Ring (CPU)
The ring , also known as the domain , designates (in the context of operating system programming and multitasking ) a privilege or security level for the program code currently running . This restricts the code with respect to the to the CPU useful instruction set and the usable storage area is an optionally. The use of privilege levels makes sense to abstract the hardware and to isolate processes from each other and from the operating system and drivers .
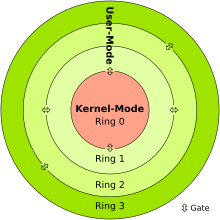
In the innermost ring (highest authorization level) the operating system is usually running , possibly even just its kernel . The operating system “is allowed to do everything”, especially direct hardware access and access to the RAM areas of other processes. Application programs are usually restricted to the outermost ring (lowest authorization level). For operations that require hardware access, application programs must commission operating system services.
implementation
The instruction set is restricted for unprivileged processes (“userland”) in such a way that they cannot access the hardware directly and cannot free themselves from their privileged level. Access to the memory area of other processes is usually prevented by memory virtualization . This ensures that program code in outer rings cannot unauthorized access to program code or data of the kernel and other system services in inner rings. The same storage virtualization is also commonly used to isolate different processes from one another. Since the unprivileged processes cannot access hardware directly, there are so-called " gates " with which program code from outer rings can call program code from inner rings. In particular, the programming interface of the kernel can be reached in this way in order to request the necessary actions.
Most processor architectures provide only two rings: program code in ring 0 is located in the kernel mode (Engl. " Kernel mode " ), kernel space (Engl. " Kernel space " or is) Super User Code (Engl. " Superuser code " ) - everyone else in the user mode (engl. " user mode " ) or user space (engl. " userspace " ).
Sequence of an operating system call
A process (running with low authorization) selects the function of the operating system to be carried out by setting CPU registers and memory areas appropriately and sets the required parameters. Then it triggers a software interrupt via CPU command . This interrupts the process, the CPU switches to the innermost ring ("kernel mode") and continues execution with a special operating system routine. This first saves further (CPU) states that have not already been saved by the CPU itself as part of the software interrupt, for example to have free registers for its own execution. It then acts in accordance with the requested job: it transfers it to the responsible driver, queues it for processing by a kernel thread, or it can possibly execute the job itself. In the first two cases, a complete context change to another process is then usually carried out, since the calling process can only continue when the operating system has completely processed the job. As soon as the job has been completely processed, the operating system routine stores the return values in the memory areas of the process and, if necessary, notes further return values for certain CPU registers in its process context. The requesting process is marked as "ready" and later resumed as part of the regular scheduling (by means of a context change): A special CPU instruction completes the context change, the CPU "returns from the software interrupt", whereby the CPU returns to the user -Mode (outermost ring) changes back and continues the execution of the low-privileged process immediately after the point of interruption.
requirement
There must be circuits in the CPU and, if applicable, the MMU that check with each command or memory access whether this is permitted in the current ring. If a process wants to do something that is not permitted, it is interrupted and an operating system routine is called, whose task it is to react accordingly.
x86 processor systems
Intel 80286 -compatible processors differentiate between four privilege levels: Ring 0, 1, 2 and 3. Ring 0, called " supervisor mode ", represents the highest privilege level, which is increasingly restricted up to level 3 (ring 3). Examples of assembler instructions that may be executed in ring 0 but not in ring 3 include: B. "cli" and "sti". These instructions are used to switch the handling of (maskable) hardware interrupts on or off. The rings were originally intended for the kernel (ring 0), drivers (ring 1), system services (ring 2) and application programs (ring 3).
To allow processes to run in a protected area (ring> 0), the physical main memory is divided into virtual memory pages . For each memory page there is a table which, among other things, stores the level (ring) in which the program code, which is stored within this memory page, is executed. The MMU usually carries out this evaluation externally.
With the introduction of the AMD64 - opcodes that even Intel for some of its processors as Intel 64 acquired exists in Speicherseitendeskriptor addition, the NX - Flag (English ". No eXecution "), which allows a distinction between data and program code so vulnerabilities to be prevented by buffer overflows . The buffer overflow is not prevented directly, but program code in data pages cannot be executed.
Change between the rings
There are three gate types available for changing the ring, which require different amounts of computing time when used, since every change from one ring to the other also represents a context change of at least some states in the CPU:
- Call gates for calling program code directly from higher privilege levels. The call gate determines at which point and with what privileges the called program code will run. For security reasons, the program code from the higher privilege level is assigned its own stack , the call parameters from the stack of the calling code are copied to the new stack. Otherwise, the privileged code runs in the context of the calling code.
- Interrupt gates are used when triggering a so-called software interrupt, but hardware interrupts also require an interrupt gate. In addition to all the steps that are carried out when using a call gate, the flags register is also stored on the stack and further interrupts are blocked until the interrupt routine returns.
- Task gates allow control to be passed on to another process. This is the most complex form of context change, since the complete processor status of the calling process has to be saved and the called process has to be loaded.
Operating systems on x86
The common operating systems for x86 Linux and Windows (as well as macOS for x64 and DOS with EMM386.EXE memory manager) only use two of the four possible CPU rings. The kernel and all hardware drivers are executed in ring 0, while the application software works in unprivileged ring 3. This guarantees the portability of the operating system even on processor architectures that can only differentiate between two rings. However, OS / 2 uses Ring 2 for graphics drivers. A specially adapted version of the EMM386 memory manager from the development kit for DOS Protected Mode Services (for Novell DOS 7, OpenDOS 7.01 and DR-DOS 7.02 and higher) allows DPMS to run on ring 1 instead of ring 0, making it easier to troubleshoot software that DPMS uses.
The increasingly used virtualization solutions also use ring 1. Here, the operating system kernel is moved from ring 0 to ring 1, the hypervisor then resides as the layer above in ring 0 and manages one or more operating system cores running in ring 1. However, this can also be exploited by rootkits to allow malicious code to run unnoticed by the user on Ring 0 (see also Virtual Machine Based Rootkit ).
In order to simplify the use of hypervisors, newer CPUs from Intel and AMD introduce a new "ring -1", so that the operating system kernel remains in ring 0 while the hypervisor resides as the layer above it in ring -1. It manages one or more operating system cores in ring 0.
Non-x86 systems
The division into four rings made with x86 processors was used earlier, e.g. B. at VAX . The Alpha processor supports an additional protected area for its PAL code , which could be interpreted as ring −1. The Honeywell 6180 , the first system with hardware support for this concept, had eight rings.
With many current processors, a distinction is often only made between supervisor mode (“everything is allowed”) and user mode (restricted access to memory areas / system resources / CPU registers). The main memory is protected by the page management unit MMU of the CPU.
This principle can also be applied to x86 systems in that the memory is created as flat memory via segmentation . The CPU only runs in privilege levels 0 and 3.
Individual evidence
- ↑ Presentation Device Driver Reference for OS / 2 ( Memento of the original from June 16, 2013 in the Internet Archive ) Info: The archive link was automatically inserted and not yet checked. Please check the original and archive link according to the instructions and then remove this notice. on warpspeed.com (English)