Blaster
Blaster , also known as Lovsan or MSBlast , is a computer worm from 2003 that spreads by exploiting a security hole in the RPC interface of Microsoft Windows . The distribution took place primarily on the operating systems Microsoft Windows NT 4.0 , Windows 2000 , XP and Windows Server 2003 on TCP - port 135 instead.
history
The worm began to spread in early April 2003 through a vulnerability in the RPC / DCOM service that allowed code to be executed.
From August 16, 2003 to December 31, 2003, the worm was supposed to carry out a distributed denial-of-service attack on Microsoft's update sites , where the patch for the security hole is also stored.
Shortly after the worm was discovered, it became known that not only Windows systems but also other systems were vulnerable. According to the CERT , systems that have port 135 open can also become the target of an attack. For a successful attack, however, it is required that a distributed computing environment based on the developments of the Open Software Foundation is installed.
In the event of an attack, however, the worm was unable to tell whether it was attacking a computer that was already infected. This property slowed the spread of the virus rapidly, as it also tried to attack systems that were already infected and cause them to crash. Only then did the worm check whether it was already out of the system, which it recognized from the existence of the msblast.exe file on the hard drive.
Despite the protection of corporate networks by firewalls, the worm managed to penetrate corporate networks as well. It is assumed that this happened through already infected laptops of some employees, i.e. past any firewall or intrusion detection system . To protect private users from the virus, some Internet service providers blocked connections via port 135, but this only protected against W32.Blaster and was no protection against the security hole.
On May 12, 2004, the author of a version of the worm, Jeffrey Lee Parson of Hopkins Minnesota, was arrested and sentenced to eighteen months in prison in January 2005.
security breach
The spread of the worm is made possible by a security gap in the RPC / DCOM service. A manipulated packet is sent to port 135 used by RPC . This package triggers a so-called buffer overflow and overwrites parts of the stack memory . Code can be injected into the system, which can then be executed and thus infect a system.
The weak point is particularly critical because it is very difficult to close port 135, if at all. Switching off the RPC service can cause important parts of the system to stop working. The only protection would be to apply the patch provided by Microsoft or to use a firewall that prevents access to this port.
functionality
- The attacker started a TFTP server in order to smuggle the worm onto the computer.
- A connection between the attacker and his victim is established on TCP port 135.
- A shell is created on the victim, which listens on TCP port 4444.
- The attacker executes a command through the shell to induce the victim to install the worm.
- The attacker terminates the connection to the victim's shell, then the shell stops listening on the victim's TCP port 4444.
- The victim starts a TFTP server and processes other instructions (e.g. to change registry keys, etc.).
Identification of a virus attack
In the first version, a virus attack could be recognized by the fact that a file named was msblast.exein the directory %WinDir%\System32. In later versions, however, it was always connected to an open TFTP server on UDP port 69, which was waiting for incoming connections. In addition, the worm opened 20 different TCP ports in the port range 2500 to 2522, on which it tried to establish connections to other systems.
The following registry keys have also been added:
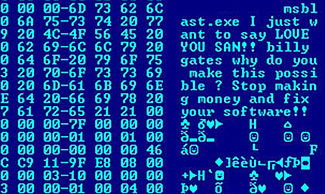
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run "windows auto update" = msblast.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run "windows auto update" = msblast.exe I just want to say LOVE YOU SAN!! bill
variants
The worm now appears in numerous variants; some of them combine the worm with Trojan horses .
This development also poses a direct threat to system security, as the worm is no longer limited to spreading itself, but rather prepares the systems for a future attack.
The worm occurs in six variants:
- option A
- B. Variant in which the worm file was renamed "penis32.exe"
- C. Variant in which the worm file was renamed "teekids.exe"
- Variant D in combination with the Trojan BKDR_LITH.103.A , which installs a backdoor
- Variant E has the names Nachi , Welchia and Lovsan.D , among others . The pest is also looking at the TCP - port 135 for vulnerable Windows systems on the Internet. Alternatively, the worm sends data over TCP port 80 in order to use the WebDAV security hole discovered in March 2003 to spread. The worm only attacks machines with Windows XP via the RPC leak, while both systems with Windows 2000 and XP are attacked via the WebDAV hole. It can be recognized massively many ICMP - Floodings the local network.
- Variant G
Web links
- Blaster: Security update for Windows XP
- Programs to remove the W32.Blaster
- Microsoft lets attack by Lovsan / W32.Blaster come to nothing
Individual evidence
- ↑ a b c Symantec: W32.Blaster.Worm. Retrieved September 1, 2018 .
- ↑ MS03-026: Buffer Overrun in RPC May Allow Code Execution. Retrieved September 1, 2018 .
- ↑ a b c 2003 CERT Advisories Page 99. (PDF) Retrieved on September 1, 2018 (English).
- ↑ Blaster worm spreading, experts warn of attack. August 12, 2003, accessed September 1, 2018 .
- ↑ a b c d All bulkheads tight - W32.Blaster attacks. August 12, 2003, accessed May 27, 2019 .
- ↑ W32.Blaster also attacks non-Windows systems. August 13, 2003. Retrieved May 27, 2019 .
- ↑ Multiple Open Software Foundation Distributed Computing Environment (DCE) implementations vulnerable to DoS. August 8, 2003, accessed May 27, 2019 .
- ↑ W32.Blaster affects hundreds of thousands of PCs. August 13, 2003. Retrieved May 27, 2019 .
- ↑ Blaster worm author gets jail time. January 28, 2005, accessed September 1, 2018 .
- ↑ Minnesota teen sentenced for releasing Blaster worm variant. January 28, 2005, accessed September 1, 2018 .
- ↑ infoworld.com
- ↑ Errors in Windows endanger Internet PCs. July 17, 2003, accessed May 27, 2019 .
- ↑ a b 2003 CERT Advisories Page 100. (PDF) Retrieved on September 1, 2018 (English).