Malicious program
As malware , malicious software or increasingly as malware [ malwɛːɐ̯ ] - English badware , evil ware , junkware or malware [ mælˌwɛə ] ( portmanteau of times icious , vicious' and soft ware ) - refers to computer programs that are designed to prevent unwanted and possibly harmful functions execute. Malware is therefore a generic term that u. a. includes the computer virus . The concept of the virus is older and often not clearly defined. There is talk of virus protection , which in a much more general way means protection against malware of any kind. A typical virus spreads, while the malicious programs common today show the structure of Trojan horses, the primary purpose of which is not to spread, but to be remote controllable. Faulty software is to be distinguished from malware , although this can also cause damage itself or can be exploited to attack computer systems due to security gaps or insufficient information security .
functionality
The malicious functions are usually camouflaged, or the software runs completely unnoticed in the background ( see below for typing ). Malicious functions can be, for example, the manipulation or deletion of files or the technical compromise of the security software and other security devices (such as firewalls and anti-virus programs ) on a computer , but also the unsolicited collection of data for marketing purposes. In the case of malware, it is also common for a proper deinstallation to fail using the commonly used means, so that at least software fragments remain in the system. These may still perform unwanted functions even after uninstalling.
For a detailed description of how malware and especially viruses work, see Computer Virus .
Classification
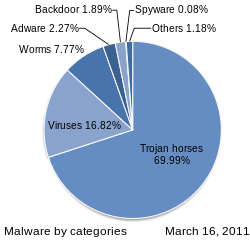
The malware known to date can basically be divided into three different classes, computer viruses , computer worms and Trojan horses .
- A computer virus is by definition a program code that can spread independently or automatically by inifying files. The first known computer virus was Elk Cloner in 1982. The term " computer virus " was established by Professor Leonard M. Adleman in 1984, who first used the term publicly. However, there have been comparisons with program codes with biological viruses in previous years.
- A computer worm is by definition a stand-alone program or script that spreads independently or automatically. John von Neumann is considered to be the inventor of the theoretical concept of self-replication in 1953. The term " computer worm " goes back to the end-of-time novel Der Schockwellenreiter by John Brunner from 1975. From the time he invented the term himself, it is not known but at least shaped him permanently. The first known malware was the Creeper computer worm in 1971.
- A Trojan horse is containing harmful for his major or minor function code, by definition, a standalone program, but can not spread on their own or automated. In 1972, Daniel Edwards presented the theoretical concept of such malware as a threat to computer security , and named it " trojan horse ". The 1975 game Pervading Animal is believed to be the first known Trojan horse.
Computer viruses
Computer viruses are usually classified into the following subclasses according to the type of host file (s):
- Boot sector viruses infect boot sectors and / or MBR, which technically count as files.
- Companion viruses create infected copies of an Exe file as a Com variant.
- File viruses infect executable files with the extension Exe or Com .
- Kernel viruses infect files that belong to the kernel of the operating system.
- Cluster viruses link to infected sectors on the disk, with the exception of the boot sector and MBR.
- Macro viruses infect MS Office documents.
- Hybrid viruses infect executable files as well as boot sectors and / or MBR.
If a link is set to the actual virus code in another file, this file also counts as infected or as a host file, since the link is regarded as part of the virus code. Memory-resident viruses also infect the RAM, but this is irrelevant for the classification of the virus by host file.
Numerous other names for viruses mostly refer to their behavior, the host systems or the techniques used.
Computer worms
Wümer is divided into four different classes according to their distribution method:
- Network worms use exploits in operating systems and applications and copy themselves directly to other computers via the network.
- E-mail worms send themselves automatically or partially automatically by email and often use exploits in MS Outlook or similar programs.
- Removable disk worms spread via USB sticks and removable hard drives and often use security holes in the autostart function.
- Bluetoth worms exploit Bluetoth technology from cell phones and tablet computers.
Worms are often incorrectly referred to as viruses in the mass media. A clear distinguishing feature is that a computer worm does not need a host file.
Trojan horses
Depending on the nature of its harmful effects, there are many other, more or less established names for malware. Often these are Trojan horses because they cannot spread independently or automatically. A commonly used short form is Trojan, but this term is often considered incorrect due to the origin of the word. However, the term is firmly established in the German language both in the specialist field and in general and thus represents a correct designation. A Trojan horse is usually downloaded from the Internet as a result of deception, it is caught as a drive-by download, or gets it leaked accidentally or on purpose. The following examples are mostly Trojan horses:
- A backdoor is a widespread malicious function that is usually introduced and installed by viruses, worms or Trojan horses. It allows third parties unauthorized access ("back door") to the computer, but hidden and bypassing the usual security devices. Backdoors are often used to misuse the compromised computer as a spam distributor or for denial-of-service attacks.
- Spyware and adware research computers and user behavior and send the data to the manufacturer or other sources in order to either sell them or to place targeted advertising. This form of malware is often installed along with other useful software without asking the user, and often remains active after it is uninstalled. As Spyware is a software program that collect information on the activities of the user and to third parties. Adware is software that - often together with desired installations or web accesses - starts functions thatserve advertising or market research without being asked for and without any benefit to the user.
- Scareware is designed to unsettle the user and induce him to install malicious software or to pay for a useless product. For example, fake warning messages are displayed about alleged virus attacks on the computer that commercially available software is purporting to remove.
- Ransomware blocks access to the operating system or encrypts potentially important files and asks the user to pay a ransom - usually via the digital Bitcoin payment system.
- Keyloggers are programs that are used to log the entries made by the user on the keyboard of a computer and make them available to a third party. Among other things, entered user names and passwords are recorded, which in turn give the third party the opportunity to access the systems for which these access data are intended. Repeated use of the compromised access data can also enable an attack on a large number of user accounts and systems.
- Grayware is sometimes used as a separate category in order to distinguish software such as spyware and adware or other variants that do not directly affect system functions from clearly harmful forms (not to be confused with grayware or re-importing goods by the official importer).
- Dialers (dial-up programs for premium-rate telephone numbers ) are also sometimes mentioned as malware, although they are not included in the narrower sense. Illegal dialer programs secretly dial-in, i. H. in the background and unnoticed by the user and inflict financial damage on the victim, which is billed to the telephone bill, for example. Under criminal law, this is fraud .
- Rogueware (even rogue software, rogue security software or English "rogue security software" ) deceives the user supposed to remove other malicious programs. Some versions are offered for a fee, other versions install additional malware during the deception process.
- Coin mining (also known as cryptocurrency mining ) describes a technique in which an attacker uses the hardware and energy resources of victims unnoticed and without their consent for computationally intensive mining , e.g. B. via manipulated websites or malware.
distribution
In 2008, security companies like F-Secure were expected to see “a million new malware threats”. According to this, around 25,000 new malware programs - so-called unique samples , i.e. malware with a unique "fingerprint" according to MD5 - reach servers specially set up for this purpose, e.g. B. Honeypots . In contrast, AV-Test was able to count ten million new malware programs in 2008 as early as mid-April 2008. A major change can be seen in the spread of malware: Trojan horses in e-mail file attachments are becoming increasingly rare, while attacks via the web, for example via drive-by download, are increasing. In addition, the use of rootkit techniques to hide malware is becoming more common. According to the California malware specialist Kindsight Security, an average of 13% of private computers in Germany were infected by malware in 2012. According to a security study by the magazine <kes> and Microsoft in 2014, “infection by malware” has advanced to the first place in terms of threats to corporate IT. In doing so, she has pushed “employee error and negligence” into second place. 74 percent of the study participants stated that they had been affected by malware incidents in the past two years. In the companies surveyed, email is at the top of the path of infection. This would be followed by web content that distributes the malware via active content or "drive-by downloads".
motivation
Studies dealing with the motivation of malware developers have come to the five primary results:
- Greed: Attacks are carried out in order to gain personal, material gain
- Curiosity: Attacks are carried out to satisfy personal curiosity
- Espionage: Attacks are carried out in order to gain specific information
- Retaliation: Attacks are used to purposefully cause harm to satisfy personal emotions
- Conspiracy: Attacks are carried out to lure possible pursuers on the wrong track.
See also
- Botnet
- Content filter
- Crimeware
- Dropper
- Information security
- Logic bomb
- Malicious code
- Pharming
- Phishing
- Riskware
- Vishing
- Quarantine of malware
literature
- Eugene Kaspersky: Malware: About Viruses, Worms, Hackers and Trojans and How to Protect Yourself from Them. Hanser-Verlag, Munich 2008, ISBN 978-3-446-41500-3 .
Web links
- Risks from malware from the Internet (seminar paper FH Würzburg, PDF file and Powerpoint presentation)
- Viruses, worms, Trojan horses Information page of the CERT of the University of Stuttgart (RUS-CERT) on malware
- Kaspersky Malware Classifications Classification of types of malware according to harmfulness
- Mikko Hypponen: The Malware Museum. Internet Archive , 2016, accessed on February 8, 2016 (Collection of emulations of historical malware).
- Malware: How to Detect, Remove, and Prevent Malware. 1und1.de/digitalguide, June 2, 2016, accessed June 30, 2017.
Individual evidence
- ↑ [ http://seclab.cs.ucdavis.edu/projects/history/papers/ande72.pdf Computer Security Technology Planning Study , 1972, p. 62, (PDF; 8.1 MB)
- ↑ http://news.cnet.com/8301-13506_3-9745010-17.html 25th anniversary of the computer virus? Not so almost! by Don Reisinger , November 30, 2013
- ↑ wsj.com: In the Bitcoin Era, Ransomware Attacks Surge
- ↑ Bitdefender.de: E-Threat-Trends 2011 , accessed on July 8, 2013.
- ↑ Microsoft.com: Beware of False Virus Alerts , Retrieved July 8, 2013.
- ↑ Marvin Strathmann: CoinHive - This software secretly mines digital money while you surf , Süddeutsche Zeitung, November 30, 2017, accessed on December 1, 2017
- ↑ October's Most Wanted Malware: Cryptocurrency Mining Presents New Threat , Check Point Research Team, November 13, 2017, accessed December 1, 2017
- ↑ heise.de: F-Secure expects 1 million malware threats this year
- ↑ Spiegel-Online: Virus hunter Kaspersky: "[...] the era of e-mail viruses is over [...]. Today nobody needs an email to get a virus into circulation. Criminals distribute their viruses via hijacked websites: just one visit is enough to infect the computer. They hide their programs in multimedia files and circulate them via social networks (→ social software ). They leave links in guest books or on Wikipedia, and if you click on them, you catch something. "
- ↑ <kes> / Microsoft Security Study 2014 special edition . 2014.
- ↑ Heise Security : Study: Malware is the main threat to corporate IT from October 1, 2014. Retrieved October 14, 2014.
- ↑ Threats . In: Security @ Work . Springer Berlin Heidelberg, 2006, ISBN 978-3-540-22028-2 , p. 49–83 , doi : 10.1007 / 3-540-36226-6_5 ( springer.com [accessed July 10, 2018]).