Access right
The access rights - or even execution rights - call in the computer the rules of administrative access control , applied in determining whether and how users, programs or parts of programs, operations on objects (eg, networks, printers, file systems.) Are allowed to run. This concept is most common for file system permissions , which determine which users are allowed to read, write, change or even execute which files and directories .
example
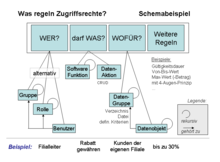
The graphic shows an example of what can be specified via access rights. In the simplest case, this is WHO is allowed to do WHAT. Under “WHO”, it is often not a specified person but a group / role to which individual users are assigned. Elementary functions or groupings thereof can also be named for “WAS” and, if necessary, special data actions (Create, Read, Update, Delete) can be permitted on certain types and amounts of data. Additional stipulations such as 4AP etc. can be regulated as required .
The form and data format of the specifications depend on the access control system used. The facts mentioned as examples can, if necessary, be specified by an expression such as "Rights group A510"; the specific meaning and the necessary tests are known to the access control system and are carried out there. The prerequisite for access control is that the user has been clearly identified .
Methods of access control through rights management
One way to make access very flexible, are Access Control Lists : For every object to be protected, there is a list for each user ( user role specifies) or any group which functions are allowed and which are not. In the past, however, the options for restricting access were much more limited in order to keep the implementation simple, for example with traditional file access rights on Unix systems.
Some programming languages also have their own security system that is independent of the operating system and that is integrated into the runtime environment . Examples of this are the security concepts of Java and .NET . The access rights are mostly not dependent on the user, but on the extent to which a certain program library is viewed as trustworthy (see sandbox ).
Access classes
To assess the security of computer systems, the security systems for managing access rights are divided into different classes:
- Discretionary Access Control (DAC): Access isgranted or deniedbased on the identity of the actor (user) and object. This class includes, for example, access protection for files in common file systems .
- Mandatory Access Control (MAC) or multilateral security models: In addition to the identity of the user and object, rules and properties are also checked in order to decide whether access to an object is granted or denied. This is an important part of high security systems and often goes hand in hand with the requirement that access control beimplementedby a reference monitor.
- Role Based Access Control (RBAC): Access is checked based on the role of the user. A user can be assigned to several roles. Access to an object is granted or denied depending on whether a user has the appropriate role.
The model and management of access rights is an important part of secure computer systems and therefore a criterion for certification in accordance with common security standards such as TCSEC , ITSEC and their international successors, the Common Criteria .