Locator / Identifier Separation Protocol
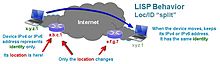
Locator / ID Separation Protocol ( LISP ) is a routing architecture that separates identity and whereabouts. This applies schematically to the topic of Internet Protocol (IP). An IPv4 address contains identity and location within a 32-bit address. So it's complicated to just take an IP address with you.
history
In October 2006, the Internet Architecture Board again brought its interest up for discussion within a routing and addressing committee. The aim should be to support designs that optimize the requirements for highly scalable routing tables and addressing in the Internet. A fundamental problem was the flooding of the current IPv4 routing table learned via BGP . So far, many proposals have been made to resolve the issue, and all of them are based on the location and identity division in the numbering of the Internet, often called the "Loc / ID split".
example
Person A is in a location east. The identity is A and the location is East. If this person A changes location, for example to location West, then it is still person A.
In the course of IP, the end device changes its IP address, as in the example above; Terminal A has the IP address 192.168.1.1 in the East location. If terminal A now changes to location West, it is assigned an address from the IP subnet of location West via DHCP, for example 10.1.1.1 - so the location and the identity have changed.
The result is that 1. the identity is lost and 2. all IP connections expire.
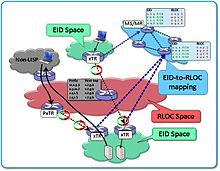
Due to the separation of “Endpoint Identifier” (EID = identity) and “Routing Locator” (RLOC = location) given in LISP, an end device can retain its identity. In order to find the location of a device or a subnet, you need a database that connects EID and RLOC, the so-called mapping system. This mapping system is similar to DNS.
An EID can be a host IP address or an entire IP subnet.
An RLOC is usually the IP address of the interface of a LISP-activated router via which it can be reached, for example from the Internet or from an MPLS network.
By separating identity and location, different scenarios can be transmitted: The simple ones are, for example, encapsulating IPv6 host packets in IPv4 headers and vice versa. IPv6 islands or entire IPv6 sites can be connected via IPv4 networks in order to facilitate and accelerate migration. Alternatively, non-IP packets can also be transmitted via LISP. This includes geo-coordinates, MAC address , and RFID .
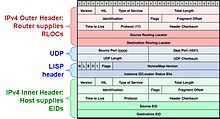
Packets between two LISP locations are packed in a special LISP UDP header.
Current internet protocol architecture
The current name used by the Internet Protocol is called the IP address , which has two separate functions:
- As an endpoint ID to uniquely identify a network interface within a local network
- As a locator for the routing process. This should give the possibility to find an end point in the network, even in large routing environments
Advantages of LISP
The following advantages result from the separation of location and identity and thus for LISP:
- Greatly improved scaling in large routing environments
- BGP -free multihoming in "active-active" environments
- Address family transport: IPv4 over IPv4, IPv4 over IPv6, IPv6 over IPv6, IPv6 over IPv4
- Incoming traffic management and load sharing
- mobility
- Easy to configure and distribute (including coexistence with all other IP technologies)
- No changes to the end devices necessary
- VPN support, for example VPN as a tunnel over MPLS networks
- Network virtualization
- Customer-operated and encrypted VPN environment based on LISP / GETVPN solve IPsec scaling problems
- Highly available and seamless communication is addressed with active multihoming and a change in the data packet is signaled.
Definition of terms
- Routing Locator (RLOC): An RLOC is an IPv4 or IPv6 address from an egress tunnel router (ETR). An RLOC is the outgoing interface based on the resolution of the EID-to-RLOC mapping.
- Endpoint ID (EID): An EID is an IPv4 or IPv6 address that is used in the source and destination address fields. It is used inside (first header) of a LISP packet. Usually it is the IP network of the location end devices.
- Egress Tunnel Router (ETR): An ETR is a router that accepts IP packets where the destination IP address in the outer header is its own RLOC. It normalizes LISP packets to native IP packets. An ETR can also be a device other than a router - for example a mobile device.
- Ingress Tunnel Router (ITR): An ITR receives IP packets from a sender within the EID network and packs them into LISP packets. He enters the ETR RLOC on the opposite side as the destination in the outer header.
- Proxy ETR (PETR): A PETR is used for communication between LISP and non-LISP locations. On the LISP side it works like an ETR on the non-LISP side like a native IP router.
- Proxy ITR (PITR): A PITR is used for communication between non-LISP and LISP locations. It behaves like an ITR in the LISP network and like a native IP router on the non-LISP side and has to announce the LISP networks to the non-LISP network.
- xTR: An xTR is the name of a component on which the ITR and ETR functions are mapped simultaneously. It is also called the tunnel or encapsulation endpoint.
The LISP mapping system
One element in the Locator / ID Separation Protocol is the mapping system. This has the task of connecting EID and RLOC. This process is not visible on the internet or transport network. The assignment is organized in a distributed database that reacts to requests from ITR devices. An ETR must log on to the mapping system and enter its status.
The following terms are used in the mapping system:
- MAP server (MS): The MAP server is filled with information from the ETR devices and it saves the assignment of EID to RLOC. In addition, he is responsible for forwarding requests from an ITR to the ETR based on his database.
- MAP resolver (MR): The MAP resolver accepts requests from ITR devices to resolve the target location and forwards them to the MS.
Uses
With LISP, many existing solutions and options can be combined under one architecture and, in addition, completely new usage options in the network can be derived. Which are described here in the following.
- VPN (Virtual Private Networks) with very large scaling
- Migration from IPv4 to IPv6
- VM or host mobility
- Location based inbound load distribution of IP traffic
- LISP Mobile Node - Support of the LISP function on mobile devices
Available software
- Cisco has IOS and NX-OS software with LISP support in official releases.
- Development teams from the Université catholique de Louvain and T-Labs / Technische Universität Berlin have written a FreeBSD stack called OpenLISP.
- LISPmob is an open source implementation for LISP Mobile Node and its specification for Linux and OpenWrt , which is maintained by Universitat Politècnica de Catalunya . It can be used as an xTR or LISP mobile node.
- AVM GmbH offers LISP support for the Fritz! Box routers from FRITZ! OS 06.00 and in some laboratory firmware versions
standardization
This architecture was standardized by the IETF under the title LISP (Locator / ID Separation Protocol) in the following RFCs:
| RFC | description |
|---|---|
| RFC 6830 | The Locator / ID Separation Protocol (LISP) |
| RFC 6831 | The Locator / ID Separation Protocol (LISP) for Multicast Environments |
| RFC 6832 | Interworking between Locator / ID Separation Protocol (LISP) and Non-LISP Sites |
| RFC 6833 | Locator / ID Separation Protocol (LISP) Map-Server Interface |
| RFC 6834 | Locator / ID Separation Protocol (LISP) map versioning |
| RFC 6835 | The Locator / ID Separation Protocol Internet Groper (LIG) |
| RFC 6836 | Locator / ID Separation Protocol Alternative Logical Topology (LISP + ALT) |
Active draft RFCs
| Draft | description |
|---|---|
| draft-ietf-lisp-architecture-00 | An Architectural Perspective on the LISP Location-Identity Separation System |
| draft-ietf-lisp-ddt-00 | LISP Delegated Database Tree |
| draft-ietf-lisp-deployment-06 | LISP Network Element Deployment Considerations |
| draft-ietf-lisp-eid-block-03 | LISP EID block |
| draft-ietf-lisp-introduction-00 | An Introduction to the LISP Location-Identity Separation System |
| draft-ietf-lisp-lcaf-01 | LISP Canonical Address Format (LCAF) |
| draft-ietf-lisp-mib-08 | LISP MIB |
| draft-ietf-lisp-sec-04 | LISP Security (LISP-SEC) |
| draft-ietf-lisp-threats-03 | LISP Threats Analysis |
Web links
- http://lisp.cisco.com/
- http://njedge.net/
- https://www.ict.tuwien.ac.at/lva/384.081/LISP_TU-Wien_v3-0.pdf
Individual evidence
- ^ IETF ID draft-meyer-lisp-mn . Retrieved September 13, 2011.
- ↑ Support for the Locator Identifier Separation Protocol (LISP) . Archived from the original on September 26, 2013. Info: The archive link was automatically inserted and not yet checked. Please check the original and archive link according to the instructions and then remove this notice. Retrieved September 27, 2013.
- ↑ FRITZ! OS 6.0 from AVM makes the home network smarter . Archived from the original on November 4, 2013. Info: The archive link was automatically inserted and not yet checked. Please check the original and archive link according to the instructions and then remove this notice. Retrieved November 3, 2013.