Transaction number
A transaction number ( TAN ) is a one-time password that usually consists of six decimal digits and is mainly used in online banking .
realization
There are different approaches to generating, checking and transmitting TANs to the user. Some of these are described below.
TAN list (classic TAN procedure)
With the classic TAN procedure, the participant receives a list of transaction numbers in electronic banking , usually by post. For each booking process - the transaction - any TAN from the active list must be entered. It is a supplement to the personal identification number (PIN). If the bank receives a booking order with the correct TAN after entering the correct PIN, it assumes that the order was sent by the customer. The bank interprets the TAN as a quasi- signature . It expires after a single use. If a customer's TAN list is low, the bank will send a new one upon request or automatically.
Due to the increasing number of phishing attacks, this type of TAN list was replaced by the indexed TAN list by many banks from around 2005 .
Indexed TAN list (iTAN)
The indexed transaction numbers, iTAN for short, go one step further than the classic TAN procedure : Customers can no longer legitimize their order with any TAN from the list, but are requested by the bank to specify a specific item identified by an item number ( index ) Enter the TAN from the list that is now numbered for this purpose. The TAN must be entered within a few minutes. Even if the TAN is not used, it is marked as used in the bank computer.
This technique can be attacked by hackers in two different ways:
- Infection of the victim's system with a Trojan horse
- Man-in-the-middle attack
In both cases, the attacker's goal is to go unnoticed into the bank's communication with the customer and to suggest to the bank customer that he is on a bank website, even though he is actually on a fake bank website. By displaying a form within a fake online banking system, the online banking customer can then e.g. B. be requested to enter several TANs including index number.
The malware exchanges the transfer data in the background; With the requested TAN, the online banking customer actually confirms the fraudulent transfer of the hacker. He can still see his original transfer on his PC screen. Even the sales display and the account balance can be manipulated in this way to avoid suspicion.
More and more banks see the iTAN list only as a minimum protection and recommend other methods to their customers (see below).
A disadvantage of the iTAN is that the complete iTAN list must always be carried with you for transfers on the go (e.g. from vacation). With the simple TAN procedure, it is possible to carry a few TANs with you in such a way that they cannot be recognized as such by strangers or cannot be read correctly, for example in a telephone list. An iTAN list is harder to camouflage and a thief always gets the complete list. However, this is worthless as long as the thief does not also have the PIN. Only then can he steal money through transfers.
On the other hand, there is a practical advantage of the iTAN compared to the simple TAN that you do not have to remove used iTANs from the list. In this way, for example, you can work with several independent encrypted electronic copies of an iTAN list without synchronization problems.
The iTAN procedure has not been considered 100% secure since its introduction. Phishing attacks have become more difficult thanks to iTAN, but not impossible. In 2008, the BKA registered around 1,800 successful phishing attacks, most of which were caused by the smuggling of Trojans .
At the beginning of 2007, the first phishing kits appeared that were able to use iTANs fished in real time for their own transactions via the aforementioned man-in-the-middle attack. In 2010, 1.65 million euros were captured with a corresponding iTAN Trojan . The Trojan manipulated both the transfer data and the account overview page in the background, so that the transfers actually made remained hidden.
In 2012, the European Agency for Network and Information Security (ENISA) therefore recommended that all banks consider their customers' PCs basically infected and therefore use security procedures that allow them to check the actual transfer data again independently of the PC. Examples are, according to ENISA - with the proviso that the security of the mobile phone can be guaranteed - mTAN or smart card-based solutions with their own control display such as chipTAN .
Due to the European Second Payment Services Directive (Payment Service Directive 2, PSD 2 for short) , banks must abolish the paper TAN for payment accounts by September 14, 2019.
Indexed TAN list with control image (iTANplus)
The man-in-the-middle attack possible with the iTAN procedure is made more difficult by the so-called iTANplus procedure, but not prevented. With this method, before entering the iTAN, a control screen is displayed in which all transaction data are listed again. In addition, the account owner's date of birth is displayed as a digital watermark, which a man-in-the-middle attacker should normally not be aware of. This is intended to make it more difficult for an attacker to automatically generate a manipulated control image. The disadvantage of this method is the deterioration in ergonomics, since the control image is more difficult to read than the request for iTAN input in normal text form.
TAN with confirmation number
The procedure can be extended to include a confirmation number (BEN) with which the bank acknowledges the order acceptance in return. This means that an attack must take place as man-in-the-middle and almost in real time in order not to attract attention. Phishing and pharming were noticed because no (correct) BENs were returned.
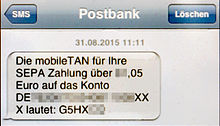
SMS-TAN (smsTAN, mTAN)

Working principle
The variant SMS-TAN ( smsTAN ) is often also called Mobile TAN ( mTAN ) and consists of the integration of the SMS transmission channel . The online banking customer receives a TAN that can only be used for this process on their landline or mobile phone after the bank has sent the completed transfer on the Internet by SMS . The order must then be confirmed with this TAN.
safety
If a landline connection is used for the mTAN ( landline SMS ), this procedure is far more secure than with a mobile network. The main cell phones used today are smartphones with the Android or iOS operating system, which can be attacked by viruses, bots and unsafe apps . This option does not apply to landline telephones, as there is no connection to the Internet and usually no software can be installed. In addition, almost all attack options with regard to the mobile network, SIM, etc.
It should also be noted that older cell phones without an internet function also rule out malware infestation. However, all other attacks are still possible (see Possible attacks ).
By sending the TAN by SMS, mTAN is considered more secure than iTAN or the classic TAN process. Because the validity period of the TAN is limited, the target account number (or parts of it) and the transfer amount are also specified in the SMS and the TAN is only valid for exactly this transaction, a redirection to another account by a man-in the middle attack on the home banking website can be prevented. Phishing attacks on TANs in the mTAN procedure are also made more difficult. The TÜV Rheinland certified in 2006, the mTAN system of Postbank AG , an "effective protection of the externally accessible technical systems against unauthorized use." In mid-2007, the mTAN system from Fiducia IT AG (IT service provider for the Volks- und Raiffeisenbanken) also received this TÜV certification.
It is seen as an advantage that you do not need to have a TAN list with you for transactions on the go. Experience has shown that the loss of the mobile phone is more likely to be noticed by the user than the loss of the bank card or the TAN sheet. In addition, the user may find out about unauthorized transfer attempts via SMS, so that the account can be blocked.
Since cell phones are increasingly equipped with Internet access, the mTAN process has fundamental weaknesses, for example when the mTAN is sent to the same device that is also used for online banking. If the mobile phone is lost, the only protection against fraudulent transactions is the banking access data. TAN generators offer much more security in this regard, as they are not networked.
Accordingly, a Trojan horse that takes control of the system can first listen to the user name and password of the online banking on a smartphone and then carry out transfers fully automatically by first logging into the online banking, then filling in a transfer, then the SMS of the mTAN intercepts and thus legitimizes the transfer. A single login to online banking via the smartphone is sufficient for a Trojan so that this security gap can be exploited. The whole thing also works if the attacker found out the username and password of the online banking system in another way, e.g. B. by another Trojan horse on the PC.
In September 2010 new variants of the banking Trojan ZeuS were reported for the first time, which carries out parallel infections with a mobile variant. In December 2012 it was reported that this Trojan had already stolen over 36 million euros.
Another weak point is the mobile phone's SIM card linked to the phone number. In this regard, attacks became known in which the victim's phone number was ported to a new SIM card with the help of user data stolen by Trojans, for example, or a second SIM was requested by the attackers with which they could then bypass the mTAN procedure.
Possible attacks
Conceivable attacks against the mTAN procedure are based on the fact that the PIN for online banking is first spied out using conventional methods such as phishing or Trojans. As soon as the phisher has the PIN, he can log into the victim's online banking system and read out his or her personal data, including account number, bank code, address and the stored cell phone number for the mTAN procedure. The cellular network used can be found out via a network query . Therefore, the stored mobile phone number is not completely displayed in the online banking portal.
In the second step, the phisher must also manage to manipulate the mTAN.
Access to the victim's PIN
As soon as you have the PIN, you can register yourself (i.e. your own landline or mobile phone) for the mTAN procedure. The authentication procedures used by the banks are not yet fully developed, but the processes are constantly being optimized
Attack on the landline phone
An attack on landline telephones is not yet known. Simple landline telephones have no software, the SMS is read out here (see also landline SMS ). With more modern comfort landline telephones with (text) SMS function (such as Siemens Gigaset), the firmware is stored in a flash ROM and therefore remote changes are not technically possible. Theoretically, the unlikely possibility that intruders physically “bug” the phone would remain.
Attack on the mobile phone
One possibility would be to compromise the victim's mobile phone as well, smartphones in particular are at risk here. An already infected computer can also infect the victim's mobile phone if the victim connects his mobile phone to the computer, for example for the actual purpose of synchronization. SMiShing or exploiting the cell phone would also be conceivable .
Due to the initially still low profits to be expected from fraud with mobile devices and due to the many different platforms ( operating systems ) of the mobile phones that were incompatible with each other at the time, cell phone viruses were not widespread in the past.
In the meantime, smartphones with the Android and iOS operating systems are mostly used, which has changed that fundamentally. This is why the current conditions of financial institutions prohibit the use of one and the same cell phone for online banking and for receiving the mTAN.
As soon as the victim's mobile phone is compromised, the fraudster can carry out any transfers, while the display and signaling of the mTAN are only visible to the fraudster, not the victim of the fraud.
Such an attempted attack using spyware on the mobile phone was actually discovered in April 2011.
Another point of attack, regardless of the cell phone model, are older SIM cards that still work with the DES encryption that has now been cracked . This makes it possible to take over the victim's SIM card unnoticed via a prepared service SMS. In addition, due to insufficiently secured Java VMs on the SIM card, you can also read out their master key and thus clone the SIM card.
Attack on the cellular network
Other possibilities would be the use of an IMSI catcher or breaking the no longer secure GSM encryption. These methods, however, require local proximity to the victim of the fraud, which requires considerably more criminal energy than phishing, which is carried out without any spatial reference.
By exploiting a security gap in the Signaling System 7 used in cellular networks, it is also possible to intercept SMS remotely, as Tobias Engel demonstrated in 2014 at the 31st Chaos Communication Congress . At the beginning of 2017, this vulnerability was successfully used by criminals to redirect mTANs and thus steal money from bank customers.
Attack on the network operator
Another possibility would be a compromised network operator, either through a human accomplice or through security breaches.
Request a new or second SIM card
On behalf of the victim, an attacker can apply for a new SIM card from their mobile phone provider and have it sent to them or, in some cases, have it replaced immediately in the mobile phone shop ( SIM swapping ). With most mobile phone providers, this is relatively easy to do. However, the old card is usually blocked 1-2 days before the new card is received so that the victim can easily notice the attack.
In addition, an attack became known in Germany in 2013 in which the attackers, after stealing the victim's online banking access data and mobile phone number , presumably using a Trojan , installed a second SIM card as a multi-SIM under the victim's name ordered from the mobile network provider. With this offer from the network operator, another SIM card is logged into the cellular network under the same phone number, which can be configured via speed dial so that all SMS are only received from this second SIM card. The victim does not need to be aware of this, as incoming and outgoing calls are still possible with their cell phone and the original SIM card.
The perpetrators then have unrestricted control over the victim's account: Since the mTAN required for authentication is sent to their SIM card, they can change the transfer limit and make any number of transfers to third-party accounts. The amounts of damage caused by these attacks are correspondingly high.
In 2014, several cases became known in which the perpetrators were given second cards in mobile phone shops because they did not have to identify themselves there with official ID as the first card holder, as was actually required.
Porting the number
The attacker can terminate the victim's term or prepaid contract and then trigger a number portability to a new mobile operator. For the termination with the old provider as well as for the new term or prepaid contract and the transfer of the number with the new provider, only the signature is required. This can be forged with little effort and is sometimes only insufficiently or not at all checked. A corresponding attack was found in Australia in 2009.
It is possible to formulate a fraudulent change of address and termination in one letter to the old provider in one letter. The confirmation of termination and the new SIM card could therefore be sent to an address that the attacker could choose.
In the most favorable case for the attacker, the victim's phone number on his old SIM card would be switched off at midnight and switched on for him at 6 a.m., which is a promising time window.
Social engineering
This attack tries to use "social engineering" to induce users to voluntarily make a transfer for the benefit of the fraudsters. To do this, the victim's PC is infected with a Trojan horse and the bank's online banking site then displays the message that an alleged “test transfer” should be carried out on behalf of the bank for “test purposes” in favor of the fraudsters, or it is displayed a larger sum was wrongly transferred to the customer's account and the customer should now "transfer money back". In other cases, the user should take part in a competition or synchronize data by bank transfer. The banks warn against these fraud attempts. A bank would never ask a customer to make a transfer that he did not initiate himself.
costs
Sending the TAN messages by SMS is billed to the customer by some banks or they may only receive limited free quotas. However, according to a ruling by the Federal Court of Justice in July 2017, banks are only allowed to charge fees for sending SMS messages from TANs that are actually used.
pushTAN
pushTAN is a mobile app -based TAN process that eliminates some of the disadvantages of the mTAN process. For example, there are no costs for sending pushTAN messages at some financial institutions and SIM card fraud is not possible, as the messages are sent to the user's smartphone using a special text messaging app via an encrypted Internet connection.
One of the expense of this method is that the relevant apps require a new registration each time they are reset or reinstalled. E.g. At the savings banks, this is possible both via a letter sent by post, which results in an interruption until re-registration, as well as via an SMS that enables immediate continued use after the direct registration.
Some banks prefer to call the process TAN2Go or appTAN instead of pushTAN. The names VR-SecureGo, easyTAN and SpardaSecureApp are also in use.
safety
As with mTAN, the transfer data actually received by the bank are sent again in the pushTAN message to protect against manipulation. However, analogous to the use of mTAN with a smartphone, there is a risk that both the PC and the smartphone will be infected by malware. To reduce this risk, pushTAN apps try to detect rooted devices and in this case refuse to function. In addition, with the pushTAN process, two-factor authentication can be used on just one device, which means that an attacker only needs access to one device.
At the end of November 2017, however, security researchers Vincent Haupert and Nicolas Schneider succeeded in overriding the security mechanisms of the pushTAN procedure. The Promon Shield app hardening procedure was removed and the pushTAN app manipulated in such a way that 1.23 instead of 15 euros was transferred. During the demonstration at the 34C3 conference , the two security researchers showed how this can be done on an Android smartphone with a supposedly harmless app from the Google Play Store. Promon announced to close these security holes.
TAN generator
With a TAN generator, TANs can be generated electronically. There are several different ways of doing this.
sm @ rt-TAN
With this procedure, introduced in 2003 by the Volks- und Raiffeisenbanken, the user receives a TAN generator without numeric keys from his credit institution. As soon as the customer card (e.g. a Maestro card or a V-Pay card) is inserted into the generator, TANs can be generated at the push of a button. These TANs can only be entered one after the other in online banking. If, for example, 5 TANs are generated, but only the last TAN generated is used for a transaction, the previous four TANs are invalid. As the issuer of the customer card, the bank can check the validity of the TANs.
The TANs are generated via the chip on the customer card. The TAN generator itself is not individualized. If the card is lost, any TAN generator can be used to generate valid TANs. Since the PIN is also required for transactions, this represents a manageable risk.
This method is prone to phishing or man-in-the-middle attacks, as the generated TANs can be used for any transactions. There is no binding order.
eTAN generator
BW-Bank introduced this procedure in December 2006 . Customers receive an individualized TAN generator that generates a temporarily valid TAN using a secret key, the current time and the recipient's account number. The recipient's account number must be entered using the number field of the TAN generator. Further personal data are not used. The method is still z. B. also used by BW-Bank and Consorsbank.
This procedure protects against phishing or man-in-the-middle attacks, provided the correct recipient account number is entered. Entering the account number manually is not very convenient. If the TAN generator is lost, TANs can still be generated. Since the PIN is also required for transactions, this represents a manageable risk.
At other banks (e.g. Santander Consumer Bank ), a control number (start code) generated for the respective transfer must be entered instead of the recipient account number. In contrast to entering the recipient's account, this method is susceptible to man-in-the-middle attacks because the recipient's account number is not controlled.
Some TAN generators from other banks create TANs that are valid for a limited time only on the basis of an individual secret key and the time, without entering a control number or a recipient account. Neither a card reader nor a keyboard is required on the generator. Since there is no reference to an order, the procedure is similarly prone to phishing as the sm @ rt TAN procedure described above. However, the undesired transaction would have to be initiated within the short period of validity of the TAN.
chipTAN manual, Sm @ rtTAN plus or SecureTAN plus1
Numerous Volks- and Raiffeisenbanken as well as many savings banks offer this procedure.
It was presented in the first version HHD (HandHeld Device) 1.2 under the name "Sm @ rtTAN plus" by the German cooperative publishing house 2006 at the CEBIT . With the following versions HHD 1.3 and HHD 1.4 (the latter available from 2010), the option was then created under the designation "SmartTAN optic" or "chipTAN comfort" to transfer the order data not only manually, but also via an optical interface, as well as each the amount of order data that is transmitted to the device and included in the TAN calculation is increased (see chipTAN comfort / SmartTAN optic (flickering) ).
After a transfer has been entered in online banking, a (start) code is displayed on the screen. The personal bank card must now be inserted into the TAN generator and the (start) code must be entered and confirmed using the numeric keypad of the TAN generator. At most institutes, the recipient account number (or parts of it) and, in some versions, the amount of the transfer must then be entered. If this is not the case (such as with the Wüstenrot Bank), the step must be confirmed on the TAN generator without any entry.
After entering the TAN in online banking, the order is carried out. By entering the account number and the amount on the TAN generator and including them in the TAN calculation, the process is protected against phishing and man-in-the-middle attacks.
Even if the devices from different manufacturers are called and look different, they are compatible within the same HHD version, interchangeable with one another and work with cards from different credit institutions.
If the bank card is lost, the finder can still generate TANs using any TAN generator that is suitable for this process. Since online banking access data are also required for transactions, this represents a manageable risk. After a bank card has been blocked, the TANs generated with this card are rejected by the bank.
chipTAN comfort or SmartTAN optic (flickering)
In this further development of the Sm @ rtTAN plus process, the order data is transmitted using optical sensors. Many savings banks and Volks- and Raiffeisenbanken as well as the Postbank use it. The savings banks and Postbank call it “chipTAN comfort”, while the Volksbanken use the term “SmartTAN optic” or sometimes continue to speak of “Sm @ rtTAN plus”. In Austria the system is known under the name "cardTAN", whereby cardTAN represents a technically independent standard.
Here, customers purchase a TAN generator with a number field and card slot. There are five optical sensors on its back . After a transfer has been recorded in online banking, a graphic appears on the screen that contains five flickering black and white areas. Now the personal bank card has to be inserted into the TAN generator. As soon as the TAN generator is held in front of the graphic on the screen, data is transmitted by light signals. Parts of the recipient's data are transferred, for example the (start) code, the recipient's account number and the transfer amount in the case of a single transfer. The transmitted data is then shown on the display of the TAN generator for control and confirmation. The chip on the bank card in the TAN generator now calculates an order-related TAN, which is entered in online banking.
This procedure protects against phishing or man-in-the-middle attacks, provided that the data shown on the display are checked for correctness before confirmation. Thanks to the optical transmission, no order data has to be entered on the TAN generator. Since online banking access data are also required for transactions, the loss of the bank card is also a manageable risk. After a bank card has been blocked, the TANs generated with this card will be rejected by the bank in any case.
Opportunities for attack arise in connection with collective transfers. Here only the number of items and the total amount are shown in the display of the TAN generator. The individual recipient account numbers are not displayed, as this would not be possible with extensive collective transfers. In the event of an attack, the individual items of the collective transfer could now be changed. As long as their number and the total amount remain the same, the manipulation would not be recognizable in the display of the TAN generator.
Another possible attack would be to convert a single transfer into a collective transfer with one item. In this case, the user would only see the number of items (here "1") and the amount in the display of the TAN generator. After this became known, the German savings banks changed the display for collective transfers with just one item. In this case, the recipient's account number and the amount will be displayed despite the collective transfer. In the case of Volksbanks in the GAD environment, on the other hand, collective transfers with only one item are not permitted and will be rejected.
With this method, however, some users criticize the fact that the device does not seem to recognize the flicker code with different display types. Here it often helps to hold the device at a slightly inclined angle (especially with S-PVA displays) or to increase the screen brightness. It can also help to change the flicker speed and to prevent direct radiation from light sources on the monitor. It can also help to deactivate hardware acceleration in the browser.
In all cases, the security is at least as high as when using TAN or iTAN lists. However, if the user checks the data shown in the display of the TAN generator and does not use a collective transfer, security is significantly increased.
Due to the high security measures of chipTAN, fraudsters are now trying to use "social engineering" to induce the user to voluntarily make a transfer in favor of the fraudsters.
chipTAN-QR and Sm @ rt-TAN photo
Since the optical chipTAN process based on a flicker graphic places some demands on the display and room lighting, the savings banks have also been offering the chipTAN QR process since 2018. With this procedure, a camera integrated in the TAN generator reads a QR code . Since no optical sensors are used here, the detection speed is significantly higher and the error rate lower. A TAN generator for chipTAN-QR is a bit more expensive to buy because a camera is built in.
At the Volks- und Raiffeisenbanken the corresponding procedure is called Sm @ rt-TAN photo. It differs in the graphic displayed, which consists of a color code, which is why the two methods are not compatible with each other.
In contrast to the photoTAN or QR-TAN process, the chipTAN-QR and Sm @ rt-TAN photo process require the use of a compatible TAN generator. It is not possible to use an app.
photoTAN and QR-TAN
photoTAN
The photoTAN procedure is also called imageTAN or CrontoSign by some credit institutions.
With the photoTAN procedure, the transaction data is displayed as a multicolored mosaic graphic on the screen. This code is read in and decrypted with an external reader , the transaction data is displayed on the reader for checking and the associated TAN is generated. The TAN generated in this way is then entered to approve the transaction.
Instead of a reader, a mobile device such as a smartphone or tablet with a corresponding iOS or Android app can also be used. However, this means compromising data security, as these devices (especially if they are connected to the Internet) can be contaminated with Trojans and viruses.
To initialize the process, the reader or the app on the mobile device must be given a unique identifier and this feature must be linked to the bank account. For this you get i. A. a letter with an activation code or an activation graphic, which you have to scan with the reader or app.
If the TAN generated by the reader or the app is entered in the online banking portal after the initialization of a transfer, it can be proven that the confirmation was generated by the registered reader or app.
In Germany, the process developed by a British branch of the University of Cambridge , Cronto Ltd., was introduced at the beginning of 2013 by Commerzbank and its direct bank Comdirect and is also used by the Swiss Raiffeisen banks and Deutsche Bank . In addition, it was introduced by the Dutch Rabobank together with a further developed version of the reader ( Rabo Scanner ). Cronto Ltd. was acquired by VASCO Data Security International Inc. in 2013. In the course of PSD2 and the abolition of the iTAN list, ING also introduced photoTAN as an alternative approval procedure.
QR-TAN
The QR-TAN procedure, which has been introduced at 1822direkt since the end of 2012 and was developed together with LSE Leading Security Experts GmbH, works in a similar way . This is based on the open OCRA algorithm ( RFC 6287 ) and transports the signed transaction information in a QR code . The rollout, in which the smartphone is registered, takes place via the separate channels of an HTTPS connection and a letter sent by post.
safety
Compared to iTAN, both procedures should be considered more protected against attacks by Trojans or man-in-the-browser attacks, as long as the security of the mobile device or the photoTAN reader is guaranteed due to the PC-independent control of the transfer data. An internet connection of the mobile device (smartphone, tablet) is not absolutely necessary for the use, there is no connection between online banking and mobile device. However, if both the banking and photoTAN functions are combined on a single mobile device (e.g. smartphone) in mobile photoTAN banking, so that the photoTAN app and the banking app communicate directly with one another, the Manipulate transfers again. Such apps are provided by Deutsche Bank , Commerzbank and Norisbank , for example .
General TAN security
In general, fraudsters can try to guess a TAN. With a 6-digit TAN, the probability is 1: 1,000,000 of guessing a certain TAN in one attempt. If customers can choose any one of a list of 100 TANs for legitimation, for example, the probability for fraudsters to guess one of these TANs is 1: 10,000. If a cheater has three tries, the probability of success is approximately 0.03%.
Instead of guessing, scammers can try to spy on TANs. Phishing attempts have often been made to obtain transaction numbers. In one variant, the bank customer is sent an e-mail with a link to a wrong Internet address for the bank. The text of the e-mail or website is intended to induce the customer to enter his account number, PIN and TANs that have not yet been used on this false website.
Phishing is successful because many users of online banking do not check exactly whether the page displayed in the browser really comes from the bank they want. With the classic TAN procedure, fraudsters are successful when they find out the account number, PIN and any TAN that has not yet been used, i. H. Customers enter this data on the fake website. With the iTAN procedure, fraudsters have a low statistical probability of being able to exploit a captured iTAN.
The security of the iTAN procedure is differentiated according to the type of threat. While with the classic TAN procedure an average of 50 TANs are valid on a TAN sheet (the TAN sheet contains 100 TANs, half of which have already been used on a statistical average), with the iTAN procedure only the single TAN is valid. which the bank queries during the transaction. It therefore offers good protection against phishing, provided the bank customer does not enter too many iTANs on a phishing page. It does not protect against man-in-the-middle attacks, as various publications have pointed out.
Corresponding attacks are carried out by Trojans , e.g. B. by changing the DNS server used and the SSL root certificates , or by direct intervention of the Trojan in the programs on the computer, such as a man-in-the-browser attack . The actual transfer data is replaced in the background by the fraudsters and the account overview pages are manipulated in such a way that the fraud is not noticed.
The security of the classic TAN procedure and the iTAN procedure is limited because the TAN is not linked directly to the content of the transfer. This means that the bank cannot use the transmitted TAN to decide whether the order is correct. In contrast, the mTAN process offers better protection against phishing and man-in-the-middle attacks. At some financial institutions, the transfer amount and the recipient's account number are sent in the text when the mTAN is sent. This enables customers to compare this data with the transfer entered at the bank and to detect possible fraud. When receiving the SMS, you not only have to read the mTAN, but also check the amount and the recipient's account number.
However, the mTAN procedure has already been broken by parallel malware infections on the PC and mobile phone. Corresponding mobile malware programs are known for Symbian OS , Blackberry OS , Windows Mobile and Android . In addition, mTAN was overturned several times in that the attackers, under false pretenses, had replacement or second SIM cards for the victims' cell phone numbers issued by the relevant cell phone providers ( SIM swapping ).
Even procedures based on electronic signatures , such as the HBCI procedure with a chip card , do not offer any higher protection. A checksum is calculated from the content of the transfer using a cryptographic process and transmitted to the bank. The bank can use the checksum to determine whether the transfer is from the customer or not, and also whether the transfer has not changed since it was signed. If a customer PC is infected with malware (Trojans or viruses ), data could already be manipulated and sent to the card reader. If a Secoder -capable card reader is used and the respective bank and the home banking software support the Secoder extension with the Secoder visualization texts for HBCI, it is not possible to see which data is available for the electronic signature.
Newer TAN processes with a TAN generator (e.g. chipTAN comfort / smartTAN optic) link the TAN with the order data. The TANs generated in this way cannot be used for deviating (fraudulent) transfers. If transfer data is changed by malware, these changed values are visible on the display of the TAN generator. In this case, the bank customer can cancel the transaction. Since the TAN generator is not connected to the PC, manipulation of the display is impossible. All previous, technical types of attack can thus be effectively prevented. The only source of danger remains the careless handling of the order data displayed on the TAN generator's display.
However, due to the high security of procedures with dedicated signature devices with their own display for checking the transfer data such as chipTAN or photoTAN, attempts are now being made to use "social engineering" to induce the user to voluntarily make a transfer in favor of the fraudsters.
history
The PIN / TAN procedure was already used at the time of Btx online banking. The idea is attributed to Alfred Richter, the technical director of the consumer bank at the time (now Norisbank ). Initially, this access protection was only intended for internal use in 1976; in 1979 the bank introduced online banking.
In 2002 the Upper Austrian company TeleTan was granted the patent EP1259046 for a method of transmitting individual TANs via SMS . No bank ever recognized the patent; similar processes were developed. A legal dispute between TeleTan's representative, lawyer Bruno Steiner, and a number of banks has lasted from 2006 to the present day (as of 2018).
See also
- Home banking computer interface (HBCI)
- Personal identification number (PIN)
- RSA SecurID
- Secure Sockets Layer (SSL)
Web links
Individual evidence
- ↑ Postbank with a new TAN system against phishing , heise.de, August 7, 2005, accessed on February 3, 2018
- ^ A b c Daniel Bachfeld: Successful attack on iTAN procedure . Heise Newsticker, November 11, 2005, accessed on February 3, 2018
- ↑ a b Christiane Schulzki-Haddouti / dab: BKA: iTAN procedure no longer a hurdle for criminals. In: heise Security. May 18, 2009, accessed October 8, 2010 .
- ↑ a b Katusha: LKA smashes ring of online fraudsters WinFuture.de, October 29, 2010
- ^ "High Roller" online bank robberies reveal security gaps European Union Agency for Network and Information Security, July 5, 2012
- ↑ Paper TAN lists gradually abolished. MDR, archived from the original ; accessed on October 6, 2018 .
- ↑ dab: Improved iTAN procedure should protect against manipulation by Trojans. In: heise online. October 26, 2007, accessed October 8, 2010 .
- ↑ Fiducia AG: Online banking with iTANplus. In: Fiducia AG. October 15, 2007, archived from the original on July 2, 2011 ; Retrieved February 2, 2012 .
- ↑ bb: TÜV certification for Postbank's mobile TAN. In: heise online. April 18, 2006, accessed October 8, 2010 .
- ↑ The mobileTAN procedure from FIDUCIA IT AG receives the seal of TÜV Rheinland. In: Website of FIDUCIA IT AG. May 2, 2007, archived from the original on July 10, 2012 ; Retrieved October 8, 2010 .
- ↑ Daniel Bachfeld: Banking Trojan ZeuS is targeting SMS-TAN procedures Heise Security, September 27, 2010, accessed on February 3, 2018
- ↑ Online banking: criminals steal 36 million euros article on the Zitmo Trojan on e-recht24.de with mobile phone Trojans , accessed on December 11, 2012
- ↑ a b Christian Kirsch: mTAN canceled in Australia Heise Newsticker, October 14, 2009, accessed on February 3, 2018
- ↑ a b Urs Mansmann: Attack by mTAN . In: Heise Zeitschriften Verlag (ed.): C't magazine for computer technology . 18, 2013.
- ↑ Attacks on German mTAN banking users Heise Security, April 5, 2011
- ↑ Jürgen Schmidt: DES hack exposes millions of SIM cards. In: Heise online , Heise Security. July 31, 2013, accessed July 25, 2017 .
- ↑ 31C3: Mobile radio protocol SS7 open like a barn door Heise Newsticker, December 28, 2014
- ↑ Fabian A. Scherschel: German bank accounts cleared out about UMTS security gaps. May 3, 2017, accessed on May 5, 2017 : “Criminals have cleared their accounts by accessing the online banking of German bank customers. They succeeded in doing this by rerouting mobile TANs (mTANs) intended for the customers' devices and thus authorizing the transfers. These diversions were apparently made possible by security gaps in the SS7 protocol of the UMTS network that have been known for years. "
- ↑ Vulnerability in the cellular network: criminal hackers empty accounts. In: Sueddeutsche Zeitung. May 3, 2017. Retrieved May 5, 2017 .
- ↑ MultiSIM & Co .: One number, several SIM cards teltarif.de
- ↑ Nationwide series of frauds in online banking Süddeutsche.de, October 24, 2013
- ↑ 77,826.33 euros simply debited Süddeutsche.de, October 9, 2013
- ↑ New fraud series with the mobile Tan number Süddeutsche.de, August 17, 2014
- ↑ Ronald Eikenberg: Online banking Trojans target chipTAN users Heise Security, September 5, 2012, accessed on February 3, 2018
- ↑ Bert Ungerer: Trojan believes wrong transfer before Heise Security, June 1, 2013
- ↑ Postbank, Current Security Information, accessed on December 6, 2013
- ↑ Achim Sawall: Online banking: Costs for TANs via SMS are often borne by customers . In: Golem.de . November 7, 2011 ( golem.de [accessed July 25, 2017]).
- ↑ BGH, judgment of July 25, 2017, Az.XI ZR 260/15 (still unpublished, as of July 15, 2017)
- ↑ Augsburger Allgemeine: BGH: Only SMS-TANs actually used may cost extra . In: Augsburger Allgemeine . July 25, 2017 ( augsburger-allgemeine.de [accessed July 25, 2017]).
- ↑ Online banking with pushTAN - FAQ berliner-sparkasse.de, Berliner Sparkasse (AöR), accessed on August 27, 2014
- ↑ Dominik Hayon: Online banking is changing for many: iTANs are being abolished. December 24, 2018, accessed October 2, 2019 .
- ↑ Stiftung Warentest: current accounts and online banking - an overview of the Tan process - Stiftung Warentest. September 17, 2019, accessed October 2, 2019 .
- ↑ media.ccc.de: 34C3 - The fabulous world of mobile banking. December 28, 2017, accessed August 6, 2018 .
- ↑ heise online: 34C3: "Nomorp" leverages the protective shield of numerous banking apps. Retrieved on August 6, 2018 (German).
- ↑ Federal Association of German Volksbanken and Raiffeisenbanken: Volksbanken and Raiffeisenbanken rely on the chip card and HBCI against phishing presseportal.de, August 12, 2005, accessed on August 21, 2019
- ↑ BW-Bank press release on the TAN generator. (PDF) January 4, 2007, archived from the original on September 19, 2010 ; accessed on January 29, 2014 .
- ↑ The TAN process Sm @ rtTAN plus. vb-hohenneuffen.de, Volksbank Hohenneuffen eG, archived from the original on April 13, 2014 ; Retrieved April 10, 2014 .
- ↑ DG VERLAG presents innovative card solutions dgv-webservices.de, Deutscher Genossenschafts-Verlag eG, January 20, 2006 (PDF; 102 kB)
- ↑ Sm @ rt-TAN plus bbbank.de, BBBank eG, accessed on September 27, 2015
- ↑ Online banking with the TAN box: safe and convenient. ( Memento of the original from October 1, 2015 in the Internet Archive ) Info: The archive link was inserted automatically and has not yet been checked. Please check the original and archive link according to the instructions and then remove this notice. wuestenrotdirect.de, Wüstenrot Bank AG Pfandbriefbank, April 2013 (PDF; 312 kB)
- ↑ The cardTAN raiffeisen.at, info page of the Raiffeisen Banking Group Austria, accessed on April 1, 2014
- ↑ The new cardTAN ebankingsicherheit.at, Gemalto NV, accessed on 22 October 2014
- ↑ Man-in-the-middle attacks on the chipTAN comfort procedure in online banking RedTeam Pentesting GmbH, November 23, 2009, accessed on October 27, 2010
- ↑ chipTAN procedure-der-Sparkassen-tricked on Heise Security
- ↑ https://www.sparkasse.de/service/sicherheit-im-internet/tan-verfahren.html#chiptan Overview of the variants of chipTAN, accessed on August 22, 2019
- ↑ https://www.vr-dienste.de/cms/sicherheit/sicherheitsverfahren/smarttan-photo.html Sicherheitsverfahren sm @ rtTAN photo, accessed on August 22, 2019
- ↑ Operating instructions photoTAN reader on commerzbanking.de ( Memento from February 21, 2014 in the Internet Archive )
- ↑ Announcement of the collaboration ( Memento of the original dated December 2, 2013 in the Internet Archive ) Info: The archive link was automatically inserted and not yet checked. Please check the original and archive link according to the instructions and then remove this notice. of Commerzbank with Cronto dated February 6, 2013, accessed on August 19, 2013
- ↑ commerzbanking - photoTAN. In: commerzbanking.de. Commerzbank Aktiengesellschaft, archived from the original on April 22, 2014 ; Retrieved April 30, 2013 .
- ↑ New at comdirect: photoTAN. Press release. In: comdirect.de. comdirect bank AG, April 9, 2013, accessed on April 30, 2013 .
- ↑ Raiffeisen launches e-banking login via PhotoTAN raiffeisen.ch, Raiffeisen Switzerland Cooperative, November 19, 2012 (PDF; 42.6 kB)
- ↑ The photoTAN - Our picture for your security deutsche-bank.de, Deutsche Bank AG, accessed on March 12, 2015
- ↑ Rabobank Selects VASCO CrontoSign Technology for Online Banking Security and Customer Convenience ( Memento of the original from July 24, 2015 in the Internet Archive ) Info: The archive link was inserted automatically and has not yet been checked. Please check the original and archive link according to the instructions and then remove this notice. vasco.com, VASCO Data Security International Inc., September 18, 2014
- ↑ VASCO Announces Acquisition of Cronto ( Memento of the original dated April 2, 2015 in the Internet Archive ) Info: The archive link was inserted automatically and has not yet been checked. Please check the original and archive link according to the instructions and then remove this notice. vasco.com, VASCO Data Security International Inc., May 20, 2013
- ↑ photoTAN. In: www.ing.de. ING-DiBa AG, accessed on September 9, 2019 .
- ↑ 1822direkt is now offering QR-TAN. In: 1822direkt.com. 1822direkt Gesellschaft der Frankfurter Sparkasse mbH, archived from the original on February 21, 2014 ; Retrieved April 30, 2013 .
- ↑ LinOTP QR-TAN procedure ( Memento of the original from December 8, 2015 in the Internet Archive ) Info: The archive link was automatically inserted and not yet checked. Please check the original and archive link according to the instructions and then remove this notice. lsexperts.de, LSE Leading Security Experts GmbH, accessed on November 27, 2015
- ^ OATH Challenge Response Algorithm. In: ietf.org. IETF, accessed May 13, 2013 .
- ↑ Kristina Beer: Commerzbank offers photoTAN. In: heise.de. Christian Heise, Ansgar Heise, Christian Persson, February 7, 2013, accessed April 30, 2013 .
- ↑ Mobile phone as TAN generator Heise Security, December 21, 2012
- ↑ Vincent Hauptert: PhotoTAN banking is not secure. Friedrich-Alexander-Universität Erlangen-Nürnberg , October 20, 2016, accessed on October 31, 2016 .
- ↑ Research Group "RedTeam" RWTH Aachen warns against false sense of security of the new method iTAN RedTeam Pentesting GmbH, August 25, 2005 accessed 27 October 2010
- ^ Daniel Bachfeld: iTAN procedure less secure than claimed by banks. In: Heise Newsticker. August 26, 2005, accessed October 27, 2010 .
- ↑ Banking Trojan infection without Trojan Heise Security, July 23, 2014
- ↑ Zeus Trojan intensifies attacks on mTANs Heise Security, August 7, 2012
- ↑ 30 years ago: Online banking starts in Germany Heise Newsticker, November 12, 2010
- ↑ European patent specification EP1259046 accessed on September 13, 2018
- ↑ Fierce legal dispute over the TAN procedure: "They're actually laughing at us" orf.at, August 3, 2018, accessed August 21, 2018






![{\ displaystyle P = {\ frac {100} {10 ^ {6}}} + \ left (1 - {\ frac {100} {10 ^ {6}}} \ right) \ cdot \ left [{\ frac {100} {10 ^ {6} -1}} + \ left (1 - {\ frac {100} {10 ^ {6} -1}} \ right) \ cdot {\ frac {100} {10 ^ { 6} -2}} \ right] = 0 {,} 0002999703 \ ldots \ approx 0 {,} 03 \, \%}](https://wikimedia.org/api/rest_v1/media/math/render/svg/de814f5a8b5d18be79b809b7c00c9d771e4748c2)