Encryption method
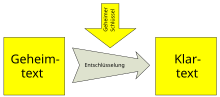
With an encryption method a can plaintext into a ciphertext is converted ( encryption ) and vice versa of the ciphertext are reconverted back into the plaintext ( decryption ). A key is often used here . Cryptography has a long history, so encryption methods are already known from ancient Egypt . Important milestones in the development of new encryption methods are the invention of the telegraph , the computer and asymmetrical cryptosystemsThe most widespread method today due to digital communication is the RSA method .
principle
A source text, such as B. a message or a password can be encrypted. Such a source text is called plain text , the encrypted text is called ciphertext . In this way, the source text can be protected from unauthorized access. Despite this encryption, a third party, usually called a code breaker , can try to decipher the text that he cannot understand . In principle, one differentiates between the classic symmetrical cryptosystems and the asymmetrical cryptosystems that have only been known for a few decades .
Symmetrical encryption method
With symmetrical procedures, encryption and decryption are carried out with the same key. This means that the sender and recipient must have agreed on this secret key in advance and the key must of course be kept secret in order to protect the information . The transfer of the secret key represents a security problem. The first known of this type is the Caesar cipher .
Asymmetrical encryption method
With asymmetric methods, there is not one key to encrypt and decrypt, but two; a public key that is accessible to everyone and a private key that must be kept secret. The text is encrypted with the public key and can only be decrypted with the private key. The encryption key does not have to be kept secret here, but it must be ensured that the public key really belongs to the recipient. In addition, asymmetric methods are usually slower, which is why hybrid methods are mostly used in practice .
ID-based encryption method
ID-based encryption methods are a special subset of the asymmetric methods in which there is only one secret decryption key. Only the public parameters of the procedure and the identity of the recipient need to be known for encryption. The recipient can have a decryption key associated with his identity issued by a central authority that has a kind of superkey. The specialty of this procedure is that no key is transmitted any more, the encryption can even take place before the recipient knows his secret key.
See also
- History of cryptography
- List of algorithms # cryptography
- CrypTool - demonstration and reference program for cryptography and cryptanalysis
literature
- Bruce Schneier : Applied Cryptography . Protocols, algorithms and source code in C. Addison-Wesley, Bonn et al. 1996, ISBN 3-89319-854-7 , p. 4.
- Friedrich L. Bauer : Deciphered Secrets. Methods and maxims of cryptology. 3rd revised and expanded edition. Springer, Berlin et al. 2000, ISBN 3-540-67931-6 , p. 7.
- Johannes Buchmann : Introduction to Cryptography. 4th expanded edition. Springer Berlin et al. 2008, ISBN 978-3-540-74451-1 , p. 59.
- Albrecht Beutelspacher Cryptology. An introduction to the science of encryption, concealment, and concealment; without any secrecy, but not without deceitful rogue, presented for the benefit and delight of the general public. 9th updated edition. Vieweg + Teubner, Braunschweig et al. 2009, ISBN 978-3-8348-0253-8 , p. 2.
Web links
- Christian Spannagel : Encryption . Lecture series, 2012.