Denial of Service
Denial of Service ( DoS ; English for "denial of service") describes in information technology the unavailability of an Internet service that should actually be available. The most common reason is the overload of the data network . This can be caused unintentionally or through a concentrated attack on the server or other components of the data network.
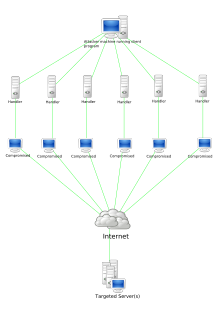
In the case of a willful service blockade caused by a large number of targeted requests, one speaks of a denial-of-service attack and, if the requests are carried out from a large number of computers, of a distributed denial-of-service attack ( DDoS attack , German literally distributed denial of service attack ). Since the requests for a DDoS attack come from a large number of sources, it is not possible to block the attacker without completely cutting off communication with the network.
Intentional server overloads
If an overload is caused willfully, it is usually done with the intention of rendering one or more of the services provided inoperable . While this was originally primarily a form of protest or vandalism, denial-of-service attacks are now being offered for sale by cyber criminals in order to harm competitors. Server operators are also blackmailed into paying money so that their Internet offer can be accessed again.
functionality
DoS attacks such as SYN flooding or the Smurf attack burden the Internet access, the operating system or the services of a host , e.g. HTTP , with a larger number of requests than they can process, whereupon regular requests are not answered or only very slowly. If possible, it is more efficient to exploit program errors to trigger an error function (such as a crash ) in the server software, whereupon it no longer responds to requests. Examples are WinNuke , the land attack , the teardrop attack or the ping of death .
In contrast to other attacks, the attacker usually does not want to break into the computer in a DoS attack and therefore does not need any passwords or the like from the target computer. However, the attack can be part of another attack on a system, for example in the following scenarios:
- To divert attention from the actual attack on a system, another system is paralyzed by a DoS. This is to ensure that the staff entrusted with the administration is distracted from the actual location of the action or that the attack attempts are lost in the increased data volume caused by the DoS.
- If replies from a regular system are delayed, requests to this can be compromised by their own, forged replies . An example of this is the hijacking of foreign domains by delivering fake DNS responses.
Distributed reflected denial of service attack
The Distributed Reflected Denial of Service attack (DRDoS attack) is a special form. In this case, the attacker does not address his data packets directly to the victim, but to regular internet services, but enters the victim's sender address ( IP spoofing ). The answers to these queries then represent the actual DoS attack for the victim. This procedure means that the attacked person can no longer directly determine the origin of the attack. An example of such an attack is the DNS amplification attack , in which the domain name system is misused as a reflector .
Other well-known methods are the Smurf and Fraggle attacks, in which a packet with the IP address of the victim as the sender is sent to the broadcast address of a network. This causes the packet to be multiplied by the number of devices in the network and sent back to the victim.
Email backscatter is used to fill a victim's email inbox using a similar process.
DDoS and botnets
Willful DDoS attacks are often (but not exclusively, see DDoS as a protest action ) carried out with the help of backdoor programs or the like. These backdoor programs are usually installed by Trojans on computers that are not adequately protected and independently try to infect other computers in the network in order to create a botnet . The larger the botnet, the more likely it is that the attack will penetrate even against well-protected systems. The attack is controlled via IRC , HTTP or a peer-to-peer network .
DDoS and the Internet of Things
With the increasing importance of the Internet of Things , devices that appear harmless at first glance are also being misused for DDoS attacks: Internet-enabled TV recorders, set-top boxes, televisions, surveillance cameras or clocks. The devices are often shipped with standard passwords and their firmware is rarely updated, making them attractive targets for automated attacks from the Internet. Once infected, they can be orchestrated like computers in a botnet .
DDoS as a protest action
As a form of protest, DDoS attacks have become increasingly popular. Tools that are easy to use, such as the popular Low Orbit Ion Cannon , now enable non-computer savvy people to disrupt the operation of third-party computers, websites and services with denial-of-service attacks.
Proponents of this form of protest argue that during online demonstrations, the protesters only use their own resources and that their actions are therefore neither violent nor threatened with a sensitive evil. Therefore this political form of the DDoS should be distinguished from the economically motivated form.
In Germany, even attempting to disrupt computer sabotage is a criminal offense, see section Legal situation .
State DDoS
States also used DDoS attacks to paralyze undesirable websites, at least temporarily. The People's Republic of China has created the so-called Great Cannon of China and is attacking websites that offer tools to circumvent the Great Firewall .
Examples
The following are eight known examples of deliberate server overloads.
- August 2008: The website of Georgian President Mikheil Saakashvili is no longer accessible.
- Beginning of July 2009: South Korean and US government websites, shopping portals and intelligence services are temporarily unavailable after attacks. The remote-controlled accesses of up to 30,000 PCs infected with malicious software are said to have been involved in the attack.
- December 6 to 8, 2010: As a reaction to the blocking of WikiLeaks accounts at PostFinance as well as the payment services MasterCard, Visa, PayPal and Amazon, their websites were attacked and - with the exception of the Amazon site - were temporarily brought to their knees.
- May 18, 2012: The website of the city of Frankfurt am Main was attacked by Anonymous as part of the Blockupy protests and was temporarily no longer accessible.
- from September 2012: attacks on American banks
- March 19, 2013: A dispute between the Spamhaus platform and presumably the anonymous host Cyberbunker led to the currently largest known DDoS attack via DNS amplification / reflection, which was reported at short notice due to clever PR by Cloudflare , the Spamhaus website proxy became that he had "noticeably slowed the Internet down". With a DNS server requesting around 300 gigabits per second, this is unlikely , compared to peaks of 2.5 terabits / s in DE-CIX alone , and the Renesys specialist service classifies it as a “local attack”.
- October 21, 2016: The Internet service provider Dyn was the target of a DDoS attack from 7 a.m., starting on the east coast of the USA , which partially disabled the offers of well-known Dyn customers such as Twitter , Netflix , Spotify , Airbnb , Reddit and others. What was new about the attack, which came in waves over the course of the day, was that it apparently relied on an infrastructure of remote controlled devices belonging to the Internet of Things .
- February 28, 2018: The online service GitHub was hit by a new form of DDoS attack, the Memcached Amplification Attack , around noon . In doing so, 1.35 terabits of data were sent to the server per second. After 8 minutes the attack could be ended by intervention of the service provider Akamai .
The content delivery network Akamai noted an increase in attacks from the fourth quarter of 2013 to the first quarter of 2014 by 39%, compared to the same quarter last year it is 47%. Security specialist Imperva reports that a third of all network DDoS events have a volume of more than 10 Gbit / s. "These attacks are becoming more aggressive from year to year and circumvent DDoS protective measures." The purpose of such attacks is usually blackmail, damage to a competitor or infiltration of the target system. There are attacks with 180 Gbit / s that go on for hours and overwhelm even provider networks. Some attackers pose as search engine bots. More than a quarter of the attacking botnets are located in China, India and Iraq.
Conventional overloads
If the sudden increase in inquiries to a website that has so far only been underfrequently frequented leads to its overloading and thus to refusal of service due to the reporting in a medium that attracts the public , this is also called the " slash dot effect " in online jargon by local readers and is sometimes jokingly called a DDoS attack compared. Another well-known example of this in German-speaking countries is the IT news site heise online and the "Heise effect" that occurs there occasionally. In addition, tweets from popular users of the Twitter network and retweets from their followers can lead to server-side failures.
Countermeasures
In order to prevent or limit overloading of critical IT infrastructure, some countermeasures have been developed over time:
- A general protective measure is the choice of secure passwords for routers , networks and networked devices in the Internet of Things .
- It is recommended to deactivate the UPnP function on routers and to block unused services in order to prevent the devices in a local network from being misused.
- In the case of minor overloads caused by only one or a few computers / senders, a service refusal can be carried out with the help of simple blacklists (usually a list of sender addresses). These blacklists are executed by a firewall : It discards data packets from IP addresses from this blacklist (or redirects them). Often a firewall can automatically recognize simple attacks and generate these block lists dynamically, for example, rate limiting of TCP -SYN- and ICMP packets. With rate limiting, however, no distinction is made between wanted and harmful requests.
- The use of SYN cookies reduces the effects of a SYN flooding attack.
- Analysis and filtering measures can be set up both on the affected computer and on the provider's border router . The latter is especially the more effective variant when the Internet access is overloaded.
- In addition, border routers should filter invalid sender addresses according to RFC 2267 in order to prevent DoS attacks that attempt to circumvent the blacklists via IP spoofing .
- If the attacker only knows the IP address of the affected computer, it is also possible to change it (with a PC at home, restarting the router would usually suffice). Takes place, however, a DoS attack on a public DNS - hostname and not the IP address alone, these measures will help only in the short term.
- When choosing the provider, it should be taken into account whether they explicitly offer basic protection against DDoS attacks. The basic protection is a combination of multiple Internet connections in the two- to three-digit Gbit / s range and specialized hardware for data flow analysis and defense against attacks at the application level .
- Another possible - but usually more expensive - countermeasure against overloads is what is known as server load distribution . The services provided are distributed to more than one physical computer with the help of various virtualization techniques .
- Since DNS amplification attacks have already reached attack volumes of more than 200 to 300 Gbit / s in the past, the only permanent option is to use a filter service. These are offered by several commercial providers, who necessarily have to have even stronger connections up to the terabit range. Even the largest attacks can be dealt with safely without disrupting your own data center. The services differ in the quality and size of the attacks that can be intercepted. However, the data protection situation must be observed. Many US providers route the data through the USA or the United Kingdom, which is not permitted with regard to order data processing according to the BDSG .
Legal situation
- In Germany, participation in DoS attacks as computer sabotage is threatened with up to three years imprisonment or a fine if the data input or transmission is intended to harm someone else and thereby data processing, according to Section 303b (1) StGB , which is essential to another is significantly disrupted. According to Section 303b (3) StGB, the attempt is also punishable. In addition, the preparation of a criminal offense according to § 303b Abs. 1 StGB itself is punishable, § 303b Abs. 5 StGB i. V. m. § 202c StGB. This includes in particular the production and distribution of computer programs for DoS attacks. In addition, the injured party can claim compensation. In the relationship between the access provider and the reseller , the Gelnhausen District Court is of the opinion that the contract risk regularly lies with the reseller, so that he is also liable to pay if the line is disrupted by a DDoS attack.
- In Austria, DoS or DDoS attacks can result in criminal offenses under Section 126a StGB (data corruption) and Section 126b StGB (disruption of the functionality of a computer system). The misuse of computer programs according to § 126c StGB is to be seen as a preparatory act for these offenses and is itself a criminal offense.
- In the UK , even downloading the LOIC software used in the attacks faces a two-year prison sentence.
- In Switzerland , DoS as rendering data unusable and data corruption is punishable under Art. 144 bis StGB and can be punished with a fine or a prison sentence of up to three years, in the case of qualification (major damage) with a prison sentence of one year to five years .
frequency
Broad-impact attacks nearly doubled between 2015 and 2016. Unsecure IoT devices in particular pose an increasing risk. In 2016, a Mirai offshoot caused a major disruption in the Deutsche Telekom network. In the same year there were widespread attacks on the websites of the candidates in the US presidential election campaign, as well as an attack on the DNS service provider Dyn, which made Twitter, Netflix and Spotify, among others, inaccessible for a weekend.
The increasing networking of more and more devices poses new challenges for IT security. The "Security by Design" principle, according to which IT security is taken into account from the start in software and hardware development, can help. Installing security updates to close security gaps in good time is also an important component.
See also
literature
- Johannes Öhlböck, Balazs Esztegar: Legal qualification of denial of service attacks. In: Journal for Criminal Law. Vol. 126, No. 4, 2011, ISSN 1813-3517 , pp. 126-133
Web links
- Representation of current global DDoS attacks in the form of a map
- DDoS Survival Handbook
- A list of free German-language documents on the subject
- Detailed description of the denial of service
- Legal qualification of denial of service attacks according to German law , Internet-Strafrecht.com
- DDoS attacks - information from the Reporting and Analysis Center for Information Assurance MELANI of the Swiss federal administration
Individual evidence
- ↑ Shadow economy botnets - a million dollar business for cyber criminals. In: Viruslist.com
- ^ Background report by Brian Krebs: Who Makes the IoT Things Under Attack? In: krebsonsecurity.com . Retrieved October 5, 2016.
- ↑ Achim Sawall: Anonymous demands legalization of DDoS attacks. In: golem.de . January 10, 2013, accessed March 28, 2013.
- ↑ Hack attack on Georgia: Voluntary attacks. In: Spiegel Online , August 14, 2008
- ↑ Hacker attack on South Korea: Austria under suspicion. In: DiePresse.com , July 10, 2009
- ^ "Shame on you, Postfinance" (update). In: 20min.ch. December 7, 2010, accessed December 7, 2010 .
- ↑ "Wikileaks opponents" bombed by hackers (update). (No longer available online.) In: 20min.ch. December 9, 2010, archived from the original on December 11, 2010 ; Retrieved December 9, 2010 . Info: The archive link was inserted automatically and has not yet been checked. Please check the original and archive link according to the instructions and then remove this notice.
- ↑ Anonymous attacks Frankfurt city website. ( Memento of the original from July 24, 2012 in the Internet Archive ) Info: The archive link was inserted automatically and has not yet been checked. Please check the original and archive link according to the instructions and then remove this notice. In: Frankfurter Blog , May 18, 2012
- ^ Bank Hacking Was the Work of Iranians, Officials Say. In: nytimes.com
- ↑ Gigantic DDoS attack: Spam dispute slows down the entire Internet. In: Spiegel Online , March 27, 2013
- ↑ Spamhaus attack does not shake the Internet. In: golem.de , accessed on July 24, 2013.
- ↑ Nicole Perlroth: Hackers Used New Weapons to Disrupt Major Websites Across US In: New York Times , October 21, 2016
- ↑ "1.35 terabits per second: World's largest DDoS attack against Github" Der Standard from March 2, 2018
- ↑ according to Sebastian Schreiber, managing director of the security specialist SySS
- ↑ DDoS attacks are becoming more and more dangerous. In: VDInachrichten No. 20 , Technology & Economy, May 16, 2014, page 14
- ↑ What is the "Slashdot Effect"? Section in the Slashdot FAQ, June 13, 2000
- ↑ The curse of small pixels and inflationary commenting. In: Alles Roger , September 19, 2007
- ↑ The HEISE effect. ( Memento of the original from August 25, 2017 in the Internet Archive ) Info: The archive link was inserted automatically and has not yet been checked. Please check the original and archive link according to the instructions and then remove this notice. In: jurabilis , February 20, 2008
- ↑ Twitter + Retweet = Twitter effect. In: netzwertig.com , February 6, 2009
- ↑ a b The bot in the baby monitor. Federal Office for Information Security , October 24, 2016, accessed on October 27, 2016
- ↑ Gröseling, Höfinger: Computer sabotage and apron criminalization - effects of the 41st StrÄndG to combat computer crime , MMR 2007, 626, 628f.
- ↑ Ernst: Das neue Computerstrafrecht , NJW 2007, 2661, 2665.
- ^ Stree / Hecker, in: Schönke / Schröder , 28th edition 2010, § 303b StGB margin no. 21st
- ^ A b "Illegality" of LOIC-Tool in UK, Germany & Netherlands? In: netzpolitik.org . December 10, 2010, accessed December 10, 2010 .
- ^ AG Gelnhausen, ruling from October 6, 2005 - 51 C 202/05
- ↑ DDoS investigation. In: Heise online . Retrieved February 23, 2017 .