Encryption
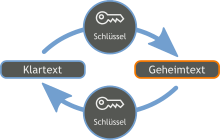
Encryption (also: ciphering or cryptography ) is the conversion of "clear text" called data into a " ciphertext " (also called "cipher" or "ciphertext"), depending on a key , so that the clear text from the ciphertext can only be obtained using a secret Key can be recovered. It is used to keep messages secret, for example to protect data against unauthorized access or to be able to transmit messages confidentially.
Basics
The encryption
Encryption converts a “plain text”, ie a clearly legible text, into a “ciphertext”, ie an incomprehensible string of characters. The terms plain text and ciphertext have grown over time and should be seen symbolically. In addition to text messages, other types of information can also be encrypted, such as voice messages, image recordings or the source code of programs. The underlying cryptographic principles remain the same.
Coding (also: coding) is a special and relatively simple type of encryption . As a rule, it is not individual plain text characters or short character combinations that are encrypted, but entire words, parts of sentences or entire sentences. For example, important commands such as “Attack at dawn!” Or “Withdraw from the hills!” Can be assigned to specific code words or incomprehensible combinations of letters, numbers or other secret symbols. This is mostly done as a tabular list, for example in the form of code books . To increase the cryptographic security of codes, the secret texts obtained with them are often subjected to a second encryption step. This is known as over-encryption (also: over-encryption ). In addition to secret codes, there are also open codes, such as Morse code and ASCII , which are not used for cryptographic purposes and do not represent encryption.
The key
The key parameter in encryption is the "key" . The good choice of a key and its secrecy are important prerequisites for keeping the encrypted secret. In the case of coding, the code book is the key. In the case of most of the classic and also some modern methods of encryption, it is a password (also: password, key word, code word or code word, slogan, slogan or slogan from Italian la parola “the word "; English: password ). With many modern types of encryption, for example email encryption, the user is now spoiled for choice when it comes to choosing a key. The key is generated automatically without his noticing. This also eliminates the “human factor”, namely the often too careless choice of an insecure password that is too short and easy to guess.
The decryption
The reverse step to encryption is decryption . The authorized recipient recovers the plain text from the ciphertext. A secret key is required for decryption . In the case of symmetrical encryption methods , this is the same as for encryption, but not in the case of asymmetrical methods . If the key is lost, the ciphertext can no longer be decrypted. If the key falls into the wrong hands, third parties can read the ciphertext, so the secret is no longer kept. A summary term for encrypting and / or decrypting the keys .
The deciphering
The term “ decipherment ” must be linguistically separated from decryption . When deciphering the art is referred to wrest his secret message to the ciphertext, without being in possession of the key. This is the work of a cryptanalyst , often called "code breaker" (Engl .: Codebreaker called). In the ideal case, no decipherment is possible because the encryption method is sufficiently "strong". It is then called “unbreakable” or at least “cryptographically strong”. In contrast to “strong encryption”, “weak encryption” can be broken without prior knowledge of the key using cryptanalytical methods with reasonable effort . With advances in cryptology, supposedly strong encryption can prove weak over time. For example, the “ Vigenère encryption ” was known for centuries as “Le Chiffre indéchiffrable” (“The indecipherable encryption”). We now know that this is not the case.
The field of work that deals with the deciphering of ciphertexts is cryptanalysis (older term: cryptanalysis). Alongside cryptography, it is the second branch of cryptology. The cryptanalysis is not only used for the unauthorized deciphering of secret messages, but it also deals with the “(im) breakability” of encryption, i.e. checking the security of encryption methods against unauthorized deciphering.
Most encryption methods are only pragmatically secure , which means that no practicable way of deciphering them was found during their cryptanalysis. The longer a method has been publicly known and the more widespread it is in use, the more justified the trust in security is, because the more one can assume that many capable cryptologists have examined it independently of one another and that a possibly existing weakness would have been found and published (see also Kerckhoffs' principle ).
There are procedures whose safety can be proven assuming the validity of certain mathematical assumptions . For the RSA cryptosystem , for example, the following can be shown: The private key of a user can be calculated efficiently from his public key if a large number (of the order of a few hundred decimal places) can be efficiently broken down into its prime factors . The only encryption method whose security has really been proven and not only based on guesswork is the one-time pad .
example
To illustrate an encryption, the plain text given below (for reasons of better distinguishability as usual in lower case) is converted into a ciphertext (here in upper case) using a very old and extremely simple process, the Caesar encryption . The secret key used here is “C”, the third letter of the Latin alphabet . This means the replacement of each individual plain text letter by the respective letter shifted by three places in the alphabet. For example, the first letter "B" of the plain text becomes the letter "E" in the ciphertext, which appears three places later in the alphabet, and so on:
bevordertextverschluesseltwirdisterklarlesbar EHYRUGHUWHAWYHUVFKOXHVVHOWZLUGLVWHUNODUOHVEDU
The ciphertext beginning with “EHYRU” in the example, created here by Caesar encryption (and shown in capital letters as usual for reasons of illustration) is actually incomprehensible at first glance. It is therefore suitable for hiding the information contained in the plain text from strangers. If a possible attacker does not know the underlying encryption method, or if he does not succeed in finding the key used, then the ciphertext has no meaning for him. Of course, the method used in this example, which the ancient Romans already knew, is far too weak to protect the secret message for long. It will not take much effort for an experienced code breaker to decipher the ciphertext after a short time , even without prior knowledge of the key or procedure.
In the course of human history, increasingly stronger methods of encryption have therefore been developed (see also: History of cryptography ). A modern encryption method is the Advanced Encryption Standard (AES) , which is currently considered unbreakable. However, this may change in the coming decades (see also: Cryptanalytic attacks on AES ).
Classification
In principle, a distinction is made between different classic and modern symmetrical encryption methods and the asymmetrical encryption methods that have only been known for a few decades . Classic encryption methods can be classified according to the alphabet used.
Symmetrical encryption
Symmetrical encryption methods use the same key for encryption and decryption. Two classes of encryption can be distinguished in historical methods. With the first, as in the Caesar encryption used in the example, the letters of the plaintext are replaced individually by other letters. With the Latin word substitere (German: "replace") they are referred to as substitution processes . In contrast to this, with the second class of encryption, called transposition (from Latin: transponere ; German: “offset”), each letter remains as it is, but not where it is. Its place in the text is changed, the individual letters of the text are, so to speak, mixed up. A particularly simple form of transposition encryption is the “reverting” (from Latin: reverse ; German: “reverse”) a text , which is popular with children . For example, the ciphertext SINMIEHEG is created from the plain text “secret”.
In modern symmetrical methods, a distinction is made between stream encryption and methods based on block encryption . With stream encryption, the characters of the plain text are encrypted individually and one after the other. With block encryption, on the other hand, the plain text is divided into blocks of a certain size in advance. How the blocks are then encrypted is determined by the operating mode of the encryption method .
Interestingly, even modern block ciphers, such as the DES (Data Encryption Standard) encryption method, which became the standard for several decades towards the end of the 20th century, are based on the two classic methods of substitution and transposition. They use these two basic principles in combination and derive their strength significantly from the repeated use of such combinations, not infrequently in dozens of "rounds". So, like kneading dough repeatedly, the plain text is increasingly encrypted. The strength of the encryption usually increases with the number of rounds used.
Asymmetric encryption
For centuries it was believed that there was no alternative to symmetric encryption and the associated key distribution problem. Asymmetric encryption ( public-key cryptography ) was only invented a few decades ago . Asymmetric encryption is characterized by the fact that a completely different key is used for encryption than for decryption. A distinction is made here between the “public key”, which is used for encryption, and the “private key” for decrypting the ciphertext.
Since asymmetrical processes are algorithmically more complex than symmetrical ones and are therefore slower to execute, in practice mostly combinations of the two, so-called hybrid processes, are used. For example, a randomly generated individual session key is first exchanged with the help of an asymmetric method, and this is then used together as a key for a symmetric encryption method, whereby the information that is actually to be communicated is encrypted.
glossary
In cryptology, a clear delimitation of terms and a clean and consistently used technical terminology serve to facilitate work and avoid misunderstandings. In contrast, colloquial expressions are not infrequently used incorrectly and confused with each other, which can lead to unnecessary and easily avoidable irritations. One example is the improper use of the term decryption when actually deciphering is meant.
- Alphabet - An ordered arrangement of symbols permuted in sequence, specifically the 26 uppercase Latin letters (Example: EKMFLGDQVZNTOWYHXUSPA IBRCJ)
- Break - Another term for deciphering
- Cipher - another term for ciphertext
- Cipher - Another term for encryption methods
- Cipher - Another term for encryption
- Encryption - Another term for encryption
- Codebook - Coding aid
- Code breaker - Another term for cryptanalysts
- Coding - mostly fixed assignment of plain text groups to ciphertext groups
- Dechiffrat - Another expression for plain text
- Crack - Another term for deciphering
- Decryption - converting the ciphertext into plain text using the key
- Deciphering - finding the plaintext from the ciphertext without prior knowledge of the key
- Ciphertext - Text generated from plaintext by encryption
- Involuntary - encryption and decryption are identical
- Cryptanalyst - someone who tries to extract information from the ciphertext without first knowing the key, e.g. B. to find out the plain text or the key
- Cryptogram - Another term for ciphertext
- Key - Secret information that is used for encryption or required for decryption
- Keys - A general term for encryption and decryption
- Encryptor - the person who encrypts or decrypts messages
- Key space - set of all possible keys
- Ciphertext - another term for ciphertext
- Weak encryption - encryption that can be deciphered
- Strong encryption - encryption that cannot be deciphered with today's knowledge and methods
- Encrypt - converting plain text into ciphertext
Applications in information technology practice
Transmission of messages in networks
An encrypted message (e.g. an e-mail or a website) usually has to be transmitted over several stations. Today these are mostly individual computer systems, which means that the encrypted message is transmitted over a computer network. A distinction is made between two fundamentally different modes of transmission. With line encryption, the message is only encrypted for the neighboring computer. The latter decrypts the message, encrypts it in turn (possibly with a different method) and sends it to its neighbor - and so on to the target computer. The advantage of this method is that only neighboring computers have to agree on an encryption method and the key used. In addition, this type of transmission can be located on a very low protocol level (e.g. already in the transmission hardware). The disadvantage is that each individual computer must be trustworthy and secure on the transmission path. With end-to-end encryption, on the other hand, the message is encrypted by the sender and, in this form, transmitted unchanged across several computers to the recipient. Here none of the transmitting computers can see the plain text of the message. The disadvantage, however, is that the sender has to agree on an encryption method and associated key (s) with every possible recipient.
Encryption of data on data carriers ("data safe")
[For a detailed discussion see full disk encryption ]
Sensitive data on a data carrier can be protected from unauthorized access in two main ways:
- Encryption software is used to encrypt the entire hard disk or a single partition (Full Disk Encryption or FDE) or even just a data container in the form of a single file on the data carrier;
- With hardware encryption, a microchip on the USB drive performs automatic and transparent encryption. Authentication is achieved, for example, if the device has a physical keyboard that requires a PIN code to be entered before use.
literature
- Friedrich L. Bauer : Deciphered Secrets. Methods and maxims of cryptology. 3rd, revised and expanded edition. Springer, Berlin et al. 2000, ISBN 3-540-67931-6 .
- Linda A. Bertram, Gunther van Dooble, et al. (Ed.): Nomenclatura - Encyclopedia of modern Cryptography and Internet Security. From AutoCrypt and Exponential Encryption to Zero-Knowledge-Proof Keys. Books on Demand, Norderstedt 2019, ISBN 978-3746-06668-4 .
- Albrecht Beutelspacher Kryptologie - An introduction to the science of encryption, concealment and concealment without any secrecy, but not without deceitful rogue, presented for the benefit and delight of the general public . Vieweg & Teubner, 9th updated edition, Braunschweig 2009, ISBN 978-3-8348-0253-8 .
- Johannes Buchmann : Introduction to Cryptography . Springer, 4th expanded edition, Berlin 2008, ISBN 978-3-540-74451-1 .
- Michael Miller: Symmetrical encryption methods - design, development and cryptanalysis of classic and modern ciphers . Teubner, Wiesbaden 2003, ISBN 3-519-02399-7 .
- Klaus Schmeh : Code breakers versus code makers - The fascinating history of encryption . W3L-Verlag, 2nd edition, Herdecke 2008, ISBN 978-3-937137-89-6 .
- Bruce Schneier : Applied Cryptography . Protocols, algorithms and source code in C. Pearson Studium, Munich 2006, ISBN 3-8273-7228-3 .
- Simon Singh : Secret Messages . Carl Hanser Verlag, Munich 2000, ISBN 3-446-19873-3 .
- Fred B. Wrixon: Codes, Ciphers & Other Secret Languages - From Egyptian Hieroglyphics to Computer Cryptology . Könemann, Cologne 2000, ISBN 3-8290-3888-7 .
Web links
- An introduction to the use of encryption
- Lecture on IT security with a focus on encryption at the FH Frankfurt
- Encryption methods and their applications
- Simon Singh: The Code Book (1999) (English)
- Introduction to encryption
- Encryption: Common Vulnerabilities
- Christian Spannagel : Encryption . Lecture series, 2012.
Individual evidence
- ↑ Bundeswehr drone flies with German "encryption" on heise online from October 6, 2016, accessed on April 30, 2019.