Layer architecture
The layer architecture (also layer model or layer pattern) is a frequently used structuring principle for the architecture of software systems . Individual aspects of the software system are conceptually assigned to a layer ( tier or layer ). The permitted dependency relationships between the aspects are restricted in a layer architecture to the effect that aspects of a higher layer may only use those of lower layers. A system with a layered architecture is also referred to as “multi-layered”.
The aspects assigned to the layers can, depending on the type of system or the level of detail of the consideration, e.g. B. functionalities, components or classes .
Classifications
There are different ways of designing a layered architecture:
- In the case of a strict or closed layer architecture ( strict layering , closed architecture ), no layers may be skipped and only the next lower layer may be called. In this way, a high level of flexibility is guaranteed, since if a layer is changed, in the worst case scenario, adjacent layers have to be adapted (but not the entire system); the individual layers are therefore easier to test and maintain. One speaks of direct addressing.
- With a non-strict or open layer architecture ( loose layering , open architecture ), a layer can call any lower layer. One advantage is that open systems are often more efficient than closed systems, since the data does not have to be passed through layers in between. However, this then leads to a higher degree of coupling of the layers in contrast to the i. d. Usually only loosely coupling is desired ( loose layering ). This type of addressing is also called indirect addressing.
- There are also systems in which the individual layers communicate with the layers above and below. The best known example of this is the ISO / OSI model .
Layer architectures are often divided according to the number of layers used. In the case of application systems, different application-dependent layer architectures are used.
Advantages and disadvantages
A layer architecture reduces the complexity of the dependencies within the system and thus a lower level of coupling with higher cohesion of the individual layers. In particular, this avoids cycles in the dependency graph. This has advantages for both understanding and maintenance of the system. In addition, individual layers can be easily exchanged without having to change the entire system.
A disadvantage of a layer model can be that the execution speed of the application is reduced by the code written over a layer for forwarding and transforming data. This is noticeably the case in particular with those parts of the application for which the data in lower layers would be structurally better suited than in the layers to which they are allowed to access. A prominent example of this are reports that display aggregates of data such as sums or average values. In these cases, the named application parts often do without the advantages of the layer architecture in favor of the execution speed.
Layer architectures according to the number of layers
Two-tier architecture
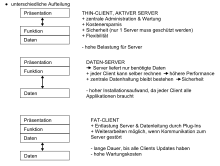
The two-tier architecture consists of two layers. Since only the higher layer is allowed to access the lower layer, the lower layer is a service provider (English server ) of the higher. One therefore often speaks of a client-server architecture .
Client-server architectures do not necessarily have to be implemented using different computers; rather, the client can also be understood as a software module that accesses a second software module on the same computer, usually within the same application. The example given in the figure, however, uses a computer-side client-server architecture.
With architectures as shown in the figure, the computing capacity is largely outsourced to the client computers in order to relieve the server. Traditionally, a fat client and a fat server are used. A database application is running on the server . The clients take on the logic and display of the user interface .
Three-tier architecture
The three-tier architecture is an architecture that has three layers on the software side. In contrast to the two-layer architecture, the three-layer architecture has an additional layer, often the logic layer, which handles the data processing.
A typical three-tier architecture consists of the following layers:
- Presentation layer ( client tier ) - This, also known as the front end , is responsible for the representation of the data, user input and the user interface .
- Logic layer ( application server tier , business layer, middle tier or enterprise tier ) - it contains all processing mechanisms. The application logic is united here.
- Data storage layer ( data server tier , back end ) - It contains the database and is responsible for saving and loading data.
Three-tier architectures in distributed systems
Multi-layer system architectures such as the three-layer architecture are easily scalable, as the individual layers are logically separated from one another. So z. For example, in the case of distributed system architectures, the data layer runs on a central database server, the logic layer on workgroup servers, and the presentation layer is on the respective workstation of the user. An example of a distributed three-tier architecture is Citrix : Interaction: Client; Function: Citrix Server; Data: database server .
As the graphic shows, there are various options for distributing the layers between client and server. Basically, the higher (closer to the presentation layer) the layer, the more likely it will be processed by a client. The deeper (closer to the data layer) the layer, the more likely it is to be the task of a server.
Three-tier architectures within software systems
The architecture can also be implemented within a software system by assigning the software modules, which are responsible for presentation, application logic and persistent storage of data, to the individual layers and decoupling them from one another according to the layer division. In addition to structuring according to the Model-View-Controller architecture pattern, such a three-layer architecture is usually considered the minimum level of architectural structuring, unless there are compelling reasons for other architectural decisions.
More layers
In addition to the layers mentioned above, other classifications are used in various sources. A layer architecture basically describes an architecture pattern that is not restricted in terms of the type and number of layers. The following layers are very often found in software systems as well as in distributed applications:
- application
- Applications are further divided into:
- Dependency injection
- Application presentation
- Business logic
- Data access
- control
- Data presentation
- Data storage
Further details on the individual layers are described in the section Classic layers within a multi-layer architecture .
An example of a seven- tier architecture is the ISO / OSI model shown in the figure on the right. The OSI model describes the division of the network stack, but not the division within an application.
Classic layers within a multi-layer architecture
Dependency injection
The dependency injection layer is the top layer in applications. It is completely transparent for the clients of the application and serves to provide all objects required by the application. Applications that do not use a DI layer have the service locator - anti-pattern or even strong dependencies and only offer limited validation and testability.
Presentation layer
The presentation layer (Engl. Client layer or presentation layer ) is responsible for the presentation and acceptance of the software processed data, and the functions provided by the software.
In distributed systems, there are two alternatives for displaying the content:
- The web browser is used as a thin client and the content and forms are displayed in XHTML , XML , JavaScript and other languages created for the World Wide Web , thus using a classic " web application ". Communication with lower layers usually takes place via HTTP .
- You produce your own graphical user interface as a fat client . This uses the extended display options of the programming language or graphics library such as Flash , Java Swing or XAML . This communicates with the application layer via network protocols such as SOAP , Java RMI or Microsoft .NET Remoting .
Control layer
The control layer ( process layer ) is used to coordinate several functionally separated parts of the business logic layer .
In the case of a service-oriented architecture , for example , the orchestration takes place here . Often, the control layer is also responsible for transaction control .
Business logic layer
The business logic layer (also processing layer , application logic layer, domain layer , application layer or middle tier ) realizes the actual business model by implementing the business objects involved in the business model with the associated logic.
Data access layer
The data access layer encapsulates the access to persistent data and the techniques used for it.
Databases are often used for persistent storage, but normal files can also be used with other systems .
When using databases, database interfaces and, alternatively, direct access to the DBMS (database management system) are used for data exchange with the data storage layer (e.g. with PHP). When using object-oriented programming in conjunction with a relational DBMS in the data access layer is an object-relational mapping ( object-relational mapping , ORM) is required, which is often implemented by the use of an ORM frameworks.
Further applications of layered architectures
Layer model in operating systems
A layer model , also known as a shell model , is one of three essential architectural models of operating systems. In addition to the monolithic kernel and the microkernel, there is the layer model. In the layer model, the various operating system components are built on top of one another like shells. This can also be seen in the illustration opposite.
The transitions between the layers are formed by interfaces, whereby the transitions must be clean, there are no jumps (e.g. from an application program directly into the data structure). Communication takes place via the interfaces of each individual intermediate layer.
In general, one can say that the closer a layer is to the hardware, the more privileged it is with regard to write and read permissions. The transition from kernel mode to user mode can be difficult to define.
- See also: Ring (CPU)
Traceability
End-to-end tracking of communication between the individual layers is becoming more and more important in complex systems and can be implemented by the Application Response Measurement Standard using correlated transactions of each layer.
See also
- Application server
- Architectural pattern
- Client-server model
- IT architecture
- Model-View-Controller
- Orchestration
- Service-oriented architecture
- Distributed system
- Web service
- ISO / OSI model
Web links
- "Three-Tier-Development" by Manfred Rätzmann
- 3-tier architecture with .NET (video + howto)
- Description of a concrete layer architecture for .NET / WPF rich client applications (English)
Individual evidence
- ^ Frank Buschmann et al .: Pattern-Oriented Software Architecture: A System of Patterns, John Wiley & Sons, 1996.
- ^ Frank Buschmann et al .: Pattern-Oriented Software Architecture: A System of Patterns, John Wiley & Sons, 1996.
- ↑ Daniel Baharestani: Mastering Ninject for dependency injection . Packt Publishing, ISBN 978-1-78216-620-7 (English, 142 pages).