Network-Centric Warfare
Network-Centric Warfare ( NCW ; German network-centered warfare ) is a military concept developed by the US armed forces, which creates information superiority through the networking of reconnaissance, command and control systems and thus the US military a cross-military superiority in the entire range to guarantee military operations ( full spectrum dominance ) .
Other states have also taken this conception of the US armed forces as a model and developed their own models that differ from one another, especially in terms of their claims. The Bundeswehr calls its concept networked operations management ( NetOpFü ). Sweden has given its concept the name Network Based Defense (NBD) , while Great Britain has named its variant Network Enabled Capabilities (NEC) .
The material backbone for this US Department of Defense doctrine is the Global Information Grid .
The ideas of Soviet General Nikolai Ogarkow at the beginning of the 1980s provided rudimentary approaches to fully networked warfare . As the first army after the Cold War , the United States armed forces picked up on this development. A fully-fledged concept was created through the publication of the strategy documents Joint Vision 2010 and Joint Vision 2020
Definition of terms
In the military sector , NCW has achieved a status similar to that of the term e-business for business.
The principles of NCW lie in the economy, from which Admiral a. D. Cebrowski borrowed these principles for the military. Both terms are linked in such a way that they understand information as the key to gaining competitive advantage. You achieve this through a higher effectiveness and efficiency in the use of information technology and a simultaneous "customer-oriented" further development of organizations and processes .
Networking of entities

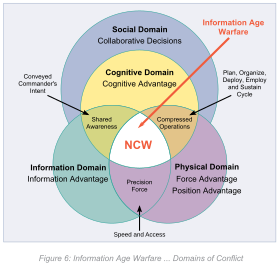
Network Centric Warfare is intended to achieve an increase in military combat strength compared to conventional concepts. This is to be achieved by networking all relevant components (“entities”): intelligence , management and control systems (also called effectors).
Networking them is intended to overcome previous range limitations and increase the speed of response and accuracy. Digital data transmission enables information to be distributed with almost no loss of time or quality. The associated demand for data connections with large bandwidths (which can only be implemented via satellite for a large number of military operations), however, results in high costs.
NCW is not limited to the pure bundling and all-round availability of information. The impending information overload for the individual recipient is one of the main problems facing NCW. Knowledge management systems and "artificial intelligence" are intended to convert the flood of information into knowledge and distribute it.
Example of the effects of networking
A simple example can be used to explain what is hidden behind the term entities in NCW and how networking can increase range, reaction speed and accuracy:
A soldier has sensors (eyes, nose, ears, ...) to record information about his surroundings. In this example he is the decision maker himself and the system of operations he oversees is the weapon in his hand.
It takes the information from its sensors and combines it with commands or instructions from higher-level bodies. Based on this information, he makes his decisions:
He can
- cause its sensors to absorb more information
- Give instructions to subordinates
- use his weapon to engage an identified target
In this example, the operational capability of the entities is essentially determined by their range. The range of the soldier's sensors (field of vision, hearing range, etc.) determines the radius of the information horizon . Only the immediate environment falls into the decision-making framework. For example, the soldier can only operate the weapon he has in hand and only contact the superordinate or subordinate bodies that are within the immediate range of the conversation. The weapon has a limited range which limits the radius of the soldier.
The communication range of the soldier can be increased with the help of radiotelephony. However, this has little effect on its sensor or weapon range. A target that is outside of his sensor range could not be targeted accurately, even if the weapon range was higher, as he could not aim at it via radio.
With the help of a data connection between all entities, a soldier can access the sensors of another soldier. For example, this would be possible with a helmet camera, which displays your current image of the surroundings on a small monitor in the field of view of each soldier. All soldiers can therefore potentially fade in the field of vision of another soldier.
If the entities were closely networked in almost real time, they would ideally merge into a collective entity. Thanks to the exchange of information with one another, self-synchronization could be achieved which coordinated actions and could enable faster adaptation to changed environmental conditions.
Each weapon platform is provided with all of the data relevant to it (far more than it could collect on its own) in a processed form. So this information consists of processing data gathered by all the other available sensors.
Example:
Enemy planes are spotted by an AWACS aircraft while on patrol. Air surveillance radar systems and interceptors aim their sensors at the targets. All data is processed by all sensors and merged and transmitted to all defense systems. As a result, surface-to-air missile systems and interceptors have an overwhelming amount of data about the targets. Without an early warning system like AWACS, it would have been too late for the low-flying targets to be detected by ground-based radar sensors or interceptors.
Example:
Tomahawk cruise missiles are flying over enemy territory awaiting further orders. Suddenly one discovers Boeing E-8 Joint STARS - reconnaissance aircraft an enemy ground-to-air missiles position with deactivated radar. The tomahawks happen to be near the targets. Through a secure channel, the GPS coordinates are transmitted to the cruise missiles in less than a minute, along with the order to destroy the target. The tomahawks change course, fly towards the target and attack it. The target is reported as destroyed and no further action is taken against a target that is already considered destroyed.
In the last days of the Second Gulf War in 1991, such a process (i.e. the time between detection and destruction of a target), the so-called sensor-to-shooter cycle , could take two full days. In the Third Gulf War , this time was significantly reduced to a few minutes.
Networked companies as a role model
In the classic military communication concept, reconnaissance, command and control systems were only partially interconnected. Each entity was associated with only a few entities. Data was managed in incompatible systems (so-called "island solutions") that could only be viewed by a small number of the relevant entities. NCW would like to overcome these limits and implement a complete network. Similar concepts are already in use in the private sector. Under the term Collaborative Business , department and company boundaries are overcome with the help of open systems and an unhindered exchange of information is made possible. This shows that the military orientates itself directly on the experiences of the economy with the idea of Network Centric Warfare.
When NCW is fully deployed, it means that every entity is supplied with all information relevant to it, including beyond the boundaries of the armed forces (jointness) and even beyond the boundaries of national armed forces (combinedness). According to the Metcalfe rule , which states that the benefit of a network increases with the number of participants, this comprehensive introduction of NCW also has a positive feedback effect on the result of the networking.
Current developments
During the Iraq war of 2003, the concept of Network Centric Warfare was first implemented on a large scale. It didn't work completely, but in principle the new system offered users a few options:
- The military command ( CENTCOM ) was connected to almost all units of the US armed forces via direct data lines (e-mail, video conference, chat).
- Radar data was transmitted in real time to ships, planes, tanks and other combat units and largely provided with so-called friend-foe identifiers in order to give the commanders a precise overview.
- Mission data, maps, satellite photos, deployment videos from previous missions as well as current information on stocks, weapons equipment and the condition of devices and vehicles could be queried via a kind of intranet .
literature
- Francis Fukuyama , Abram N. Shulsky: Military Organization in the Information Age: Lessons from the World of Business . (PDF; 74 kB; 34 p.) In: Zalmay Khalilzad, John P. White, Andrew W. Marshall (Eds.): The Changing Role of Information in Warfare . (Series: Strategic Appraisal). RAND Corporation, Santa Monica 2006, ISBN 0-8330-2663-1 .
- Defense technical report. IT report 2006. Bonn / Frankfurt am Main: Report-Verlag, 2006. - 72 pp., Ill., Graph. Darst.
- Stefan Plogmann: The “just-in-time war” . Feldkirch 2004.
- Stefan Plogmann: The future of European defense policy in the era of “Information Warfare” . Vaduz 2005.
- James Moffat, Defense Science and Technology Laboratory ( United Kingdom ): Complexity Theory and Network Centric Warfare . (PDF; 2.4 MB) Series: Information Age Transformation Series. Command and Control Research Program (CCRP), 2003, ISBN 1-893723-11-9 , 201 pp.
- David S. Alberts, John J. Garstika, Frederick P. Stein: Network Centric Warfare - Developing and Leveraging Information Superiority . DoD C4ISR Cooperative Research Program CCRP, Washington DC 2000.
- David S. Alberts, John J. Garstika, Richard E. Hayes, David A. Signori: Understanding Information Age Warfare . (PDF) DoD C4ISR Cooperative Research Program (CCRP), Washington DC 2001.
- Stefan Aust , Cordt Schnibben : Iraq - History of a Modern War . SPIEGEL-Buchverlag, Hamburg 2003, ISBN 3-421-05804-0 .
- Heiko Borchert (Hrsg.): Networked security - guiding principle of security policy in the 21st century . 2004.
- Networked Operations Management - An Introduction . (PDF) luftwaffe.de, 2005
- Sascha Lange: Network-based warfare . Science and Politics Foundation , Berlin, SWP Study 2004 / S v. May 22, 2004, swp-berlin.org (PDF; 246 kB; 30 pages).
Television documentary
- Klaus Prömpers, Scott Willis: The perfect war - high tech, plans, illusions . New York Times Television 2004
See also
- Global Strike
- Combat of the combined arms
- Management and information system
- Cyberwar
- Electronic warfare
- Future Combat System
Web links
- Command and Control Research Program (CCRP, a division of DoD ); Publications
- Peter Bürger ,: War as a computer game: remotely controlled combat missions, electronic brains and surveillance systems . Telepolis , October 14, 2006 (Part 3 of a series of articles by the author)
- Tactical Networker: Creating a Dynamic, Self-Forming Network for Formations on the Move - Interview with Colonel Angel L. Colon (Military Information Technology, Online Edition, USA, October 24, 2006)
- Landpower and Network-Centric Operations: How Information in Today's Battlespace can be Exploited . (PDF; 587 kB) US Army War College, May 15, 2006; further DoD documents on the subject: oft.osd.mil
- Lt. Gene. Harry D. Raduege Jr: Net-Centric Warfare Is Changing the Battlefield Environment .
- Pentagon Envisioning a Costly Internet for War
- Network-Centric Warfare A new concept of warfare. Introductory seminar paper on the topic
Individual evidence
- ↑ Benjamin Schreer: The transformation of the US armed forces in the course of the Iraq war . Science and Politics Foundation , December 2003, p. 7; Retrieved July 18, 2007.