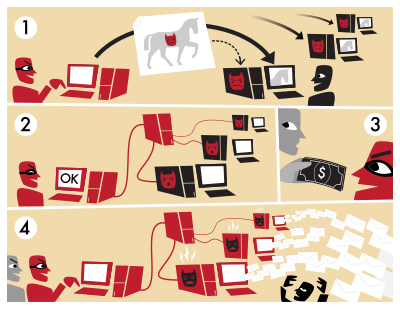
Botnet
A botnet or botnet is a group of automated malicious programs known as bots . The bots (from English: robot "robot") run on networked computers whose network connection as well as local resources and data are available to them without the consent of the owner. In 2010 there were over 470,000 such bots in Germany, of which an average of around 2,000 were active per day. In 2014, the botfrei.de initiative of the Association of the Internet Industry (ECO) found 92,000 contaminated systems with around 725,000 infected files from 220,000 randomly examined computers, which results in an infection of around 40 percent of all computers in Germany. According to the 2015 report on the IT security situation in Germany by the Federal Office for Information Security (BSI) , up to 60,000 systems were infected every day in Germany in the first half of 2015. Operators of illegal botnets install the bots on computers without the knowledge of the owner and use them for their own purposes. Most bots can be monitored by a botnet operator (also called bot master or bot herder) via a communication channel and receive commands. This is known in technical terms as a command and control server; Short form: C&C server.
Applications
A bot provides the operator of a botnet with various services depending on the range of functions. Meanwhile, multifunctional botnets are increasing. The botmaster can flexibly switch to other uses. Basically, the possible uses of a bot network can be distinguished as follows:
- Reloading and execution of further programs or updating of the bot
- Attacks to the detriment of an external victim system
-
Proxy
- Proxies offer the possibility of establishing a connection to a third computer via the zombie and can thus hide the actual origin address . The intermediate host created in this way can then be used for further attacks on other computers. From the point of view of the target computer, the attack comes from the proxy host.
- Sending spam e-mails , especially Phishing Emails
- Executing DDoS attacks and DRDoS attacks
- Many bots can carry out DoS attacks . In most cases, different methods such as SYN flood or HTTP request flood are available. If these attacks are carried out simultaneously by all bots in the network with the entire network bandwidth available to them, network services on the target computer of the attack are deactivated or the entire bandwidth of its connection is required for data from the zombies.
- Executing click fraud
- Another way of using an operational botnet for financial gain is called click fraud. To do this, the fraudster uses an account with an online service provider, which reimburses its advertising partners for clicks on advertising banners or referring visitors. The fraudster uses the bots to click the banners or to visit the paid website. This is done with the computer-specific information such as the operating system, browser and IP address of the hijacked computer and is therefore not recognizable as fraud for the advertising portal operator.
-
Proxy
- Internal botnet attacks
- Access to locally stored data through the use of sniffers and password grabbers
- The private data of computers ( zombies ) infected with bots are lucrative. Most bots offer options for accessing locally stored access data for various applications ( e.g. IE or ICQ ). Bots specializing in data theft also offer functions to read data from web forms and can thus spy on information entered into SSL-secured websites, including passwords or credit card numbers. Many IRC bots can log the computer's network traffic.
- Use as ransomware
- Storage medium for the distribution of illegal content (e.g. file sharing of protected material)
- Use of computing power (e.g. for Bitcoin mining)
- Access to locally stored data through the use of sniffers and password grabbers
Bot-nets provide an excellent infrastructure for conventional Internet crime . This is also the reason for their rapid growth.
Command and control technology
The vast majority of bots offer a means of communication with the operator of the botnet, whereby so-called command and control servers (from English ' command and control server ' ; short C&C servers or C2) are used. This includes getting data from a bot as well as distributing new instructions.
IRC C&C
IRC became a popular internet chat solution in the 1990s. Legitimate and useful bots, such as Eggdrop , are designed to help users manage IRC and communications. This simple technique then became the first C&C strategy. When communicating via an IRC channel , the bots establish a client connection to an IRC server . Orders are carried out by the bots without delay, and the operator receives an immediate response from the bots. An IRC C&C server is very easy for a bot operator to create and manage. If a computer is infected, the zombie tries to connect to the IRC server and channel. If the connection was successful, the bot operator can control the bot. This can be done individually via private messages or globally to all zombies within the channel. To make this more efficient, some bot operators create a “topic” for the channel, which represents a command for the bots, such as performing updates or a DDoS attack.
Advantages of the IRC technology:
- It's interactive: although it's a relatively simple protocol, IRC is interactive and allows full duplex communication between the client and server.
- Creating an IRC server is easy. There are also a large number of existing servers that can be used if necessary.
- It is possible to create and control multiple botnets using one server. Functionalities such as nicknames, chat channels, password-protected channels etc. make this possible.
- It's easy to build redundancy by connecting multiple servers together.
DNS and C&C
Followed by the use of private servers and passwords, C&C techniques continued to improve. The first technique uses several interconnected IRC servers using standard IRC technology. IRC is designed in a way that multiple servers can be linked together to form a network of servers. When using this technology, the addresses of all servers are permanently entered in the bot. This then tries to connect to each of these entered addresses. Once a connection has been established between the server and the client, the bot logs on to the channel in which the bot operator gives instructions. It becomes difficult for botnet hunters to paralyze the entire network, especially when new servers are added over and over again. If the addresses of the C&C server are permanently implemented in the bot, it can no longer reach the server if the addresses are blocked. As you can see, this technique has its limits, which is why DNS records were introduced.
DNS is divided into domain names and multihoming. The difference between the two is that with domain names different domains point to the same IP address, while with multihoming a domain points to several different IP addresses.
The introduction of domain names and multihoming helped the bot herders to increase the reliability of the C&C servers.
Web-based C&C
Tools can be bought for a few hundred dollars or less these days. These tools usually contain malicious code that is individually adapted to web-based security vulnerabilities and that cannot be detected by the antivirus programs, and a web-based command and control engine that contains a backend database for storing stolen information. Since the user interface of web-based C&C is very easy to use, it is very popular with many bot-herders.
Bots can be configured to repeatedly send SYN packets to the C&C server so that the server can get the zombies' IP addresses. With the help of this IP address, the attacker can send encrypted bot commands and data to the client.
Communication via HTTP with a web application works without a persistent connection, the bots transfer data and ask for new commands at intervals. HTTP botnets are enjoying increasing popularity, as setting up the administration infrastructure is easier compared to an IRC server and communication between the bots is less noticeable.
Some botnets automatically install reverse proxies on infected systems in order to conceal the true location of the C&C server. The infected systems pass the requests on several times, similar to the principle of TOR .
Web-based C&C has the following advantages over the traditional IRC solution:
- Hide in traffic for port 80: Almost all companies allow TCP port 80 for normal web activities over the network. The requests from bots to a website go undetected. This is a big advantage over IRC and P2P C&C solutions.
- “Pushes” instead of “Pulls”: With IRC, the bots connect to the server and wait for instructions. With Web-C&C, the server connects to the bots. This reduces the traffic between the C&C server and the bot and thus the chance of detecting a bot on a network.
- Scalability and usability: A single web server can manage several hundreds of thousands to millions of bots. In most cases, traditional IRC channels can only manage several thousand bots before they are overloaded. In addition, web-based C&Cs are easier to use for the average bot operator than the more complicated IRC C&C technique that requires self-programming. Nowadays you can buy solutions that not only contain a management function for the bots, but also a management program for the stolen data.
There are two types of web-based botnets:
- Echo-Based: Echo-Based means that the bot reports its existence to the C&C server.
- Command-Based: Command-Based is a web service or web application that is supposed to help operate a botnet more efficiently.
P2P botnets
Peer-to-peer networks have become increasingly popular through services such as music and file sharing. Within a few years of the first bots emerging, bot herders started creating their own P2P networks to manage bots. This technology is a very efficient way for the bot operator to manage his botnets without a central control structure. The zombies can act as both client and server, meaning any node can give and receive commands. Every single node of the P2P network can be reached by the bot operator, who can then control the entire network. For example, the bot operator can connect to a zombie and cause it to update. This starts a chain reaction: all other bots in the P2P network also download the update and synchronize with each other according to the configuration file that the hacker imported into the zombies. It is practically impossible to identify an attacker in such a distributed P2P network solution. On the other hand, a simple peer can find other bots. P2P networks are generally easier to spot based on the network traffic that the zombies generate.
FTP-Based C&C
As with many other protocols, FTP has been experimented with as a control channel. Nowadays this species is not often found. However, there is one type of bottom that regularly reports FTP C&C, and that is the phishing or banking trojan. These bots, such as Dumador or Haxdoor , are basically keyloggers, with the difference that they are much more extensive. They monitor (“sniffing”) the data traffic when the user surfs the Internet on the compromised system. If the user enters an encrypted website (HTTPS), they carry out a man-in-the-middle attack on the computer itself. Since this attack takes place in the victim machine itself, it is often called a man-on-the-inside attack. The bot presents the user with a fake website. With this technique, it is possible to record authentication data, etc. The stolen data is then uploaded to an FTP server where the bot operator can wait for it. Bot operators usually produce detailed statistics about the data and its origin.
The top 10 countries where botnet command and control servers were identified in 2008 were:
- United States: 16,774
- Germany: 3,909
- China: 2,998
- Russia: 2,960
- Canada: 2,388
- Great Britain: 1,703
- South Korea: 1,151
- France: 985
- Malaysia: 857
- Japan: 788
Distribution of the bots (spreading)
A botnet is expanded by installing the bots on a computer that is not yet connected. In order to have as many resources as possible available, the operators try to get a large number of computers under their control. The installation is usually invisible to the user. During the operation of a botnet, new computers are constantly being added; on the other hand, computers where the bot has been removed are eliminated.
The dissemination takes place in the following ways:
-
Malware
- The bot's installer is emailed to many addresses and the recipient is asked to run the program on their computer. Sometimes only a link to an infected website is sent.
-
Downloads
- The bot is a so-called Trojan horses (actually Trojan Horse) bundled with an application that downloads the user voluntarily performs at his computer. Often it is illegal programs like Cracks , Warez or other questionable software. More and more often, however, legal offers are also being hacked and infected with a Trojan.
-
Exploits
- The bot is installed by exploiting a security gap in the operating system , in the browser or in an application on the computer. Bots installed via exploits often have an automatic propagation function ( computer worm ). Some exploits require user interaction, such as B. clicking on a prepared link to execute the malicious code. Other exploits are triggered automatically when the page is called up ( drive-by infection ). It happens that popular websites are hacked and provided with malicious code or that the exploit is loaded from another server via an advertising banner .
- Manual installation
- The bot is manually installed on a computer after a break-in. This is mainly used with servers. Due to their high availability and the mostly good network connection, it is particularly worthwhile to look specifically for weaknesses.
According to a 2008 study by the antivirus manufacturer Kaspersky Lab , every tenth PC was part of a botnet. That would make them one of the largest illicit sources of income on the internet.
The annual statistics from botfrei.de show that in 2014 40% of 220,000 scanned computers were infected with bots. In the course of the year, almost 725,000 infected files were discovered on more than 92,000 infected systems. This is an alarming value and represents an increase over the previous year.
Combating botnets
In general, preventive measures are recommended. A general protective measure, for example, is the choice of secure passwords for routers , networks and networked devices in the Internet of Things . The Federal Office for Information Security also recommends, for example, deactivating the UPnP function on routers in order to prevent devices from being misused as part of botnets for denial of service attacks.
- As the BKA announced on December 30, 2014, after preliminary investigations, it had succeeded in breaking up a botnet. It consisted of 11,000 computer systems from over 90 countries, of which more than half of the infected systems were in Germany. Through cooperation with the BSI , the Fraunhofer Institute (FKIE) and two German antivirus manufacturers, it was possible to notify the computer owners whose computers were part of the botnet via their telecommunications service providers , to give them help in cleaning up the infected computers and to give them advice on To issue complaints.
- European police forces and software companies broke up a global botnet called “Ramnit” in February 2015 with more than three million infected computers, mostly in the UK. "Ramnit" had been used to steal millions of passwords and bank details. Software companies such as Microsoft , Symantec and AnubisNetworks were also involved in the break-up operation, which was led by the European police authority Europol in The Hague. Police officers from Germany, Italy, the Netherlands and Great Britain took part in the action. According to operations manager Paul Gillen, it was possible to turn off the hackers' control servers in several European countries. The perpetrators have lost control of their infrastructure, he said. The botnet has existed since 2012 and the malware to integrate the computers into the botnet had reached the computer via links in spam e-mails or through infected websites .
- Scientists from Ben Gurion University who do research in the "Deutsche Telekom Innovation Laboratories" succeeded in February 2016 in developing a program that can detect botnets using honeypots . Dudu Mimran, Technical Director of “InnovationLabs @ BGU”, explained that a breakthrough in the automatic detection of botnets had been achieved. The program can be used to determine whether an attack is coming from a real person or a bot. So it was finally possible (through machine learning ) to develop algorithms that led to the detection of six different botnets so that the law enforcement authorities could be informed.
- At the end of 2016, under the direction of the Verden Public Prosecutor's Office, in cooperation with the Federal Office for Information Security , Eurojust , Europol , the FBI , Fraunhofer FKIE and other partners, the Avalanche botnet infrastructure was smashed. As part of the takedown, more than 800,000 domains were seized.
Largest botnets
| Known since | Switched off since | Surname | Maximum number of bots | Billions of spam emails a day |
Other names, remarks |
|---|---|---|---|---|---|
| May 2009 | October 2010 | BredoLab | 30,000,000 | 3.6 | Oficla |
| May 2009 | December 2009 | Mariposa | 13,000,000 | ? | Bots in 190 countries; collected data from over 800,000 internet users, u. a. Website credentials |
| October 2008 | - | Conficker | 9,000,000 | ? | DownUp, DownAndUp, DownAdUp, Kido |
| 2006 | March 2011 | Rustock | 1,700,000 | 44.1 | RKRustok, Costrat |
| January 2007 | - | Cutwail | 1,600,000 | 74 | Pandex, Mutant, Pushdo |
| March 2007 | - | Srizbi | 1,300,000 | 60 | Cbeplay, exchanger |
| June 2017 | Sivad | 1,100,000 | ? | Bitcoin miner, keylogger | |
| ? | July 2012 | Grum | 1,100,000 | 39.9 | Tedroo |
| 2004 | - | Bagle | 780,000 | 17.3 | |
| August 2009 | - | Maazben | 770,000 | 4.8 | |
| ? | - | Gheg | 500,000 | 0.44 | Tofsee, Mondera |
| ? | - | Octopuses | 400,000 | 9 | Crack |
| ? | - | Bobax | 370,000 | 14.6 | Bobic, Oderoor, Cotmonger |
| end of 2009 | - | Lethic | 350,000 | 2 | |
| August 2009 | - | Festi | 220,000 | 1.4 | |
| ? | - | Mega-D | 180,000 | 10 | Ozdok |
| ? | - | Torpig | 180,000 | ? | Sinowal, Anserin |
| January 2007 | - | Storm | 160,000 | 3 | Nuwar, Peacomm, Zhelatin |
| ? | - | Donbot | 125,000 | 0.8 | Buzus, Bachsoy |
| November 2008 | February 2010 | Waledac | 80,000 | 1.5 | |
| March 2009 | - | Cimbot | 48,000 | 1.9 | |
| ? | July 2012 | Grum | 120,000 | 18.0 | |
| September 2011 | - | Flashback | 670,000 | ? | Flashfake |
| June 2013 | Star Wars botnet | 350,000 |
Commercial use of botnets
Many forums openly advertise the implementation of bot attacks. The prices for 24-hour attacks range from $ 50 to a few thousand dollars.
See also
literature
- Ken Dunham, Jim Melnick: Malicious bots. An inside look into the cyber-criminal underground of the internet. CRC Press, Boca Raton FL et al. a. 2009, ISBN 978-1-4200-6903-7 ( An Auerbach Book ).
- Wenke Lee (Ed.): Botnet detection. Countering the largest security threat. Springer, New York a. a. 2008, ISBN 978-0-387-68766-7 .
- Craig A. Schiller, David Harley, Gadi Evron, Carsten Willems, Tony Bradley, Michael Cross, David Dagon: Botnets. The killer web app. Syngress, Rockland MA 2007, ISBN 1-59749-135-7 .
Web links
- The Anti-Botnet Advice Center - An initiative of the German Internet industry , botfrei.de
- Trojans 2.0 use Web 2.0 , Heise.de
- Vint Cerf - A quarter of Internet PCs are members of a botnet . Heise.de
- What are bots and botnets? RUS-CERT
- Lecture on the function and detection of botnets (PDF; 639 kB)
- GRC.COM: The Strange Tale of the Denial of Service Attacks Against GRC.COM ( Memento of November 28, 2007 in the Internet Archive ) (English)
- New threat from botnets with P2P structures . Heise.de
- Bruce Schneier : The Storm Worm . q-vadis.net (German translation of the essay)
- Analysis of the internal structure of a botnet (PDF; 138 kB; English)
- Peer-to-Peer Botnets: Overview and Case Study; further taxonomy of uses (English)
- BBC show 'Click' on botnet with Demonstration (English)
- The top 10 botnets
multimedia
- Is your PC doing a hacker's dirty work? (BBC, March 12, 2009 - video demonstration of a spam transmission via a botnet, 2:24 min. )
Individual evidence
- ↑ Symantec Security Report: Cybercrime is a German export hit. (No longer available online.) In: symantec.com. April 5, 2011, archived from the original on April 12, 2011 ; Retrieved April 12, 2011 .
- ↑ Botnets: 40 percent of PCs in Germany infected March 2, 2015 Spiegel Online retrieved May 13, 2016.
- ↑ The situation of IT security in Germany 2015 Federal Office for Information Security (PDF 1.39MB)
- ↑ C&C (command and control) - ITWissen.info , on October 27, 2014
- ↑ Statistical data, collected by Team Cymru , quoted from: Steve Santorelli, Levi Gundert: Safety net - Cybercriminals adapt to new security measures. In: Jane's Intelligence Review . March 2009, p. 40.
- ↑ Vitaly Kamluk: Botnet - Business with Zombies. In: Securelist. Kaspersky Labs GmbH, May 13, 2008, accessed February 12, 2016 .
- ↑ botfrei.de annual statistics 2014: More zombie computers on the net again. (No longer available online.) In: Press releases. eco - Association of the Internet Industry V., March 2, 2015, formerly in the original ; accessed on February 12, 2016 . ( Page no longer available , search in web archives )
- ↑ The bot in the baby monitor , Federal Office for Information Security from October 24, 2016, accessed on October 27, 2016.
- ↑ Successful strike against cyber criminals - BKA initiates deactivation of a botnet. (No longer available online.) In: Press Releases. Federal Criminal Police Office, December 30, 2014, archived from the original on February 15, 2016 ; accessed on February 12, 2016 .
- ↑ Police succeed in striking a worldwide hacking ring. In: Die Welt - Digital Cybercrime. WeltN24 GmbH, February 25, 2015, accessed on February 12, 2016 .
- ↑ Ulla Thiede: Every tenth PC is a "zombie". In: General-Anzeiger - Crime on the Internet. Bonner Zeitungsdruckerei und Verlagsanstalt H. Neusser GmbH, February 5, 2016, accessed on February 17, 2016 .
- ↑ 'Avalanche' network dismantled in international cyber operation. In: press releases. Europol, December 1, 2016, accessed June 6, 2018 .
- ↑ 'Avalanche' network dismantled in international cyber operation. In: press releases. Europol, December 1, 2016, accessed June 6, 2018 .
- ↑ Spy swallows spy | heise security. (No longer available online.) In: heise.de. Archived from the original on March 19, 2011 ; Retrieved March 19, 2011 .
- ↑ BredoLab downed botnet linked with Spamit.com . Infosecurity (UK)
- ↑ a b Mariposa Analysis.pdf. (PDF; 340 kB) (No longer available online.) In: defintel.com. Archived from the original on March 19, 2011 ; Retrieved March 19, 2011 .
- ↑ Computer crime: Spanish police unearth huge bot network . Mirror online
- ↑ Botnets: Dark attack by zombie computers GBS Blog
- ^ Calculating the Size of the Downadup Outbreak , F-Secure Weblog
- ↑ Rustock botnet out of action | heise security. (No longer available online.) In: heise.de. Archived from the original on March 19, 2011 ; Retrieved March 19, 2011 .
- ↑ a b c d e f g h i MessageLabs Intelligence: 2010 Annual Security Report. (PDF) Retrieved January 14, 2011 .
- ↑ a b c August 2010 Report. (PDF) MessageLabs Intelligence, accessed January 14, 2011 .
- ↑ a b c d e f g MessageLabs Intelligence: 2009 Annual Security Report. (PDF) Retrieved January 14, 2011 .
- ↑ Pushdo Botnet - New DDOS attacks on major web sites . ( Memento from August 16, 2010 in the Internet Archive ) Harry Waldron - Computer Security News
- ↑ a b 2008 Annual Security Report. (PDF) MessageLabs Intelligence, accessed January 14, 2011 .
- ^ Spam on rise after brief reprieve. BBC News | Technology
- ↑ darkreading.com
- ↑ a b c messagelabs.com (PDF)
- ↑ Researchers hijack control of Torpig botnet ( Memento of May 11, 2011 in the Internet Archive ), SC Magazine US
- ^ Spam Botnets to Watch in 2009 - Research - SecureWorks. (No longer available online.) In: secureworks.com. Archived from the original on March 21, 2011 ; Retrieved March 21, 2011 .
- ↑ A botnet works, the spam remains | heise security. (No longer available online.) In: heise.de. Archived from the original on March 21, 2011 ; Retrieved March 21, 2011 .
- ↑ a b c Botnet Grum switched off. In: golem.de. Retrieved July 12, 2012 .
- ↑ zdnet.de
- ↑ Motherboard Staff: The biggest social botnet to date has been exposed — it only tweets about Star Wars. In: Vice. January 13, 2017, accessed March 25, 2020 .
- ↑ Shadow economy botnets - a million dollar business for cyber criminals . Viruslist.com, July 22, 2009.