Shodan (search engine)
|
|
|
|---|---|
| Computer search engine | |
| languages | English |
| Registration | optional |
| On-line | 2009 |
| https://www.shodan.io | |
Shodan is a computer search engine . It allows users to find specific types of computers and services ( webcams , routers , servers , etc.) connected to the Internet through a series of filters. It is also known as the service banner search engine, which sends metadata back to the client from the server . The data collected in the process usually contain information about the server software, supported options, a welcome page or the like, which the server transmits in its interaction with the client.
Shodan usually collects data on web servers ( HTTP / HTTPS via ports 80, 8080, 443, 8443), as well as FTP (port 21), SSH (port 22), Telnet (port 23), SNMP (port 161), SIP (port 5060), and Real Time Streaming Protocol (RTSP, Port 554). The latter are regularly used to access webcams and their video stream .
Shodan was launched in 2009 by software developer John Matherly, who came up with the idea of finding Internet-connected devices in 2003. The name Shodan is a reference to SHODAN, a character from the video game series System Shock .
background
The website started as Matherly's home project due to the fact that a large number of devices and computer systems are connected to the Internet.
Shodan has since been used to find systems with low security precautions, including control systems for critical infrastructure such as water systems, power grids, and power plants. Many devices use trivial authentication criteria such as the user name “admin” and passwords such as “1234”. In many cases, the only software needed to connect to these systems is any web browser .
Media coverage
In May 2013, CNN Money published an article describing how SHODAN could be used to find systems on the Internet that could be compromised, including traffic light controls. In it were u. a. Screenshots of these systems with the warning banner "DEATH MAY OCCUR !!!" (Can cause death) shown when the connection is being established.
In September 2013, Shodan was referred to in a Forbes article. This claimed that it was used to find the security holes in TRENDnet surveillance cameras. The next day, a second Forbes article followed on the kind of things that can be found with Shodan. These included Caterpillar trucks whose onboard monitoring systems were accessible, heating and security control systems for banks, universities and businesses, surveillance cameras and fetal heart monitors.
In January 2015, the pros and cons of Shodan were discussed in an article on CSO Online . This article published Hagai Bar-El's opinion that Shodan is actually doing the public a good service, despite highlighting vulnerable devices. This perspective is also described in one of his essays.
In December 2015, various news outlets, including Ars Technica , reported that a security researcher had used Shodan to find MongoDB databases available on thousands of systems , including one from Kromtech, the developer of the MacKeeper OS / X security tool . It would have been possible to access data from 13 million users.
use
The website searches the Internet for publicly accessible devices that have at least one open port . Shodan currently delivers ten results to users without and 50 to those with a user account. If users want to remove the restriction, they must provide a reason and pay a fee. Shodan's primary users are cyber security specialists, researchers, and law enforcement agencies.
Automated search tools
Bulk searching and processing of SHODAN queries can be performed with SHODAN Diggity (part of SearchDiggity, Bishop Fox's free collection of search engine attack tools). The free tool offers an easy-to-use scan interface via the SHODAN API.
SHODAN Diggity provides a convenient list of 167 search queries in the SHODAN Hacking Database (SHDB), a ready-made dictionary file. It supports various technologies such as webcams, printers, VoIP devices, routers , toasters, switches and even SCADA / industrial plant controls (ICS), to name just a few.
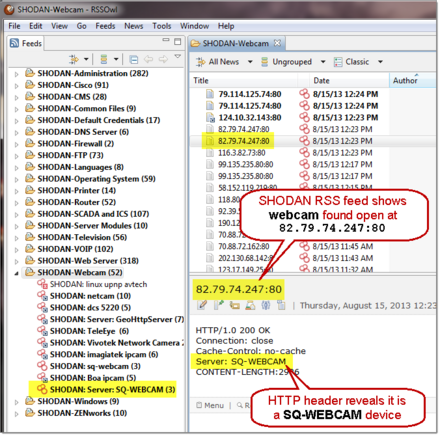
Continuous monitoring via RSS feeds
SHODAN Hacking Alerts are live reports via RSS feeds about vulnerable systems that regularly provide search results from the SHODAN search. Bishop Fox's free Defensive Tools integrate SHODAN data into their own security alerts using the feature to convert SHODAN search results into RSS feeds by &feed=1appending them to common SHODAN query URLs. As an an example:http://www.shodanhq.com/?q=Default+Password&feed=1
These free notifications via RSS can be used to keep a constant eye on SHODAN results for any new security threats related to organizations. They are part of the Google Hacking Diggity Project's free defensive tool suite, which form a type of intrusion detection system for search engine hacking (including results from SHODAN, Google , Bing , etc.).
literature
- Chris Baraniuk, The internet of unprotected things , New Scientist No. 3073, (eng.) Interview with John Mattherly
Web links
- shodan.io Homepage of Shodan
Individual evidence
- ^ SHODAN Help . SHODAN. Archived from the original on January 20, 2013. Retrieved June 21, 2013.
- ↑ SHODAN FAQ . SHODAN. Archived from the original on February 28, 2010. Retrieved June 21, 2013.
- ↑ Shodan: The IoT search engine for watching sleeping kids and bedroom antics. zdnet.com.
- ↑ a b Robert O'Harrow Jr .: Search engine exposes industrial-sized dangers . In: The Sydney Morning Herald . June 3, 2012 ( com.au ).
- ↑ a b Robert O'Harrow Jr .: Cyber search engine Shodan exposes industrial control systems to new risks . In: The Washington Post . June 3, 2012 ( washingtonpost.com [accessed April 8, 2013]).
- ^ A b c David Goldman: Shodan: The scariest search engine on the Internet. CNNMoney, April 8, 2013, accessed December 3, 2016 .
- ^ David Goldman: Shodan finds the Internet's most dangerous spots. CNNMoney, May 2, 2013, accessed June 21, 2013 .
- ^ Kashmir Hill: Camera Company That Let Hackers Spy On Naked Customers Ordered By FTC To Get Its Security Act Together . Retrieved October 17, 2013.
- ^ Kashmir Hill: The Crazy Things A Savvy Shodan Searcher Can Find Exposed On The Internet . Retrieved October 17, 2013.
- ↑ Shodan exposes IoT vulnerabilities . Retrieved January 13, 2015.
- ↑ Shodan makes us all more secure . Retrieved January 13, 2015.
- ↑ Andrii Degeler: 13 million MacKeeper users exposed after MongoDB door was left open .
- ↑ Martin Brinkmann: Shodan, a search engine for vulnerable Internet devices . In: ghacks.net . April 9, 2013. Retrieved April 9, 2013.
- ^ Francis Brown, Rob Ragan: Tenacious Diggity: Skinny Dippin 'in a Sea of Bing . DEF CON July 20, 2012. Archived from the original on July 13, 2012.
- ^ SHODAN Diggity . Bishop Fox. Retrieved June 21, 2013.
- ↑ SHODAN Developer API . SHODAN. Retrieved June 21, 2013.
- ^ SHODAN Diggity . Bishop Fox. Retrieved June 21, 2013.
- ^ SHODAN Hacking Alerts . Bishop Fox. Retrieved June 21, 2013.
- ^ Google Hacking Diggity Project . Bishop Fox. Retrieved June 21, 2013.