Petya
Petya is an extortion trojan that encrypts all files in the computer without the user's knowledge. The victim is asked to pay a ransom for a system or data recovery . In contrast to other encryption Trojans, Petya encrypts the table of contents of the hard disks (the so-called Master File Table ). Petya also encrypts the first kilobyte of many, but not all, files. The name Petya is a nickname Петя that is widespread in Slavic languages such as Russian and corresponds to the German-language variant Peter , Peterlein .
Petya now exists in four different variants. The first variant is marked by a red skull. Since this version of Leostone was cracked with the help of genetic algorithms , the blackmailers released a second variant in May, which could, however, also be cracked with the help of graphics cards, provided that the user account control of Windows was confirmed by the user. The green version contained a second encryption software called Mischa, which was only used if the user account control was not confirmed by the user. In this case, the user's files in the user space were encrypted without the green skull being visible. The operating system also remained bootable in this case.
As a result, another green skull variant of the ransomware was published in July, which could no longer be deciphered using brute force methods. In December 2016, another variant was published under the name "Goldeneye", which is characterized by a yellow skull and, unlike earlier variants, now completely encrypts files before the hard drive's table of contents is encrypted. In contrast to previous versions, full file encryption is carried out before the computer is restarted.
functionality
Petya is mainly transmitted via email and disguised as a cover letter. In the email is a Dropbox - Link pretending that it is an application. In reality, however, the link leads to a program disguised as a PDF file . If this file is downloaded and executed, the program will unpack and overwrite the master boot record . When the overwrite process is completed, a blue screen is displayed and the operating system crashes.
Shortly afterwards the system boots up again and shows the victim a fake CHKDSK scan. But in fact, by means of Salsa20 - algorithm , the Master File Table encrypted. With the encrypted main file of the hard drive's table of contents, the system can no longer locate where the files are on the hard drive or whether they still exist at all.
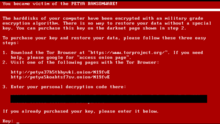
Once the fake CHKDSK scan completes, the overwritten master boot record will open a lock screen with system recovery instructions. The instructions ask the victim to use a Tor browser to open a website on the Darknet . On this website, the victim now has to pay ransom in the form of bitcoins in order to regain access to the data.
Decryption
In April 2016, the decryption of Petya was announced by an anonymous computer specialist. He developed the software hack petya , which generates a password for accessing the encrypted files.
In June 2016, the decryption of the first green Petya version was published by the engineering firm Dipl.-Ing.Rolf B. Drescher VDI & Partner, whereupon the extortionists sent masses of emails with the malware in its new version on behalf of the engineering firm in December sent to get revenge on the company.
Both the last green version of Petya, which was published in July, and the yellow skull version, which was published under the name "Goldeneye", are no longer decipherable. Paradoxically, however, not by the blackmailers themselves, since the blackmailers' encryption algorithm still contains a program error that prevents reliable decryption.
Cyber attack in June 2017
On June 27, 2017, a new version disabled many computers around the world. Ukraine in particular was hit by hard drives being erased. Kaspersky and other manufacturers of security software refer to the new malware (in the software update of an accounting software ) explicitly as NotPetya (or Wiper ). After the failure of Windows computers, radioactivity had to be measured manually at the ruins of the Chernobyl nuclear power plant in Ukraine . Important technical systems of the station functioned normally there. In addition, German companies such as Beiersdorf , the Danish shipping company Maersk , the Russian oil producer Rosneft , the American pharmaceutical company Merck Sharp & Dohme , the food producer Mondelez and many others were also affected by the Ukrainian accounting software "MEDoc" .
A. P. Moller-Maersk put the cost of the cyber attack in June 2017 at up to 300 million US dollars. In September 2017, FedEx communicated a loss of 300 million US dollars for its subsidiary TNT Express as a result of the attack.
Reactions
The European Police Office announced that it had been notified of the cyberattacks by the member states of the European Union and had taken immediate action. In the United States of America , the Department of Homeland Security deals with the issue and coordinates the national and international partners concerned.
The BSI President believes that the cyber attack in June 2017 would have been largely avoidable as the security gap had been known for months and could be closed.
The governments of the United States, the United Kingdom and Australia attribute "NotPetya" to the Russian Federation according to statements from 2018. The software was used by Russia to destabilize Ukraine.
Individual evidence
- ^ Petya - Taking Ransomware To The Low Level . hasherezade. Retrieved May 25, 2016.
- ↑ Attention: New encryption Trojan Goldeneye is spreading rapidly In heise.de. Retrieved on April 11, 2017
- ^ Petya: the two-in-one trojan . Fedor Sinitsyn. Retrieved May 25, 2016.
- ↑ Petya Ransomware Goes Low Level . Razvan Benchea, Vatamanu Cristina, Maximciuc Alexandru, Liviu Arsene. Retrieved May 25, 2016.
- ↑ Petya Ransomware skips the Files and Encrypts your Hard Drive Instead . Lawrence Abrams. Retrieved May 25, 2016.
- ↑ Petya ransomware eats your hard drives . John Snow. Retrieved May 25, 2016.
- ↑ Helmut Martin-Jung: Ransomware. Blackmail Trojan cracked: Victims get data back. In: Süddeutsche . April 12, 2016. Retrieved May 28, 2016.
- ↑ Goldeneye Ransomware specifically attacks HR departments In heise.de Retrieved on April 11, 2017
- ↑ Everything we know so far about the Petya / NotPetya outbreak heise.de, on June 28, 2017
- ↑ Axel Weidemann: It's not over yet. Computer virus "Petya" causes great damage , in: FAZ , July 8, 2017, p. 16
- ↑ https://www.wired.com/story/notpetya-cyberattack-ukraine-russia-code-crashed-the-world
- ↑ Blackmail Trojan is around the world - Hacker attack hits Chernobyl and corporations in Western Europe , manager magazin from June 27, 2017, accessed on June 28, 2017
- ↑ Giles Turner, Volodymyr Verbyany, Stepan Kravchenko: New Cyber Attack Goes Global, Hits WPP, Rosneft, Maersk . June 27, 2017. Retrieved June 28, 2017.
- ↑ 'Petya' Cyberattack Cripples Ukraine, And Experts Say It's Spreading Globally , NPR. June 27, 2017. Accessed June 28, 2017.
- ↑ Again global cyber security incidents caused by ransomware , Federal Office for Information Security from June 27, 2017, accessed on June 30, 2017
- ↑ "America blames Russia for explosive cyberattack" FAZ from February 16, 2018
- ^ Sarah Young and Denis Pinchuk: Australia joins UK, US to blame Russia for NotPetya . In: Itnews , February 16, 2018.