Wassenaar Agreement
The Wassenaar Arrangement on Export Controls for Conventional Arms and Dual-Use Goods and Technologies ( english The Wassenaar Arrangement on Export Controls for Conventional Arms and Dual-Use Goods and Technologies ) is an international, non-binding agreement and successor to the COCOM .
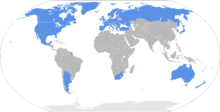
It was drawn up on December 19, 1995 in Wassenaar ( Netherlands ) and signed by 33 founding members on May 12, 1996 in Vienna ( Austria ). Similar to CoCom, lists of armaments-related goods are maintained. The states decide independently about the approval or rejection of delivery requests from third countries , but inform the other member states via the office in Vienna. This is to prevent rejected requests from being approved by other member states.
With Regulation (EC) No. 428/2009 (Dual Use) , the European Community included the list in its common commercial policy on May 5, 2009. Together with the Foreign Trade Ordinance , it thus forms the effective basis of German export controls in Germany .
40 member states signed the agreement: Argentina , Australia , Belgium , Bulgaria , Denmark , Germany , Estonia , Finland , France , Greece , Great Britain and Northern Ireland , Ireland , Italy , Japan , Canada , Croatia , Latvia , Lithuania , Luxembourg , Malta , New Zealand , Netherlands , Norway , Austria , Poland , Portugal , Romania , Russia , Sweden , Switzerland , Slovakia , Slovenia , Spain , South Africa , South Korea , Czech Republic , Turkey , Ukraine , Hungary , USA .
Mexico became the 41st member state on January 25, 2012 .
Consideration of information technology dual-use goods
With the revision of 2013, the agreement also regulated software as a potential defense technology for the first time. In the version valid since March 2015, u. a. "Infiltration software" (intrusion software) listed as dual-use good and defined as software that was specially designed to circumvent monitoring tools and defense systems of computers and computer networks and enables data to be diverted or manipulated in systems of this kind. The manipulation of program sequences to make them vulnerable to external commands is also mentioned.
Publicly available software (e.g. open source projects or retail products) and cryptographic software, the primary function of which is to protect information, are explicitly not affected by the agreement.
Web links
- Website of the Agreement (English)
Individual evidence
- ↑ Christopher Kuner, Jörg Hladjk, in: Hoeren / Sieber / Holznagel (ed.) “Multimedia-Recht” 39. Supplementary delivery 2014, part 17 Legal problems of cryptography, marginal no. 17 f.
- ^ The Wassenaar Arrangement. Second corrigendum to the list of dual-use goods and technologies and ammunition list. (PDF; 1.4 MB, as of February 17, 2019).