Computer virus
A computer virus ( Latin virus 'poison, slime'; plural viruses ) is a self-propagating computer program that infiltrates into other computer programs, a boot sector or the RAM, and thus reproduces itself. The classification as a virus refers to the spreading and infection function.
Once started, it can make changes to the operating system or other software (damaging function), and indirectly damage the hardware . A typical effect is data loss. Computer viruses affect computer security and are classified as malware .
The term computer virus is also used colloquially for computer worms and Trojan horses , as there are often mixed forms and users can hardly tell the difference.
Working method
Like its biological role model, a computer virus uses the resources of its host computer and often harms it in the process. It also usually multiplies in an uncontrolled manner. Through malicious functions built into the virus author or through errors in the virus, the virus can affect the host system or its programs in various ways, from harmless malfunctions or loss of data to hardware damage.
Viruses are often embedded in a host program. If this host program is called, the virus is executed and can continue to spread.
Nowadays, computer viruses have been almost completely displaced by worms, since almost every computer is connected to the Internet or local networks and the active spreading strategy of the worms enables them to spread more widely in less time. Viruses are only important in new niches ( see below ).
Difference Between Virus and Worm
Computer viruses and worms both spread on computer systems, but they are based in part on completely different concepts and techniques.
A virus spreads by copying itself into uninfected files and adapting them so that the virus is executed when the host program is started. Files that can be infected include normal program files, program libraries , scripts , documents with macros or other executable content, and boot sectors (even if the latter are not normally represented as a file by the operating system).
Spreading to new systems occurs by a user copying an infected host file to the new system. It does not matter in which way these host file is copied: Formerly, the main distribution channels removable media such as floppy disks , today there are (sent as e-mail, of Computer Networks FTP servers, Web servers, or from sharing downloaded). Viruses also exist that infect files in shared folders in local networks if they have the appropriate rights.
In contrast to viruses, worms do not wait passively to be spread by a user on a new system, but rather try to actively invade new systems. To do this, they take advantage of security problems on the target system, such as:
- Network services that use standard passwords or no password at all,
- Design and programming errors in network services,
- Design and programming errors in user programs that use network services (e.g. e-mail clients).
A worm can then insert itself into another program file like a virus; however, it usually tries to hide itself in an inconspicuous place in the system with an inconspicuous name and changes the target system so that the worm is called when the system is started (such as the autostart function in Windows systems).
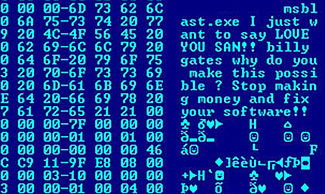
In everyday language, computer worms like " I Love You " are often referred to as viruses, as the difference is often not apparent to the user.
Degree of risk of different operating systems
The operating system used has a major influence on the probability of a virus infection or how high the probability of a system-wide infection is. Basically, all operating systems that allow one program to manipulate another file are vulnerable. Whether security systems such as user rights systems exist and are used affects the extent to which a virus can spread on a system.
Operating systems without any rights systems such as MS-DOS , MS-DOS based Windows or Amiga systems are the most vulnerable systems. If the user works exclusively as an administrator and thus cannot intervene in the rights system of the operating system, newer Windows versions, Unix and Unix systems such as Linux and macOS are just as susceptible.
In particular with Windows NT and systems based on it, such as Windows 2000 or XP, there is the problem that although a good user rights system is available, this is not used in the standard setting to restrict the rights of the user. One reason for this is that after the installation of some Windows versions, the automatically set up user accounts have administrator rights. This is different from Windows Vista, however, where setting up a standard account does not have full administrator rights, and the system is also protected with the help of User Account Control (UAC). Most Linux distributions set up a user account without administrative rights during installation, so that during normal use of the computer only limited rights are initially available and only the special root account has administrator rights.
If a user works with a user account with restricted rights, a virus can only spread to files for which the user has the appropriate rights to modify. This usually means that system files cannot be infected by the virus as long as the administrator or system services with administrator rights do not access files belonging to the infected user. Users who may be working on the same system can usually not be infected either, as long as they do not execute an infected file belonging to the infected user or the rights of the infected user allow other users to change files.
Because Windows systems have the most prevalence on PCs today, they are currently the primary target of virus writers. The fact that a large number of Windows users work with accounts that have administrator rights, as well as the ignorance of security practices among the relatively high number of inexperienced private users, make Windows systems even more worthwhile as a target for virus authors.
While over hundreds of thousands of viruses are known for Windows systems, the number of known viruses for Linux and the classic Mac OS is significantly lower. In the "wild", however, far fewer different viruses are observed than are theoretically known. The first virus for Apple's Mac OS X operating system was published on February 13, 2006 in the forum of a US rumor site. Until then, the Macintosh operating system was considered to be completely free from viruses and worms. The manufacturer of Windows antivirus programs, Sophos , publicly states in its Security Report 2006 that Mac OS X is more secure than Windows.
With Unix and Linux systems, the high security standards and the low prevalence of these systems among end users also ensure that they are currently not a worthwhile target for virus authors and that viruses practically do not occur “in the wild”. The situation is different with computer worms. Unix or Linux systems are meanwhile a frequent target of worm authors because of the high market shares in Internet servers.
General prevention
General prevention for all operating systems
Users should never run unknown files or programs from unsafe sources and should generally exercise caution when opening files. This is especially true for files that were received by email. Such files - including documents that appear harmless such as images or PDF documents - can activate malware in various ways through security gaps in the associated applications. We therefore recommend checking them with an up-to-date anti-virus program.
The operating system and applications should be updated regularly and service packs and patches / hotfixes provided by the manufacturer should be installed. Please note that it can take some time for patches to be deployed. Some operating systems simplify this procedure by supporting the automatic download and installation of updates . Some even support the targeted download and installation of only those updates that fix security-critical problems. There is also the option of installing the service packs and hotfixes for Windows 2000 and Windows XP via "offline updates". These offline updates are particularly recommended for new PCs, as otherwise the PC could be infected the first time it is connected to the Internet.
The built-in protective functions of the operating system should be used. This includes, in particular, not working as an administrator with all rights, but as a user with restricted rights, as he is not allowed to install any software system-wide.
The automatic opening of files from the Internet and the automatic hiding of known file attachments should be deactivated in order not to accidentally execute files that would otherwise be recognized as disguised malware. Thanks to the auto-start function for CD-ROMs and DVD -ROMs , programs can be executed as soon as such a data carrier is inserted , thus infecting a system.
Computer viruses also exist for non-Microsoft operating systems such as Symbian OS , Linux , Mac OS and operating systems of the BSD series. However, since these viruses are rarely distributed, they do not pose a major threat to the user. One reason for this is, on the one hand, the lower prevalence of these platforms (their spread was around five percent at the beginning of 2009), so that virus developers have spared these systems in the past and on the other hand it presents a considerable difficulty for the malicious programs to find further infection victims. Another technical reason is the explicit separation of rights in many other operating systems. In the case of open source operating systems, there is also the fact that there are many different distributions, which in turn is a restriction for viruses.
Personal firewall
Personal firewalls are not effective against viruses because their functionality is tailored to the way worms work and does not affect viruses.
Antivirus software
Antivirus programs essentially only protect against known viruses. Therefore, when using such a program, it is important to regularly import the updated virus signatures provided by the manufacturers . Next generation viruses (stealth viruses) can almost no longer be detected by antivirus software (see also rootkit ).
With the help of these programs the hard disk and RAM are scanned for harmful programs. Antivirus programs usually offer two operating modes: a manual one in which the antivirus program only checks all files once when requested by the user ( on demand ), and an automatic one in which all write and read accesses to the hard disk and partly also to the main memory are checked ( on access ). There are anti-virus programs that use several program engines responsible for scanning for viruses . If these search independently of one another, the probability of detection increases.
Antivirus programs never offer complete protection, since the detection rate is not 100% even with known viruses. Most of these programs can detect unknown viruses based on their behavior (" heuristics "); however, these functions are very unreliable. Antivirus programs also often only detect viruses after infection and may not be able to remove the virus during normal operation.
If there is justified suspicion of infection, several on-demand programs should be used one after the other. It makes sense to ensure that the programs use different engines so that the recognition rate increases. There are antivirus programs from different manufacturers that use the same scanning methods and therefore have a similar risk of overlooking certain viruses. Different on-access antivirus programs ("Wächter", "Guard", "Shield", etc.) should never be installed at the same time, because this can lead to malfunctions of the PC: Since many of these on-access scanners already after the operating system is started If they search for boot sector viruses, they are started almost simultaneously and try to gain sole and first access to every file to be read, which is naturally impossible and therefore can or must lead to serious system malfunctions.
If several on-demand scanners are installed and - even independently, i.e. not simultaneously - started and executed, false viruses are often found, in which one program recognizes the virus signatures of the other on the hard drive or in the main memory as a virus or virus files that have already been saved in the finds the so-called "quarantine folder" of the other program. Even an on-access scanner can therefore falsely find one or more viruses in the competing product when an on-demand scan is also started by another virus scanning program.
In principle, the entire PC should be checked for viruses occasionally, but regularly, since - with the help of new virus signatures - old, previously undetected virus files can be discovered and, in addition, the "guard modules" from one and the same manufacturer sometimes search and recognize differently than the associated one On-demand scanner.
Protection through live systems
Live systems like Knoppix , which are started from a CD regardless of the installed operating system, offer almost complete protection if no write permission is given for the hard disks. Because no changes can be made to the hard disk, no malicious program can nestle on the hard disk. Memory- resident malware can also cause damage to such live systems because these systems can serve as an intermediate host or source of infection for other computers. Malware that resides directly in the main memory is only rendered harmless after a reboot.
Computer virus types
Boot viruses
Boot viruses are among the oldest computer viruses. These viruses were a very common form of virus until 1995. A boot sector virus infects the boot sector of floppy disks and hard disk partitions or the master boot record (MBR) of a hard disk.
The boot sector is the first physical part of a floppy disk or hard disk partition . Hard disks also have a so-called master boot record . Like the boot sector of floppy disks, this is at the very beginning of the data carrier. With the boot loaders, boot sectors and MBR contain the software that is executed by a computer immediately after its start, as soon as the firmware or the BIOS has put the computer in a defined start state. Boot loaders usually load the installed operating system and give it control of the computer.
As described, boot loaders are programs that run before the operating system and are therefore very interesting for viruses: Boot viruses can intervene in the operating system that is loaded after them and manipulate it or bypass it completely. This allows them to spread, for example, on the boot sectors of inserted floppy disks.
If a computer does not load the hard disk's MBR but the infected boot sector of a floppy disk, the boot virus it contains usually tries to spread into the hard disk's MBR so that it can become active every time the computer is started without a floppy disk.
Boot viruses, however, have to struggle with the technical limitations associated with the storage location “boot sector” or, above all, “MBR”: They can be a maximum of 444 bytes, provided they do not hide other components in other areas of the hard disk. The industry standard MBR is one sector, i.e. 512 bytes, but some bytes are used for hardware and BIOS compatibility. They also have to take over the tasks of the boot loader so that the system remains functional, which takes up even more space from the already very limited space for the virus logic. In addition, since they become active before an operating system, they cannot access functions provided by an operating system, such as finding and opening a file.
Boot sector viruses for CD-ROMs have also existed since 2005. These infect bootable CD-ROM image files . It is technically possible to create a boot sector virus for a bootable local network or for a USB stick, but this has not yet happened.
There are almost no boot sector viruses these days, as BIOS and operating systems usually have well-functioning protection against them. While boot sector viruses exist that can bypass this protection, they are generally very slow to spread. Due to the technical problems associated with this type of virus, they also require significantly more knowledge and programming skills from the virus author than is necessary with other forms of viruses, while at the same time severely limiting his possibilities.
File viruses and link viruses
Link viruses, or file viruses, are the most common type of virus. They infect executable files or program libraries on an operating system.
In order to infect an executable file, the virus has to insert itself into this host file (often right at the end, as this is the easiest). The virus also modifies the host file so that the virus is called when the program starts. A special form of link virus selects a different strategy and fits into an existing program function.
For the different types of link viruses, see Types of infection .
Macro viruses
Macro viruses require applications that process documents with embedded macros. They infect macros in non-infected documents or insert appropriate macros if they do not already exist.
Many types of Office documents use macros. But other document files can also contain macros. They are usually used to automate or simplify recurring tasks in the documents.
Applications with such documents often support a special macro that is automatically executed after the document is loaded. This is a preferred location for macro viruses to infect because it is the most likely to be invoked. Like link viruses, macro viruses try to infect files that have not yet been infected.
Since most users are not aware that, for example, a text document can contain executable content and thus a virus, they usually deal with such documents relatively carelessly. They are very often sent to other users or offered for download on public servers. This allows macro viruses to spread quite well. Around the year 2000 they represented the greatest threat, until they were replaced by computer worms.
One protection against macro viruses is to ensure that only certified macros are executed by the application. This is of particular interest to (larger) companies and authorities, where a central certification authority checks macros for general use before they are released and certifies accepted macros.
It is also advisable to switch off the automatic execution of macros in the relevant application.
Script viruses

A script is a program that is not translated into machine language by a compiler , but is executed step by step by an interpreter . A script is often used on web servers (for example in the form of the scripting language Perl or PHP ) or by scripting languages embedded in websites (for example JavaScript ).
A script is often used in websites in addition to normal HTML or XML in order to implement functions that would otherwise only be possible with the help of executable programs on the server ( CGI programs ). Such functions are, for example, guest books, forums, dynamically loaded pages or webmail. Script languages are mostly independent of the operating system. To run a script, a suitable interpreter - a program that converts the script from a human-readable programming language into an internal representation and then executes it - is required. Like any other virus, the script virus looks for a suitable host file to infect.
In the case of HTML files, the script virus inserts itself into (or creates) a special area, the script area, of an HTML file. Most browsers load this script portion of the HTML document in order to eventually execute it. So these special script viruses behave almost exactly like the macro viruses described above.
Unix, Mac OS X and Linux systems use scripts to automate many tasks, which were written, for example, for a Unix shell such as Bash, in Perl or in Python . The command line interpreters from MS-DOS and Windows can also execute special scripts. There are viruses for these scripting languages as well, but they are only of laboratory character and are as good as not to be found in the "wild". Moreover, unlike script viruses embedded in HTML, they cannot be accidentally caught; instead, as with a link virus, a contaminated script must first be copied onto your system and executed.
Mixed forms
Not all computer viruses clearly fall into a specific category. There are also mixed forms such as viruses that infect both files and boot sectors (example: kernel viruses ) or macro viruses that can also infect program files . Almost every variation is possible in the composition.
EICAR test file
The EICAR test file is a file that is used to test virus scanners. It is not a virus and does not contain any “viral” content, but can only be recognized as a virus by definition. Every virus scanner should recognize this file. It can therefore be used to test whether the virus scanner is working correctly on a system that has not been infected by a virus.
Types of Infection
Companion Viruses
Companion viruses do not infect the executable files themselves, but instead rename the original file and create a file with the original name that contains just the virus, or they create a file with a similar name that runs before the original file. So it is not actually a virus, as no host program is being manipulated.
Under MS-DOS, for example, there are companion viruses that create a hidden file with the same name with the extension “.com” for an executable EXE file , which then only contains the virus. If a program name without an extension is entered in the command line of MS-DOS, the operating system first searches for programs with the extension “.com” and then only for programs with the extension “.exe”, so that the malware detects the actual program in the Search order appears and is called. The malware executes the original program after it has mostly settled in the working memory, so that the user often does not notice the infection.
Overwriting computer viruses
Overwriting computer viruses are the simplest form of viruses, but are easiest to detect because of their highly destructive effects. When an infected program is executed, the virus searches for new infectable files and either overwrites the entire file or just part of it (usually the beginning) with a required length. The host file is irreparably damaged and no longer works or no longer functions correctly, which means that an infection is noticed almost immediately.
Prepender
This type of computer virus inserts itself at the beginning of the host file. When the host file is executed, the virus first becomes active, which spreads or unfolds its harmful effects. The virus then restores the original state of the host program in the main memory and executes it. Except for a small loss of time, the user does not notice that a virus has just become active, as the host file is completely operational.
Appender
An appender virus attaches itself to the end of a host file to be infected and manipulates the host file in such a way that it is executed before the host program. After the virus becomes active, it executes the host program by jumping to the original program entry point. This virus form is easier to write than a prepender, since the host program is only minimally changed and therefore it does not have to be restored in the main memory. Because appenders are easy to implement, they are fairly common.
Entry point obscuring
The technical term "Entry Point Obscuring" (EPO for short) means "concealment of the entry point". Viruses that use this technique search for infection at a specific point in the host file that is not at the beginning or at the end. Since this point varies from host to host, viruses of this type are relatively difficult to develop because, among other things, a routine for searching for a suitable point of infection is required. The advantage of this virus type is that virus scanners would have to examine the entire file in order to find EPO viruses - in contrast to the detection of prepender and appender viruses, in which the virus scanner only has to examine the beginning and end of the file in a targeted manner. If a virus scanner is also looking for EPO viruses, it needs more time - if the virus scanner is set in such a way that it saves time, EPO viruses usually remain undetected.
For entry point obscuring, the virus looks for a special location, such as a program function, somewhere in the file in order to infect it. The function to terminate the program, for example, is particularly worthwhile, as it usually has an easily identifiable recognition pattern and is called exactly once. If the virus were to infect a time-critical function or a function that is called very often, it would be more easily noticed. The risk for EPO viruses is that they may choose a point in a host that is never called, or not called every time the host runs.
techniques
random access memory
Memory- resident viruses remain in memory even after the host program has ended. Under MS-DOS a technique called TSR (Terminate and Stay Resident) was used, in operating systems such as Windows, Unix or Unix-like systems (Linux, Mac OS X) the virus creates a new process. In this case, the virus tries to give the process a name that does not seem suspicious or to hide its process completely. Occasionally, these viruses also try to manipulate functions of the operating system or redirect them to themselves, provided the operating system enables or does not prevent this.
Viruses self-protection
Stealth viruses
Computer viruses of this type take special measures to disguise their existence. System calls are intercepted so that, for example, when querying the size of an infected file, the size before the infection is specified (some viruses do not change the original size at all because they copy themselves to unused areas of the file) or when reading the File return the data from the original file.

Encrypted Viruses
This type of virus encrypts itself. The key can vary from infection to infection. This is to prevent antivirus programs from simply looking for a specific string of characters in files. The routine for decryption must, of course, be available in normal form and can be recognized by antivirus programs.
Polymorphic Viruses
These types of viruses change their shape from generation to generation, sometimes completely. This often happens in combination with encryption - variable encryption is used here. However, part of the virus must be in an unencrypted form in order to decrypt the rest when it runs. In order to make this part variable too, the decryption routine is recreated with each infection. The routine, which the decryption routine always creates anew, is itself located in the encrypted part of the virus and can, for example, exchange commands that are independent of each other and code operations with different command sequences, so that different variants arise.
Metamorphic viruses
In contrast to polymorphic viruses, which only change the form of the code (through variable encryption or permutation ), with metamorphism the virus is temporarily rewritten in a metalanguage (hence the name). The meta-language is using an obfuscator again compiled . The formal grammar of the virus always remains the same.
This technique is possible because the assembly language offers various options for executing an instruction. For example, the command mov eax, 0x0 can be converted to xor eax, eax or sub eax, eax . Because a mutation is a change in the virus's command sequence (and not just a different representation of the same command sequence), metamorphic viruses are more difficult to detect than polymorphic viruses.
Examples are Win32.ZMist, Win32.MetaPHOR or Win32.SK. Although these viruses are highly complex and have caused problems for many antivirus manufacturers, they are still trivial from a theoretical point of view.
Retroviruses
Retroviruses aim to disable virus protection programs and personal firewalls. Since they not only protect themselves from being discovered, but also open the door to other malware, they are considered very dangerous.
Possible damage or payload
Computer viruses are feared above all because they have a reputation for destroying all data. However, this is only correct in a very few cases. Most computer viruses mainly try to spread themselves as widely as possible and therefore not attract attention.
- Harmless effects
One characteristic that every virus has is that it steals computer time and memory. As a virus spreads itself, it uses the power of the processor and hard drives. Viruses are usually written in such a way that they do not noticeably impair the system, so that the user does not recognize them. Given the size of current hard disks, the additional hard disk space required is no longer noticeable.
- Unintentional damage - programming error
Many computer viruses contain errors which, under certain circumstances, can lead to fatal consequences. Although these errors are mostly unintentional, they can still destroy files through a false infection or even destroy entire databases in individual cases.
- "Existence report" - messages to the user
Some viruses make their existence known to the user. Examples of virus reports can be for example:
- Beeping or music
- Message boxes or suddenly appearing texts on the screen with often (for the virus author) amusing news or even political content
- Manipulation of the screen content such as falling letters, distortions or objects moving across the screen.
Most of these existence reports are harmless and often only occur at certain times of the day or only on certain days in order not to attract attention too quickly and thus to achieve a higher distribution. There are also “viruses” that do not actually contain malicious routines, but only such messages. These are so-called joke programs. Examples of this are Eatscreen or FakeBlueScreen.
- Data destruction
Infecting files manipulates and possibly destroys the data they contain. However, since most viruses are to be protected from detection, a reconstruction of the data is possible in many cases.
A few viruses are written specifically to destroy data. This can range from deleting individual files to formatting entire hard drives. This type of payload is directly associated with all viruses by most people. Since the memory is the "habitat" of viruses, these actions often destroy themselves.
- Hardware destruction
Direct hardware destruction by software and thus by computer viruses is only possible in individual cases. To do this, the virus author would have to know how certain hardware can be controlled so extremely or incorrectly that it can be destroyed. Some (partly more theoretical) examples of such possibilities are:
- Sending extreme image signals to screens. Fixed frequency monitors that are no longer in use today were susceptible to this, there were viruses that actually carried out these attacks on such monitors. Today, damage from faulty or extreme image signals is as good as impossible.
- Overclocking graphics cards that allow the clock frequency of the components to be set using software. If the overclocking is too high and the cooling is insufficient, components can overheat and be damaged or destroyed.
- Overclocking of components on the motherboard , which can overheat themselves or overload other components (resistors, integrated components).
- Hard drives cannot be used due to certain unofficial ATA commands.
- Reduce the fan speed to cause the components to overheat.
Since the selection of hardware components in today's PC area is very heterogeneous , the opinion so far has been that it is not worthwhile for virus authors to carry out such attacks.
- Firmware destruction
One damage that is misinterpreted as hardware damage is overwriting the BIOS, which today is mostly stored in flash memories . If this flash memory is maliciously overwritten, the computer can no longer start. Since the computer does not start anymore, hardware damage is often wrongly assumed. In this case, the flash memory must be removed and re-recorded with a correct BIOS. If the flash memory is firmly soldered in, it is often not economically viable to expand and the entire motherboard must be replaced. In the case of motherboards with SPI or JTAG interface for the flash memory, a deleted or overwritten BIOS can be renewed using suitable programming devices.
Economic damage
The economic damage caused by computer viruses is less than the damage caused by computer worms. The reason for this is that viruses can only spread very slowly and are therefore often only spread locally.
Another reason why the economic damage is not so great with computer viruses is the fact that they need the compromised computer or the attacked file in general for a longer period of time in order to be able to spread effectively. Computer viruses that destroy data instantly are very ineffective because with this action they also destroy their own living space.
In the age of the DOS viruses , however, there were some viruses that caused considerable damage. One example is the DataCrime virus , which destroyed entire databases. Many governments responded to this virus and passed laws that make spreading computer viruses a criminal offense.
There were also isolated cases of computer viruses under Windows, which meant serious financial damage for individual companies. In early 1998, for example, the XM / Compat virus was discovered, a macro virus that infects Microsoft Excel files with an extremely malicious malware function: whenever Excel is closed, the malware searches a random document from the processing history for unprotected ones Cells with numeric values. In these cells he randomly changes the values with a one percent probability within a range of +5 to −5%. Due to the initially insignificant changes, the data manipulated in this way may only be noticeable after weeks or even months. If the damage is discovered, it can only be repaired by importing a backup - of course, it must be known exactly when the first infection took place. Although the malware is not particularly widespread, there have been cases of companies whose business balance sheets and sales reports have become completely unusable due to an XM / Compat infestation.
Win32.CIH , also known as the "Chernobyl virus" (after the Chernobyl nuclear accident on April 26, 1986), was also a virus with high economic damage. It spread over a large area and on April 26, 2000 the data content of more than 2000 BIOS Chips destroyed in South Korea . According to the antivirus manufacturer Kaspersky, 3000 PCs were said to have been affected in the previous year.
Another economic factor used to be primarily the damage to the image of the companies concerned; today this immaterial damage is no longer so high, as a computer virus is more likely to be accepted as a normal and customary danger.
construction
Computer viruses come in many different forms, making it difficult to describe how a virus is basically structured. The only necessary component that, by definition, turns a computer program into a computer virus is the propagation routine.
The following explanation is by no means a standard for all viruses. Some viruses can have more functions, others less.
- Decryption routine : In the case of encrypted viruses, this part ensures that the encrypted data can be executed again. Not all viruses have this part because not all of them are encrypted. Often the virus decryption routine is used by antivirus manufacturers to identify the virus, as this part is often more clearly recognizable than the rest of the virus.
- Multiplication part: This part of the program ensures that the virus replicates. It's the only part every virus has (definition).
- Detection part: The detection part checks whether a program or system area has already been infected. Each host program is infected only once. This part is present in almost all non-overwriting computer viruses.
- Damage component: In relation to the number of computer viruses, only very few have a damage component (payload). The damage part is the reason why many people fear computer viruses.
- Condition part: The condition part is responsible for ensuring that the damage part is carried out. It is contained in most computer viruses with a harmful part. Viruses without a condition part either carry out the damage part with every activation or - in very rare cases - never. The condition part (trigger) can, for example, execute the payload on a certain date or with certain system requirements (number of files, size of free storage space, etc.) or simply randomly .
- Camouflage part: A camouflage part is only present in a few, complex viruses. For example, he can encrypt the virus or give it another form (polymorphism, metamorphism). This part is used to protect the virus from being detected by anti-virus software. However, there is only a very small number of viruses that cannot be fully detected (for example: Win32.ZMist, ACG, Win32.MetaPHOR or OneHalf ).
Achilles heel of a virus
In order for a classic reactive virus scanner to identify a virus, it needs its signature. A virus tries to infect a system, and a link virus, for example, does this by attaching it to an existing program. In doing so, it must first (apart from overwriting viruses) check whether it has already infected this program - in other words, it must be able to recognize itself. If it did not do this, it could theoretically infect a program as often as required , which would be noticed very quickly due to the file size and the CPU load. This recognition pattern - the signature - can also be used by virus scanners under certain circumstances to recognize the virus. Polymorphic viruses are able to work with different signatures that can change, but always obey a rule. It is therefore relatively easy and quick for the manufacturers of anti-virus software to identify a new virus after it has become known.
Instead of polymorphic signatures, many viruses use very small identifiers, such as an unused byte in portable executable format. A virus scanner cannot use this one byte as a detection pattern because there would be too many false positive hits. However, it is not a problem for a virus if it does not infect some files under unfavorable conditions.
history
Theoretical beginnings: until 1985
In 1949, John von Neumann published his work Theory and Organization of Complicated Automata . In it he puts forward the thesis that a computer program can reproduce itself. This was the first mention of virus-like software. In 1961 the theory was successfully translated into a computer game called Darwin by Victor Vyssotsky , Robert Morris Sr., and Doug McIlroy , researchers at Bell Labs . Two or more players let software organisms fight for control of the system. The programs tried to overwrite each other. Later versions of the game became known as Core Wars . The Core Wars concept gained wide recognition through an article by Alexander K. Dewdney in the Computer Recreations column of Scientific American magazine .
In 1972 Veith Risak published the article Self- reproducing automatons with minimal information transfer . It reports on a virus written for research purposes. This contained all essential components. It was programmed in the machine code of the SIEMENS 4004/35 computer and ran perfectly. The science fiction author David Gerrold was the first to mention the term “computer virus” in 1972 in the story When Harlie Was One ( pre-published in parts in GOD Machine and others) about the GOD machine.
In 1975, the British author John Brunner published the novel The Shock Waves Rider , in which he anticipated the danger of Internet viruses. His colleague Thomas J. Ryan described in 1979 in The Adolescence of P-1 how an artificial intelligence spreads like a virus over the national computer network.
In 1980 Jürgen Kraus wrote a diploma thesis at the University of Dortmund , in which the comparison was made that certain programs can behave similarly to biological viruses.
In 1982 the 15-year-old American student Rich Skrenta wrote a computer program that distributed itself on diskettes on Apple II systems. The program was called Elk Cloner and can be described as the first boot sector virus.
However, the line between theory and practice in computer viruses is blurring, and even experts argue about which actually came first.
Professor Leonard M. Adleman first used the term "computer virus" in 1984 in a conversation with Fred Cohen .
Practical beginnings: 1985–1990
Fred Cohen completed his PhD thesis Computer Viruses - Theory and Experiments in 1984 . It presented a working virus for the Unix operating system. Today this is considered to be the first computer virus.
In January 1986 the first virus infection was discovered on a mainframe computer at the Free University of Berlin.
In 1986, two software dealers from Pakistan distributed the first virus for the MS-DOS operating system, which is known as the Pakistani, Ashar or Brain virus . These dealers were selling cheap black copies of original software. This was possible because copying software was not a criminal offense there. They included the virus with every copy of the software, which was supposed to have the purpose of binding customers to the dealer. Surprisingly, this virus even spread to the United States . The program was relatively harmless as it only renamed the table of contents of the infected floppy disks to Brain .
Finally, in 1987, the first virus for Macintosh computers was discovered. Apple then delivered its system complete with a virus scan program. However, it could only find this one virus family and was blind to other virus types, so to speak. So the program was only of limited use.
Shortly afterwards, the Cascade virus was found for the first time in Germany. It was the first virus to become memory resident and also to appear encrypted in files. Because of these properties, it is counted among the second generation of viruses.
The Jerusalem or PLO virus was one of the first viruses . It also became known as Friday the 13th Virus because on such a day it deletes all COM and EXE files. On all other days, it slows down the computer speed after about 30 minutes.
Viruses attacked not only MS-DOS , but also other systems such as Apple Macintosh , Amiga , Atari and Unix .
In the same year, 1987, the Data-Becker-Verlag published the first book on the subject of computer viruses, Das große Computervirenbuch by Ralf Burger. Since Burger published the source code of some viruses in the book, dozens of variants of the viruses he described appeared in public in the months that followed.
In 1988 the first virus construction set appeared. This also made it possible for beginners to create viruses to measure. The program was written for the Atari ST computer .
It was during these years that the first antivirus programs were launched, mostly to protect large companies. In 1989, the first polymorphic virus, V2Px , appeared , which was able to encrypt itself again and again and was very difficult to detect.
The DOS Virus Era: 1990-1995
In these years viruses have become increasingly complex in order to be able to spread better and to be protected against detection by antivirus programs. At the beginning of 1991 the first polymorphic virus, the tequila virus, spreads . A little later, in 1992, a virus writer called Dark Avenger published the first polymorphic program generator , MTE . This way, even the simplest viruses could easily protect themselves from detection. Some of the antivirus software makers at the time couldn't solve this problem and stopped developing their programs.
In 1992 the Michelangelo virus also triggered enormous media hysteria. With him the existence of the viruses became known to the general public.
During these years, new techniques were repeatedly discovered in viruses, such as the simultaneous infection of files and the boot sector, OBJ files or source code files. In 1992, Win16.Vir_1_4 was the first computer virus to be registered for the Microsoft Windows 3.11 operating system . This proof-of-concept virus was never discovered "in the wild".
Viruses like ACG and OneHalf mark the end of MS-DOS viruses. To this day, they are among the most complex viruses of all. They are highly polymorphic and also contain techniques such as metamorphism.
The era of viruses for 32-bit Windows operating systems: 1995–2002
From 1995, with the appearance of Microsoft Windows 95 and the constant increase in users, viruses were also written for this operating system (and its obligatory programs such as Microsoft Office). The first macro virus for Microsoft Word appeared in 1995. Since documents were exchanged more often than programs, macro viruses became a very big problem for users. In the years that followed, the first macro viruses appeared for Excel (1997), Powerpoint and Access (both 1998) and Visio (2000). In 1996, the first virus constructor kit for macro viruses was written, which also made it possible for people without programming knowledge to create viruses.
In 1996, Boza, the first virus for Microsoft Windows 95 appeared. This showed that the latest Microsoft operating system was not, as previously claimed, inviolable for viruses.
When the battle between antivirus manufacturers and virus authors seemed to have been won in favor of the antivirus manufacturers, the first polymorphic Windows 32-bit viruses were written in 1998 with W32.HPS and W32.Marburg . A short time later, Regswap was the first metamorphic virus for these operating systems.
In 1998 and 1999 the first VBS and JavaScript viruses appeared and, as a logical consequence, the first HTML viruses. These viruses worked with the controversial add-on program "Windows Scripting Host". Now websites could also be infected by viruses.
During this time, several other viruses that are safe for the user and are still interesting were written. Examples are the OS2.AEP virus, which was the first to infect executable files of the OS / 2 operating system , or the first viruses for HLP files, for PHP files, for Java , for AutoCAD , for Bash , for Palm OS and for Flash .
At the end of this era (as in the DOS era) the most complex viruses that existed up to that time reappeared. Examples are Win32.MetaPHOR or Win32.ZMist , which are very highly metamorphic and cannot be fully detected by antivirus programs from all manufacturers. These viruses were written by members of Virus Writer Group 29A who have significantly advanced the techniques of polymorphism and metamorphism over the years.
New niches: from 2002
From around 2002, viruses faded into the background and were replaced by worms . The development of viruses continues nonetheless and mainly relates to new niches.
In 2002 the first virus was written that could infect both Win32 applications and ELF files (for example Linux applications). This virus can be seen as heralding a new age for viruses.
In 2004 a new era for viruses finally dawned: The first virus for PocketPCs (with the Windows CE operating system ) appeared and showed that these widely used communication devices are not spared either.
A few months later, the Win64.Rugrad virus was discovered. This virus could infect the applications of the newly released Microsoft Windows XP 64-bit Edition and has played a pioneering role in the development of new viruses.
A few months later, in 2005, the first virus was written for cell phones (with the Symbian OS operating system ). After worms for this operating system have already appeared, it can also infect files.
In mid-2005, shortly after the release of the first beta version of the XP successor Microsoft Windows Vista , the first virus for the Microsoft Command Shell (code name Monad ) was released. At first it was propagated that there would be a first virus for the new Windows. However, after the virus became known, Microsoft announced that Monad would not be included in Vista as planned. So this would be a beta virus with an extremely low chance of spreading.
The first real computer virus for MS Windows Vista appeared a few months later, in October 2005. MSIL.Idoneus uses the .NET Framework 2.0 to spread.
During this time, the first viruses for Ruby , MenuetOS , F # , CHM and Microsoft Office Infopath were discovered, but these will not pose a threat to users either now or in the future, as these platforms are hardly widespread and the viruses can therefore hardly multiply.
literature
- Eric Amberg: KnowWare 183. Security on the Internet. IPV, Hamburg 2004, ISBN 87-91364-38-8 .
- Klaus Brunnstein : Computer Virus Report. WRS Verl. Economics, Law and Taxes, Munich 1989, ISBN 3-8092-0530-3 .
- Ralf Burger: The great computer virus book. Data Becker, Düsseldorf 1989, ISBN 3-89011-200-5 .
- Andreas Janssen: KnowWare 170. Viruses, hackers, firewalls. KnowWare, Osnabrück 2005, ISBN 87-90785-83-5 .
- Eugene Kaspersky: Malware: About viruses, worms, hackers and Trojans and how to protect yourself against them Hanser-Verlag, Munich 2008, ISBN 978-3-446-41500-3 .
- Mark A. Ludwig: The Giant Book of Computer Viruses. American Eagle Publications, Show Low, Ariz. 1998, ISBN 0-929408-23-3 .
- Skardhamar rune: Virus. Detection and Elimination. AP Professional, Boston 1995, ISBN 0-12-647690-X .
- Peter Szor: The Art Of Computer Virus Research And Defense. Addison-Wesley, Upper Saddle River NJ 2005, ISBN 0-321-30454-3 .
Web links
- botfrei.de: The Anti-Botnet Advice Center - An initiative of the German Internet industry
- Article about viruses - free German-language publications on the subject
- History of virus programming ( Memento from January 14, 2005 in the Internet Archive ) on Telepolis
- To mark the 20th anniversary of computer viruses on Telepolis
- Journal in Computer Virology - scientific magazine on computer viruses and worms
- VX Heavens - Archives of Computer Viruses, Virus Programmer Magazines, etc.
- The Pakistan flu in the west on Telepolis - about the supposedly first MS-DOS computer virus
Individual evidence
- ↑ Sophos Security Report 06. In: sophos.com. (PDF; 1.1 MB, English)
- ↑ Microsoft has been waiting almost a year to provide a patch . In: golem.de. September 20, 2004, accessed January 29, 2017.
- ↑ Web analysis - operating systems and devices. In: webmasterpro.de. Retrieved January 29, 2017.
- ↑ ROOTKITS: Virus filters are threatened with knockout . In: Spiegel Online . December 27, 2005, accessed January 29, 2017.
- ↑ Peter Ferrie, Peter Szor: Hunting for Metamorphic. In: pferrie.tripod.com. Virus Bulletin Conference, September 2001, accessed on January 29, 2017 (PDF; 237 kB, English).
- ↑ Peter Ferrie, Frederic Perriot: Detecting Complex Viruses. In: pferrie.tripod.com. December 6, 2004, accessed January 29, 2017.
- ↑ Peter Ferrie, Péter Ször: Zmist Opportunities. In: pferrie.tripod.com. March 2001, accessed on January 29, 2017 (PDF; 122 kB)
- ↑ Eric Filiol: Metamorphism, Formal Grammars and Undecidable Code Mutation. In: vxheavens.com. International Journal of Computer Science, Vol. 2, No. 1, April 2007, pp. 70-75, ISSN 1306-4428 . Retrieved January 29, 2017.
- ↑ Information about the viruses that damage the CMOS and the BIOS. In: sophos.de. Retrieved January 29, 2017.
- ↑ Darwin, a Game of Survival of the Fittest among Programs , accessed June 2, 2017
- ↑ Heike Häger and Sonja Engels: Virus alert! RWTH Aachen, October 24, 2003, p. 5 , archived from the original on December 9, 2012 ; accessed on January 3, 2018 .
- ↑ Self-reproduction in programs. ( Memento of the original from October 8, 2013 in the Internet Archive ) Info: The archive link was inserted automatically and has not yet been checked. Please check the original and archive link according to the instructions and then remove this notice. Jürgen Kraus, diploma thesis, Düsseldorf, 1980. (English translation: Journal In Computer Virology, Vol. 5, No. 1, February 2009) In: vxheaven.org. Retrieved January 29, 2017.
- ↑ Konrad Lischka: 25 years of computer viruses - the apple eater. In: Spiegel Online , July 13, 2007, accessed on January 28, 2017. ("The program propagated itself via floppy disks, showed a poem, but otherwise left the infected Apple computers intact.").
- ↑ Fred Cohen: Computer Viruses - Theory and Experiments. In: all.net. 1984, accessed January 29, 2017.
- ^ E-zine Releases New Virus Technologies. In: blog.trendmicro.com. Trend Micro Inc., archived from the original on January 11, 2008 ; accessed on January 28, 2017 (English).


