IEEE 802.15.4

The IEEE 802.15.4 standard describes a transmission protocol for Wireless Personal Area Networks (WPAN). It defines the two lowest layers of the OSI model , the bit transmission and the MAC layer. Other standards for wireless networks such as ZigBee are responsible for higher protocol levels with functions for routing and an application interface . The main development goals for the protocol are low power consumption for long operation via battery supply , cost-effective hardware, secure transmission, use of license-free ISM bands and parallel operation with other transmitters on these frequencies, especially WLAN and Bluetooth . These properties make the IEEE 802.15.4 standard particularly suitable for wireless sensor networks (WSN) and for sensors and actuators worn directly on the body ( WBAN , Wireless Body Area Network ).
Basics
In the late 1990s, a need for a simple standard for wireless data transmission for devices with low power consumption and low data transmission rates was seen. The IEEE 802.11 and Bluetooth standards available at the time were too complex and required too much energy to be implemented with inexpensive components. When IEEE 802.15.4 was developed, the highest priority was therefore not a high data transmission rate, but rather energy management and the simplicity of the standardized protocol.
The long idle phases are characteristic of the nodes in an IEEE 802.15.4 network, which means that a node can remain in an energy-saving operating state for most of the time. As soon as he wants to send or receive data, he can wake up in just 15 ms, then handle the communication and go back to sleep. As a result, battery-operated network nodes can achieve typical operating times of six months to two years.
Topologies
IEEE 802.15.4 provides for two types of network nodes, each with a different scope of functions: The "Reduced Function Devices" (RFD) and the "Full Function Devices" (FFD). An RFD only has a subset of the standardized functional scope, which means that it is only able to communicate with FFDs, but it can also be developed more easily and cost-effectively. RFDs are typically sensors or actuators in the network that only very rarely send or receive data, do not take on any administrative tasks and thus remain in an energy-saving state most of the time. FFDs, on the other hand, have the full range of functions and can communicate with both RFDs and other FFDs. One FFD per network takes on the special function of the PAN coordinator. It defines the PAN identifier that separates the network from other IEEE 802.15.4 networks within radio range . Furthermore, it takes over the synchronization of all network nodes in slotted mode. A network can have up to 254 nodes.
The standard defines three different network topologies based on the node types mentioned:
- Star . In a star, all nodes communicate directly with the coordinator. In such a constellation, the coordinator is usually a powerful device connected to the power grid, while the other nodes are battery-operated.
- Peer-to-peer . Although there is also a coordinator in this network, the nodes can also communicate directly with one another, provided they are within mutual range.
- Tree structure (cluster tree) . RFDs here represent the leaves of a tree. They are connected to FFDs, which take on the function of a coordinator for part of the network. The FFDs themselves are in turn connected directly or indirectly via further FFDs with a coordinator function to the PAN coordinator of the entire network. The resulting tree structure with the PAN coordinator as the root represents a mixture of the first two topologies. With the possibilities of the standard alone, however, a complete meshing and forwarding of messages (routing) is not possible.
Since the standard does not define a network layer, functions such as routing must be implemented using higher layers of other protocols based on IEEE 802.15.4. This enables real meshed networks in which the FFDs serve as repeaters and each node can communicate with another via intermediate stations, even RFDs with other RFDs.
Standardized interfaces
IEEE 802.15.4 defines the lowest two layers of the OSI reference model . Higher layers are implemented using other standards such as ZigBee . The individual layers implement certain functions, for which they use the services of the next lower layer. In turn, they make their own functions available as a service to the layers above. The interfaces between the layers are called service access points . The exact implementation of the functions can be carried out differently by each manufacturer, but the available range of functions and services is firmly prescribed. In this way, the standard ensures that communication between devices works smoothly even with implementations from different manufacturers.
Physical layer
Frequency bands and data rates
The ISM bands 868/915 MHz (Europe or USA) and 2.45 GHz (almost worldwide) are available for radio transmission. Due to the different frequencies, the hardware can only use one band at a time. The use of radio modules for the 2.45 GHz band is very widespread ; only a few use the 868/915 MHz band.
| Channel parameters | Data parameters (2003) | Spreading parameters (2003) | |||||||
|---|---|---|---|---|---|---|---|---|---|
| Frequency band | Bandwidth | Channel spacing | Channel number | region | Data rate (gross) | Symbol rate | Symbols | Chirp rate | modulation |
| 868-868.6 MHz | 300 kHz | 0 | Europe | 20 kBit / s | 20 kBaud | binary | 300 kchirps / s | BPSK | |
| 902-928 MHz | 600 kHz | 2 MHz | 1-10 | United States | 40 kBit / s | 40 kBaud | binary | 600 kchirps / s | BPSK |
| 2400-2483.5 MHz | 2 MHz | 5 MHz | 11-26 | worldwide | 250 kBit / s | 62.5 kBaud | 16 orthogonal | 2 Mchirps / s | Offset QPSK |
The frequency spreading method DSSS is used to reduce susceptibility to interference . In the 868 MHz frequency band, each symbol represents one bit due to the modulation method used and is converted to a 15 chirps long code. With a chirp rate of 300 kchirps / s, this results in a data rate of 20 kBit / s. In the 915 MHz frequency band, the chirp rate of 600 kchirps / s is twice as high, resulting in a data rate of 40 kBit / s. In the 2.45 GHz frequency band, modulation with 4 bits / symbol, symbol spreading to 32 chirps and a chirp rate of 2 Mchirps / s are used, which leads to a data rate of 250 kBit / s. The modulation methods used were chosen because they have a good balance between simplicity and robustness.
Since the length field is 7 bits, a data packet can contain 0 to 127 bytes. For data types that comprise more than one byte, the byte order follows the principle of “least significant byte (little endian) first”. The range is a maximum of 100 meters outside and 30 meters inside.
Further development:
- In 2006, a revised version of the standard raised the data rates from the 868 MHz band exclusively with Parallel Spread Spectrum Technology (PSSS) to 250 kBit / s and from the 915 MHz band and the like. a. also with PSSS to 250 kBit / s.
- In August 2007, with the addition of IEEE 802.15.4a, two more transmission methods were added for the physical layer. The first is an ultra broadband technology (UWB) that transmits on frequencies below 1 GHz, between 3 and 5 GHz and between 6 and 10 GHz. The other is the chirp spread spectrum method (CSS) which works in the 2.45 GHz band and offers the possibility of localization in the network. This further development was officially standardized with the IEEE 802.15.4-2011 version in 2011.
Transmission power
The typical transmission power of a transceiver is 0 dBm (1 mW) and the sensitivity is below −90 dBm. Even if the specified model of path losses applies to buildings, practice shows that often only a third of the specified range is possible.
IEEE 802.15.4 was designed for parallel operation with WLAN and Bluetooth. Practice tests showed problems with the coexistence of IEEE 802.15.4 with WLAN and Bluetooth in the 2.45 GHz band. With Bluetooth, the adaptive frequency hopping introduced since version 1.2, but the WLAN evades the remaining frequencies more often, proves to be an interferer. WLAN causes problems due to the strong growth in data traffic. The ZigBee Alliance has questioned the validity of these results and a compatibility study has provided counter-evidence.
hardware
The size of the antenna in the 2.45 GHz band can be very small; a module with antenna, transceiver and microprocessor is roughly the size of two one-euro coins. It is also possible to use the articulated antennas developed for WLAN.
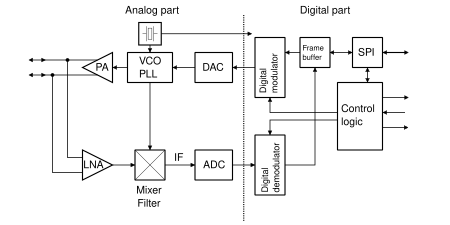
The graphic below shows the block diagram of a transceiver chip that most manufacturers' hardware corresponds to. Only the reduction to the intermediate frequency is done with analog components, the demodulation / modulation is done digitally. The transmission takes place in packets and a buffer stores incoming or data to be sent. Almost no external components are required apart from an oscillating crystal and backup capacitors .
MAC layer
Of the data link layer according to the OSI reference model, the IEEE 802.15.4 standard defines only the lower sub -layer with the MAC layer . The LLC layer is not implemented at this point. Since the MAC layer is essentially implemented by software, this reduces the size of the protocol stack. The MAC layer thus forms the upper end of IEEE 802.15.4. The ZigBee standard is based directly on this layer. (The “symbol period” represents the basis for all time information. In the 2.45 GHz band, this is 16 µs. The values for the MAC layer all relate to the specifications for the 2.45 GHz band. )
CSMA / CA
A CSMA / CA algorithm is used to avoid collisions when accessing the medium . Before transmitting, the transmitter checks whether another device is transmitting on the channel by measuring the signal strength from the antenna. If the channel is free, data transmission begins; otherwise the device waits a random period of time and carries out another channel-free test. If the channel-free test fails several times, the algorithm aborts the transmission with the error message "Channel occupied". An ACK packet can be requested from the recipient to secure the transmission. If there is no confirmation of a message, this means a transmission error - the packet is sent again. If this happens several times, the attempt to send ends with the error "NOACK"; the recipient cannot be reached. A CSMA / CA algorithm is not required to send ACK packets; it is sent directly after a message has been received.
The layer above can draw several conclusions from the error message after an unsuccessful transmission attempt. "NOACK" means that the remote station is no longer in the reception range. From "Channel occupied" it follows that the channel used is overloaded and should be changed if necessary.
The CSMA / CA algorithm specifies that the random back-off takes place before the first channel-free test, which significantly reduces the effective data rate. The waiting time before the first attempt to transmit in the 2.45 GHz band is between 0 and 2.24 ms. If the channel-free test fails, this can increase to 9.92 ms. There are also further delays if no ACK is received from the recipient. The following formula is based on the specifications of the standard and calculates the backoff time.
The timeout for the ACK packet is 864 µs (symbol period · AckWaitDuration) and may take place at the earliest 192 µs after receipt of the complete message.
Transmission method
The standard defines two transmission methods. In the so-called unslotted mode, the network participants send their data asynchronously. In slotted mode, the PAN coordinator synchronizes the access by dividing the transmission periods into so-called superframes.
Unslotted mode (nonbeacon-enabled)
Before each transmission, a participant checks via CSMA / CA whether the channel is busy and sends its data as soon as it becomes free. Optionally, he can specify in the sent packet whether he wants a response (ACK), on the basis of which he can check whether the packet arrived correctly or whether the transmission was disrupted. This mode does not require any administrative effort from the PAN coordinator.
A distinction is made between 3 communication scenarios:
- Data from participant to PAN coordinator. Coordinator receives data and, if specified, sends an ACK. In order to be able to receive the data, the coordinator must always be ready to receive and must not go to sleep in an energy-saving mode.
- Data from participant to participant (peer-to-peer topology). As in the first scenario, the recipient must always be ready to receive.
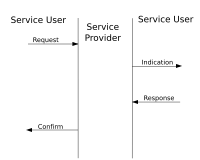
- Data from PAN coordinator to participants. Participant regularly asks whether the coordinator has any data for him. This replies (ACK) and sends the data, if any, or an empty data packet if it has no data for the subscriber. See right picture. Here, too, the coordinator is always ready to receive.
In relation to the energy demand, one node, usually the PAN coordinator, must always be ready to receive in this mode, while the other nodes can save energy most of the time.
Slotted mode (beacon-enabled)
In slotted mode, the PAN coordinator divides the transmission periods into so-called superframes. Their structure can be seen in the picture on the right. A superframe is limited by two beacons (German signal beacons). The coordinator sends the beacons at fixed intervals (without CSMA / CA) so that the participants can synchronize with the beginning of the superframe. The length of the superframe is specified with the parameter BI (beacon interval). This is calculated using the parameter BO (Beacon Offset) as follows:
BO can have values between 0 and 14. A value of 15 means that the superframe should be ignored. The length of a superframe can therefore be between 15 ms and 246 s. The superframe is divided into an active and an inactive phase using the SO (Superframe Order) parameter. The active period (SD = Superframe Duration) is calculated using the same formula as before, except that BO is replaced by SO:
SO can have values between 0 and 14, but must be ≤ BO. A value of 15 means that the superframe has no active phase after the beacon. The active phase consists of 16 time slots of the same length. The first is occupied by the beacon, the rest are divided into the contention access period (CAP) and the contention free period (CFP). In the CAP, all participants willing to send compete in each slot via CSMA / CA to be able to send their data. The time slots of the CFP are combined by the PAN coordinator into Guaranteed Time Slots (GTS) and permanently assigned to participants, so that there is no competition via CSMA / CA during this period . A subscriber who receives a GTS has a guaranteed period of time in which he is the only member of the network to transmit. However, GTS does not mean that a specific data throughput is guaranteed or real-time conditions are met. GTS only regulates the distribution of transmission capacity within a network. A participant from outside the network who does not adhere to the time slots of the superframe can continue to disrupt the transmission. In addition, the allocated transmission capacity can be lower than the required one if the participants ask more than the coordinator can distribute.
In the inactive phase, the PAN coordinator can switch to a power-saving operating mode and conserve the batteries. This is an improvement compared to the unslotted mode, which, however, comes at the cost of more administrative overhead for the synchronization. For the subscribers willing to send, the synchronization increases only minimally and they can continue to spend most of their time saving energy.
There are also 3 communication scenarios here:
- An attempt is made to obtain a free slot in the CAP for data transmission from the participant to the coordinator.
- If the coordinator has data for the participant, he indicates this in the transmitted beacon. The participant listens periodically for the beacons and finally responds in the CAP to collect the data. See picture.
- With peer-to-peer, the participants first synchronize each other and then transfer the data.
Connection establishment
Before a device can communicate with another, a channel must be selected for it. If possible, the coordinator selects a channel without a competing transmitter, for this purpose the ED-Scan (Energy-Detect) is used, in which the signal strength is measured, or Active-Scan, in which all other devices active as coordinators are requested to send a beacon by a beacon request to ship. If a device is looking for a connection to a coordinator, this is done with an active scan (FFD only) or a passive scan (listening to channels on beacons).
To ensure that the structure of a network runs smoothly, end devices register with a coordinator with an associate request. This is confirmed by assigning a short address. The choice of the short address is the responsibility of the higher layers.
Encryption and security
The IEEE 802.15.4 standard offers security measures at MAC level through message integrity check and symmetrical encryption. You can choose between several methods based on CCM and AES . The keys are defined by the layer above and then managed by the MAC layer. The encryption is specified separately for each communication partner and automatically applied by the MAC layer. If a received packet was encrypted, this is indicated by a parameter in the indication primitive.
The implementation of the encryption varies slightly between version 2003 and 2006.
Individual evidence
- ↑ IEEE802.15.4-2011 standard . DecaWave. Archived from the original on July 5, 2015. Info: The archive link was inserted automatically and has not yet been checked. Please check the original and archive link according to the instructions and then remove this notice. Retrieved March 10, 2018.
- ↑ zigbee.org ( Memento of the original from April 2, 2015 in the Internet Archive ) Info: The archive link was inserted automatically and has not yet been checked. Please check the original and archive link according to the instructions and then remove this notice. ZigBee and Wireless Radio Frequency Coexistence
See also
Web links
- Working group (WG) 15 of the IEEE
- The IEEE 802.15 standard as a free download