under any legal aspect.
Techniques for identifying users on the web
In addition to using the IP address, there are other ways to track surfers on the World Wide Web and thus also to save data about them.
Wiretapping
Internet providers, proxy operators, company or university network operators and Tor exit nodes can eavesdrop on the unencrypted data traffic . Under certain circumstances, this data can be used to infer the identity of the user. Internet users can avoid this by choosing a trustworthy provider or by using encryption.
Tracking cookies
Tracking cookies are a common means of “marking” a website visitor in order to be able to recognize him later. Normal cookies are used, for example, in practically all Internet offers where the visitor has to log in with a user name and password in order to be able to identify a user for a session. Shopping baskets in online shops are also mostly implemented with cookies. However, tracking cookies are also used to monitor the surfing behavior of a user over a longer period of time, even without the user explicitly logging in, and across multiple websites. With Collusion , this tracking can be graphically displayed. Controversial programs like Ghostery display these trackers and block them if desired.
From a technical point of view, cookies are small blocks of text that the server sends to the browser and later gets back and can use. On the first visit, the user receives a cookie with a unique identification number, and the server can recognize the visitor on each subsequent page view. Cookies are either stored permanently or for a specified period of time. On the server, they usually consist of the IP address of the user and a time, while the server address is saved by the browser for the user. The cookies cannot contain any executable commands and therefore do not initially pose a security risk.
Operators of different websites can work together to track a visitor across different pages. If a user logs on to a website B and then calls up a website A in which a web address ( URL ) of website B is embedded, website B can access the cookies that contain the login data and then transfer them to website A. to transfer. Such an embedding of a web address could, for example, be an advertising banner or a counter graphic. Whether or not page B can access the browser's cookies when it is embedded from another website depends on the browser configuration.
A website A can also request information from a website B through a specifically set exception for the same-origin policy .
Directive 2009/136 / EC , which was issued on November 25, 2009 and is also known as the Cookie Directive , regulates the use and storage of cookies in addition to Directive 2002/58 / EC - E-Privacy. However, it has not yet been implemented by many European countries or the authorities deliberately do not pursue violations.
Virtual fingerprint (profile)
DNS profile
All calls to websites using a domain name result in a DNS request which determines the IP address of the requested server. By combining the IP address of the requesting client with the DNS requests, the DNS server can create profiles for the websites accessed. However, the profiles are only rough because the DNS server does not receive the path of the web address, and due to DNS caching , not every new call to the same domain causes a DNS request.
The DNS server can also censor websites by not breaking down certain domains into IP addresses; these are then not available. Anonymous, uncensored DNS name resolution is an important prerequisite for effective anonymization and against censorship. Anonymous name resolution means using an anonymous, uncensored DNS server to reach the desired web address. If the client does not use a preconfigured DNS server, it is usually assigned automatically via DHCP .
Browser profile
Many so-called HTTP - headers provide information about the used browser type, the operating system ( user agent ), previously visited website ( referrer ) and the called when leaving the page next website. The server only needs to evaluate the data contained in the call.
Extensive (secretly loaded) scripts program browsers to send data for identification. Usually JavaScript code requested as much information as possible from the browser before the IndexedDB interface 2009 and sent it to the server. Even before that, z. B. about the screen resolution used, color depth, installed plugins, etc. users can be found out and tracked .
The EFF has been collecting anonymized data with the Panopticlick application since 2010 in order to assess how easily the surfer can be recognized in the crowd. The service does not need cookies, which can expire or be deactivated, or IP addresses which can change. It evaluates the HTTP request headers, which consist of browser identification and accepted MIME types, and, using JavaScript, information about installed plug-ins, fonts, screen size and time zone. In addition, data about standard and “ super cookies ” ( Flash cookies, web storage , IE user data) are included in the ranking. In many cases, this enables a unique virtual fingerprint to be created. The information content of this fingerprint can be reduced by various measures, but these measures are usually not ideal because they limit convenience, such as switching off JavaScript.
Deleting cookies immediately (or at least regularly) has been a recommendation for the last millennium. If standard and "supercookies" are combined, one speaks of so-called "evercookies", which enable a profile to be created and which are difficult for the user to remove.
This is why users of Mozilla Firefox , for example, are demanding that both the HTTP fingerprint and the JavaScript fingerprint be reduced.
System compromise
The user can be de-anonymized if unauthorized persons can gain access to his system or to other systems that have his data. This can take place, for example, through infiltrated malware or through the use of security holes and back doors in the system. These can then be used to record and transmit all user activities and data from all available sources. These sources can include all accessible media, webcams and microphones. Authorities can compromise suspects' systems in order to monitor them as part of an online search . Measures against compromise are assigned to the area of information security .
Effects of anonymized internet use
Benefits of disclosing personal information
Online anonymity is a politically controversial issue as it has both advantages and disadvantages. There are a number of use cases in which the disclosure of personal data has a positive effect on internet usage.
The following should be mentioned here:
- Personalized advertising reduces the number of advertisements with little or no reference to the Internet user. The selection of advertising messages is then based on the evaluation of the customer profile. Instead of random content, providers now present offers that ideally offer a direct relationship with the user.
- By transmitting the location of a user ( geotargeting ) z. B. regional services are offered or online directions are given.
- Releasing personal data increases the accountability of actions on the web. This increases trust between business partners and enables sales contracts to be processed.
- In the online mail order business, shipping is only made possible by giving your name and address.
- Authors can not enforce their copyright if the copyright infringer is anonymous. Also, data breaches can not be cleared up for anonymous perpetrators.
- Law enforcement authorities have difficulties with the investigation if such anonymization services are used in criminal offenses that take place on the Internet. Therefore, a restriction or a ban on such services is required on their part. Opponents of this demand, such as B. Security expert Bruce Schneier , argue that because of the way the Internet works, tech-savvy criminals will always find a way to remain anonymous. It can never be clearly determined which person is responsible for a particular data packet. B. other computers can be used or misused as proxy servers .
Advantages of anonymized internet use
On the other hand, personality profiles can contain intimate data about the Internet user, which offer a wide range of opportunities for abuse. The user wants to keep information such as social contacts, political attitudes, personal worldview, information about financial problems or even information about health problems as confidential as possible.
But his research on the Internet can reveal him. Without the possible anonymity measures, such as B. changing IP addresses or expiring cookies , this data can easily be collected about each user.
Especially in e-commerce there are business areas in which the user benefits from his anonymity on the Internet. In contrast to retail, interaction on the Internet does not take place with a real person, but with a goods system. The user is therefore not forced to give another person an insight into his private area, but rather interacts with an electronic system. This factor has a positive effect on the following business areas, for example:
- Distribution of adult articles and internet pornography
- Internet sales of medicines and prescriptions
- Advice portals for personal problems (e.g. eating disorders)
- Advice portals for medical problems
A significant advantage of anonymized Internet use is the bypassing of content blocks and the guarantee of freedom of expression, see also the article Censorship on the Internet .
Legal policy
In Germany, the responsible minister, Christine Lambrecht, rejects the introduction of real names .
See also
- Real name compulsory
- Data protection on the Internet
- Cyber crime
- Provider privilege
- Self data protection
- confidentiality
literature
- Thomas Demuth : A contribution to anonymity in communication networks. Shaker 2003, ISBN 3-8322-1650-2 .
- Helmut Bäumler , Albert von Mutius (Ed.): Anonymity on the Internet. Vieweg 2003, ISBN 3-528-05850-1 .
- Martin Rost : On the social function of anonymity. In: Data protection and data security . (DuD) 2003, No. 27, pp. 156–158, maroki.de (PDF; 43 kB)
- Thomas Roessler: Anonymity on the Internet. In: Data protection and data security. (DuD) 1998, pp. 619-622.
- Henry Krasemann: Anonymity very simple and legal ( Memento from July 24, 2013 in the Internet Archive ) In: Datenschutz Nachrichten. DANA 3/2005 (September 2005) p. 13ff.
- Henry Krasemann: The anonymous apple: With the Mac unobserved into the Internet. In: Mac Life. 8/2005. Anonymity and Mac ( Memento from July 24, 2013 in the Internet Archive )
- Marc Störing: In the sights of the law enforcement officers - State access to anonymization servers . In: c't . 24/2006, pp. 208-210.
- Eric J. Stieglitz: Anonymity on the Internet: How Does It Work, Who Needs It, and What Are Its Policy Implications? (PDF; 136 kB) In: Cardozo Arts & Entertainment Law Journal. 2007, Volume 24, Issue 3.
- Jens Kubieziel: Anonymous online: How to protect yourself and your data. 3. Edition. Open Source Press, Munich 2012, ISBN 978-3-941841-67-3 .
- Phillip Brunst: Anonymity on the Internet - Legal and Factual Framework . Duncker & Humblot, Berlin 2009, ISBN 978-3-86113-854-9 .
- Martin Molle: Nothing except expenses? CyberGhost VPN blog entry from May 27, 2011 about data seizure.
- Ingrid Brodnig : The invisible person. How anonymity on the Internet is changing our society. Czernin, Vienna 2013, ISBN 978-3-7076-0483-2 .
- Kevin D. Mitnick : The Art of Anonymity on the Internet: How to Protect Your Identity and Your Data mitp-Verlag , Frechen / New York 2018, ISBN 978-3-9584-5635-8 .
Web links
- The end of anonymity? Data traces in modern networks ( Memento from September 7, 2015 in the Internet Archive ) Study by the German Federal Office for Information Security (Status: 2001)
- Web Tracking Report 2014 Fraunhofer Institute for Secure Information Technology SIT Markus Schneider, Matthias Enzmann, Martin Stopczynski, ed. Michael Waidner Fraunhofer Verlag PDF 118 pages ISBN 978-3-8396-0700-8 Accessed February 23, 2014
Individual evidence
- ↑ § 13 TMG - single standard. Retrieved June 22, 2019 .
- ↑ Debate about mandatory real names: What social media and SIM cards could soon have in common . In: FAZ.NET . ISSN 0174-4909 ( faz.net [accessed February 13, 2020]).
- ↑ heise online: BGH confirms judgment on the deletion of IP addresses
- ↑ Federal Constitutional Court: Concrete design of data retention not constitutional
- ↑ § 111 TKG: "Anyone who provides telecommunication services on a business basis or participates in them and assigns phone numbers or other connection IDs or provides telecommunication connections for call numbers or other connection IDs assigned by others, has the phone numbers and other connection IDs for the information procedure according to §§ 112 and 113 1. , 2. the name and address of the subscriber, 3. their date of birth for natural persons, 4. for landline connections also the address of the connection, 5. in cases in which a mobile phone terminal is provided in addition to a mobile phone connection, the device number of this device and 6. to collect the date of the start of the contract before activation and to save it immediately, even if this data is not required for operational purposes; "
- ↑ § 113 TKG, 1st paragraph: "Anyone who provides telecommunication services on a business basis or participates in them must in individual cases immediately provide the competent authorities with information about the data collected according to §§ 95 and 111 on request, insofar as this is for the prosecution of criminal offenses or administrative offenses, to avert threats to public safety or order or for the fulfillment of the statutory tasks of the constitutional protection authorities of the federal and state governments, the Federal Intelligence Service or the military counterintelligence. "
-
↑ Press release No. 13/2012 of February 24, 2012. bundesverfassungsgericht.de, accessed on April 29, 2012 .
“In the interpretation of § 113 TKG, it is common but controversial practice that information about the owner of a so-called dynamic Internet protocol address (dynamic IP address) is also given. These are the telecommunications numbers that private individuals in particular normally use to surf the Internet. ”
“ In addition, Section 113 (1) sentence 1 TKG does not authorize the assignment of dynamic IP addresses. For a transitional period, up to June 30, 2013 at the latest, the provision may be applied regardless of these provisions. ”
“ The storage and provision of information arranged in Sections 111 to 113 TKG only relates to the abstract assignment of telecommunications numbers to certain subscribers, which also how the assignment of a static IP address to a user does not fall within the scope of protection of Art. 10 GG. ”
“ On the other hand, the provision may not be used to assign dynamic IP addresses. This is forbidden because the assignment of dynamic IP addresses is to be qualified as an encroachment on Article 10 (1) of the Basic Law. For such encroachments, the quotation requirement applies in accordance with Article 19, Paragraph 1, Sentence 2 of the Basic Law, according to which the legislature must state the fundamental right that is encroached upon, stating the article. This is missing here. Incidentally, Section 113 (1) TKG does not regulate with sufficient clarity whether it is also intended to allow the identification of such addresses, which have their own weight. ”
“ For the same reasons, a transitional regulation is also required with regard to the constitutional requirements for the Interpretation of section 113 (1) sentence 1 TKG. If these requirements were to take effect immediately, information on telecommunication numbers would not be possible in numerous cases and no dynamic IP addresses could be identified until new retrieval regulations of the specialist law were issued. "
- ↑ heise online: Karlsruhe limits the use of telecommunications data (February 24, 2012)
- ↑ the JAP project of the TU Dresden enables anonymous surfing on the Internet
- ↑ China's Green Dam: The Implications of Government Control Encroaching on the Home PC
- ↑ heise online: No more anonymous SIM cards: Federal Council confirms new anti-terror package. In: heise online. Retrieved July 8, 2016 .
- ↑ "Black surfing" in unencrypted operated foreign WLAN radio networks is not a criminal offense - District Court Wuppertal, decision of October 19, 2010, 25 Qs 177/10, free-urteile.de
- ↑ EU cookie directive: A biscuit causes a stir
- ↑ Soft biscuit: British Cookie Eulenspiegeleien
- ↑ Almost entire EU now violating Brussels cookie privacy law
- ↑ Panopticlick page of the EFF
- ↑ Is it possible to defend against browser fingerprinting? (No longer available online.) Panopticlick.eff.org, archived from the original on July 26, 2011 ; Retrieved on July 24, 2011 (English): "Browser fingerprinting is quite a powerful method of tracking users around the Internet. There are some defensive measures that can be taken with existing browsers, but none of them are ideal. "
- ↑ Bug 572650 “(http-fingerprint) Reduce the amount of data and entropy sent out in HTTP requests” - “(HTTP fingerprint) Reduce the amount of data and entropy that is sent in HTTP requests”.
- ↑ Consider standardizing / normalizing navigator.plugins (browser fingerprinting)
- ^ Schneier on Security: Anonymity and the Internet
- ↑ Christian Rath, "Not only Sunday speeches " LTO of October 10, 2019
