Z80 interrupt logic
The Z80 interrupt logic is used to control the interrupts of the Z80 processor.
Microprocessors communicate with external devices via peripheral components, for example to receive data from a modem. So that the processor can react quickly to external events - for example the receipt of a character - the peripheral device sends an interrupt request to the processor, which interrupts its normal program, branches into an interrupt service routine (ISR) and after processing of the character continues in the normal program flow. In order to pass an interrupt to the processor, special components are usually required, the interrupt controller . To these controllers more peripheral devices can be connected in Prehistory PC from IBM , for example, eight pieces. If more than eight external devices are to be connected, another controller is required, which leads to costly design changes.
The interrupt concept of the Z80

Zilog therefore set up the interrupt control of the Z80 processor completely differently. The Z80 did not require an interrupt controller, but could still serve up to 128 external interrupt sources in the IM2 interrupt mode - with a very simple software structure at the same time. So that the Z80 can call up the associated ISR, each peripheral module has an 8-bit wide register which, together with an internal CPU register, points to an interrupt vector table in the memory, which in turn contains the entry addresses of the ISR. Since the lowest bit of the interrupt register must always be zero, there are a maximum of 128 entries in the interrupt vector table.
Expiry of an interrupt request
- The peripheral device activates an interrupt request signal (IRQ) on the CPU
- The CPU confirms the interrupt request.
- The peripheral device then puts the content of the interrupt register on the data bus.
- The CPU interrupts the current program, reads the address, fetches the address of the associated program code ISR from the interrupt vector table and executes it. After the interrupt service routine has been processed, the CPU continues the interrupted program.
conflict management
Since several external events occur simultaneously and important events can also interrupt the ISR from less important events, a conflict or priority control is required. As with the vectors, the peripheral components are responsible for this. Each block has one input (Interrupt Enable Input, IEI) and one output (Interrupt Enable Output, IEO). All blocks involved are connected in a chain, the IEO is connected to the IEI of the next one. The IEI of the first link is fixed at logical 1. The following applies:
- An interrupt is only triggered if IEI is logical 1.
- If an interrupt is active, IEO becomes logic 0, which means that all following links in the chain are blocked.
- This means that the first link in the chain always has the highest priority.
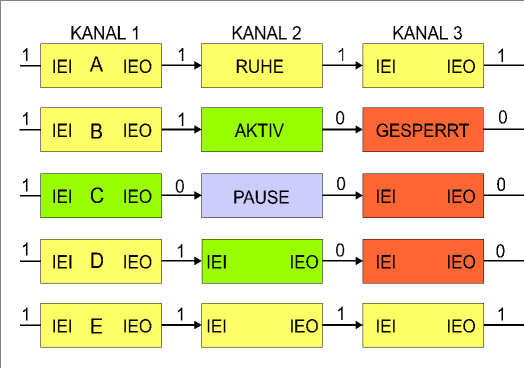
The picture explains this chain in more detail:
- A: Idle state, all modules can trigger an interrupt.
- B: Channel 2 has triggered an interrupt, is blocking channel 3
- C: Channel 1 triggers an interrupt, interrupts the ISR of channel 2
- D: Interrupt from channel 1 has ended, ISR from channel 2 continues.
- E: Interrupt from channel 2 has ended, normal program flow continues.
So that the peripheral modules know when they can release their IEO again, they listen to what program code the CPU is currently executing. Each ISR ends with the command RETI(ED 4D), which the external module recognizes and then enables its IEO.
The bag of tricks
It is often desirable to change the interrupt priorities from the program, but this is not possible due to the rigid hardware wiring. With a few tricks it is still possible, for example, that channel 3 interrupts the ISR of channel 1.
Standard ISR :
Kanal2:
PUSH AF ;Sichern der Register
PUSH BC
PUSH DE
PUSH HL
EI ;neue Interrupts gleich wieder erlauben
…
LD HL,irgendwas ;der Programmcode
…
POP HL
POP DE
POP BC
POP AF ;Zurückholen der Register
RETI ;Ende der ISR
Channel 1 could interrupt the ISR of channel 2, but not channel 3, as this is blocked by hardware. The following program fragment is used to outsmart the hardware:
Tricky ISR :
Main:
LD DE,wasauchimmer
ADD HL,DE
…
LD A,1 ;<--- Hier wird der Interrupt wirksam,
;die Adresse Main_R
;wird als Rücksprungadresse auf den Stack gelegt.
Main_R:
LD B,2
…
;Interrupt-Service-Routine fuer Kanal2
Kanal2:
CALL TRICKY_SAVE ;Unterprogramm
Kanal2_R:
…
LD HL,irgendwas
…
RET
TRICKY_SAVE:
EX (SP),HL ;Rücksprung-Adresse nach HL holen
PUSH AF ;Register sichern
PUSH BC
PUSH DE ;Stack: MAIN, HL, AF, BC, DE
;HL: Kanal2_R
LD DE,CONTINUE ;Adresse von Programmcode CONTINUE
PUSH DE ;als Rücksprungadresse auf Stack legen
EI
RETI ;Programm wird durch den RETI-Befehl
;an der manipulierten Rücksprungadresse CONTINUE fortgesetzt.
;Das Peripheriegerät erkennt die RETI-Instruktion,
;betrachtet damit "seine" ISR als beendet
;und gibt den Interrupt wieder frei.
CONTINUE:
CALL HL_JP ;Programmcode wird an der im HL-Register gespeicherten Adresse
;(=Kanal2_R) fortgesetzt
POP DE ;Register zurückholen
POP BC
POP AF
POP HL
RET ;normales "return" reicht hier aus, da RETI bereits ausgeführt wurde.
HL_JP:
JP (HL)
Each peripheral device can trigger an interrupt at any time, the priority control can be done by software.