Authentication
Authentication (from ancient Greek αὐθεντικός authentikós , German `` reliable, after a sure source '' ; root form combined with Latin facere `` make '' ) is the evidence ( verification ) of an alleged property (claim) of an entity , for example a person, a device, a Can be a document or information and which carries out its authentication through its contribution .
The associated verb is authenticate (English: authenticate ), which stands for witnessing the authenticity of something. In computer science, the substantiated word authenticate is often used both for the authentication process and for the result of this verification, since in the English-speaking world there is no syntactic distinction between the actions of the entities involved . In the German-speaking area, the term authentication is used to check authenticity and the term authentication is used to attest to authenticity.
The authentication of an entity with regard to the claimed property of authenticity, which can be, for example, granting an “existing access authorization ” or “ authenticity ”, allows the authenticated entity to take further actions. The entity is then considered to be authentic .
The final confirmation of an authentication is also referred to as authorization if it is restricted by certain permitted modes and / or in a certain context . Authentication is valid until the relevant context is left or changed, or until the relevant mode is left or changed.
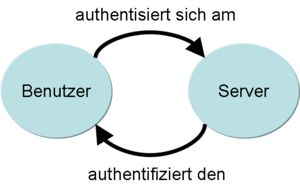
The process in context
In the case of authentication between two entities, one authenticates itself while the other authenticates the former.
The authentication is a verification of the assertion of authenticity . The authentication of a counterpart is often used to identify them and is also conceivable in the sense of establishing an identity . Authentication is thus in principle the proof that it is the original, whereby an authentication can refer not only to people, but to any material or immaterial objects, e.g. B. electronic documents or art objects.
In the example of a computer program that can grant access to a secured area, the user first asserts his access authorization by entering a user name. In addition, he authenticates himself by providing his password. The program then uses this information to identify the user and then carries out the authentication, i.e. the verification of the allegation made about authenticity. Only when this verification is successful will the user be assigned the specified access rights as part of the authorization, usually for the duration of a session. This means that the identity of the communication partner is certain for the program, although this can change over time (for example during an MITM attack ) or it may not have existed from the start (for example after phishing ). During the authorization process , the program decides whether the authenticated user can be granted access . If this is also successful, the program grants the user access to the secured area.
Methods
A user can achieve authentication (proof of their own identity) in three different ways:
- Proof of knowledge of information : He knows something, for example a password
- Use of a property : He has something, for example a key
- Presence of the user himself: He is something, for example in the form of a biometric feature
Depending on the area of application, the choice of authentication methods leads to various advantages and disadvantages in terms of practicality for the user in everyday life and the security requirements of the property to be protected. Careful consideration before implementation and commissioning ensures the security level actually achieved.
Knowledge
Characteristics:
- can forget to be
- can be duplicated, distributed, passed on and betrayed be
- can possibly be guessed
- the disclosure of knowledge can be compromised are
- carrying knowledge does not require any practical aids
Examples of authentication based on knowledge:
- password
- pin code
- Answer to a specific question ( security question )
- Zero knowledge proof
possession
Characteristics:
- Creation of the feature (possibly also the control points) is subject to comparatively high costs (often requires a special manufacturing process and a physical distribution process)
- Management of the property is insecure and involves effort (must be carried with you)
- can get lost
- can be stolen
- can be passed, passed on, or (in some cases) duplicated
- can be replaced
- can save user-specific data
- can protect itself and actively change (Smartcard, SecurID )
Examples of authentication based on possession:
- Chip card , also known as a smart card or signature card
- swipe card
- RFID card
- physical key
- Key codes on a hard drive
- SIM card for the mTAN procedure
- Certificate z. B. for use with SSL
- TAN and iTAN list
- One Time PIN Token (e.g. SecurID )
- USB stick with password safe
- USB hard drive with integrated PIN input keyboard
Physical trait / biometrics
Characteristics:
- is public information
- is always carried by people
- cannot be passed on to other people
- After the feature has been recorded, it is necessary to distribute the recorded data for comparison at control points
- requires a special device (technology) for detection
- can i. A. cannot be compared with a reference sample with certainty, but only with a probability (<1)
- false acceptance is possible (false acceptance)
- false rejection is possible (false rejection)
- Life detection may be required (e.g. so that an artificial fingerprint or cut finger is rejected)
- changes over time or as a result of accidents and is therefore less recognizable
- if the characteristic is chosen unfavorably, certain groups of people who lack the characteristic are excluded
- cannot be replaced
- can pose data protection problems
Examples of authentication based on biometric features:
- fingerprint
- face recognition
- Typing behavior
- Voice recognition
- Iris recognition
- Retinal features (fundus)
- Handwriting ( signature )
- Hand geometry ( palm scanner )
- Hand line structure
- Genetic information ( DNA )
Securing the transmission
Data is transferred during authentication. If this data is intercepted, it can be used by an attacker to create a false identity. In order to rule out the risk of disclosure, methods such as challenge-response authentication and zero knowledge are used, in which the authenticating subject no longer transmits the identification data itself, but only proof that it has this identification data beyond any doubt. An example from challenge-response authentication is that a task is set whose solution can only come from a counterpart who has a certain knowledge or a certain property. In this way, a counterpart can be authenticated without having to reveal his knowledge or property. It should be noted, however, that such methods can also be attacked.
Other systems solve the problem by using the identification data only once. One example of this is the TAN system. However, eavesdropped or spied on identification data can be used later if the initial use and thus the invalidation of the data can be prevented during the eavesdropping process. One-time password systems reduce this problem by linking the identification data to the current time.
Another possibility for securing the transmission is the so-called "second channel" communication, in which part of the identification data is transferred via a second channel. One example is the sending of an SMS with the mobile TAN (mTAN) system.
In the context of cryptographic protocols, additional random numbers are often used as so-called “ nonce ” or “ salt ” values in order to prevent an identification from being repeated.
With U2F and UAF , the FIDO Alliance published two free industry standards in December 2014 that are used to prove access authorization for any number of different web-based services.
Combination of methods
A suitable combination of the methods can reduce deficits in authentication. On the other hand, combinations of several methods are associated with higher costs and / or greater effort. Dynamic systems that automatically choose stronger or weaker authentication methods depending on the value and thus the risk of a transaction or the security of the online connection used, however, increase user acceptance and avoid productivity-reducing work steps in low-risk transactions.
A combination of two methods is called two-factor authentication or two-step authentication . The Federal Office for Information Security (BSI) defines this as strong authentication . A typical example of the combination of knowledge and ownership is a money machine: It has the bank card and know the personal identification number (PIN). A similar principle already exists in the area of mobile security hard drives. With special high-security hard drives, access is secured using a smart card and an 8-digit PIN. In the Internet, access is often granted using a password as a first step. However, in order to gain full access, a one-time code is sent to the mobile phone via SMS, which must then be entered on the website for confirmation. This is often used in online banking , for example , to authenticate a transaction . The industry standard Universal Second Factor (U2F) is used for device and provider-independent two-factor authentication.
The four-eyes principle means separate authentication by two people. Such authentication is mostly used for systems with high protection requirements: For example, opening safes in banks sometimes requires two people who authenticate themselves by possession (two separate keys).
A master key is a secure through knowledge and backed (hidden) ownership, which still provides an authentication option for a total loss of all other authentication features.
Authentication as an IT service
Offering secure and practicable authentication options for IT services is seen today as an independent and superordinate task. One speaks of "Authentication as a Service" (AaaS) and of "Authentication and Authorization Infrastructure" (AAI). At the company or university level, authentication services are organized as part of a central identity management system . The government also offers an electronic authentication service with the new ID card .
The authentication service acts as the third intermediary entity alongside an IT service and the user of the IT service. The authentication service is also referred to as the “identity provider”. If the user wants to use the service, he is first redirected to the identity provider. The authentication takes place between the user and the identity provider. After successful authentication, the identity provider issues a so-called assertion , which the user receives and which he shows to the IT service. The IT service must of course trust the identity provider to authenticate users correctly, and it must have a way of checking the origin of the assertion. Examples of such methods are Shibboleth , CAS and OpenID .
See also
literature
- Sebastian Bösing : Authentication and authorization in electronic legal transactions: Qualified signature key and attribute certificates as legal instruments of digital identity , Nomos, ISBN 3-8329-1535-4
- Josef von Helden : Improvement of the authentication in IT systems through special services of the operating system , Shaker Verlag , ISBN 3-8265-0897-1
- Sebastian Rieger: Uniform authentication in heterogeneous IT structures for a secure e-science environment , Cuvillier Verlag; Edition: 1 (2007), ISBN 3-86727-329-4
Web links
Individual evidence
- ^ Wilhelm Pape , Max Sengebusch (arrangement): Concise dictionary of the Greek language . 3rd edition, 6th impression. Vieweg & Sohn, Braunschweig 1914 ( zeno.org [accessed on July 23, 2019] In the dictionary only the adverb ancient Greek αὐθεντικῶς authentikōs is given. It is a late Greek word, so the derivation of ancient Greek αὐθέντης authéntēs , here in the sense , would be more common from 'author'.).
- ↑ a b c d authenticate. Duden , accessed on January 3, 2018 .
- ↑ Litowski, Eric and Bettina Weßelmann: Risk-based authentication technology: security made to measure . In: LANline . No. 6 , 2006, ISSN 0942-4172 ( lanline.de ).
- ↑ IT-Grundschutz: Glossary. BSI , accessed on September 27, 2019 .