Certified Information Systems Security Professional
The Certified Information Systems Security Professional ( CISSP ) is a certification offered by the International Information Systems Security Certification Consortium, Inc. (also: (ISC) ² ). The certificate is an internationally recognized training standard in the field of information security . According to (ISC) ² on November 16, 2015 there were more than 110,980 CISSP-certified persons worldwide, 1,654 in Germany, 798 in Switzerland and 191 in Austria.
To obtain the certificate, extensive knowledge of safety-relevant aspects from eight areas of the so-called Common Body of Knowledge (CBK) must be proven. The areas span an arc from physical security, software architectures, network and telecommunications as well as cryptography to legal issues (complete list of areas see below). While the legal issues focus strongly on the USA , the other nine areas contain internationally valid security requirements, which explains the global relevance of the certificate.
For Germany and the European area there are specialized certifications like the one from TeleTrusT e. V. developed Teletrust Information Security Professional (TISP) certificate.
Use of a CISSP certificate
The Certified Information Systems Security Professional exam is a knowledge test in the field of information security . The exam was the first certification accredited by ANSI as ISO standard 17024: 2003 in the area of information security and is intended to offer security professionals an objective assessment of their competence. Quality assurance of certification includes a. an obligation to provide evidence of relevant work experience as well as the obligation to continue training in order to maintain the certification. In addition to specialists in information security, the exam is primarily of interest to people who work in the IT environment or in the IT security environment.
Obtaining the CISSP certificate
The certification process consists of several parts. First, you have to take an exam covering eight prescribed areas of knowledge, for which you can prepare yourself through training or self-study . Then the actual certification process is initiated. For this purpose, the professional expertise of the candidates must be confirmed by a third person . All candidates can be randomly selected for an audit and their technical knowledge can be checked in more detail. This is to ensure that the candidate has actually acquired and used the tested knowledge in practice.
Structure of the CISSP exam
The basis of the examination is the Common Body of Knowledge (CBK) , which consists of eight subject areas (domains ).
It is a multiple choice exam. 250 questions from the eight CBK areas have to be answered over six hours. It is about answering questions quickly, the answer of which should be learned through appropriate learning techniques . Logical derivation and freely formulated answers are not required. The exam should cover the broadest possible cross-section of the security spectrum and test the candidates' broad-spectrum knowledge through targeted questions.
The questions are structured according to a very specific scheme . The basic idea of the exam is to only ask so-called closed questions . Each question must therefore be formulated in such a way that, given four possible answer options, exactly one is correct. There are basically only three types of questions: selection (recognition), order (ranking) and approximation (best / worst). These recur again and again and can be easily read from keywords.
Since 2005, the examination can also be taken in German . Since the exam questions very often aim at definitions and descriptions with a very special vocabulary and certain keywords , a purely German exam is not recommended. Nevertheless, German should currently be specified as the examination language. You then receive a bilingual questionnaire and can thus use the advantages of both languages.
While the official questionnaires are not public and therefore cannot be used for exam preparation, there are practice questions in books and on the Internet. The questions to be answered here give a good first impression of the depth and quality of the questions, which are often similar to the official questions. As a result, this quiz occasionally leads to incorrect sample answers. Caution is advised here.
Recertification Requirements
To retain its certification, the CISSP must undertake continuous professional education (CPE) activities to earn 120 CPE points over a three-year period. There is a whole range of different options to choose from. Most CPE points result in teaching activities in safety (4 points per hour, maximum 80), publication of articles or books (maximum 40 points) and self-study , with a maximum of 40 points, or reading safety-related books, with a maximum of 30 points. Further training activities include attending manufacturer training courses (1 point per hour), attending security conferences (1 point per hour) and courses at universities in the field of security (11.5 points per certificate). Commitment in professional politics or in honorary positions is also rewarded: Membership in the board of a professional association in security with a maximum of 20 points and voluntary work for the (ISC) ² at their discretion.
Code of Ethics
Every CISSP has to commit to adhering to certain ethical principles. If a CISSP does not act according to these principles, it can be reported to the (ISC) ² at any time by another CISSP. This can result in a formal audit , which can lead to the revocation of the certificate and exclusion from the (ISC) ².
The code has the following provisions:
- Protect society , the community and the infrastructure .
- Act honorably, honestly, justly, responsibly and in accordance with the law.
- Work conscientiously and competently.
- Promote and protect the profession .
Further development: Concentrations
As a further development option, certified CISSPs have three concentrations to choose from, which represent a specialization and in-depth knowledge in a certain direction.
- Information Systems Security Architecture Professional (ISSAP), further development of security architectures
- Information Systems Security Engineering Professional (ISSEP), further development in the field of secure software development
- Information Systems Security Management Professional (ISSMP), further development in information security management
CBK areas for the CISSP exam
The CBK areas represent a collection of topics from the area of information security . They are subdivided into 10 subject areas.
Access Control - Area 1
In this subject area (domain), the basic mechanics of access control are dealt with.
Security models
Rules and structures that enable a decision about access are called security models . They regulate the relationship between subjects, objects and operations . For the test, the models shown below and their function are queried in particular.

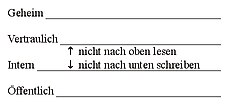
First, a distinction is made between some basic models, some of which have found their way into the advanced models. The goal of the state-oriented machine is a safe system state at all times. To do this, the model works in clearly defined states. The information flow model stands out above all on the information flows taking place between the levels of the multilayer models. As a further basic model, the Goguen-Meseguer model or model of non-interference aims to prevent inferences between the levels.
The Clark-Wilson model aims to ensure integrity and pursues all three integrity goals. Inadmissible modifications by unauthorized users , inadmissible modifications by authorized users and internal and external inconsistencies are equally prevented.
With the multi-layered, condition-based Bell LaPadula model, confidentiality is ensured. The two rules do not read up and do not write down apply to the subjects between the levels . The Biba model , which is also multilayered, pursues the first integrity goal, the impermissible modifications by unauthorized users. The two rules do not write up and do not read down apply to the subjects between the levels .
The Brewer-Nash model or model of the Great Wall of China adapts the access rights of a user dynamically and activity-oriented in order to prevent possible conflicts of interest .
The relationship-oriented Graham-Denning model provides a basic set of instructions for operations between subjects and objects and, like the Harrison-Ruzzo-Ullman model, which specializes in changing the law, creating and deleting subjects and objects, follows a practical approach.
Access control models
Access control models are closely related to security models. Here, too, the focus is on the access of subjects to objects. They serve to implement the rules and goals of a general security policy.
The three main access control models for the CISSP exam are the open, closed, and role-based models.

The open access control models or discretionary access control models (DAC) allow the owner of objects to control the type and scope of access. This is usually done using Access Control Lists (ACLs) in which the rights are assigned according to the need-to-know principle .
Closed access control models or mandatory access control models (MACs), on the other hand, relieve the subject of making decisions about access control . Each object has a security identifier that is used to control access. If a subject does not have the necessary authorization, no access can take place.
The role-based models or role-based access control models (RBACs) make the access decision on the basis of special roles or groups. The subjects are classified in this system at the RBACs and thus receive their rights. The assigned object inherits the rights of the respective role or group.
DAC, MAC and RBAC models can be used together and combined to form a complete system. They are implemented through physical, administrative, logical and data-based access control elements.
Practical access control
The biometric access controls represent an important category . The variants relevant in the CISSP test include the tried and tested methods with fingerprints , retina and iris scanners, but also more specific techniques such as face recognition , hand geometry , typing on keyboards or individual Speaker recognition play a role.
When using token authentication , memory cards and smart cards are examined more closely.
Furthermore, the functionality, advantages and disadvantages of ticket-based access controls such as B. One-time passwords or single sign-on solutions such as Kerberos or the Secure European System for Applications in a Multi-Vendor Environment (SESAME) are requested.
In terms of central access control management techniques, the three technologies RADIUS , TACACS + and Diameter are of particular interest. RADIUS is an authentication protocol for access control for dial-up connections , which is mainly used by Internet service providers . TACACS + offers similar functionalities as RADIUS, but offers a higher level of security due to more extensive encryption. However, RADIUS and TACACS + cannot be used to authenticate any device because the protocols that can be used are limited. The Diameter Protocol provides this additional flexibility .
other topics
In addition to the topics mentioned above in Domain 1, there are many other security topics. The four-eyes principle or separation of duty is introduced as an organizational security measure . This measure is suitable to supplement and tighten other measures.
The secure design of passwords and passports and the secure handling of personal IDs are part of the topic of identification and authentication techniques .
Extensive knowledge about checking the access control measures is requested. This includes knowledge of intrusion detection systems (IDS) as well as the secure and legally safe operation of special traps for attackers: the so-called honeypots .
Under the generic term of penetration tests , knowledge of various types of attack is tested. This includes techniques for exploiting previously unresolved programming errors through zero-day exploits and falsifying websites by exchanging the website address ( DNS spoofing ). In particular, the risks and technical requirements for man-in-the-middle attacks are considered. These are attacks in which the attacker switches unnoticed between the victim and the system that the victim would like to use.
The subject area queried is supplemented by questions about dictionary attacks and the brute force method on passwords . In the event of dictionary attacks, word lists are tried out as passwords using software. The brute force method extends this idea to all possible passwords. For the test, it is important to be able to place these attack methods in the context of security measures.
Attacks that aim to impair the availability of systems are called Denial-of-Service- Attacks (DoS). The CISSP must have knowledge of the different types of DoS attacks. This includes e.g. B. Knowledge of the Smurf attack .
Information Security and Risk Management - Area 5
For the CISSP exam, the basics of the CIA triad are asked. This catchphrase summarizes the terms confidentiality, integrity and availability (German: confidentiality , integrity , availability ). Under integrity is meant to protect from loss and the protection against deliberate change. Another requirement is the traceability of system operations and privacy .
A large part of the exam deals with questions about the management view of information systems . This includes the topics of risk management , security analysis and security management . In contrast to other approaches, the CISSP exam focuses on security in information systems . Depending on the definition of the term , this goes beyond the pure security of information . In the management part, the CISSP exam deals with techniques of change and configuration management .
Models for the classification of information in public administration (including the military ) and the private sector are queried. Personal measures are also important. Job rotation is introduced as part of the CISSP in relation to corruption prevention . Security measures for job descriptions as well as the drafting of confidentiality agreements are part of the scope of the examination. To increase the acceptance of security measures, possibilities of security awareness programs are examined.
The CISSP-CBK requires extensive knowledge of industry standards in the areas of information security and IT security . The most important are the standards of the ISO / IEC 27000 series, ITSEC , Common Criteria , COBIT and TCSEC , which illuminate the topic of security from different angles. A certified CISSP must be able to select the correct standard for specific situations.
Telecommunications and Network Security - Area 10
Physical characteristics
Network layouts
- Star topology
- Bus topology
- Token ring
- Ethernet
- Wireless LAN
- Wide area network
- Local Area Network
- Metropolitan Area Network
Routers and firewalls
Logs
- TCP / IP
- IPsec IP security
- Secure Communication Interoperability Protocol (SCIP)
- Transport Layer Security (TLS)
- Secure Sockets Layer (SSL)
- S / MIME
- Privacy Enhanced Mail (PEM)
- Challenge Handshake Authentication Protocol (CHAP)
- Password Authentication Protocol (PAP)
- Address Resolution Protocol (ARP)
- Simple Network Management Protocol (SNMP)
- Domain Name System (DNS)
- Internet Control Message Protocol (ICMP)
Services
- High-level data link control (HDLC)
- Frame Relay
- SDLC
- Integrated Services Digital Network (ISDN)
- X.25
- CSMA / CD
Security-related techniques
- Virtual Private Network (VPN)
- Network Address Translation (NAT)
- Remote Authentication Dial-In User Service (RADIUS)
- TACACS
- S-RPC
- Packet sniffer
- Cyclic redundancy check (CRC)
- Block check string
other topics
other areas
- Application Security - Area 2
In this domain, software-based security measures, software development and especially the software life cycle are summarized.
- Business Continuity and Disaster Recovery Planning - Area 3
Based on a business impact analysis (BIA), 3 strategies for response and restart measures are queried in Domain 3. This includes in particular measures for business continuity management (BCM) and the disaster recovery plan (DRP).
- Cryptography - Area 4
The Cryptology is divided into two main areas cryptography and cryptanalysis (a literal translation of Cryptography would be an unacceptable restriction thematic). Important concepts such as B. Public-Key-Infrastructures (PKI) and common algorithms as well as their weak points in this domain are treated.
- Legal, Regulations, Compliance and Investigations - Area 6
In Domain 6 in particular, the legal differences to the European area come into play. German law does not play a role in the examination. The differences are particularly significant in the area of the Federal Data Protection Act (BDSG). US law forms the basis. Other countries are only mentioned in passing. They are only queried in the context of cross-border data transmission , but not in detail.
- Operations Security - Area 7
This section mainly deals with topics from the field of IT management . Media management, backup strategies and change management are checked in Domain 7.
- Physical (Environmental) Security - Area 8
Physical security is often not counted as part of information security . Fire protection , site security and security are important issues for the CISSP exam .
- Security Architecture and Design - Area 9
Area 9 deals with Trusted Systems and Trusted Computing . Further topics are system and enterprise architecture .
Web links
- International Information Systems Security Certification Consortium, Inc. also: (ISC) ² , the certification provider; (ISC) ² offers various certifications (including CISSP) and preparatory courses (through partners)
- (ISC) ² Chapter Germany e. V.
References and comments
- ↑ a b With distinction - certificates for security professionals . In <kes> , 3, 2006, p. 27.
- ↑ (ISC) ² Member Counts
- ↑ a b Mike Meyers, Shon Harris: CISSP . 2nd revised edition. Redline Verlag, Heidelberg 2007, ISBN 978-3-8266-1745-4 , p. 22.
- ↑ TeleTrust Germany e. VTISP - TeleTrusT Information Security Professional
- ↑ (ISC) ²: Career Path Brochure 09/2008, p. 12.
- ↑ a b CISSP® - How to Certify
- ↑ a b About the (ISC) ² CBK ®
- ↑ Mike Meyers, Shon Harris: CISSP . 2nd revised edition. Redline Verlag, Heidelberg 2007, ISBN 978-3-8266-1745-4 , p. 26.
- ↑ (ISC) ² Code of Ethics
- ↑ ISC² Concentrations ( Memento of the original from December 11, 2014 in the Internet Archive ) Info: The archive link was automatically inserted and not yet checked. Please check the original and archive link according to the instructions and then remove this notice.
- ↑ Mike Meyers, Shon Harris: CISSP . 2nd revised edition. Redline Verlag, Heidelberg 2007, ISBN 978-3-8266-1745-4 , p. 129 ff.
- ↑ Mike Meyers, Shon Harris: CISSP . 2nd revised edition. Redline Verlag, Heidelberg 2007, ISBN 978-3-8266-1745-4 , p. 139.
- ↑ Mike Meyers, Shon Harris: CISSP . 2nd revised edition. Redline Verlag, Heidelberg 2007, ISBN 978-3-8266-1745-4 , p. 86 ff.
- ↑ Mike Meyers, Shon Harris: CISSP . 2nd revised edition. Redline Verlag, Heidelberg 2007, ISBN 978-3-8266-1745-4 , p. 65 ff.


