Spam
As spam / spæm / or junk ( / dʒʌŋk / , English for Garbage ') are undesirable, transmitted usually electronically mass messages referred to (information) to be delivered to the recipient unsolicited, often harass him and also contain frequently promotional content . This process is spamming or spamming called the polluter spammers .
Origin of the term
SPAM was originally a brand name for canned meat, which originated in 1936 from SPiced hAM , incorrectly also called Spiced Pork And Meat / hAM or Specially Prepared Assorted Meat . During war rationing, spam was one of the few foods available virtually everywhere and in unlimited quantities in Britain. The omnipresence of this flesh, similar to the later unwanted messages (for example as e-mails), promoted the development of the term. As a synonym for unnecessarily frequent use and repetition, the term was coined by the spam sketch from the English comedy series Monty Python's Flying Circus : In a café, the menu consists almost exclusively of dishes with spam . Several times , a group of Vikings loudly starts a song, the text of which consists almost entirely of the word spam, which makes normal conversation impossible. The word creeps more and more into the texts of a tourist and a newscaster, and the credits of the episode are inappropriately teeming with "spam" and a few other foods (e.g. Graham spam spam spam Chapman ).
The use of the term spam in connection with communication probably has its origin in the multi-user dungeons , i.e. text-based computer role-playing games for several players, in the 1980s. There, spam did not initially refer to advertising, but rather the massive flooding of the text interface with their own messages, as practiced by some users .
In connection with advertising, the phenomenon of spam was first brought up on Usenet . There it is used to refer to articles that are repeated several times in the newsgroups that are essentially the same or advertise the same service.
The first spam e-mail was probably sent on May 3, 1978 with advertising content from the DEC company , although it was not designated as such until 1993.
Effects
| worldwide virus and spam dispatch | ||||
|---|---|---|---|---|
| country | ||||
| China | Viruses | 16% | ||
| Spam | 45% | |||
| Singapore | Viruses | 10% | ||
| Spam | 35% | |||
| Ireland | Viruses | 8th % | ||
| Spam | 67% | |||
| Germany | Viruses | 8th % | ||
| Spam | 64% | |||
| Hong Kong | Viruses | 7% | ||
| Spam | 62% | |||
| Austria | Viruses | 5% | ||
| Spam | 50% | |||
| Japan | Viruses | 5% | ||
| Spam | 36% | |||
| France | Viruses | 4% | ||
| Spam | 51% | |||
| Australia | Viruses | 4% | ||
| Spam | 40% | |||
| Switzerland | Viruses | 3% | ||
| Spam | 75% | |||
| Great Britain | Viruses | 3% | ||
| Spam | 60% | |||
| Belgium | Viruses | 3% | ||
| Spam | 56% | |||
| Netherlands | Viruses | 3% | ||
| Spam | 50% | |||
| United States | Viruses | 2% | ||
| Spam | 77% | |||
| Canada | Viruses | 1 % | ||
| Spam | 77% | |||
| based on received emails in 2005 | ||||
Spam causes considerable damage in the system of global communication. This is mainly due to the additional amount of data and the effort involved in processing.
- Sorting out and reading spam takes time.
- Spam filters need to be obtained and maintained.
- Since companies and Internet service providers typically do not bill their lines according to time, but rather according to the amount of data transferred, there are costs for every byte of spam that is transferred.
- The processing of the mails can lead to a failure or to a slowdown in the desired mail traffic. The compensation of the load in turn generates costs for new, more powerful hardware.
- In the case of fax spam , costs can arise from the consumption of paper and ink or toner.
Spam causes $ 22 billion in annual damage in the United States alone . According to a study carried out in 2009, 62 trillion spam emails consume around 33 billion kilowatt hours of energy and 100 billion hours of working time to view and delete spam emails. According to this, spam now makes up 89 to 97% of the total e-mail volume, depending on the estimate.
Types of Spam
Email spam
Unsolicited bulk email
First of all, unsolicited bulk e-mail ( UBE for short ) should be mentioned because of its large volume and the resulting level of awareness . These are emails that are sent to a large number of recipients. Often these are email marketing campaigns - but proselytizing or inciting emails and chain letters also belong in this category.
Due to the abundance of variants, specific terms have emerged for some particularly common types, such as scam , phishing , joe job , hoax and stock spam .
Unsolicited commercial email
The unsolicited commercial e-mail (UCE for short, from English "Unsolicited Commercial E-Mail") is an e-mail with commercial content that is sent to recipients (including a few or individual). UCE is legal in Germany under certain circumstances, see legal situation in Germany . Typical examples of UCE are dubious or particularly cheap offers for sex, sexual enhancers , pornography, penis enlargement , illegal online gambling casinos, fake watches, life extensions, software, branded products, financial services or drugs, etc.
Collateral spam, backscatter
As collateral spam or backscatter emails are called, which generated in response to an incoming e-mail and delivered an unrelated third party. Collateral spam is often triggered by malware - or spam emails, as fake senders are usually used here.
There are two main ways in which collateral spam arises:
- If e-mails are sent with a forged sender address (the address of the uninvolved third party), the receiving e-mail system first accepts this e-mail and then sends a non-delivery message , an absence message or similar to the alleged sender.
- Collateral spam is also generated by recipients who, misunderstanding the situation, cover the alleged sender of a spam mail or a virus with complaint e-mails or e-mail bombs .
See also: Backscatter (email)
Usenet spam
In the mid-1990s, when very few people and companies had an e-mail address and, if only for this reason, mass sending of e-mails was not yet possible, the word spam found its way into Usenet. It should describe the activity of individuals to post their always identical advertising in thousands of newsgroups, without worrying about the misappropriation of the topic or being interested in the subsequent discussions.
The very first spam to contaminate an extremely large number of newsgroups was an advertising campaign by the Canter & Siegel (USA) law office in 1994 to encourage participation in the drawing of green cards .
Search engine spamming
When search engine spamming is trying to influence positively on entries in their own or other websites the scoring algorithms of search engines.
Referrer spam
Referrer spam is a special form of search engine spamming. Here, websites are called en masse so that they appear as referrers in the log files of the web servers of the attacked websites.
Spam over Internet Telephony (SPIT)
As VoIP spam , just SPIT , unwanted and automatically rehearsed calls by are VoIP referred. An attempt is made to automatically establish telephone connections (when using the SIP protocol using INVITE messages). If the called subscriber answers, the audio data (e.g. a recorded advertising message) is played in via the RTP protocol .
Spam over Mobile Phone (SPOM)
Communication by mobile phone is also affected by spam. Unwanted short messages or calls are referred to as (mobile) phone spam , sometimes also as spam over mobile phone (SPOM) . Due to the increased use of mobile marketing for market research and unsolicited short messages, mobile phone spam already reaches up to 90% of the electronic message volume in Japan. One variant are so-called spam or ping calls , which only last a fraction of a second and are intended to induce the called party to call back an expensive value-added service .
Others
Other forms of spam are Spam over Instant Messaging , or SPIM for short , which uses protocols such as B. IRC , ICQ or the Windows messaging service or Spam over Presence Protocol , SPPP for short .
Technical requirements for e-mail spam
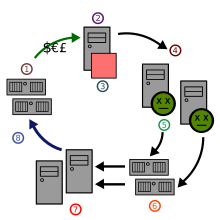
In order to send unsolicited e-mail advertising, all you need is an e-mail program that provides spam e-mails with the recipient addresses, as well as an SMTP relay server , which then sends these e-mails to the recipients . Since every e-mail can contain a lot of address data, only a comparatively small bandwidth is required for transmission to the relay server, a simple Internet connection and an average computer are sufficient.
In the past, open mail relays were often used as relay servers, i.e. poorly configured mail servers were misused. This procedure has two main advantages for the spammer: the sender is concealed and your own resources are saved. Thanks to realtime blackhole lists , the number of open mail relays has meanwhile decreased significantly. Therefore, some spammers soft on botnets out to her to send spam.
Countermeasures
General measures
Authorization
To prevent the user from being annoyed by unwanted people, most instant messengers offer the option of only delivering messages from approved people. Chat rooms can also be set up so that only members are allowed to chat.
Traceability
Since sending unsolicited advertising is illegal in most countries as well as in Germany, the sender can be sued if he is traceable. The sender's identity can be found out via the sender's IP address if the Internet provider saves the assigned IP address with the assignment of the customer.
Measures against email spam
In general, measures can be taken at every instance that generates or transports spam to reduce the volume of spam. Currently, spam is mainly combated through spam filters. Newer methods suggest fighting spam through corrections in the Simple Mail Transfer Protocol (SMTP) or in the Domain Name System (DNS). Occasionally, there are also suggestions to make it more difficult for spammers to collect recipient addresses, but this only prevents the collection of addresses on the Internet due to the existing address trade, but not the use of addresses from other sources (e.g. competitions or online orders). So-called greylisting is another effective method . This can reduce spam by around 95%, but the disadvantage is that incoming messages only arrive with a delay.
Prevent your own e-mail address from being added to spammers' address lists
Disposable email addresses and alias addresses
If an e-mail address is required to register for a service, a disposable e-mail with an internal counter ( e.g. from Spamgourmet ) and a time-limited validity or an alias address can be used to identify your own Hide main email address.
E-mail address obfuscation
Since most e-mail addresses from the Internet are automatically extracted from the newsgroups and websites by so-called address harvesters , it promises some success not to mention any addresses there or to disguise the addresses in such a way that they are not from the address harvesters being found.
For this purpose, the addresses are changed in such a way that they can only be understood by people, not by machines. For example, instead of [email protected], the address [email protected] (remove XYZ) is given. Simple robot programs do not recognize the manipulation - the email address [email protected] remains UBE-free.
Forgeries in the domain part of an email address (i.e. behind the @ sign) are also possible. In order to deliberately use an invalid address and make it easier for postmasters to recognize, the Top Level Domain (TLD) .invalid was invented.
Often, a list of employees is simply kept and a note is attached at the top of the page: the email addresses of the respective persons correspond to the scheme first [email protected].
The frequently recommended Unicode encoding of the characters in the form & # x61; & # x40; & # 98; & # x2e; & # x63; Replacing the @ with (at) , [at] or similar is hardly an obstacle for address collectors, since the command line- enabled browser Lynx , for example, can correctly read the addresses ( ) or search for different spellings of the @. However, it helps against many simple address collectors.
lynx -dump <url> | grep @
The problem with these measures is that many users use mail programs that do not allow simply deleting XYZ from the mail address. In the header of Usenet articles, i.e. in the settings of the news reader, this measure violates RFC 1036 and RFC 2822 .
In addition, the view is justified that the falsification of e-mail addresses does not combat the causes of spam, but only affects users and uninvolved third parties: the responding recipient has additional work to change the address, and third parties can be harassed if the manipulated Address actually exists (but belongs to a third party, not the sender).
Encryption using JavaScript is also often suggested. To avoid this, the harvester must integrate a JavaScript-enabled browser . However, this excludes users of browsers that do not support JavaScript or those with JavaScript deactivated. Here's an example
<a href="javascript:location='mailto:'+'info'+ /* Kommentar */ '@ex' + 'ample.org'">E-Mail senden</a>
A much simpler encryption with modern browsers, at least in websites, can be done via CSS , for example in the form:
mailname<span style="display:none;">-Entfernen Sie diesen Text- </span>@<span style="display:inline;">example.com</span>
The generated display is easy to read with CSS even for people without a browser, while address collectors have so far foregone the evaluation of CSS for reasons of efficiency and therefore do not filter out the correct address.
It is also possible to save the email address graphically, for example in the form of an image. Here, too, it can be read by most people, but automatic collectors have not yet read addresses from text in pictures. It should be noted that text readers, such as those used by the visually impaired, cannot read addresses displayed in this way (see also: Accessible Internet ).
There are other options, some of which offer greater security or flexibility than the above solutions, but which can only be used in individual cases due to the technical requirements. Example: If you have administrative access to the mail server and the website can be generated dynamically, you can generate a random, unpredictable e-mail address when you call up the website, for example [email protected], and enter this temporarily as valid in the mail server . After a specified period of time, it is automatically removed from the mail server. This means that a visitor to the website can contact the barrier-free e-mail address, but sending spam later will fail because the address is no longer valid.
Access control
So-called captchas , which are used to distinguish people from machines, offer a high level of security . For example, it is suggested to include the email address in a picture or to spell it out in an audio file. However, these solutions are neither particularly convenient nor barrier-free . Even if they are specified as audio files and images, they are incomprehensible for the deaf-blind , for example , and even for sighted people these images are not always legible due to visual defects or color perception disorders.
With Mailhide, Google offered a reCAPTCHA- protected service to protect the email address. HTML code was generated for a mail address to be protected, which the user can embed on a website. In order to see the email address, website visitors had to solve two reCAPTCHA tasks. mailhide.io now provides a comparable function.
As an alternative to captchas, honeypots and time measurements are available to combat spam and still operate barrier-free offers.
In Usenet and on mailing lists , an unread garbage address can also be entered in the From header and the actual address in the Reply To . This means that replies arrive at the correct address, but the perpetrators usually only scan the from addresses.
On websites, contact forms ( CGI or PHP ) are an alternative to specifying the e-mail address. They offer the reader the possibility of contacting the contact person without specifying an e-mail address and thus harvesting the e-mail Address is bypassed. This is done at the expense of convenience, as the sender cannot use his familiar writing environment (e.g. keyboard shortcuts, text blocks, copies to himself or other recipients).
Use of BCC
In order not to distribute e-mail addresses unnecessarily, it can make sense not to address e-mails intended for a closed group of recipients to anyone ( undisclosed recipients ) or to yourself and the actual recipients in the BCC - Field to set. These then receive a so-called blind copy (BCC, Blind Carbon Copy). The addresses in the BCC field are not transmitted to the recipients.
However, this method also has disadvantages. Some spam filters rate mails that reach the recipient via BCC as negative, that is, they see sending via Blind Carbon Copy as a possible criterion for spam. Anyone who regularly sends mails to a large group of recipients should therefore consider setting up a mailing list .
Measures for operators of mail servers
If the individual user can only prevent himself from receiving UBE, administrators of mail servers have the option of restricting the distribution of UBE. This starts with the correct configuration of the mail server, which should only allow authorized users to send e-mails.
On the other side, the mail server can refuse to receive e-mails that originate from so-called open relays , via which anyone can deliver unauthorized mail. Several organizations, for example the Open Relay Database , offer lists of such misconfigured mail servers ( RBL ) that the server administrator can use for checking. Since open relays are increasingly rare, a far more effective option is to allow delivery through dial-up access only after authentication. There are also public databases for this purpose ( DialUp Lists (DUL) ).
Broad support of SMTP message submission by mail server operators could help in the medium term to curb the spread of spam and malware via botnets. If the end user's mail programs are only allowed to deliver their mail via the message submission port 587, the operators of mail servers (ISPs) can make the delivery of spam much more difficult: Incoming mail data traffic from external via SMTP (TCP port 25) can be heavily filtered in particular, mail from dial-up networks (mainly from Trojanized PCs) can be rejected. This measure will only help against the sending of spam from Trojanized PCs themselves, since the botnets can also be sent via message submission if necessary. SMTP message submission is already supported by many mail server operators.
So-called tar pits cannot prevent UBE from being delivered, but they offer a countermeasure against the perpetrators' dispatch mechanism by stopping a UBE-dispatching counterpart from working with extremely slow reactions. The communication between the receiving system and the UBE sending system becomes as viscous as tar, instead of just fractions of a second the sending process takes several minutes, making it impossible to deliver a lot of spam emails in a short time.
With automatic white / blacklist filters, the recipient's mail system first replies to all unknown senders and asks them to register with the mail system. By taking an action (e.g. copying a number from a generated image) the sender confirms that he is a person and that he is seriously interested. If he answers correctly, the recipient will receive the email that has been suspended until then. The sender is then added to the whitelist . If it is spam, the sender can be moved from the white list to the black list .
There are other registration options in the W / B filter process, for example via a URL with ID (example: http://www.example.com/mail.php?ID=20032311-021). Systems of the type that require the sender to respond are also known as challenge-response systems . However, many users and (especially) administrators see it as an inadequate system for UBE avoidance, for the following reasons:
- In the best case scenario, the sender address of a UBE is provided with an invalid address, and normally with the address of an uninvolved person. In the case of an invalid address, attempting to deliver the challenge mail will result in a bounce, which means wasting resources. If the address is valid, it is harassed by the challenge-response system , which technically turns the system user into the perpetrator (collateral spam).
- If the user of a challenge-response system sends a mail to a challenge-response system (e.g. a mailing list with a confirmed opt-in ), the effect is that both systems wait for the response from the other system (the mail list on the explicit confirmation that the e-mail address should be included in the list, the system of the user that the mail list is authenticated as a regular user). Such a user is then usually accepted by the mail list operator manually editing, which results in a corresponding additional administrative effort for them.
- A user of a CR system who takes part in a mail list generally causes a large number of challenge mails, since the sender address is generally not changed for mails to the mail list. As a result, everyone involved in the mailing list must authenticate himself to each individual user of such a system so that he or she can receive the respective mail from the mailing list. Since this exceeds the acceptance threshold of many users from a certain number of users of CR systems within a mail list, this usually leads to the users of such systems excluding themselves from the discussions sooner or later.
Black and gray lists (RBL and greylisting)
RBL servers are servers on which the addresses of known spam senders are collected in real time. The incoming mail server can query these servers before accepting mail. If the sender is in an IP range from which spam is frequently sent, the acceptance will be refused. This often happens regardless of whether the specific sender address actually sent or sent spam. A well-known, freely accessible RBL server is www.spamhaus.org .
Gray lists take advantage of the fact that spam spammers often do not follow the mail protocol correctly. When an email arrives, acceptance is initially refused with a simulated error message and the sender address is temporarily placed on a gray list . If the sender repeats the shipment after a certain time, they are considered compliant and will be removed from the gray list; otherwise it is ignored. Upon request, a sender recognized as compliant can be entered in a white list and will be accepted immediately in the future. However, it can also happen that serious senders fail this procedure if their mail servers are configured incorrectly.
Spam filter
There are now a number of different spam filtering techniques for the automatic detection and removal of spam in the mailbox. Some e-mail programs such as B. Mozilla Thunderbird or Microsoft Outlook have integrated spam filters that sort out advertising e-mails from the start.
However, the filters suffer from their error rates: Spam mails are often not reliably detected and still get into the inbox, which is referred to as false negatives . The reverse error is also possible: Desired emails can be classified as spam if the filters are too strict (so-called false positives ) and may not reach the recipient or reach the recipient with delay.
Only well-configured spam filters that are individually tailored to the user or a user group have high success rates. In such cases, false positives can be almost completely ruled out and false negatives can be reduced to 10% to less than 1%. However, the one-time effort is high and requires a certain amount of experience. In addition, the filter has to be constantly adapted to the new methods of the spammers using new and improved methods.
Filters have the disadvantage that due to the error rates discussed (which are always present) the user has to check the e-mails that were filtered out again in case of doubt and the actual purpose of the filter is thus limited to presenting a preselection for the user . Conversely, it must be clear to the recipient that the manual filtering of emails also has considerable potential for false positives . It can be more efficient to rely on a good spam filter than manually filtering , especially when there is a high volume of email .
From a legal point of view, filtering is critical under certain circumstances: If the provider or employer filters without the consent of the recipient, this is a criminal offense according to widespread case law (see the legal literature below). This problem can be circumvented to a certain extent by rejecting emails recognized as spam as soon as they are received. According to the prevailing opinion, the e-mail is then deemed not to have been delivered, the sender receives a non-delivery notification and can therefore fix the problem, work around it or contact the recipient in another way.
Complaints / legal process
If the direct complaint to the spammer does nothing, you can complain to the spammer's provider. If the desired effect does not materialize afterwards, only legal recourse remains: Due to the procedural costs and fines to be paid, sending spam can possibly become expensive in the long term. However, this way causes a lot of work when fighting manually.
You have less work if you automate the complaints as much as possible in order to deal with as many as possible per day. Critics of (semi-) automated spam reports, however, rightly point out that automated complaints or complaints generated via corresponding service providers / software are not only often faulty and therefore not infrequently affect bystanders, but are also deleted across the board by the complaint handlers of many providers . The provider can also classify such messages as spam if it reaches too many from one sender.
The more sensible alternative can therefore be a handwritten complaint that relates to several spam messages received promptly from the same source.
What needs to be analyzed is the header of the email, which is not automatically displayed by many mail clients. Everything in it is easy to forge except the IP addresses of the MTAs ( mail servers ) that transported the email. These are in header lines that begin with the keyword Received . Which provider the IP address belongs to can be determined with the Unix command whois and the whois server of the responsible registry.
The format with which the individual Whois servers respond is not standardized. Since everyone can set up their own server, provider and perpetrator can be identical.
Most providers have their own complaint address, which is not always entered in the Whois server. To find out which is the correct complaint address for a particular domain, you can use Abuse.net and check with the provider there.
Service providers such as SpamCop offer options for automating this investigation and complaint process.
Internet complaints office
The internet complaints office of the alliance partner eco -Verband has been accepting spam complaints since January 1, 2007 , and the consumer advice centers have been available for legal advice on spam since then .
By December 31, 2006, the consumer association Bundesverband e. V. (hereinafter abbreviated to VZBV) took care of the prosecution and punishment of unwanted e-mails in a test project . On July 1, 2005, the Federal Ministry for Consumer Protection, Food and Agriculture (BMVEL) together with the German Consumer Association. V. started a complaint office project to combat spam, which has since been suspended. Consumers could send unwanted spam to the VZBV by email at [email protected]. The VZBV checked these cases and, in appropriate cases, took legal action against spam senders and their clients. The VZBV worked with other consumer advice centers around the world. His goal was to make spam unprofitable by any legal means. The service was free and was only intended for private individuals. Registration was not necessary.
The thing had an effect. In particular, spammers from Germany and the legal area of the EU could no longer hide in the apparent anonymity of the WWW. But the VZBV was also active internationally thanks to several partnerships. The advantage over spam filters was that the senders of spam were prosecuted, spamming was illegalized and thus the sending of spam decreased in the long term. The disadvantage was that the spam mails ended up in the mailbox for the time being and forwarding including the extended header was time-consuming.
eBay / PayPal
Even eBay or PayPal track - of course primarily in their own interests - spammers. They are sued for omission, with the aim of eliminating the spam emails about the company. eBay and PayPal follow up every lead and track the senders of spam mail worldwide. All you have to do is forward spam mails that claim to be eBay or PayPal or refer to them with the extended header to the following address: [email protected] or [email protected]. You will then receive an answer as to whether the mail was real or not, as well as general information on the topic.
mimicry
In addition to technical possibilities, there are other methods of preventing the perpetrator from carrying out his business. So recipients of UCE z. B. enter into the offered business with false personal data. This causes a flood of errors in orders from customers who have been recruited by the perpetrator for the dealer who is assisted by the perpetrator. This may even lead to the termination of the business relationship. This procedure can be automated (for example with proxies ), but it is legally highly questionable. Sending phishing emails can also be made more difficult by entering incorrect bank account details.
Senders of Nigeria Connection emails (advance fraudsters) can be kept busy simply by replying and leading aimless discussions, the so-called scambaiting . This ties up the perpetrator's time, but it can be dangerous because it disturbs criminals, who usually have connections to Europe and North America. Scambaiting should only be carried out by experienced persons or under their guidance in order to avoid the transmission of data that could lead to identification. This includes in particular personal data such as name, address and bank details, but also your own pictures, nicknames in forums and chats, IP or e-mail addresses and telephone numbers.
SpamMatters
Australia has developed a very convenient and effective method of fighting it. The Australians are provided with the free program SpamMatters , which transmits emails marked as spam by the user to the Australian telecommunications authority ACMA . This identifies the spammer and informs the responsible law enforcement authorities.
Measures against Usenet spam
- The most immediate and effective tool is canceling. This causes all configured news servers to delete the spam. The faster it reacts to spam, the more successful this measure is, because it only benefits those who have not yet downloaded the spam from the news server with the newsreader. Canceling spam requires careful compliance with a variety of rules, and you can do a lot wrong.
- Complaints to the spammers' news providers can mean that they are deprived of the ability to use the respective news server.
- Very rarely, news providers who do not respond to complaints are subject to a Usenet Death Penalty (UDP), which can take two forms:
- Passive UDP: The administrators of the most important news servers agree that all Usenet articles that have run through the black sheep's news servers will not be forwarded and will therefore disappear.
- Active UDP: The spam cancellers agree to cancel all articles that have entered the Usenet from the black sheep's news servers , as if they were spam.
- Newsgroups that have sex in their name can be renamed. This has happened very successfully with the former newsgroup de.talk.sex, which is now called de.talk.liebesakt and thus hardly attracts spam.
- NoCeM as an alternative to canceling: While canceling requires a separate cancel message to be sent after each individual spam article, this procedure manages with control messages that contain entire lists of spam articles. However, these NoCeM control messages are only understood by special clients that are not particularly widespread and, in contrast to cancel messages, are not able to thwart discussions about the spam as a result of spam, which are not related to the respective newsgroup that make newsgroups illegible.
- Moderated newsgroups: The posts do not reach Usenet in an uncontrolled manner, but are processed by a moderator who can intercept spam. It is not always possible to find a volunteer for this position. The formerly very successful job advertisement newsgroup misc.jobs.offered had to be abolished for this reason.
- Server-side measures: News server software can be supplemented with add-ons that recognize and reject spam. This includes B. the software Cleanfeed .
- Client-side measures: Most news readers have a so-called kill file that controls what you see. The Bayesian filter sorts wanted and unwanted emails after training by the user of the email client.
- Disposable e-mail addresses : When using disposable e-mail addresses, the user enters a temporary, valid e-mail address instead of his own address. The user keeps his actual address anonymous and prevents his e-mail account from being covered with spam.
Legal position
Legal situation in Germany
A question of liability for the dispatch of e-mail worms and Trojans, which are likely to make up the largest share of UBE after UCE, is still controversial in Germany. Under very limited conditions, some authors see at least companies as liable; for private individuals, the literature predominantly denies any liability. An injunction against accidental worm senders has not yet been enforced. The creation and distribution of worms, viruses and Trojans as computer sabotage is relevant under criminal law. In 2005, a student in Germany who wrote Netsky and Sasser was sentenced to one year and nine months in prison on probation.
Unsolicited e-mail advertising can give rise to both a competition law and a private law injunction on the part of the recipient against the sender. It is irrelevant whether and how often the spammer has already spammed: An injunction arises from the first e-mail.
Competition law
According to the established jurisprudence of the instance courts and meanwhile also of the BGH (BGH, judgment of March 11, 2004, AZ: I ZR 81/01) on the old law against unfair competition (UWG), sending unsolicited e-mails to the the same principles that are immoral and thus anti-competitive that have already been accepted in advertising by telex , fax and telephone .
As a result, the recipient cannot be expected to tolerate advertising that he has not consented to receive if this results in costs and / or other disruptions on the part of the recipient.
The new UWG (since 2004) unequivocally regulates the demands that are made on e-mail advertising so that it is flawless under competition law. This includes, in particular, that the recipient has previously consented to the sending of advertising by email. Only competitors of the spammer are entitled to injunctive relief from the UWG, even if the term competitor is interpreted broadly . In return, a right to cease and desist under competition law affects all business transactions. The spammer may no longer send unwanted advertisements to third parties. If he were caught doing this, he could face the payment of a fine to the state treasury or even custody . In fact, fines have already been imposed on spammers if they breached a court injunction.
Liability law
Less comprehensive, but individually protective and without a competitor position, a right to cease and desist against the spammer can also be derived from the general liability law. Like every injunction claim in this area, it is constructed from §§ 1004 analogously and 823 para. 1 BGB.
For private users , recourse is then made to the general right of personality , which is derived from the Basic Law , and the business user sees an encroachment on the right to the established and exercised commercial enterprise , which is also protected by constitutional rights . Both are other rights within the meaning of Section 823 (1) BGB.
Criminal law
Recently there has also been increasing discussion about prosecuting the sender of unsolicited advertising emails. One approach to this was provided by Thomas Frank's dissertation on the criminal management of spamming . A summary of this was in Computer und Recht 2/2004, pp. 123ff. printed. However, the case law on this is still inconsistent, in particular the public prosecutor's offices currently see no need for action, as the legal situation does not allow the public prosecutor's office to take legal action against spam without a law.
The Telemedia Act, which came into force on March 1, 2007, prohibits in Section 6 (2) concealing or concealing the sender and the commercial nature of the message. The violation of the prohibition is punished as an administrative offense with a fine .
Anti-spam law
On February 17, 2005, the German Bundestag discussed the draft of an anti-spam law in a first reading. The Anti-Spam Act is intended to expand the Teleservices Act by the following regulation:
- "If commercial communications are sent by electronic mail (e-mail), neither the sender nor the commercial nature of the message may be obscured or concealed in the header and subject line. Concealment or concealment is particularly the case if the header or subject line is intentionally designed in such a way that the recipient receives no or misleading information about the actual identity of the sender or the commercial character of the message before viewing the content of the communication. "
A violation of this regulation is to be punished as an administrative offense with a fine of up to 50,000 euros. However, the regulation would only prohibit misleading about the sender and content of the email, but not the unsolicited sending of advertising emails themselves.
The law was no longer passed in the 15th legislative period of the German Bundestag and could not come into force as an independent law in the 16th legislative period. Instead, a similar regulation was introduced in the new Telemedia Act as Section 6 (2), cf. the previous section Criminal Law .
The law against unfair competition protects consumers since 2004 but also independently comprehensively from harassment by unwanted advertising. and is mentioned as a reference in guides on legally compliant sending of e-mails.
Legal situation in Austria
In Austria from 1999 to 2003, the prior consent of the recipient (opt-in) was required for sending mass or advertising e-mails according to Section 101 of the Telecommunications Act (TKG) 1997, and UCE and UBE were therefore prohibited. The follow-up regulation, § 107 TKG 2003, allowed UCE to companies or authorities, with restrictions also for existing private customer relationships, if they can refuse further messages (opt-out). Mass or advertising emails to private individuals still require the recipient's prior consent (opt-in). Since March 2006 the dispatch of UCE and UBE (without the prior consent of the recipient) has been generally prohibited again. An email or a phone call to obtain such consent also fulfills the requirements of Section 107 TKG.
Legal consequences of violations
By making an unsolicited phone call, sending unsolicited fax or sending unsolicited electronic mail, the sender is committing an administrative offense and is punishable by a fine of up to € 37,000. The regional telecommunications offices are responsible for reporting a violation of Section 107 TKG. In addition, violations of the imprint and disclosure obligations as well as violations of the labeling requirement for (direct) advertising can be punished with up to EUR 2,180 or EUR 3,000.
The case law interprets annoying advertising as a violation of the Federal Act against Unfair Competition (UWG). Due to unsolicited communication, action for omission and damages can be sued.
Requirements for electronic mail without prior consent
In exceptional cases, prior consent for electronic mail is not required if the following five requirements are met:
- the sender has received the contact information for the message related to the sale or service to his customers and
- the message is used for direct advertising for own similar products or services and
- the customer has been given the opportunity to receive such messages when collecting and receiving
- refuse free of charge and without any problems with each transfer and
- the customer did not refuse the delivery in advance. In particular, it is not allowed to send to recipients who are entered in the Robinson list. This list is kept by the regulatory authority for telecommunications and broadcasting and must always be observed by the sender if there is no consent.
This exception only applies to electronic mail, but not to telephone calls and faxes. The consent requirement applies without restriction to these.
Bulk mailings
According to the law, electronic mail with more than 50 recipients is considered a bulk mail, even if it does not contain any advertising. Not every mass mail is illegal. There are special legal provisions for interest groups. The bulk mailing to a single recipient is also considered a bulk mailing (e.g. mass mails to several departments of one recipient).
approval
Consent can be expressly given by the future recipient by signing a declaration.
Labelling
Any (direct) advertising in electronic communication must be identified as such. The identification can be made, for example, in the subject line of an email. The words can be freely chosen, but it should be clear to the recipient that it is direct mail.
imprint
According to the company code (§ 14 UGB) and the trade regulations (§ 63 GewO), all emails must contain an imprint . For mailings that are distributed electronically at least four times a calendar year in a comparable format (e.g. e-mail newsletters), an imprint must be specified directly in the newsletter in accordance with the Media Act . In addition, disclosure must be made in the newsletter itself or via a link to a website.
Legal situation in other countries
In the rest of Europe, the legal situation is governed by the Directive of the European Parliament and of the Council on the processing of personal data and the protection of privacy in electronic communications (2002/58 / EC) of July 12, 2002, which was approved by the EU Member States to transpose into national law, the result was comparable:
The sending of e-mail advertising is only allowed if the recipient has given his prior consent. The specific implementation in the respective national law is different in the respective countries. Björn Bahlmann's dissertation provides an overview of the possibilities and limits of legal control of unsolicited e-mail advertising. International regulations and alternative solutions that are only available directly from the publisher.
In Switzerland sending spam is prohibited since 1 April, 2007. The Telecommunications Act prohibits the threat of fines or imprisonment from sending unsolicited mass advertising or commissioning it via email, SMS or other telecommunications channels. In addition, the providers and telephone companies are obliged, as far as they are known, to disclose the names and addresses of the senders so that the victims can file a lawsuit.
In the USA , the CAN-SPAM Act basically banned spam. The first spammers have already been arrested, and in 2004 a spammer in the USA was sentenced to nine years' imprisonment, but not for sending spam, but for other crimes such as computer fraud or identity theft.
Australia pioneered anti-spam legislation and was the first country to severely punish spamming. However, the government kept a loophole open: unlike in Germany (see e-card ), party advertising is allowed there.
Known spammers
- Gary Thuerk sent the first spam to 400 users connected to the ARPANET on May 3, 1978.
- Vardan Vardanovich Kushnir - died on July 24, 2005. The most notorious spammer in Russia was found slain in his apartment.
- James McCalla: Was sentenced to pay $ 11.2 billion in damages to a local Internet service provider on January 6, 2006 - the largest fine to date for a spammer.
- Daniel Lin: the 30-year-old US spammer was sentenced to three years in prison and a fine of 10,000 US dollars (7,500 euros) in the United States on September 6, 2006. This is one of the first proceedings under the US Anti-Spam Act (Can-Spam Act) introduced in 2003 to an end.
- Robert Soloway , one of the world's most active spammers, nicknamed "Spam King" by law enforcement agencies, was arrested on May 30, 2007 for federal crimes in the US and sentenced in July 2008 to 47 months in prison and a payment of over $ 700,000. He has been on parole since March 2011.
- Christopher Smith: In August 2007, the 27-year-old was sentenced to 30 years in prison, not for violating the CAN-SPAM Act, but for nine other offenses.
- Sanford Wallace : was sentenced together with Walter Rines by a US federal court to pay damages of 230 million US dollars to the Internet forum operator Myspace .
- Oleg Nikolaenko : arrested by the FBI in November 2010, also called the "King of Spam" by law enforcement agencies. It was responsible for an estimated third of all global spam.
News and outlook
In the fight for / against UBE, increasing efforts are being made on both sides. The UBE volume has increased exponentially in recent years. In 2003 the UBE volume exceeded the volume of regular emails for the first time, according to a report from www.spamhaus.org at the end of the year.
In November 2008, the Californian hosting provider McColo was disconnected from the network, the hosting plans of criminals to control botnets had been abused. As a result, the global amount of spam fell to a third to a quarter.
Increased effort for countermeasures - on both sides
In the following, the best-known measures against UBE and the resulting reactions by spammers against new filter and other techniques to avoid them are described. This clearly shows the increased effort on both sides.
Checking the validity of sender addresses led to the use of valid addresses. This had the effect of showering innocent people with thousands to millions of bounces.
The introduction of filters that checked e- mails for certain terms led to e- mails that contained intentional spelling mistakes ( e.g. V1a9ra instead of Viagra ) or that obscured the true content through invalid HTML (which is ignored by HTML-displaying mail readers).
The text filters against spam, which are getting better and better, can be avoided by sending advertising spam in the form of GIF images and so cannot be easily filtered. In addition, these images are easily modified from copy to copy using simple algorithms without reducing their readability. This makes them even more difficult to track down using the filter. Instead of images, there are also PDF attachments.
The blocking of known open relays and known UBE-sending servers led to the spread of Trojan horses , which repurposed the computers of regular users as UBE senders.
The introduction of central lists, which disseminated information via open relays and other things and which are increasingly used by mail operators, led to DoS attacks against the operators of the respective list and their ISPs .
It is assumed that the increase in worms in 2003 is due to the spread and implementation of statistical analysis tools (e.g. Bayesian filters ).
Some providers are going to monitor port 25 or to block it completely in order to prevent viruses that may be present from sending e-mails on this port.
New approaches: Replacement of SMTP with new mail transmission methods
The use of new mail transmission methods that allow authentication of the mail servers involved is intended to replace the previous system ( SMTP ).
A new standard is being created by the IETF , while major mail providers are working on their own solutions. The Sender Policy Framework (SPF) is a concept that makes it difficult to falsify e-mail sender addresses and is based on an additional DNS -TXT entry. Patches are already available for many popular so-called MTAs (Mail Transfer Agents). However, this procedure makes mail forwarding more difficult.
Another approach is the introduction of virtual stamps, which Hashcash is pursuing , for example . The sender has to invest a few seconds of computing time for each email sent to create such a virtual stamp, which is only valid for a limited period of time and for a specific recipient address. On the receiving end, e-mails from unknown senders are then only accepted by a filter program such as SpamAssassin if they are provided with valid stamps. As a result, sending e-mails in bulk would mean considerable additional effort, while the occasional sender is hardly affected. An advantage of this method is that checking the validity of a virtual postage stamp can be done with very little computational effort (compared to generating the postage stamp). One weak point is that perpetrators no longer use their own computers and therefore have more computing power available.
See also
- Certified Senders Alliance
- DomainKeys , a method for authenticating e-mail senders
- GTUBE
- Robinson list
- Spam stocks
- Social Network Spam
- Thom's version of Friday's friendly torture questionnaire , a standard text for spam recipients of all kinds
- Unsolicited telephone advertising
- Litter broadcast
literature
Comparative law
- Björn Bahlmann: Possibilities and limits of the legal control of unsolicited email advertising. International regulations and alternative solutions. Publishing house Dr. Kovac, ISBN 3-8300-1276-4 .
- Weiler: Spamming - changing the European legal framework. In: MMR. 2003/04, No. 223 ff.
- Wendlandt: European, German and American regulations of e-mail advertising - considerations for the benefit of the CAN-SPAM Act. In: MMR. 2004/06, No. 365 ff.
- Commission of the European Communities: COMMUNICATION FROM THE COMMISSION TO THE EUROPEAN PARLIAMENT, THE COUNCIL, THE EUROPEAN ECONOMIC AND SOCIAL COMMITTEE AND THE COMMITTEE OF THE REGIONS on combating spam, spyware and malware. Brussels, November 15, 2006. (PDF full text)
German legal situation
- Legal aspects when using spam and virus filters. In: Peter Eisentraut, Alexander Wirt: Fighting Spam & Viruses with Open Source Tools . O'Reilly, Beijing / Cambridge / Farnham / Cologne / Paris / Sebastopol / Taipei / Tokyo 2005, ISBN 3-89721-377-X , pp. 313-317. (PDF; 355 kB)
- Thomas Frank: To deal with spamming under criminal law. Kognos Verlag, Berlin 2004, ISBN 3-8325-0491-5 .
- Thomas Frank: You've got (spam) mail. On the criminal liability of e-mail advertising. In: Computer und Recht 2/2004, p. 123 ff.
- Jörg Heidrich, Sven Tschoepe: Legal Problems of E-Mail Filtering. In: MMR . 2004/02 Rd no. 75ff.
- Jörg Heidrich, Sven Tschoepe: Punishable filtering. Legal pitfalls for antispam software
- Thomas Engels (lawyer): Advertising by fax - How NOT to do it ... - Contribution to the legal situation with fax spam according to the old and new UWG. upright.de/3991
- Peter Sester, Sibylle Mutschler: New partnerships and legal developments in the fight against spam. In: Computer Science Spectrum . Issue 1, 2006.
- Gerald Spindler, Stefan Ernst: Drafting contracts for the use of email filters. In: Computer and Law. ( CR ) 6/2004, p. 437.
- LG Hamburg: Liability of fax on-demand service providers for spam. Judgment of November 17, 2004, Az. 304 S 82/03 (final), In: Computer und Recht. (CR) 7/2005, p. 496.
Austrian legal situation
- Max W. Mosing, Gerald Otto: Spamming new! In: Media and Law (MR). 4/2003, p. 267ff.
- Max W. Mosing, Gerald Otto: Spam: new odyssey ?! In: Media and Law (MR). 6/2005, p. 359ff.
- Gerald Otto, Martin Parschalk: Spam and virus filters - a necessity in the gray area of the law. In: economic law sheets (wbl). 1/2005, p. 10ff.
Technically
- Thomas Hochstein: FAQ. Read and understand email headers .
- Center for Democracy and Technology: Why am I getting all this spam? ( Memento of October 8, 2006 in the Internet Archive ) (PDF; 311 kB), 2003.
- Tobias Eggendorfer: No Spam! It is better to prevent than cure. Software and Support Verlag, Frankfurt 2005, ISBN 3-935042-71-X .
- Tobias Eggendorfer: private address. Make homepages spam-proof. In: Linux User. 05/2004, Linux New Media, Munich 2004.
- Tobias Eggendorfer: Harvest - no thanks. Trap email address hunters on websites. In: Linux Magazin. 06/2004, Linux New Media, Munich 2004.
- Tobias Eggendorfer: Special filters. Long-term anti-spam appliance. In: Linux Magazin. 09/2004, Linux New Media, Munich 2004.
- Peer Heinlein : Delay tactics. Greylisting protects against worm-generated emails. In: Linux magazine. 09/2004, Linux New Media, Munich 2004
- Daniel Rehbein: Identifying address collectors - an example . Dortmund 2003
- Jo Bager: Against the masses of email. New procedures against spam. In: c't. 15/2004, Heise Verlag, Hannover 2004.
- Moritz Mertinkat: Spam and SPIT - Current protection options and countermeasures . (PDF; 256 kB), 2007
Web links
- Spam - information from the Reporting and Analysis Center for Information Assurance MELANI of the Swiss Federal Administration
- About the origin of the word "spam" (English)
- Spiegel.de: History of the first spam emails
- Antispam Strategies. Detecting and fending off unwanted emails - BSI study 3/2005, accessed on January 13, 2016
- Bad news ( memento from June 30, 2007 in the Internet Archive ) - article by iX (edition 7/2007) - topic: current waves of spam and greylisting as countermeasures
- private side legal position and annotated judgments
- private page Legal classification of unsolicited emails - just law Rechtsanwälte, Groner-Tor-Straße 8, 37073 Göttingen
Individual evidence
- ↑ Spam mail. ( Memento from May 18, 2008 in the Internet Archive ) Institute for German Language.
- ↑ Brad Templeton about the origin of the word spam (English)
- ↑ Spam celebrates its 30th birthday , Heise Newsticker from May 3, 2008.
- ↑ https://www.templetons.com/brad/spamreact.html
- ↑ Information on political education (Issue 291): Risks and opportunities of communication technology. Archived from the original on March 16, 2010 ; accessed on April 16, 2017 .
- ↑ Heise Newsticker from May 22, 2004
- ↑ Netzwelt from February 4, 2005
- ↑ heise ticker of April 15, 2009 on the effects of spam
- ↑ Sydney Morning Herald of 16 April 2009 on spam effect (English)
- ↑ Spam statistics 2010 on SPON
- ^ MessageLabs Intelligence: 2010 Annual Security Report. MessageLabs Intelligence 2010 Spam Statistics (PDF, 5.4 MB)
- ↑ Sophos: 97% of email traffic is spam
- ^ A b RFC 5039 J. Rosenberg, C. Jennings: The Session Initiation Protocol (SIP) and Spam.
- ↑ CAPTCHAs in the field of tension between accessibility and security
- ↑ reCaptcha ( memento of January 2, 2012 in the Internet Archive ) on: google.com
- ↑ https://mailhide.io/
- ↑ Accessibility: How can you fight spam?
- ^ Higher Regional Court Düsseldorf, judgment of May 24, 2006 I-15 U 45/06
- ↑ RFC 4409
- ^ Washington Post: Verizon to Implement Spam Blocking Measures
- ↑ abuse.net
- ↑ SpamCop
- ^ Heise Newsticker, December 25, 2006
- ↑ Consumers against spam: Spam complaint office at the Federation of German Consumer Organizations. ( Memento of October 27, 2005 in the Internet Archive ) September 22, 2005.
- ↑ Principle of unsolicited emails or Skype messages on ebay.de
- ↑ SpamMATTERS ( Memento from July 22, 2008 in the Internet Archive )
- ↑ ACMA ( Memento from July 18, 2008 in the Internet Archive )
- ↑ Sasser condemnation
- ↑ gesetze-im-internet.de
- ↑ TKG 2003 Applicable version of the Telecommunications Act 2003.
- ↑ Tages-Anzeiger, March 2, 2007.
- ↑ 30 Years of Spam ( Memento from December 20, 2008 in the Internet Archive ) Tagesschau from May 3, 2008.
- ↑ Konrad Lischka: 30 years of nerve advertising: The first spammer earned twelve million dollars - with an email. In: Spiegel Online . May 1, 2008, accessed May 6, 2016 .
- ↑ Welt-Online from January 7, 2006
- ↑ zdnet of January 5, 2006
- ↑ Spiegel-Online of May 31, 2007
- ↑ Heise Newsticker from August 5, 2007
- ↑ Spiegel Online of May 13, 2008
- ↑ Mallory Simon: Man allegedly responsible for a third of your spam e-mail to be arraigned. CNN, December 3, 2010, accessed February 21, 2015 .
- ↑ http://www.zdnet.de/news/security/0,39023046,39198981,00.htm Genealogie {Dead Link | url = http: //www.zdnet.de/news/security/0,39023046,39198981 , 00.htm | date = 2018-12 | archivebot = 2018-12-03 18:46:29 InternetArchiveBot}} (link not available)