Intrusion Detection System
An intrusion detection system ( English intrusion "penetration", IDS ) or attack detection system is a system for the detection of attacks that are directed against a computer system or computer network . The IDS can supplement a firewall or run directly on the computer system to be monitored, thus increasing the security of networks and computer systems. Detected attacks are usually collected in log files and communicated to the user or administrator; This is where the term intrusion prevention system ( English prevention "prevent", IPS ) is defined, which describes a system that automates and actively prevents attacks.
Architectures
There are three types of IDS:
Host-based IDS
HIDS are the oldest type of attack detection systems. They were originally developed by the military and were intended to guarantee the security of mainframes . A HIDS must be installed on every system to be monitored. The term “ host ” is to be understood in the sense of information technology and not as a synonym for a mainframe computer.
A HIDS must support the operating system. It gets its information from log files, kernel data and other system data such as the registration database . It sounds an alarm as soon as it detects an alleged attack in the monitored data. A subspecies of the HIDS are so-called "System Integrity Verifiers", which use checksums to determine whether changes have been made to the system.
Advantages:
- Very specific statements about the attack.
- Can comprehensively monitor a system.
Disadvantage:
- Can be undermined by a DoS attack.
- If the system is incapacitated, the IDS is also paralyzed.
Network-based IDS
NIDS try to record and analyze all packets on the network and report suspicious activity. These systems also try to identify attack patterns from network traffic . Since the Internet protocol is predominantly used nowadays , an attack must also take place via this protocol. An entire network segment can be monitored with just one sensor . However, the data volume of a modern 1 GBit LAN can exceed the bandwidth of the sensor. Then packets have to be discarded, which no longer guarantees seamless monitoring.
Advantages:
- One sensor can monitor an entire network.
- Switching off a target system does not endanger the function of the sensor.
Disadvantage:
- No complete monitoring if the IDS bandwidth is overloaded.
- No gapless monitoring in switched networks (only through mirror port on a switch).
- No complete monitoring with encrypted communication (may be able to see the data packets, but not the encrypted content)
Hybrid IDS
Hybrid IDS combine both principles in order to be able to guarantee higher coverage when detecting attacks that have occurred. In this context, one speaks of network- and host-based sensor types that are connected to a central management system. Many IDSs used today are based on such a hybrid functionality.
A hybrid IDS usually consists of the following components:
- management
- Host-based sensors (HIDS)
- Network-based sensors (NIDS)
functionality
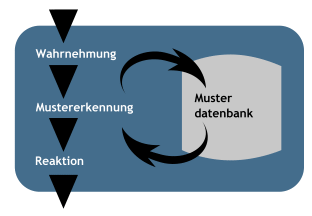
There are basically two methods of intrusion detection: the comparison with known attack signatures and the so-called statistical analysis. Most IDS work with filters and signatures that describe specific attack patterns. The disadvantage of this approach is that only known attacks can be detected.
The process is divided into three steps: The perception of an IDS is made possible by sensors that collect log data (HIDS) or network traffic data (NIDS). During the pattern recognition, the Intrusion Detection System checks and processes the collected data and compares it with signatures from the pattern database. If events apply to one of the patterns, an “intrusion alert” is triggered. This can be of various types. It can only be an e-mail or SMS that is sent to the administrator or, depending on the scope of functions, the alleged intruder can be blocked or isolated.
Other IDS use heuristic methods to detect previously unknown attacks. The aim is to detect not only known attacks, but also similar attacks or deviations from a normal state.
In practice, signature-based systems are by far the most widespread. One reason for this is that their behavior is easier to predict. A major problem with the practical use of IDS is that they either generate many false warnings ( false positive ) or fail to detect some attacks ( false negative ).
Instead of just triggering an alarm like an IDS, an intrusion prevention system ( IPS for short ) is able to discard data packets, interrupt the connection or change the transmitted data. A connection to a firewall system is often used here, through which certain rules defined by the IPS are applied.
Newer IPS / IDS designs often work with a combination of stateful inspection , pattern matching and anomaly detection. This allows deviations from the protocol specification specified in the RFC standard (Request for Comment) to be identified and prevented.
In addition, efforts towards such systems are also evident in other areas, such as the protection of telephone systems through intelligent, signature-based intrusion detection.
disadvantage
- Since an intrusion detection or intrusion prevention system is usually an active component, there is a possibility that it could be used as a target. Intrusion detection or intrusion prevention systems that can be integrated in-line - that is, without a bound IP stack and IP addresses - into a network and work as transparently operating Layer 2 network components are only from this danger limited affected.
- In contrast to intrusion prevention systems , attacks are only detected but not prevented.
Honeypot
A honeypot (bait) is a computer on the network that is designed to trick hackers into attacking it. This computer does not contain any important data or services that are used regularly. It only serves to direct attacks to an isolated part of the network by deliberately leaving security holes open. If activity is detected on this computer, it is most likely an attack. In addition, a honeypot can be used to find out more about the attacker's approach. Defense strategies for the rest of the network can then be derived from the observed attacks. The honeypot is thus another component of the IDS. However, the concept of the honeypot has one disadvantage: A honeypot can serve as an entry point to carry out further attacks on the network.