Topology (computer network)

The topology of a computer network describes the specific arrangement of the devices and lines that form a computer network via which the computers are connected to one another and exchange data.
A distinction is made between physical and logical topology. The physical topology describes the structure of the network cabling; the logical topology the data flow between the end devices.
Topologies are represented graphically (according to graph theory ) with nodes and edges .
In large networks you often find a structure that is composed of several different topologies.
The topology of a network is decisive for its reliability : only if there are alternative paths between the nodes, the functionality is maintained in the event of failure of individual connections. In addition to the commute to work, there are one or more alternative routes (or diversions ).
Knowledge of the topology of a network is also useful for evaluating its performance and necessary for investment planning and for selecting suitable hardware .
Characteristic values
diameter
The diameter of a topology describes the maximum direct distance between two nodes in hops . It is thus a direct measure of the maximum transfer times to be expected, i.e. H. the larger the diameter, the greater the worst case transfer time.
Degree
The degree of a topology indicates the number of links per node. This can be the same or different for each node. If all nodes of a topology have the same degree, the topology is regular, which has a beneficial effect on the network . In addition, the degree indirectly describes the costs that have to be raised to set up the topology. The higher the grade, the higher the cost.
Bisection width
The bisection width indicates the minimum number of links that have to be cut in order to divide a network with N nodes into two networks with N / 2 nodes each. It is therefore a measure of the performance of a network, since in many algorithms the nodes of one half of the network communicate with the nodes of the other half. The lower the bisection width, the more unfavorable this affects the time required for data exchange between the two network halves.
symmetry
With a symmetrical topology, the network looks the same from every point of view (nodes / links); That is, there are so-called graph automorphisms for nodes and / or edges . Put simply, this means that nodes and / or links in a symmetrical network behave in the same way, regardless of which node or link is viewed. This has extremely positive effects (simplification) on programming, load distribution and routing, since there are no special cases to consider.
Scalability
The scalability is the smallest Netzinkrement (number of nodes and links) in order that you can expand a topology reasonable effort to ensure optimum performance and maintaining topology typical properties after enlargement.
Connectivity
The connectivity indicates the minimum number of nodes or links (edge or node connectivity) that must be severed so that the network as such is no longer functional. It is a measure of the number of independent paths that can exist between two different nodes. It also describes the reliability of the network, i.e. H. the higher the connectivity, the more fail-safe the network.
Physical topologies
Often the electrical / signal topology ( OSI layer 1) and apparent topology (how the cables are to be laid) do not match. A widespread example is 100 Mbit Ethernet (100BASE-T with hub): The cables are run in a star shape from the end devices to the hub. From the point of view of the signal flow, however, the network is a bus topology.
Point-to-point topology
A basic topology is the point-to-point topology or two-point topology. It comes about when two nodes are directly connected to one another. All more complex topologies that do not use a shared medium are based on this simple construction principle. Two-point topologies are among the most powerful constructs because of the direct connection. Direct use as an independent topology is e.g. B. in the field of fiber channel networks .
advantages
- This network offers every connected computer the entire bandwidth of the transmission medium
- Predictable, usable transfer rate
- Easily expandable
- Easy to understand
- Easy troubleshooting
- No routing needed
disadvantage
- Entry of every user on every computer
- no central management option
- Approvals at user level not possible
- maximum effort for cabling and radio connections
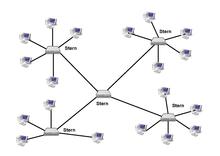
Star topology

In networks in star topology , all other participants are connected to a central participant with a point-to-point connection (see also star graph ). In computer networks it can be a specialized device, for example a switch . The network of a private branch exchange is also usually a star network: The switching system is the central node to which each subscriber set is connected in a star configuration with its own line. In any case, a central component in a network causes a higher probability of failure for the individual connections: a failure of the central participant inevitably results in the failure of all connection options at the same time. A common protective measure in star networks is to duplicate the central component ( redundancy ).
advantages
- The failure of a terminal has no effect on the rest of the network.
- High and different transfer rates possible
- Easily expandable
- Easy to understand
- Easy troubleshooting
- Combined telephone / computer network cabling possible
- Very suitable for multicast / broadcast applications
- No routing needed
disadvantage
- Network traffic becomes impossible if the distributor fails
- High cable expenditure
Ring topology

When networking in ring topology , two participants are connected to one another via two-point connections, so that a closed ring is created. The information to be transmitted is passed on from subscriber to subscriber until it reaches its destination. In order to avoid overlaps, special addressing procedures are necessary for this type of networking. Since each participant can act as a repeater at the same time (if no splitters are used), large distances can be bridged in this way (when using fiber- optic cables in the range of kilometers).
If one of the participants fails, the ring is interrupted. Depending on the organization of the communication, this can be intercepted (e.g. by switching protection ) or lead to extensive failure. In a ring with protection , a certain “direction of rotation” is often selected as the “working path” in the ring (for example clockwise), the substitute path leads in the other direction of rotation (counterclockwise in the example). This method is also used in fieldbus systems based on fiber optics.
If communication is generally carried out in both directions in the ring, the participants usually keep lists of the target device to which it is "shorter" in which direction of rotation. A ring interruption can then be marked as "infinite" for target devices that can no longer be reached in one direction - which automatically selects the other direction of rotation.
If a ring line distributor (German: RLV, English: MAU = Multistation Access Unit) is used, each device is connected to the RLV with just one cable. The RLV forwards the data from one port to the next. This technically means a star, but logically a ring topology. It is also possible to connect several RLVs, whereby the ring topology is retained. The ring line distributor prevents the failure of the entire network in the event of a terminal device failure, since the distributor can "bridge" failed or disabled participants.
A special form of the ring topology is the line topology , which can be viewed as an "open ring", i. that is, the first and last computers are not connected to each other. This system is very easy to set up, but also very fragile, since the failure of a middle participant splits the network into two separate subnetworks, which only allow further data transmission.
Data of the (obsolete) IBM token ring:
- Maximum ring length 800 m
- Computers may not be more than 100 m away from the MAU
- Transmission rate 4, 16 or 100 Mbit / s
- Active topology
- Transport protocol is token passing
- Access is deterministic (specific access)
- Is only addressed via MAC addresses
advantages
- Deterministic computer network communication without packet collisions - predecessor and successor are defined
- All stations work as amplifiers
- All computers have the same access options
- Guaranteed transmission bandwidth
- Scales very well, degree remains constant when expanded
- Regular topology, therefore easy to program
disadvantage
- Low bisection range and connectivity, i.e. This means that the failure of a terminal device can lead to the entire network communication being interrupted (depending on the type of communication, e.g. protection switchover, see e.g. FDDI and SDH ). Sometimes network components can loop the signal directly through to the next participant even without an explicit power supply. However, there are few alternative routes. B. in the case of high load conditions on a ring section can lead to bottlenecks.
- When using a ring distributor, long signal paths with frequent receiving and forwarding, i. H. high latencies to remote nodes
- Without a ring distributor, a lot of cabling is required, since the formation of a real ring often conflicts with the (office) room layout.
- Data transmissions can easily be eavesdropped .
- Slower data transmission with many connected end devices.
Examples
- Token Ring (logical)
- FDDI (physical)
In theory you can often see that the physical ring structure follows the logical structure in order to save cable lengths and thus costs, but this is usually done at the expense of flexibility when expanding.
Bus topology
With a bus topology, all devices are directly connected to the same transmission medium , the bus . There are no active components between the devices and the medium. In systems with a smaller physical expansion, the transmission medium is often implemented directly on a printed circuit board , and otherwise as a cable , cable bundle or (in the case of radio networks) free space. Examples of a network with a bus topology are the coaxial versions of 10 Mbit / s Ethernet and WLAN . The Thin Ethernet variant has a single cable that is divided into segments. The connection between the devices ( i.e. network cards ) and the segments of the cable is made via T-pieces . Terminating resistors at the ends of the cable are used to prevent reflections.
If the transmission medium of a bus is a shared medium - e.g. For example, if the same copper wire is used jointly by all participants for data transmission - it must be ensured that only one device sends signals to the transmission medium at the same time. This can be regulated by a central control, the so-called bus arbiter . Before a device can send, it has to send a request to the bus arbiter via a separate line.
Central control is often impractical, especially in dynamic networks such as computer networks. Therefore, in networks with decentralized control, simultaneous write accesses (collisions) are recognized and the problems that arise are resolved. A frequently used method is, for example, CSMA / CD .
With the time slice method ( time division multiplex ), the computers transmit in a rigid time grid on the shared medium. Each computer may only use a short time interval for sending, after which the next computer may send.
advantages
- Low costs as only small amounts of cables are required
- Simple cabling and network expansion
- No active network components are required
disadvantage
- Data transmissions can be eavesdropped fairly easily (keyword: sniffers ).
- A fault in the transmission medium at a single point in the bus (defective cable) blocks the entire network.
- Only one station can send data at a time. During this time, all other senders are blocked (the data to be transmitted must be buffered internally).
- In buses that allow collisions and rely on subsequent rectification, the medium can only be used to a small extent, since a disproportionately large number of collisions occur with higher data traffic.
Examples
Tree topology
Tree topologies are characterized by the fact that they have a root (the first or upper node) from which one or more edges (links) start. These continue to lead to a leaf (end node) or "recursively" to inner nodes of subtrees ("roots" of further "branches"; see also tree (graph theory) ). The tree topology is closely related to the star-star topology, but possibly with a stricter hierarchical order. Connections between the distributors ( hub , switch ) must be established using an uplink . This topology is often used in large buildings.
advantages
- The failure of an end device (“sheet”) has no consequences
- Structural expandability
- Large distances can be achieved (combination)
- Well suited for search and sorting algorithms
disadvantage
- If a distributor (inner node) fails, the entire (sub) tree of the distributor can no longer be reached
- Due to the bisection width of 1 defined for trees, there may be bottlenecks towards the root, since communication from one lower half of the tree to the other half always has to be done via the root
- Trees have a very large diameter with increasing depth (= number of links to be walked from the root to a leaf). In connection with the bisection width, this leads to poor latency properties in classic trees
In order to counteract these quite serious disadvantages, a large number of tree variations are used in practice.
k-tree
The k-tree is so far a classic tree, but k edges extend from each root. This allows z. B. in comparison to binary trees achieve a lower depth and thus lower latency times. The disadvantage, however, is the greater complexity of the root elements (degree k).
Ring-enlarged tree
A ring-expanded tree is a normal binary or k-tree, the leaves of which, however, are linked to a ring on the same level (so-called horizontal rings). You can either couple the leaves of all levels into rings, or only the specific (mostly lower) levels. This relieves the load on the root elements of the upper levels, since nodes on one level can now communicate more or less locally without having to go up a few levels and then down again. In practice, you usually only couple a few nodes of a level (e.g. the two outermost and the middle) to form a so-called interrupted ring. This has the advantage that it is less complex than a complete ring, but also offers some of the advantages mentioned above. It's kind of a compromise solution.
Hyper tree
The hyper tree works on the same principle as the ring-expanded tree, but the additional connections are not limited to the horizontal, but connect nodes of different levels with one another. However, this requires a relatively complex routing .
Fat tree
The fat tree or English fat tree trying to solve the problem of low Bisektionsweite. This is achieved through increased bandwidth in the direction of the root, for example through several parallel links from the root node to the lower levels. This overcomes the disadvantage that the root of the tree can become a bottle neck, but leaves the tall diameter of a tree untouched.
Mesh network
In a meshed network , each terminal is connected to one or more other terminals. If every participant is connected to every other participant, one speaks of a fully meshed network.
If a terminal device or a line fails, it is usually possible to continue communicating by redirecting ( routing ) the data.
advantages
- Safest variant of a computer network
- If a terminal device fails, data communication is still possible by rerouting (high connectivity)
- Very efficient due to large bisection width, small diameter (with fully meshed networks constant at 1)
- fully meshed networks do not require routing, as there are only direct connections
disadvantage
- Lots of cables needed; Very complex even with not fully meshed computer networks (usually high degree)
- Very high energy consumption
- Comparatively complex routing is necessary for networks that are not fully meshed, since these are then not regular and not symmetrical, which causes many special cases
Cell topology
The cell topology is mainly used in wireless networks. A cell is the area around a base station (e.g. wireless access point) in which communication between the end devices and the base station is possible. Within a cell, the cell topology corresponds to the bus topology. It differs from a bus if several overlapping cells are considered (interference from foreign cells, routing across cell boundaries, etc.)
advantages
- No cables needed
- No disruption due to failure of end devices
disadvantage
- Extremely prone to failure and limited range
- Very insecure, as anyone can access it from outside (encryption required)
Examples
Hybrid topologies
Hybrid topologies, also known as mixed topologies, use at least two topologies in a network.
Star bus
A star-bus network is created when different distributors each form the center of a star, but these distributors are connected to one another via a bus cable. In the past, this variant was often used for buildings with several floors, when coaxial cabling was still common. This technique has not been used since the end of the 20th century.
Star star
A star-star network (also called an extended star) is created when different distributors each form the center of a star and these distributors are in turn connected to a distributor via their own cable. This topology is now the standard cabling in local networks . See universal building cabling . A tree topology corresponds to an extended star!
Logical topology
The logical topology of computer networks can differ from the physical one. For example, Ethernet can be physically structured as a star or (out of date) as a bus - from a logical point of view, a distinction must be made here between the coupling components used. If a hub is used, there is a logical bus topology, as the data flow from one end device to all other end devices takes place at the same time. However, if a switch is used, the logical topology is also a star or a point-to-point connection. Broadcast traffic is an exception here; here the switch also works logically like a bus, since it forwards the data to all connected end devices. Token Ring is physically implemented as a star via a ring line distributor (MSAU), but it is a logical ring topology, as the data flow logically runs from terminal to terminal. ARCNET is physically set up as a tree over several active and passive hubs , but the data flow also takes place from device to device and is therefore logically a ring topology. The logical topology of a WLAN is the bus topology. (See also VLAN ).
The logical topologies also include so-called overlay networks , which have gained in importance, in particular due to the popular peer-to-peer networks (abbreviated to P2P networks). Overlay networks usually form logical network structures based on subordinate physical structures. The topology of the overlay network can differ completely from the topology of the underlying physical networks. For example, many structured P2P networks have tree or ring topologies, although the underlying physical structures traditionally follow a star topology.
Web links
literature
- Andrew S. Tanenbaum : Computer Networks. 5th, updated edition, Pearson Studium, Munich 2012, ISBN 978-3-86894-137-1
- Bernhard J. Hauser: Fachwissen Netzwerktechnik , 2nd edition, Europa-Lehrmittel -Verlag, Haan 2015, ISBN 978-3-8085-5402-9
- Gerhard Schnell and Bernhard Wiedemann: Bus systems in automation and process technology, Vieweg + Teubner Verlag, Wiesbaden 2008, ISBN 978-3-8348-0425-9 .
Individual evidence
- ↑ Network types, topologies and access methods , Dirk H. Traeger, Andreas Volk, chapter LAN practice of local networks , p. 88, Figure 3.2 (click on 'look inside')
- ↑ Topologies / network structures . Retrieved March 20, 2013.