Phishing
The term phishing ( neologism of fishing , English for 'fishing') is understood to mean attempts to obtain personal data of an Internet user via fake websites , e-mails or short messages and thus to commit identity theft. The aim of the fraud is to use the data received to commit account deletion, for example , and to harm the relevant people. It is a form of social engineering that exploits the victim's good faith. The term is an English made-up word that is made up of password harvesting (collecting passwords) and fishing (angling, angling) and depicts the fishing for passwords with bait. The spelling with Ph- also comes from the hacker jargon (cf. phreaking ).
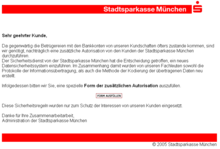
Typical is the imitation of the website of a trustworthy body, such as the website of a bank. In order not to arouse suspicion, the corporate design of the affected area is imitated, for example the same company logos, fonts and layouts are used. The user is then requested on such a fake page to enter the login data or transaction numbers for his online banking in a form . This data is then forwarded to the fraudster and used to plunder the account.
Phishing messages are mostly sent by email or instant messaging and ask the recipient to reveal secret access data on a specially crafted website or on the phone. Attempts to master the growing number of phishing attempts rely on changes in case law, user training and technical aids, among other things.
The first documented phishing attempt took place on January 2, 1996 in Usenet - newsgroup instead alt.online-service.america-Online, the term phishing but dipped may already before in the print edition of the hacker magazine 2600 on. The popular theory that phishing is a trunk word from password harvesting is an example of folk etymology .
history
Phishing is not a new phenomenon. In fact, there were similar attempts at fraud under the term social engineering long before e-mail and the Internet became common means of communication. Fraudsters tried, for example, by telephone to gain the victim's trust and coax confidential information from them. With the spread of inexpensive VoIP telephony, this procedure, now known as vishing , is once again becoming worthwhile for fraudsters. A current example of trickery scams used is the grandchildren's trick . The only new thing about phishing are the tools that enable it to spread far more widely.
The beginnings of phishing on the Internet go back to the late 1990s. At that time, users of instant messengers such as B. ICQ requested by e-mail to enter your access data in a form contained in the e-mail. With the access data obtained in this way, the fraudsters were able to use the chat accounts of their victims under their identity.
The first phishing attacks in the field of online banking began with the originator of a phishing attack sending his victim an e-mail that looked official, intended to induce him to include confidential information, in particular user names and passwords or PIN and TAN of online banking access to the perpetrator in good faith. If the visitor provides correct data, the fraudster can use the intercepted PIN and TAN to make a money transfer at the expense of the victim. This relatively simple method of intercepting account access data is only used comparatively rarely today, after most banks have improved their TAN systems.
Newer methods
At the present time, phishing scammers succeed in intervening in the communication path between bank customer and bank ( man-in-the-middle attack ) and access data that is never at the bank , primarily with the help of malware such as Trojan horses arrive. The detour of enticing bank customers to reveal their access data by sending an email is no longer necessary. This modern form of tapping account access data made it possible for the perpetrators to outsmart comparatively modern systems such as the iTAN procedure with indexed transaction numbers.
Phishing targets are access data, for example for online banking or online payment systems ( e.g. PayPal ), mail order companies, internet auction houses, web-based online advice , packing stations or dating sites . With the stolen access data, the originator of the phishing attack can take over the identity of the victim ( identity theft ) and act on their behalf. The misuse of personal data results in considerable damage in the form of financial losses (for example transferring amounts of money from third-party accounts), damage to reputation (for example the auctioning of stolen goods under someone else's name at online auctions) or damage due to expenses for clarification and reparation. There are only estimates of the amount of damage. As security experts from the IT security specialist RSA found out, there were around 280,000 phishing attacks in the US alone in 2011, an increase of 37 percent over the previous year. On average, the perpetrators were able to steal around 4,500 dollars with each attack.
Spear phishing
A more recent variant of phishing is called spear phishing (derived from the English word for spear ), which means a targeted attack. Here, for example, the attacker obtains the e-mail addresses of the students enrolled there via the student council of a university in order to send them a targeted phishing e-mail from a local bank or savings bank. The “hit rate” of this type of phishing attack is higher than that of normal attacks, since the probability that a student will have his bank account with this institute is very high. Next we talk in professional circles of Whaling ( substantiation of the English verb "to whale" with the meaning whaling ) when the targeted attack directed against high executives.
Pharming
A further developed form of classic phishing is pharming , which is based on the manipulation of DNS requests from web browsers.
Data collection methods
In general, a phishing attack begins with a personally held, official-looking e-mail or a mass sending of e-mails, whereby the recipient is always addressed with "Dear customer" instead of the actual name, which is usually known to the bank - one of the ways to detect phishing emails. The recipient is supposed to visit a fraudulent website that looks more or less deceptively real and asks for a pretext to enter his access data. The fake websites are usually recognizable simply from clumsy wording (often the result of a computer translation), orthographical or syntactic errors. Sometimes e-mails with fake senders can simply be recognized by the wrong language, for example when an allegedly German bank closes its circular with the greeting “Yours truly” or other inauthentic formulations. One can often recognize forgeries by the fact that the sender uses a wrong coding , so that instead of a special character from Western languages (for example German umlauts or letters with French or Italian accents) individual Cyrillic letters appear in a text coded in Latin. Most of the time, the victim is also lulled into a false sense of security by addressing the problem of data theft in the text and claiming that the form must be filled in so that a “new security concept” can take effect. If he follows this request, his access data will end up in the hands of the originators of the phishing attack. What then follows is only intended to dispel the victim's subsequent suspicion - a brief confirmation or a false error message.
In the more dangerous forms of attack, the malware resides on an infected website. This is then installed on the Internet user's computer simply by visiting the website. It is possible that a reputable website was infected without the operator's knowledge. In this case, there is no need to send an email.
Another variant integrates a form directly within an HTML e-mail, which asks you to enter the confidential data and sends it to the originator. There is no phishing website .
The Frankfurter Allgemeine Zeitung reported in 2009 on a man-in-the-middle attack by perpetrators from St. Petersburg who scanned 430 Internet node computers in 2008 and stole € 25 million in this way.
Methods of obfuscation
The e-mail is composed as an HTML e-mail, an e-mail with the graphic possibilities of websites. The link text shows the original address, while the invisible link target refers to the address of the fake website ( link spoofing ).
The ambiguity of visible characters can be exploited both in e-mails and in websites. In the fonts Calibri or Arial , the lower case letter “l” (12th letter of the alphabet) looks like the capital letter “I” (9th letter of the alphabet), the zero and the capital letter “O” can easily be confused, likewise Forgeries sometimes use the number “1” instead of the lowercase letter “l” (12th letter of the alphabet) and vice versa. This deceives the user about the real address of the sender of a mail or the real URL of a website.
With the integration of HTML, the link visible in the e-mail program can actually refer to a completely different website. Although it can be seen that the target of the link refers to another website, this information can also be falsified using scripting techniques if the e-mail program executes such scripts. In other cases the link is shown as a graphic in order to make text recognition more difficult by automatic filter systems. Text then appears on the user's screen, but it is a graphic.
Phishing usually also falsifies the sender's email address to make the email look more real. Phishing emails have also been observed to contain words that target Bayesian spam filters .
Web presence
The fake landing pages mostly have fake names or labels that sound similar to the official pages or companies. The landing pages with the web form look the same as the original pages. It is therefore very difficult to identify them as counterfeits.
With the ability to use internationalized domain names in URLs , new possibilities for URL spoofing emerged . For example, an original address could be http://www.oe-bank.example.com/ and a fake http: //www.ö-bank.example.com/. The two names are factually identical, but technically different, because they are resolved in the background to different addresses and can lead to completely different websites.
The use of similar looking letters from other alphabets ( homographic attack ) is even more difficult to recognize . For example, B. the Cyrillic "а" in the commonly used fonts optically in no way from the Latin "a". If the "a" in "http://www.bank.example.com/" is shown in Cyrillic, the address is different and therefore incorrect. However, the address line of the browser shows no visible difference to the original bank address.
The IDN Char Collision Detection (IdnCCD) protocol was developed as a generic protection protocol against phishing attacks based on IDNs .
There were Trojans discovered the targeted manipulation of the hosts first names file of the operating system. Computer-specific conversions can be stored in the hosts file. A manipulation of this file can mean that instead of the original page, only the fake page can be called up, even though the correct address has been entered. The DNS configuration entered in the router can also be targeted by malware. What is perfidious about this attack method is that the victim is forwarded to corresponding fake services regardless of the device.
Another method of phishing is access point spoofing, in which the attacker copies the identifier of a trustworthy wireless network so that the target can connect to a malicious access point. The latter method can be used both in local radio networks (W-LAN) and in cellular networks.
A study by the University of Cambridge ( The Impact of Incentives on Notice and Take-down , see literature) has shown that banks manage, on average, within four to eight hours to delete phishing websites around the world.
SMS (SMiShing)
This is done by SMS z. B. sent a "subscription confirmation". This includes an Internet address for logging out. B. smuggled a trojan.
protection
Since the HTML display and the use of scripts are used in most phishing e-mails, you can deactivate the HTML display and Java script in your e-mail program. Your own e-mails should also be sent at least as plain text so that the recipient can deactivate the HTML display in their e-mail program and thus protect themselves from phishing e-mails.
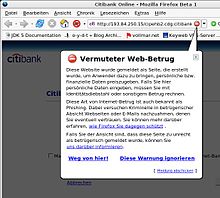

The email filters of some antivirus programs can detect and eliminate phishing emails under favorable circumstances. The prerequisite for this is to keep the antivirus program up to date at all times. E-mail programs such as B. Mozilla Thunderbird and browsers such as Internet Explorer 8, Mozilla Firefox 3.6 or Opera 9.xx warn of phishing sites. The phishing protection is either based on a blacklist , which is updated via the Internet, or typical features of phishing e-mails such as B. Checks references to IP addresses or references with a different host name than in the reference text.
For some time now, more and more credit institutions have been using Extended Validation SSL Certificates (EV SSL Certificates) in Internet banking . In the address line of the current browser (e.g. Internet Explorer 9, Mozilla Firefox 7.0.1), a field is also displayed in which the certificate and domain holder alternates with the certification authority. In addition, depending on the browser used, the address line is colored green. Internet users should be able to recognize even more quickly whether the website they are visiting is genuine and thus be better protected against phishing attempts.
There is also a way for Microsoft Outlook to protect itself against dangerous phishing. A toolbar is integrated into Outlook and every incoming e-mail can be checked for dangerous references and suspicious headers .
Toolbars and e-mail filters that are based on black lists are in principle dependent on their being up-to-date. This significantly limits their effectiveness in the case of new phishing attacks.
A phishing-resistant way to carry out online banking transactions is to use the signature-supported HBCI process with a chip card . This variant of online banking is also very convenient as there is no need to enter TANs. Another gain in security is the secure PIN entry (a corresponding chip card reader with its own PIN pad required), where eavesdropping on the PIN entry with a keylogger or Trojan horse is not possible. On the other hand, there are the disadvantages of a software installation for HBCI, the necessary installations for the card reader in the operating system and thus the lack of mobility. Even if no massive attacks against HBCI have been observed so far, the process naturally only offers a high level of protection if the underlying operating system is free of malware such as Trojan horses.
The iTAN procedure also offers good protection against phishing . However, there are man-in-the-middle attacks (to be distinguished from phishing) against which the iTAN is ineffective.
A healthy mistrust of the insecure medium of e-mail and a careful reading of phishing e-mails is also helpful. No reputable German credit institution requires its customers to “fill out a form” or “key in a TAN”. Poor grammar and spelling are not sure indicators of phishing, but they are definitely highly suspect.
Other features that are often found in phishing emails are nameless salutations ("Dear customer" - in "real" newsletters, the salutation is usually directly to the addressee, e.g. "Dear Mr. XYZ") and a Alleged special urgency ("If you do not carry out a verification within the next two days, your account / credit card will be blocked"). No company expects such short response times, and most banks and savings banks have no e-mail data from their customers anyway, so that most important messages are sent by post.
Most phishing emails are written in unusually bumpy, bad German. If you read the text carefully and critically, you will immediately notice that many emails cannot have come from a reputable sender.
If in doubt, you can display and examine the source text of the phishing email (with Thunderbird or Firefox, simply with Ctrl-U) . Usually, you can quickly identify the actual sender or a URL from abroad that has nothing to do with the pretended sender.
It is advisable to assign a different password for each application. If the password of an application is discovered by an attacker, access to another application is still denied to the attacker.
Phishing e-mails received can easily be forwarded to the corresponding e-mail address of the consumer advice center to consolidate the situation.
Examples
2005 SPAM
At the beginning of 2005 a spam email was sent with the following wording:
Sehr geehrter Kunde! Wir sind erfreut, Ihnen mitzuteilen, dass Internet – Ueberweisungen ueber unsere Bank noch sicherer geworden sind! Leider wurde von uns in der letzten Zeit, trotz der Anwendung von den TAN-Codes, eine ganze Reihe der Mitteldiebstaehle von den Konten unserer Kunden durch den Internetzugriff festgestellt. Zur Zeit kennen wir die Methodik nicht, die die Missetaeter für die Entwendung der Angaben aus den TAN – Tabellen verwenden. Um die Missetaeter zu ermitteln und die Geldmittel von unseren Kunden unversehrt zu erhalten, haben wir entschieden, aus den TAN – Tabellen von unseren Kunden zwei aufeinanderfolgenden Codes zu entfernen. Dafuer muessen Sie unsere Seite besuchen, wo Ihnen angeboten wird, eine spezielle Form auszufuellen. In dieser Form werden Sie ZWEI FOLGENDE TAN – CODEs, DIE SIE NOCH NICHT VERWENDET HABEN,EINGEBEN. Achtung! Verwenden Sie diese zwei Codes in der Zukunft nicht mehr! Wenn bei der Mittelüberweisung von Ihrem Konto gerade diese TAN – Codes verwendet werden, so wird es fuer uns bedeuten, dass von Ihrem Konto eine nicht genehmigte Transitaktion ablaeuft und Ihr Konto wird unverzueglich bis zur Klaerung der Zahlungsumstaende gesperrt. Diese Massnahme dient Ihnen und Ihrem Geld zum Schutze! Wir bitten um Entschuldigung, wenn wir Ihnen die Unannehmlichkeiten bereitet haben. Mit freundlichen Gruessen, Bankverwaltung
She asked the recipient to follow a link that was supposed to lead to the Postbank website, but which actually referred to a phishing website. This asked in incorrect German for the PIN and two TANs. After entering the digits in the form fields, the input data was saved for retrieval by the fraudster. The visitor was forwarded to the public Postbank web address.
2016 United States Presidential Election
In the run-up to the 2016 presidential election in the United States , hackers who were later assigned to the Fancy Bear and Cozy Bear groups sent phishing emails to numerous representatives of the Democratic Party in March 2016 . The authentic-looking emails pretended to come from Google and asked the recipients to change their passwords.
Someone just used your password to try to sign into your Google account Google stopped this sign-in attempt. You should change your password immediately
The link provided to change the password provided criminals with the victims' access data. Since people did not recognize the phishing attempt out of inattention or as a result of the incompetence of their security officers, information from John Podesta's Gmail account could be copied. Other phishing victims gave attackers simultaneous access to the computer network of the Democratic election committee. The FBI , which noticed the leak of information from the Democratic party network, did not get through with its warnings to the party because the contact person did not understand the seriousness of the situation. Information could be stolen for over seven months.
Before the election, excerpts of the stolen data were published by unknown bloggers and ultimately leaked to the Wikileaks disclosure platform . The publications there, which took place in tranches until shortly before the election date, ensured the alleged revelations continuous media presence and thus did serious damage to the campaign of candidate Clinton and were cited by her supporters as one of the main reasons for her election defeat.
liability
In 2008, the Nuremberg-Fürth regional court raised the question of whether banks would have been obliged in 2005 to replace the older PIN / TAN procedure with the more modern iTAN procedure. This question remained open in the specific dispute at the time, as it was not decisive in the dispute. In 2010, a higher regional court in Germany decided for the first time that banks are obliged to keep secure systems available, which, in accordance with the state of the art, make it difficult for criminals to access bank access data. The court considered a breach of duty of care by the bank as a given if the bank uses a system that is no longer in use by the majority of credit institutions and falls short of the security standards of newer systems.
See also
literature
- Ulrich Schulte am Hülse, Sebastian Klabunde: Accessing bank access data in online banking - the perpetrators' approach and new civil law liability issues in the BGB . In: Multimedia und Recht (MMR) , 13th year, 2010, No. 2, ISSN 1434-596X , pp. 84-90.
- Paul H. Dienstbach, Tobias Mühlenbrock: Liability issues in phishing attacks. At the same time comment on LG Cologne, K&R 2008, 118 ff. (Issue 2) . In: Communication & Law (K&R). Operations consultant for media, telecommunications, multimedia , 11th year, 2008, No. 3, ISSN 1434-6354 , pp. 151–155.
- Markus Gisin: Phishing . In: Kriminalistik (Krim). Independent journal for all criminal science and practice , 62nd year, 2008, no. 3, ISSN 0023-4699 , pp. 197-200.
- Ingke Goeckenjan : Phishing of access data for online banking services and their exploitation . In: wistra . Journal for Commercial and Tax Criminal Law , Volume 27, 2008, No. 4, ISSN 0721-6890 , pp. 128-136.
- Jürgen-Peter Graf : On the criminal liability of "phishing" . In: Mathis Hoffmann, Stefan Leible, Olaf Sosnitza (eds.): Intellectual property in virtual space . Richard Boorberg Verlag, Stuttgart, Munich, Berlin, Hanover, Dresden, Weimar 2007, pp. 173-184, ISBN 978-3-415-03881-3 .
- David Hansen: The criminal liability of phishing for internet banking credentials . Publishing house Dr. Kovač, Hamburg 2007, ISBN 978-3-8300-3210-6 .
- Michael Heighmanns: The criminal liability of "phishing" bank account data and their exploitation . In: wistra . Journal of Commercial and Tax Criminal Law , 26th year, 2007, ISSN 0721-6890 , pp. 167-170.
- Tobias Mühlenbrock, Paul H. Dienstbach: Comment on AG Wiesloch, ruling. June 20, 2008 - 4 C 57/08 . In: Multimedia und Recht (MMR) , 11th year, 2008, No. 9, ISSN 1434-596X , pp. 630-631.
- Carl-Friedrich Stuckenberg: On the criminal liability of “phishing” . In: Journal for the entire criminal law science (ZStW) . 118 Vol., 2006, ISSN 0084-5310 , pp. 878-912.
- Tyler Moore, Richard Clayton: The Impact of Incentives on Notice and Take-down (PDF) June 13, 2008 (PDF file; 344 kB)
- Alexander Seidl, Katharina Fuchs: The criminal liability of phishing after the entry into force of the 41st Criminal Law Amendment Act . In: HRRS (Supreme Court Jurisprudence in Criminal Law) Issue 2/2010.
Web links
- Working Group on Identity Protection on the Internet (a-i3)
- Alexander Schultz: Phishing for financial agents or the myth of easy money . MIR Doc. 099–2006, margin no. 1-15
- The economy of phishing - Description of phishing infrastructure and phishing process (English)
- Moritz Mertinkat: From Postbank to PayPal - phishing on the Internet . (PDF, 520 kB) 2007
- Phishing Radar: Current warning messages from the consumer advice center in North Rhine-Westphalia
- Phishing - information from the Reporting and Analysis Center for Information Assurance MELANI of the Swiss Federal Administration
Individual evidence
- ↑ Spam Slayer: Do You Speak Spam? PCWorld.com , accessed August 16, 2006
- ↑ A. Mitchell: A Leet Primer . In: TechNewsWorld , July 12, 2005
- ↑ Collins English Dictionary - Complete & Unabridged . 10th edition. HarperCollins, 2009 ( online quote at Dictionary.com ).
- ↑ Phishing. In: duden.de. Bibliographical Institute, accessed June 27, 2014 .
- ^ K. Tan: Phishing and Spamming via IM (SPIM) . Internet Storm Center; Retrieved December 5, 2006
- ↑ E. Skoudis: Phone phishing: The role of VoIP in phishing attacks . In: searchSecurity , June 13, 2006
- ↑ phish, v. , OED Online, March 2006, Oxford University Press. Oxford English Dictionary Online. Reviewed August 9, 2006
- ↑ G. Ollmann: The Phishing Guide: Understanding and Preventing Phishing Attacks. Technical Info. Evaluated on July 10, 2006
- ↑ Know Your Enemy: Phishing. The Honeynet Project & Research Alliance , July 8, 2006
- ↑ How to protect yourself against phishing e-mails ( Memento of the original from April 15, 2012 in the Internet Archive ) Info: The archive link has been inserted automatically and has not yet been checked. Please check the original and archive link according to the instructions and then remove this notice. , t3n, April 12, 2012, accessed April 17, 2012.
- ↑ P. Welchering: In: FAZ , August 25, 2009, Motor und Technik, S. T1
- ↑ McAfee warns of "SMiShing" attacks. In: Heise online , August 27, 2006.
- ↑ phishing@verbrauchzentrale.nrw
- ↑ Together against phishing - our open forum helps. Fraudulent websites in online banking that are deceptively made, passwords stolen: more and more people are becoming victims of Internet fraudsters. Consumer advice center NRW, August 2, 2017, accessed on August 1, 2019 .
- ↑ a b c The Perfect Weapon: How Russian Cyberpower Invaded the US New York Times , December 13, 2016
- ↑ [LG Nürnberg-Fürth, judgment of April 28, 2008, 10 O 11391/07], evaluated on December 21, 2010
- ↑ KG, judgment of November 29, 2010 - 26 U 159/09 ( Memento of the original of January 24, 2011 in the Internet Archive ) Info: The archive link was inserted automatically and has not yet been checked. Please check the original and archive link according to the instructions and then remove this notice. (PDF; 100 kB), accessed on December 21, 2010