Advanced Access Content System
The Advanced Access Content System ( AACS ) is a digital rights management (DRM) which is used for recordable and pre-recorded optical media.
The AACS, also known as copy protection used was by the companies Intel , Microsoft , Panasonic , Sony , Toshiba , Walt Disney and Bros. Warner developed.
The organization responsible for issuing licenses for AACS is called the Advanced Access Content System License Administrator (AACS LA) .
Main functions
AACS tries to combine the core elements of CSS , which failed due to the proprietary encryption algorithm, with cryptographic algorithms to create a new copy protection system for prerecorded and recordable data carriers.
Components for this are:
- Encryption of all content with AES 128-bit encryption
- a significantly expanded rights management (defined in the licensing guidelines)
- License key management, d. h., z. B. "protected" copies with limited playability (temporally or on certain drives) can be created
- Ability to block license keys
- Drive verification by hardware key
- encrypted communication between all components
- Network connection or internet possible
- The content can be activated via the Internet
- Expandable list of compatible copy protection systems with precise details of the transfer of rights (e.g. between AACS and the DRM systems from Microsoft).
The aim of AACS is not to make high-resolution video content “unprotected”, ie not to make publicly accessible without encryption and without digital rights management. This goes over the previous copy protection z. B. a DVD and means a completely closed digital rights management.
AACS does not only affect pre-recorded media and online content e.g. B. from media servers, but should also extend to high-resolution recordings from television broadcasts, even those that are sent without encryption, ie "free-to-air".
In addition, AACS also wants to overcome the “one-way street” of copy protection and prevent copy protection from becoming a “dead end” for digital data when new interfaces and transmission methods are developed that were not yet included in the original version of copy protection.
realization
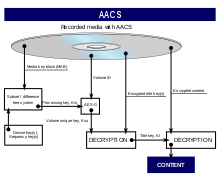
AACS is designed as a complete rights management for video data. All content is encrypted using AES-128 . The associated key is determined by the player from its own device key block and one of the media key blocks on the medium. In the case of pre-recorded media, the media key block is the same for all copies. In the case of blank media, each medium has its own, individual media key block, so that the recording device must generate its own encryption for each blank medium, which includes the media key block of the medium.
This prevents any number of films recorded on blank media from being copied and played on any device (recordings on a DVD-R, for example, are not encrypted and are not subject to any rights management).
The key management works together with the rights management. The aim is that the customer with the AACS-encrypted content receives similar freedoms as z. B. within his household for unencrypted content on z. B. VHS tape apply. However, restrictions are conceivable as to which devices the copies can be played on and how long they can be played at all (for this the signal source would have to provide appropriate DRM control signals, which is currently not the case).
AACS should also make it possible to send protected (encrypted) content over a network, provided that the sender and recipient have the appropriate licenses. This assumes that the transmission is again encrypted. For example, Microsoft plans to provide such functionality with its Windows Media Server. One possible protection method for the transmission of the content over a network is DTCP .
In order for a PC to be able to play AACS-protected content, at least one AACS-licensed playback program must be available in addition to an AACS-compatible drive ( HD DVD or Blu-ray Disc ). Its ability to run or the ability to play high-resolution films "secured" with AACS can again depend on various criteria such as the encrypted PCIe bus , HDCP-compatible graphics card and the appropriate operating system with appropriate patches.
Analog outputs for the video signal can either be scaled down to lower resolutions (PAL / NTSC) or switched off completely by the rights management at any time.
This even goes so far that AACS in the version from 2009 defines an "analog sunset", i.e. a period within which AACS-licensed devices can still be certified or produced and sold with analog output signals: Only until 2010 was it possible to output the image in high resolution via component outputs (corresponding devices were only allowed to be sold until 2012). Since 2013 it has not been possible to license a device with analog image outputs in SD quality (USA and Japan: NTSC, rest of the world: PAL). The sale of such devices will also cease after 2015. From 2015, new AACS devices will only be available for purchase with digital image outputs encrypted via HDCP.
In order for AACS to work properly, all components, from the set-top box to recording devices to playback devices, must be capable of AACS (or copy protection systems compatible with AACS). All components must be licensed from AACS LA (or the licensors of the compatible copy protection systems) and, ultimately, AACS must also function properly in the interaction of the components.
The AACS behind it is responsible for a large part of the planned rights management features of HD DVD and Blu-ray Disc, such as the planned revocation list and any restrictions on image output.
Media support
The use of AACS as a DRM system for the stored media data is currently mandatory for the following HDTV recording formats:
The AVCHD recording format is not affected by AACS . This format actually corresponds to the file format in which HD DVD and BluRay build their file structure. In plain language, this means that stand-alone devices in HD DVD and Blu-Ray format must record with AACS, but a PC can also store the same data on a corresponding drive in AVCHD without AACS.
criticism
From the user's point of view, AACS has the fundamental point of criticism that it is a comprehensive DRM. That means:
- Unlike earlier systems, the "protection" of AACS does not only extend to prerecorded data carriers, but rather formats (without the user being able to do anything about it) also previously unprotected formats (such as free-to-air television broadcasts) are packaged in the DRM system as soon as a recording is started on a corresponding AACS-compliant device.
- In order not to let content once in the DRM (i.e. high-resolution video) get out of the rights management, the obligation to use HDCP as "protection" at the video and audio output of the playback systems means older systems such as HDTV screens and A / V systems actually locked out or only supplied with inferior signals. This restriction is currently only available on request of the content, but from around 2016 at the latest, newly manufactured devices may no longer have analog signal outputs.
- In addition, special data blocks are provided in the AACS to control HDCP outputs. This means that analog outputs can be switched off and blacklists of HDCP device IDs that were subsequently blocked can even be transferred.
- With AACS there is a risk that a legally acquired player can no longer play AACS-protected media at any time without the influence of the owner, as soon as this device has been blacklisted by the AACS LA. This is because each device is provided with a device key, which is required to decrypt the protected data. With this key, devices that have been cracked for any reason can be identified at any time and retrospectively made unusable. Each data carrier contains a black list with device keys that are no longer permitted; this list can be updated by the AACS LA at any time: As soon as a user inserts a new data carrier with a current black list, on which his device is no longer permitted, into his player, the device is branded as prohibited and made unusable for playback. This last step then means that older data carriers that were previously played without problems can no longer be played on this device. It should be noted that the end user has no control over whether the device key of his own playback device is cracked by another person anywhere in the world, since the device key can appear in a series of several devices of the same type.
- In contrast to the CSS of the DVD, AACS software players do not receive a permanent key for use on computers, but the player keys of the playback software have to be renewed approximately every 1.5 years. This makes it z. For example, it would be impossible to receive HDTV content on an analog monitor connected via VGA after 2011, as playback devices certified after 2010 are no longer allowed to offer this functionality.
Copy protection problem in the area of HDTV
HDCP has already shown that the industry sometimes needs years before cryptographic copy protection is implemented in a reasonably usable form (HDCP dates from 1999, and it took until 2005 for device manufacturers to receive the first HD ready seal of approval that explicitly documented HDCP at at least one input). Assuming that the HD systems ( HD DVD and Blu-ray Disc ) offered from spring 2006 will be the first implementations of AACS, it can be assumed that the buyers interested in HD content will not only have high costs for the new developed devices will also feel the inconveniences of the initial implementations of AACS, and with complete DRM systems there is always the risk that devices that are already licensed will lose their licenses for reasons beyond the customer's control and thus become useless for the user.
The next thing is that there are already approaches for a form of “digital rights control” in the field of high-definition video that is completely independent of AACS: TV stations that force their customers to close a set-top box that is sensitive to a broadcast flag for reception use, lock when broadcast e.g. B. of a movie the analog outputs or scaling them down to SDTV quality. The HDTV signal then only comes via a digital output that is encrypted via HDCP, but which generally may not be recorded.
If the large film studios were to assert themselves with their intention of binding the granting of broadcasting rights for HDTV transmissions of feature films to the transmission of a "broadcast flag", recording devices for HDTV content would generally be questionable: Only unprotected transmissions such as news programs or sporting events would be questionable then record yourself in high resolution. Even an HDTV recording device with AACS support will not be able to record HDCP-encrypted content of a digital image transmission, since HDCP lacks the necessary rights management, because activated HDCP corresponds to the authorization level “may not be recorded”.
Only receiving devices with an AACS-compliant digital signal output could then possibly deliver a recordable signal, but here, too, it is questionable how a receiving device then sets the rights settings within the AACS transmission to the recording device in view of a set broadcast flag or whether it is possible in view of the possibility to install a hard disk in the receiving device, there will generally be devices with an AACS-compliant digital video interface.
Dispute over the "perfect" copy protection between HD DVD and Blu-ray
Around the summer of 2005, the tide seemed to be turning between the two competing formats in favor of the cheaper HD DVD. In order to get more studios on his side, a race broke out for better copy protection between HD DVD and Blu-ray Disc: After BD initially came along without any copy protection (PC drives and standalone devices of the first generation that were only sold in Japan and recorded exclusively in MPEG2), it was initially announced by the relevant manufacturers that Blu-ray would also work with AACS as copy protection.
The Blu-ray Disc Association is not even satisfied with the restrictions on HDTV playback within AACS at the time: They also implement executable Java applets on the Blu-ray Disc in their BD + system . These programs run on the player hardware or - Software in a virtual machine and check in the background whether the output stream has been manipulated. If BD + detects a change, the output is canceled. However, BD + does not make any changes to the hardware or software of the player. The first discs with BD + were released during 2007. In March 2008 the manufacturer SlySoft released AnyDVD HD, the first software that can bypass this protection.
BD + is not directly a component of AACS, but is a copy protection that is specific to BD players. However, there is the possibility that BD + and AACS complement each other in order to make it more difficult to bypass the copy protection. AACS also goes into some details of the implementation on BD players on BD +.
Delays in the copy protection standard and "analog sunset"
The potential enhancements to AACS have long meant that the final version of the standard had not yet been passed, although HD DVD and Blu-Ray players were already being built and sold. The corresponding devices were certified according to a preliminary standard.
Because, despite the intention of the rights holder in the USA, shortly before legal effect, the corresponding FCC directive for the forced introduction of a broadcast flag was overturned in summer 2005 and to address the problem of the still unsuccessful introduction of HDCP inputs on all HD television sets sold around, the AACS LA decided to allow the preliminary version 0.9 of the AACS specification with an analog output. This will initially contain the analog copy protection called CGMS-A (a kind of " Macrovision for HDTV") in devices built from autumn 2007, devices certified from 2010 will only be allowed to output SDTV on analog outputs, and from 2013 certified devices will not be any analog Allow more signal output. This regulation can be found in the AACS specification with the title "analog sunset" and corresponds to the intention of the US film industry to ban analogue signal outputs that are branded as too easy to copy.
The final version of AACS wasn't released until 2009 (four years after HD DVD and BD were launched). It stipulated that from 2014 onwards, BD players containing analog video outputs may no longer be sold (analog component outputs will no longer be operated with HDTV resolution as of 2011).
Summary of the criticism
In summary, with the introduction of AACS, the motion picture industry and device manufacturers plan to gain de facto full control over the video recording and playback devices that are owned by private individuals. Controlled solely by control signals in the data stream of the high-resolution images, the recording devices would then refuse to take a picture or only record in a lower resolution or even completely set the functions of the devices. The rights holders could also influence how long a recording can be played back. These restrictions cannot be reversed as long as the content is protected by AACS. However, AACS is designed in such a way that the protection is maintained to the greatest possible extent, even across system boundaries. B. there is no longer any analog image output.
What AACS completely lacks is a reliable way for the user to permanently access the content protected in AACS in high resolution quality: There is no reliable interface via which content packaged in AACS can be output in full quality to devices that neither HDCP still know AACS. This applies to both video and audio data.
By using an encryption method that is very secure with AES-128, it is also very unlikely that AACS will ever be hacked as extensively as the CSS of the DVD was. However, individual "hacks" of software players or playback devices can be neutralized by placing the relevant key on the AACS revocation list. In the best case scenario, the software of these devices must be exchanged for a "safe" version again within a certain period of time so that the device or program still works at all - if the manufacturer is sentenced to a fine for violating the license provisions or goes bankrupt, however this generally means the end for the devices concerned, the customer would then be left behind.
Due to the time-limited key assignment to software players (the validity of the keys of hardware players does not seem to be limited in time) the user is in fact also forced, e.g. B. replace PC components when the new version of the software player z. B. no longer wants to work with an older operating system version or with a specific drive or graphics card.
Attacks on AACS
At the end of December 2006, a programmer with the pseudonym "muslix64" succeeded in bypassing the AACS copy protection. However, the protection is not cracked, but only bypassed - because the files are apparently copied together with the original keys. He was able to determine the "Title Keys" required for decryption through an error in a software player. This stores the title keys unencrypted in the main memory of the computer. A Java program "HDDVDBackup" written by him decrypts the material with the title keys found and copies it to the hard drive. This is currently possible with the media HD DVD and Blu-ray Disc .
The program still needs the previously determined keys of the media, but from the next version it should be able to determine them itself. So far, the hack has only been documented by a video entitled "AACS is unbreakable". According to the hacker, it only took eight days to bypass the AACS protection.
According to the programmer, the ability to decrypt the data material will be retained, even if the software player's permission to decrypt it should be withdrawn by placing it on a revocation list. The program was published in 2007.
On January 28, 2007 the individual keys of the various films were found. This message was confirmed by the manufacturers and the studios.
On February 14, 2007, “Arnezami”, a forum member of the Doom9 website, claimed to have discovered a universal key for the HD-DVD and Blu-ray formats. He was able to show that both Blu-ray media and HD-DVD discs use one and the same "Processing Key".
All AACS-related hacks can currently compromise certain media or playback devices or playback programs, but are not so advanced that the copy protection itself would be as ineffective as z. B. is the case with CSS for DVD video.
The background to this is that, in contrast to CSS, AACS did not create a new encryption standard that turned out to be faulty and easily attackable in retrospect, but instead uses a cryptographically tested and widely recognized encryption with AES , so that only errors in the design of AACS ( which, apart from the general design problems with DRM, have not yet been found) or can be exploited in the implementation for a hack.
Implementation errors are e.g. B. the use of a uniform processing key for all current Bluray publications as well as the unprotected transfer of the disc ID (contrary to the AACS license conditions) with the HD-DVD drive of the Xbox 360 .
Several programs (e.g. AnyDVD HD , DVDFab Blu-ray to Blu-ray ) currently claim to be able to bypass the AACS protection for all HD media currently on the market.
Individual evidence
- ↑ https://www.heise.de/newsticker/meldung/Blu-ray-Player-ab-2014-ohne-analogen-Videoffekt-181154.html
- ↑ The key to Hollywood - Attack on the HD copy protection AACS - AACS is unbreakable. Retrieved April 5, 2014 .
- ↑ Bernd Kling: AACS decrypted? December 28, 2006, archived from the original on June 17, 2009 ; Retrieved April 5, 2014 .