Signal protocol
The Signal Protocol (formerly Axolotl Protocol ) is a cryptographic communication protocol for end-to-end encrypted exchange of messages such as instant messaging . In contrast to the related OTR protocol, the signal protocol does not require both communication partners to be online at the same time. This is especially important for instant messaging on smartphones.
The aim of the signal protocol is not only to encrypt the connection, but also to limit the damage if one of the participants is compromised. If two users were to always use the same key to encrypt messages, an attacker who came into possession of the key could also decrypt previously sent messages if he had saved them. To prevent this, short-lived session keys are used for encryption, which are frequently renewed in a special process known as double ratchet . By renewing the keys, an attacker who knows individual session keys can no longer decrypt future messages. Because of this property, the developers call the protocol self-healing. The former name alluded to the endangered, aquatic tailed amphibian axolotl , which has extraordinary self-healing abilities.
On March 30, 2016, Moxie Marlinspike announced that the then Axolotl protocol had been renamed Signal Protocol to avoid misunderstandings. It follows the previous standardization of the names of today's communication app Signal .
origin
The protocol was developed by Trevor Perrin with the assistance of Moxie Marlinspike ( Open Whisper Systems ) and introduced in TextSecure (now Signal ) in 2013 . The design is based on the renewal of session keys introduced by Off-the-Record Messaging through repeated Diffie-Hellman key exchange (DH ratchet) combined with key derivation using a cryptological hash function (hash ratchet) based on the Silent Circle Instant Messaging Protocol ( SCIMP).
properties
The signal protocol ensures the features that have long been common in end-to-end encryption systems, encryption of the content along the entire transport route, as well as authentication of the remote station and protection against manipulation of the messages.
It adopts the features provided by OTR Messaging of retroactive consequences for the disclosure of the secret master key, protection of the following messages after the disclosure of a session key and the credible denial of the authorship of a message. In addition, the use of a key derivation function allows the session key material to be renewed even without interaction with the remote station. A further key derivation step enables keys to be held available without consequences for messages that arrive out of sequence.
It is intended to detect the rearrangement, omission and replay of sent messages and to improve the lack of consequences compared to OTR messaging.
In combination with one-off pre -keys generated in advance and held by a public key infrastructure (PKI), the initiation of a conversation session in the absence of the remote station ( asynchronous communication ) can be supported. The use with triple Diffie-Hellman key exchange (3DH) as an initial key exchange procedure (for example in the case of a signal) improves the deniability properties.
function
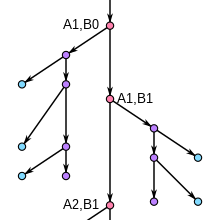
The developers called the central idea of the protocol double ratchet (from English ratchet: pawl ). When a participant sends again after a received message for the first time, he renews the session key material by means of a Diffie-Hellman key exchange, in which he combines his own new key with the key that is already known to the remote station (Diffie-Hellman-Ratchet) . Symmetrical keys are derived from the session key material using a key derivation function. Since the key derivation function is based on a hash function, this step is called hash ratchet . This construction allows new keys to be generated even if the remote station is not online.
For this purpose, the protocol forwards one of two hash ratchets (one for sending, one for receiving) for each message, which were initialized from a DH ratchet on the basis of a shared secret. At the same time, it tries to make a new public DH value available to the remote station at every opportunity and to push its own local DH ratchet on every time a new public DH value is received from the remote station. As soon as a new shared secret is available, a new hash ratchet is initialized from it.
The signal protocol uses as cryptographic primitives
- for the DH ratchet
- Elliptic Curve Diffie – Hellman (ECDH) with Curve25519 ,
- for message authentication codes (MAC, authentication)
- Keyed-Hash Message Authentication Code (HMAC) based on SHA-256 ,
- for symmetric encryption
- the Advanced Encryption Standard (AES), partly in Cipher Block Chaining Mode (CBC) with filler bits according to PKCS # 5 and partly in Counter Mode (CTR) without filler bits,
- for the hash ratchet
- HMAC .
use
In the Signal communication software , it is used on hundreds of thousands of end devices. At the end of 2013, the integration into the text messaging function of the independent Android operating system CyanogenMod from version 11 was announced, which at that time had 10 million users. In November 2013 it was integrated into the experimental asynchronous messaging system Pond. In September 2014, the integration into WhatsApp made headlines. Thanks to a cooperation with Open Whisper Systems, the protocol from version 2.11.448 is included in the Android version of the messenger. With the merging of the chat application Silent Text in the telephone application Silent Phone with the publication of September 28, 2015, Silent Circle replaced its own SCIMP protocol with the Signal protocol. In 2015, as part of a Google Summer of Code project, an extension to the Extensible Messaging and Presence Protocol (XMPP, "Jabber") called "OMEMO Multi-End Message and Object Encryption" ( OMEMO ) was developed, which uses the signal ratchet integrated. It was introduced in the Android Messenger Conversations and submitted to the XMPP Standards Foundation (XSF) for standardization in the fall . The use of the signal protocol in G Data Secure Chat is also known. Since the beginning of April 2016, WhatsApp has been encrypting all communications across systems ( Android , iOS , Windows Phone , Nokia S40 , Nokia S60 , Blackberry and BB10 ) using the Signal protocol. With Facebook Messenger , the protocol is used for the optional “secret conversations”, just like with Google Allo in “incognito mode”.
However, security experts also see weaknesses here if their own servers are used, as in the aforementioned commercial products. In particular, messages in group chats can be read out despite functioning end-to-end encryption. Users would therefore always have to trust the service provider. WhatsApp takes on the underlying end-to-end encryption from Signal, but implements the group chat infrastructure based on it differently. An attacker only needs control over the messenger's control server. Finally, the WhatsApp owner Facebook could also be obliged by US law to give investigative authorities secret access to the relevant servers.
literature
- Nik Unger, Sergej Dechand, Joseph Bonneau, Sascha Fahl, Henning Perl, Ian Avrum Goldberg, Matthew Smith: SoK: Secure Messaging . In: IEEE Computer Society's Technical Committee on Security and Privacy (Ed.): Proceedings of the 2015 IEEE Symposium on Security and Privacy . 2015, p. 232-249 ( ieee-security.org [PDF]).
Web links
- specification
- " Advanced cryptographic ratcheting " (in English), abstract representation of Moxie Marlinspike
Individual evidence
- ^ Moxie Marlinspike: Advanced cryptographic ratcheting. In: whispersystems.org. Open Whisper Systems, November 26, 2013, accessed on January 11, 2016 (English): "The OTR style ratchet has the nice property of being 'self healing.'"
- ↑ Open Whisper Systems >> Blog >> Signal on the outside, Signal on the inside. In: www.whispersystems.org. Retrieved April 1, 2016 .
- ^ Tilman Frosch, Christian Mainka, Christoph Bader, Florian Bergsma, Jörg Schwenk, Thorsten Holz (Ruhr University Bochum): How Secure is TextSecure? In: Cryptology ePrint Archive . Report 2014, No. 904 , 2014 ( iacr.org [PDF]).
- ↑ Andy Greenberg: Ten Million More Android Users' Text Messages Will Soon Be Encrypted By Default , Forbes. December 9, 2013. Retrieved February 28, 2014.
- ↑ Seth Schoen: 2013 in Review: Encrypting the Web Takes A Huge Leap Forward , Electronic Frontier Foundation. December 28, 2013. Retrieved March 1, 2014.
- ↑ Moxie Marlinspike: TextSecure, Now With 10 Million More Users , Open Whisper Systems. December 9, 2013. Retrieved February 28, 2014.
- ↑ Contribution by Adam Langley from November 9, 2013 in Pond: "Wire in new ratchet system"
- ↑ Christian Schartel: WhatsApp for Android: after update with encryption. In: CNET.de. November 19, 2014, accessed January 17, 2016 .
- ↑ What is Silent Phone? In: support.silentcircle.com. Silent Circle, September 17, 2015, accessed January 17, 2016 .
- ^ Andreas Straub: OMEMO Encryption. (No longer available online.) In: XMPP Standards Foundation website. October 25, 2015, archived from the original on January 29, 2016 ; accessed on January 4, 2016 . Info: The archive link was inserted automatically and has not yet been checked. Please check the original and archive link according to the instructions and then remove this notice.
- ↑ Daniel Gultsch: OMEMO Encrypted Jingle File Transfer. In: XMPP Standards Foundation website. September 2, 2015, accessed January 4, 2016 .
- ↑ Tara Seals: G DATA Adds Encryption for Secure Mobile Chat . In: Infosecurity Magazine . Reed Exhibitions Ltd .. September 17, 2015. Accessed September 18, 2015.
- ↑ heise Security: WhatsApp: encryption unlocked for everyone. In: Security. Retrieved April 12, 2016 .
- ↑ WhatsApp: WhatsApp Security Whitepaper. April 4, 2016, accessed April 12, 2016 .
- ↑ WhatsApp and Signal: Researchers describe weaknesses in encrypted group chats , heise online from January 16, 2018, accessed on April 20, 2018