Global System for Mobile Communications
The Global System for Mobile Communications (formerly Groupe Spécial Mobile , GSM ) is a mobile radio standard introduced in 1990 for fully digital mobile radio networks , which is mainly used for telephony , but also for circuit-switched and packet-switched data transmission and short messages . It is the first standard of the so-called second generation ("2G") as the successor to the analog systems of the first generation (in Germany: A-Netz , B-Netz and C-Netz ) and is the most widely used mobile communications standard worldwide.
GSM was created with the aim of offering a mobile telephone system that allowed subscribers to be mobile throughout Europe and offered voice services compatible with ISDN or conventional analog telephone networks .
In Germany, GSM is the technical basis of the D and E networks . GSM was introduced here in 1991, which led to the rapid spread of cell phones in the 1990s. The standard is used today in 670 GSM cellular networks in around 200 countries and areas of the world as a cellular standard; this corresponds to a share of around 78 percent of all mobile phone customers. There are later extensions to the standard such as HSCSD , GPRS and EDGE for faster data transmission.
In March 2006, 1.7 billion people worldwide used GSM and one million new customers are added every day - mainly from the growth markets of Africa, India, Latin America and Asia. If you add up all of the mobile communications standards, around 2 billion people worldwide can be reached by mobile phone. This was announced by the GSM Association and the GSA in October 2005. In 2003 (according to the Deutsche Bank ) 277 billion US dollars were turned over with GSM technology.
Emergence of GSM
At the end of the 1950s, the first analog cellular networks in Europe went into operation; in Germany this was the A network . However, they were complicated to operate and they only had a capacity of a few thousand participants. In addition, there were several different systems side by side within Europe, some of which were based on the same standard, but differed in certain details. A similar situation should be avoided with the next generation of digital networks.
| year | event |
|---|---|
| 1982 | At the CEPT (European Conference of Postal and Telecommunications Administrations) the Groupe Spécial Mobile ( working group for mobile communications ) is set up. Your task is to develop a uniform pan-European mobile radio standard. 26 European telecommunications companies are involved. |
| 1985 | Germany, Italy and France sign an initial development contract for the new standard. |
| 1987 | 17 future GSM network operators from 15 European countries form a cooperation and will sign the GSM MoU ( Memorandum of Understanding ) in Copenhagen on September 7th . |
| 1989 | The Groupe Spécial Mobile becomes a Technical Committee at the European Telecommunications Standards Institute (ETSI), which was established by the CEPT in 1988. The project gained additional momentum because network operators, manufacturers and regulators all worked together at ETSI. |
| 1989 | In Germany, the Deutsche Bundespost and Mannesmann receive the license to set up a GSM-based network each (the so-called D networks ). |
| 1990 | The phase 1 specifications of the GSM-900 standard are frozen; That is, they are no longer changed and can be used in the manufacture of cell phones and network technology. |
| 1990 | The adaptation of the specifications to the frequency range at 1800 MHz (DCS 1800) begins. |
| 1991 | The Groupe Spécial Mobile is renamed Standard Mobile Group (SMG). GSM is retained as the name of the standard itself and now stands for Global System for Mobile Communications . |
| 1991 | The specifications for DCS 1800 are frozen. |
| 1991 | The first operational systems will be demonstrated (e.g. at the Telecom 91 trade fair ). |
| 1992 | The first GSM mobile phones hit the market. |
| 1992 | Many European GSM 900 operators are starting the commercial network launch. In summer, the networks D1 (operator: DeTeMobil Deutsche Telekom Mobilfunk ) and D2 (operator: Mannesmann Mobilfunk ) will start operating in Germany. In Switzerland, Natel D is launched on a GSM basis. |
| 2000 | The GSM standardization activities will be transferred to 3GPP . The working group there is called TSG GERAN (Technical Specification Group GSM EDGE Radio Access Network). |
| 2007 | First suggestions for using SIP numbers with GSM |
technology
General
In contrast to the fixed network, there are various additional requirements for a mobile network:
- Subscriber authentication
- Channel access method
- Mobility management ( HLR , VLR , location update , handover , roaming )
- The participants are mobile and can therefore switch from one radio cell to another. If this happens during a call or a data connection, the call connection must be transferred from one base station to the next ( handover ) so that the mobile phone always gets its radio connection to the most suitable base station. In exceptional cases, the call can also be made via a neighboring base station in order to avoid overloading.
- efficient use of resources
- Since a lower data transmission rate is available on the radio interface than in the fixed network, the user data must be compressed more. In order to keep the portion of the data transmission rate that has to be used for signaling processes small, the signaling messages were specified bit-precisely in order to keep them as short as possible.
- Mobile phones only have a limited battery capacity , which should be used sparingly. In general, sending costs more energy than receiving. Therefore, the amount of data sent and status messages should be kept as low as possible in standby mode.
- Use of external networks (roaming)
standardization
The standardization of GSM was started at CEPT , continued by ETSI (European Institute for Telecommunications Standards) and later passed on to 3GPP (3rd Generation Partnership Project). There, GSM is further standardized under the term GERAN (GSM EDGE Radio Access Network). 3GPP is therefore responsible for UMTS and GERAN.
Range
The ranges that can be achieved with GSM fluctuate greatly, depending on the terrain profile and development. In the open air, up to 35 km can be reached with visual contact. At greater distances, the propagation delay of the radio signals prevents communication between the base and mobile stations. However, with the help of special tricks it is possible to increase the cell size, sometimes at the expense of capacity. This is used in coastal regions. In cities, the range is often only a few hundred meters due to attenuation from buildings and the lower antenna height, but there the base stations are also closer together for reasons of capacity.
In principle, however, the GSM 900 can achieve greater ranges than the DCS 1800 due to the lower radio field attenuation and the higher output power of the end devices.
The cell size is determined according to the range. The forecast usage is also taken into account in order to avoid overloads.
Physical transmission via the radio interface
The digital data is transmitted with a mixture of frequency and time division multiplexing , with the sending and receiving directions being separated by frequency division multiplexing and the data by time division multiplexing . The GSM frequency band is divided into several channels that are 200 kHz apart. With GSM 900, 124 channels are provided for the uplink direction (uplink) to the base station in the range from 890-915 MHz and 124 channels for the downlink direction (downlink) in the range from 935-960 MHz . The TDMA frame duration is exactly 120/26 ms (approx. 4.615 ms) and corresponds to the duration of exactly 1250 symbols. Each of the eight time slots per frame thus lasts approximately 0.577 ms, corresponding to the duration of 156.25 symbols. Bursts of various types can be sent and received in these time slots . The duration of a normal burst is approx. 0.546 ms in which 148 symbols are transmitted.
Since the mobile station only transmits in one time slot of the frame, the result is a pulse rate of 217 Hz.
The modulation method is Gaussian Minimum Shift Keying ( GMSK , German: Gaussian minimum phase position modulation ), a digital phase modulation in which the amplitude remains constant. 8- PSK was then introduced with EDGE . While only 1 bit is transmitted per symbol with GMSK, this is 3 bit with 8-PSK, but a better signal-to-noise ratio is required for the radio connection.
Since, at a distance of several kilometers, the radio signal can be delayed by the limited propagation speed (the so-called group speed ) so that the burst of the mobile phone no longer arrives at the base station within the specified time slot , the base station determines the signal propagation time and requests the mobile phone to Send burst a little earlier. To do this, it informs the mobile device of the Timing Advance (TA) parameter, which specifies the transmission advance in 3.7 μs steps. This corresponds to the duration of one bit, with the bit rate being 270.833 kbits / s (see below). The timing advance has a range of values from 0 to 63. At a given group speed, the duration of a bit corresponds to a distance of approx. 1.106 km, and since the forward and reverse directions must be considered together for the running time, a change in the timing advance by one corresponds to one Change in distance of just over 553 m. This results in a maximum range of approx. 35.4 km, which can, however, be extended with technical tricks.
After the reception burst, the mobile phone switches to the transmission frequency offset by 45 MHz and sends the burst of the return channel to the base station . Since the downlink and uplink are offset by three time slots , one antenna is sufficient for both directions. To increase the immunity to interference, the frequency pair can also be changed periodically (frequency hopping), resulting in a frequency hopping rate of 217 hops per second.
With a gross data transmission rate of approx. 270.833 kbit / s per channel (156.25 bits in each burst of 15/26 ms), 33.85 kbit / s are left per time slot. 9.2 kbit / s of this data rate are reserved for the synchronization of the frame structure, so that 24.7 kbit / s net remain for the useful channel. Due to the radio transmission, there are still many bit errors in this bit stream .
The data rate per time slot of 24.7 kbit / s is divided into 22.8 kbit / s for the coded and encrypted user data of the traffic channel and 1.9 kbit / s for the subscriber-specific control channels ( control channel ). The channel coding contains a number of error protection mechanisms, so that 13 kbit / s remain for the actual user data (in the case of voice data). An alternative channel coding introduced later allows the error protection to be reduced in favor of the application data, since in data transmission protocols, in contrast to voice transmission, a new request for the data block is possible in the event of bit errors.
Transmission power
The transmission power of the mobile station with GSM 900 is max. 2 watts and 1 watt for GSM 1800. The transmission power of the base stations for GSM 900/1800 is 20–50 / 10–20 watts. The transmission powers of mobile and base stations are reduced to the necessary minimum after the connection has been established. The base station transmits, depending on requirements, in the individual time slots of a frame with different power. It only transmits in active time slots. The power regulation takes place every seconds. In addition, the cell phone can interrupt the radiation when there is no talk. The technical reason for both measures is to lower power consumption and reduce radio interference in neighboring cells of the same frequency.
Network architecture
hardware
GSM networks are divided into five subsystems (see picture from left to right):
- Mobile phone or Mobile Station (MS) (left in the picture, unmarked)
- The MS consists of an antenna to which a transmitting and receiving unit is connected, power supply, loudspeaker and microphone (or external connections) and a possibility to select another participant (typically keyboard or voice input). The mobile station usually also has a display to show the caller's telephone number and short messages (SMS). Another essential part of the MS is the SIM card .
- Mobile radio transmission system or Base Station Subsystem (BSS)
- The BSS consists of at least one base station (BTS, Base Transceiver Station ), but usually several (usually a few 10 to a few 100). Each base station serves one or more (often three) radio cells via the antennas connected to it . The base stations are connected to a central control unit (BSC, Base Station Controller ) which monitors the radio connections and initiates cell changes ( handover ) if necessary . A conversion unit (TRAU, Transcoder and Rate Adaptation Unit ) is connected to each BSC . This is required because a compressing audio codec is used for telephone calls within the cellular network. The TRAU converts between GSM-compressed voice channels and uncompressed ISDN audio channels at 64kbit / s.
- Switching subsystem or Network Switching Subsystem (NSS) or Core Network Subsystem (CSS)
- The NSS consists of the MSC ( Mobile Services Switching Center ), which is the actual switching center and the interface between the radio network and the telephone network. The NSS also includes the VLR ( Visitor Location Register ), which stores information about all mobile subscribers who are within the radio network. The HLR ( Home Location Register ), on the other hand, stores information about all participants who are customers of the radio network owner. The AUC ( Authentication Center ) is responsible for the authentication , the (optional) EIR ( Equipment Identity Register ) stores information about the serial numbers of the mobile stations used.
- GPRS Core Network
- The SGSN ( Serving GPRS Support Node ) and GGSN ( Gateway GPRS Support Node ) are available for the packet-switched part GPRS .
- Operation and Maintenance Center (OMC) or Network Management Center (NMC) (not shown)
- The OMC monitors the cellular network and controls the MSC, BSC and BTS.
The blue letters in the picture indicate the data transmission paths between the components.
addressing
The following numbers are used to address subscribers in a GSM network: The MSISDN ( Mobile Subscriber ISDN Number ) is the actual telephone number at which a subscriber can be reached worldwide. The IMSI ( International Mobile Subscriber Identity ) is accordingly the internal subscriber identification that is stored on the SIM and is used to identify a subscriber within a radio network. For reasons of data protection, the IMSI is only sent over the radio network during the initial authentication of the mobile station; a temporarily valid TMSI ( Temporary Mobile Subscriber Identity ) is used instead in further authentications . The MSRN ( Mobile Station Roaming Number ) is used for roaming, i.e. routing calls within the cellular network .
Some important functions within cellular networks
Handover
- Inter-cell handover
One of the most important basic functions in cellular mobile radio networks is the cell change initiated by the network during an ongoing call. This can be necessary for various reasons. The decisive factor is u. a. the quality of the radio connection, but also the traffic load of the cell. For example, a call can be transferred to a more distant cell to avoid overloading.
- Intra-cell handover
Here, for example, based on the channel quality of the MS, a new channel is assigned within a cell.
Mobility Management
Several procedures in the GSM network deal with the mobility of the participants in the network. So that a mobile subscriber who is anywhere in the network area can be called or a short message can be sent, the requirement must always exist that the subscriber can receive a search query (called paging). For this purpose, his current whereabouts must be constantly updated with a certain granularity.
To reduce the workload in the core network and to extend the battery life, only the location area in which a registered mobile phone is located is recorded centrally . It is not known where it is within this area. To save energy and transmission capacity, the mobile phone reports to the network in standby mode (idle mode) at intervals specified by the network (between 6 minutes and 25.5 hours) or when changing the location area. As soon as the network wants to establish a connection with the mobile phone, this is called via all base stations in the location area and, when there is a message, the connection is established via the base station to which the terminal device reports.
The mobile phone, on the other hand, knows exactly which radio cell it is in. In standby mode, it scans the neighboring cells, the carrier frequencies of which it receives from the base station on special information channels. If the signal from one of the neighboring cells is better than that of the current cell, the mobile phone will switch to it. If it notices a change in the location area, it must inform the network of its new location.
The VLR (Visitor Location Register) and the HLR (Home Location Register) are very important for mobility management . The two are actually to be understood as databases. Each MS is registered exactly once in an HLR. All participant data is stored there. The VLR in whose area an MS last reported is always entered in the HLR. All MS in the catchment area of an MSC are entered in the VLR.
Roaming
Since many mobile network operators from different countries have roaming agreements in place, it is possible to use the mobile phone in other countries and to continue to be available and to make calls under your own number.
Security functions
This section lists the security features. Deficits in these functions are listed in the section Security Deficits .
Authentication
Each subscriber is assigned a 128-bit long Subscriber Authentication Key K i when they join the network of a mobile radio operator . The key is stored on the subscriber's side in the SIM card , on the network side either in the HLR or in the AuC . For authentication, the MS is sent a 128-bit long random number RAND from the network. From this random number and K i is the A3 algorithm of the authentication keys SRES '( S igned Res 32 bits ponse,) calculated. This calculation takes place in the SIM card. The authentication key SRES is calculated separately from the network in the AuC and from the MS and the result is compared by the VLR . If the SRES and SRES 'match, the MS is authenticated.
The A3 algorithm is an elementary component of security in the GSM network. It can be selected by each network operator, details of the respective implementation are kept secret.
User data encryption
For encryption, a 64-bit long code key (English: ciphering key ) K c is determined from the random number RAND required for authentication and the user key K i using the algorithm A8 . This code key is used by the A5 algorithm for the symmetrical encryption of the transmitted data.
Given the short key length, it can be assumed that the encryption does not offer any noteworthy security against serious attacks. In addition, several attacks in 2009 and 2010 on the A5 / 1 algorithm used showed that it is in principle insecure. However, the encryption prevents simple eavesdropping, as is possible with analog police radio.
The encryption with the insecure A5 / 1 algorithm is normally switched on in Germany. In countries such as B. India, the cell phone network must not be encrypted. In principle, the GSM standard provides that mobile phones display a warning in the event of unencrypted connections.
Anonymization
In order to guarantee a certain anonymity , the unique subscriber identifier IMSI , via which a subscriber can be uniquely identified worldwide, is hidden on the air interface. Instead, the VLR generates a temporary TMSI that is reassigned with each location update and is only transmitted in encrypted form.
User authentication
The user must authenticate himself to the SIM card (and thus to the cellular network) as an authorized user. This is done using a PIN . It is specified on the SIM card whether the PIN query can be deactivated. If the PIN is entered incorrectly three times in a row, the SIM card is automatically blocked. The PUK (Personal Unblocking Key) is required to unblock it . The PUK can be entered incorrectly ten times in a row before the SIM card is finally blocked. The cellular network does not have to authenticate itself to the user.
Services for the user
On the landline side, the GSM standard is based on the ISDN standard and therefore provides similar switching- related performance features . With the ability to send and receive short messages (SMS, short for Short Message Service ), a new service was created that has been enthusiastically received and has now become an important source of income for network operators.
Voice transmission
Several codecs have been standardized over the years for voice transmission with GSM. The usual speech codecs , which typically get by with a data rate of less than 20 kbit / s, carry out a feature extraction adapted to human speech, so that they can only be used for the transmission of speech. They can therefore only transmit music or other noises with lower quality. The speech codecs used in the GSM network are briefly summarized below:
Full Rate Codec (FR)
The first GSM speech codec was the full rate codec (FR). Only a net data rate of 13 kbit / s is available for it (in contrast to G.711 64 kbit / s with ISDN ). The audio signals must therefore be highly compressed, but still achieve an acceptable voice quality. The FR codec uses a mixture of long-term and short-term prediction, which enables effective compression (RPE / LTP-LPC speech compression: Linear Predictive Coding , Long Term Prediction , Regular Pulse Excitation ).
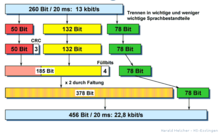
Technically, 20 ms of speech is sampled and buffered, then subjected to the speech codec (13 kbit / s). For forward error correction (Forward Error Correction, FEC), the 260 bits are divided into three classes of such a block, accordingly, as would be greatly affect a bit error in the speech signal. 50 bits of the block are divided into class Ia. They must be protected most and receive a CRC checksum of 3 bits for error detection and error concealment (error concealment) . Together with 132 bits of class Ib, which need a little less protection, they are subjected to a convolutional code that generates 378 output bits from the 185 input bits . The remaining 78 bits are transmitted unprotected. 260 bits of user data are converted into 456 bits of error-protected data, which increases the required bit rate to 22.8 kbit / s.
The 456 bits are divided into eight half bursts of 57 bits each by interleaving . After deinterleaving in the receiver, short-term disturbances (e.g. one burst long) only have a minor effect due to the error spreading. By combining the different error protection methods in GSM, a good voice quality is often achieved even though the radio channel is extremely error-prone.
Half Rate Codec (HR)
With the introduction of the half-rate codec, it became possible to handle not just one but two calls simultaneously on a time slot of the air interface. As the name suggests, only half the data rate is available for HR as for the FR codec. In order to still achieve usable speech quality, vector quantization is used instead of the scalar quantization used in the FR codec . As a result, approximately three to four times the computing power is required for the coding as with the FR codec. Because the voice quality is still rather mediocre, HR is only used by the mobile network operators when a radio cell is overloaded.
Enhanced Full Rate Codec (EFR)
EFR works with a similar data rate as the full rate codec, namely 12.2 kbit / s. A more powerful algorithm ( CELP ), compared to the full-rate codec, achieved better voice quality, which with a good radio channel corresponds approximately to the level of ISDN telephone calls (G.711a).
Adaptive Multirate Codec (AMR)
AMR is a parameterizable codec with different data rates between 4.75 and 12.2 kbit / s. In the 12.2 kbit / s setting, it largely corresponds to the GSM EFR codec in terms of algorithm and audio quality. The lower the data rate of the voice data, the more bits are available for channel coding and thus for error correction. The 4.75 kbit / s codec is therefore described as the most robust, because an intelligible conversation is still possible despite the high bit error rate during radio transmission. During a call, the mobile network measures the frequency of bit errors and selects the most suitable codec from a list, the Active Codec Set (ACS). The code rate used is thus continuously adapted to the channel quality.
Adaptive multirate codec or wide band (AMR-WB)
This codec is an extension and optimization of the already available AMR codec set. As the “WB” (wide band) suggests, the transmittable frequency range is increased from currently approx. 3.4 kHz to approx. 6.4 kHz or 7 kHz without using more radio resources. The development of this codec was completed some time ago and it was standardized by the ITU (G.722.2) and 3GPP (TS 26.171). Due to the larger bandwidth, the codec should be able to transmit speech and ambient noises better together, which enables better speech quality in a noisy environment. Ericsson has the T-Mobile - UMTS performed -Netz in Germany in summer 2006 with selected customers in the cities of Cologne and Hamburg an AMR-WB-operation test. At the end of 2008, all Ericsson BSCs in the telecommunications network were prepared for AMR-WB. Since the end of 2011, all Telekom end customers have been able to use AMR-WB. AMR-WB is marketed as HD-Voice in Germany .
Data transfer
If a GSM channel is used for data transmission, a usable data rate of 9.6 kbit / s is obtained after the decoding steps. This type of transmission is called Circuit Switched Data (CSD). An advanced channel coding also enables 14.4 kbit / s, but causes many block errors in poor radio conditions, so that the "download rate" can actually be lower than with increased security on the radio path. Therefore, depending on the bit error rate between 9.6 and 14.4 kbit / s, network-controlled switching (= Automatic Link Adaptation, ALA).
However, both are not enough for many Internet and multimedia applications , so that extensions have been created under the name HSCSD and GPRS , which enable a higher data rate by allowing more bursts per time unit to be used for transmission. HSCSD uses a fixed assignment of several channel slots, GPRS uses radio slots dynamically for the connected logical connections (better for Internet access ). A further development of GPRS is E-GPRS. This is the use of EDGE for packet data transfer.
Location
The position of a cell phone is known to the cell phone operator due to the permanent registration on the network within certain accuracy limits. In standby mode it is given at least by the assignment to the currently used location area. This information is updated regularly when the mobile station moves.
Depending on the application, GSM positioning represents an alternative to GPS and is used for various services, including location-based services , route planners, fleet management for transport companies or help in locating a mobile phone.
The use for emergency services enables accident victims to be found quickly. GSM tracking is also used in law enforcement as a tool for the police.
Extensions and further developments of GSM
GSM was originally designed primarily for telephone calls, faxes and data transmission with a constant data rate. Burst-like data transmissions with strongly fluctuating data rates, as is common on the Internet , were not planned.
With the success of the Internet, the so-called "evolution of GSM" began, in which the GSM network was expanded to be completely downward-compatible with options for packet-oriented data transmission. In addition, the replacement of frequently used components should result in minimal costs.
CSD
Speeds of up to 14.4 kBit / s are achieved with circuit switched data .
HSCSD
By coupling several channels, HSCSD achieves a higher data rate overall, a maximum of 115.2 kbit / s. In order to be able to use HSCSD, you need a compatible mobile phone, on the part of the network operator, hardware and software changes are required for components within the base stations and the core network. In Germany only Vodafone and E-Plus support HSCSD.
GPRS
For the first time, GPRS allowed packet-switched data transmission. The actual data throughput depends, among other things, on the network load and is a maximum of 171.2 kbit / s. When the load is low, a user can use several timeslots in parallel, while when the network load is high, each GPRS timeslot can also be used by several users. GPRS requires additional components (the GPRS packet core) from the network operator within the core network.
EDGE
With EDGE , a new modulation (8PSK) made it possible to increase the data rate. It is a maximum of 384 kbit / s. EDGE extends GPRS to E-GPRS (Enhanced GPRS) and HSCSD to ECSD (Enhanced Circuit Switched Data).
Streaming
Streaming services require a minimum guaranteed data rate. This is not originally intended in GPRS. In the meantime (i.e. from 3GPP release 99) the prerequisites for enabling real streaming via GPRS have been created through the introduction of corresponding quality-of-service parameters and a few other properties.
Generic Access
Since mid-2004 the standardization committees have been working on a method that will allow mobile devices to use GSM services via any other (IP) transmission system instead of via the GSM air interface. For this purpose, the transmitting stations of WLAN, Bluetooth etc. should be connected to the GSM core network via so-called Generic Access Controllers. The GSM user data and the signaling data are then tunneled through the IP network.
Cell broadcast
Cell broadcast or cell broadcasting (CB for short) is a mobile radio service for the network-side sending of short messages to all MS registered in a specific base station.
BOS-GSM
BOS-GSM (depending on the provider also BOS @ GSM, GSM-BOS) is a technology for digital radio communication of users with special security requirements such as authorities and organizations with security tasks (BOS: police , fire brigade , rescue services ).
Trivia
In French, the abbreviation “GSM” is often used for the German word “mobile phone”, especially in Belgium. In the Bulgarian language, too, which has borrowed many words from French for over 200 years, “GSM” is used synonymously for “mobile phone”.
Security deficits
GSM has some deficits in terms of security. These include:
- Only symmetric cryptography is used. One possible solution would be to use hybrid encryption .
- The crypto algorithms are not publicly accessible and verifiable.
- No mutual authentication of the mobile phone subscriber and the network operator's base station.
- GSM does not provide sufficient protection against the location of the mobile radio subscribers by outside attackers.
- No protection against an attacker from the cellular network (location and message content).
- No end-to-end services possible (authentication between participants, encryption of the language).
Man-in-the-middle
The GSM protocol is not protected against man-in-the-middle attacks (MITM). An example of a possible use is an IMSI catcher . The device forces the encryption to be deactivated.
In 2003 Elad Barkan, Eli Biham and Nathan Keller presented an alternative man-in-the-middle attack against GSM, which makes it possible to bypass the A5 / 3 encryption algorithm. This attack is an attack against the GSM protocol and not an attack against the KASUMI cipher itself. A longer version of the paper was published in 2006. The attacker positions himself with his own base station between the mobile subscriber and the correct base station (operator network). The RAND challenge is passed on to the mobile participant. However, the attacker cached the SRES response. The attacker now requests the mobile phone to start A5 / 2 encryption. After the encryption has been carried out, the attacker breaks the ciphertext within a second and extracts the key K c . The attacker then sends the cached SRES to the operator network. The attacker is authenticated to the network. The network now requests the attacker to use A5 / 1 or A5 / 3 encryption. The attacker uses the previously extracted K c and encrypted communication is established. The attacker can then listen in on conversations, decode them in real time or save them temporarily. Redirecting and taking over calls, changing SMS and making calls at the expense of others is also possible.
Denial of Service
As part of the USENIX Security Symposium 2013 it was shown that with the help of a speed-optimized OsmocomBB firmware - installed on a few devices - a GSM network can be brought to denial of service by the prepared cell phones answering all paging requests (with around 65 Responses per second) before the authorized recipient can react. GSM then refrains from further inquiries, authentication only follows in the next step. Half of all networks (global) check the legitimation of the end device in less than one out of ten cases.
Encryption algorithms
The algorithms A5 / 1 and A5 / 2 can be broken in real time. The A5 / 3 algorithm with a 64-bit key is based on the KASUMI cipher. The KASUMI cipher has been theoretically broken since 2010. A successful practical attack against A5 / 3 is not known. The A5 / 4 algorithm with a 128-bit key is considered secure.
Countermeasures
The security researcher Karsten Nohl calls for the use of SIM cards with an additional verification function at short notice . A small Java program on the card could verify the network operator against the mobile phone subscriber. This would replace the current unilateral authentication with a mutual authentication. This approach prevents MITM attacks and also helps against DoS paging attacks. In addition, network operators and mobile devices must use the A5 / 3 encryption algorithm and avoid combinations with A5 / 1 or A5 / 2.
In the long term , the expert calls for the use of A5 / 4 and USIM cards .
In the Web Links section , the GSM Security Map provides a visual overview of GSM security in different countries.
Example: eavesdropping on Angela Merkel's party cell phone
In October 2013, several media outlets reported the wiretapping of Angela Merkel's party cell phone by the US National Security Agency (NSA). According to FAZ, Merkel had a mobile phone contract with Vodafone at the time . It was suspected that the provider's GSM-based radio network was being tapped by the NSA.
Frequencies used
GSM works with different frequencies for the uplink (from the mobile phone to the network, lower band ) and the downlink (from the network to the mobile phone, upper band ). The following frequency bands can be used by the wireless service provider:
| Band name | Area | Uplink (MHz) | Downlink (MHz) | ARFCN | continent | Remarks |
|---|---|---|---|---|---|---|
| T-GSM 380 | GSM 400 | 380.2-389.8 | 390.2-399.8 | dynamic | ||
| T-GSM 410 | GSM 400 | 410.2-419.8 | 420.2-429.8 | dynamic | ||
| GSM 450 | GSM 400 | 450.4-457.6 | 460.4-467.6 | 259-293 | ||
| GSM 480 | GSM 400 | 478.8-486.0 | 488.8-496.0 | 306-340 | ||
| GSM 710 | GSM 700 | 698.0-716.0 | 728.0 - 746.0 | dynamic | ||
| GSM 750 | GSM 700 | 747.0 - 762.0 | 777.0-792.0 | 438-511 | ||
| T-GSM 810 | 806.0-821.0 | 851.0-866.0 | dynamic | |||
| GSM 850 | GSM 850 | 824.0-849.0 | 869.0-894.0 | 128-251 | America | |
| P-GSM | GSM 900 | 890.0-915.0 | 935.0-960.0 | 1 - 124 | Africa , America , Asia , Australia , Oceania , Europe | |
| E-GSM | GSM 900 | 880.0-915.0 | 925.0-960.0 | 0-124, 975-1023 | Africa , America , Asia , Australia , Oceania , Europe | |
| R-GSM | GSM 900 | 876.0-915.0 | 921.0-960.0 | 0-124, 955-1023 | Africa , Asia , Europe | |
| T-GSM 900 | GSM 900 | 870.4 - 876.0 | 915.4-921.0 | dynamic | ||
| DCS 1800 | GSM 1800 | 1710.0-1785.0 | 1805.0-1880.0 | 512-885 | Africa , America , Asia , Australia , Oceania , Europe | |
| PCS 1900 | GSM 1900 | 1850.0-1910.0 | 1930.0 - 1990.0 | 512-810 | America |
- Frequency bands 2 and 5 (blue background color) are used commercially in America.
- Frequency bands 3 and 8 (yellow background color) are used commercially in Europe, Africa, Asia, Australia, Oceania and partly in America.
- All other frequency bands are not used commercially in public cellular networks.
- There is no public GSM cellular network in South Korea and Japan .
- A mobile phone that supports the GSM and UMTS FDD frequency bands 5 (850 MHz), 8 (900 MHz), 2 (1900 MHz) and 1 (2100 MHz) is suitable for worldwide use .
For cost reasons, new cellular networks (e.g. Australia / Telstra ) or cellular network expansions (e.g. Switzerland / Swisscom ) were only built with the newer UMTS cellular technology . New mobile radio stations are increasingly sending out only one UMTS and LTE signal.
Situation in Germany
Until 2017
In Germany , until 2005, GSM mobile communications only took place in the P-GSM and DCS-1800 range. At the end of 2005, the Federal Network Agency opened the entire E-GSM frequency range for GSM mobile communications.
As a result, E-Plus and O2 began to move partly into the E-GSM area from April 2006 (E-Plus: 880.2 - 885.0 MHz / 925.2 - 930.0 MHz and O2: 885.2 - 890 , 0 MHz / 930.2 - 935.0 MHz). From now on, the two providers will use these areas to expand their networks in sparsely populated regions. Thus, all four German mobile phone providers have spectra in both areas.
Some of the old assignments in the DCS-1800 area had to be surrendered in January 2007 as compensation. They were re-awarded at the frequency auction in 2010:
- 1710.0 - 1715.0 MHz / 1805.0 - 1810.0 MHz for € 20.7 million to Telekom (previously used by the Bundeswehr)
- 1715.0 - 1720.0 MHz / 1810.0 - 1815.0 MHz for € 20.7 million to Telekom (previously used by the Bundeswehr)
- 1720.0 - 1725.0 MHz / 1815.0 - 1820.0 MHz for € 19.87 million to Telekom (previously used by the Bundeswehr)
- 1730.1 - 1735.1 MHz / 1825.1 - 1830.1 MHz for € 21.55 million to E-Plus (until January 2007 O2)
- 1758.1 - 1763.1 MHz / 1853.1 - 1858.1 MHz for € 21.54 million to E-Plus (until January 2007 E-Plus)
The current GSM licenses will expire in 2016 [out of date] and will then probably be auctioned again by the Federal Network Agency.
The channels (ARFCN) of the individual bands are distributed among the five German operators as follows:
| Users | GSM 900 ARFCN |
DCS 1800 ARFCN |
Number of channels GSM 900 / DCS 1800 |
|---|---|---|---|
| D1 / Telecom | 13 - 49, 81 - 102, 122 - 124 | 587-611 | 62/25 |
| D2 / Vodafone | 1 - 12, 50 - 80, 103 - 121 | 725-751 | 62/27 |
| E1 / E-Plus | 975-999 | 777-863 | 25/87 |
| E2 / O2 | 1000-1023, 0 | 637-723 | 25/87 |
| Deutsche Bahn | 955-973 | 19 / - |
The upper end of the GSM1800 range (from ARFCN 864) was kept free until the 2015 frequency auction in order to avoid disruptive effects on DECT cordless telephones (so-called DECT protective band 1875.5 - 1880.0 MHz). In addition, this area was awarded to companies and private individuals by the Federal Network Agency until the end of 2015 for temporary and permanent test and trial systems.
R-GSM, E-GSM (GSM 900), E-UTRA band 8


The DB runs along the railway lines a non-public GSM-R -Mobilfunknetz.
DCS 1800 (GSM 1800) E-UTRA Volume 3


Sch = safety distance to the neighboring DECT band
End of June 2013 had given the Federal Network Agency announced that the 31 December 2016 [dated] are running rights to use mobile phone frequencies again in an auction will be auctioned. In addition to the frequencies in the 900 MHz and 1800 MHz range, frequency blocks in the 700 MHz and 1.5 GHz range are also to be awarded during the auction. The four previous mobile network operators are each to be allocated a frequency block in the 900 MHz range outside of the auction in order to ensure basic coverage.
Current situation (since 2017)
The valid from January 1, 2017 Federal Network Agency - Concessions allow the use of mobile radio frequencies by the German mobile operator as shown below. The frequency band assigned by the Federal Network Agency can be used by the mobile operator in Germany for GSM, UMTS or LTE . It is common to use the assigned frequency band for different technologies (for example: E-UTRA band 8: GSM and UMTS).
R-GSM, E-GSM (GSM 900), E-UTRA band 8


The DB runs along the railway lines a non-public GSM-R -Mobilfunknetz. The information for E-UTRA Volume 8 corresponds to the allocation from 2017!
DCS 1800 (GSM 1800) E-UTRA Volume 3


The channels (ARFCN) of the individual bands are distributed among the four German operators as follows:
| Users | GSM 900 ARFCN |
DCS 1800 ARFCN |
Number of channels GSM 900 / DCS 1800 |
|---|---|---|---|
| D1 / Telecom | 50 - 124 50 - 99 (where 5 MHz LTE carrier is available) |
- (used exclusively for LTE ) | 75 / - 50 / - (where 5 MHz LTE carrier is available) |
| D2 / Vodafone | 0 - 49 | 862 - 885 (not fully used due to adjacent DECT band) | 50/24 |
| E2 / O2 | 975-1023 | 661 - 760 661 - 735 (where 5 MHz LTE carriers are available) |
49/100 49/75 (where 5 MHz LTE -carrier available) |
| Deutsche Bahn | 955-973 | - | 19 / - |
Situation in Austria
Valid until the end of 2034 RTR - concessions allow the use of mobile radio frequencies by the Austrian mobile operator as shown below. The frequency band assigned by the RTR can be used by the mobile operator in Austria for GSM, UMTS or LTE . It is common to use the assigned frequency band for different technologies (for example: E-UTRA band 8: GSM and UMTS).
R-GSM, E-GSM (GSM 900), E-UTRA band 8


The ÖBB operates a non-public GSM-R mobile network along the railway lines. The information for E-UTRA Volume 8 corresponds to the allocation from 2018! By January 1, 2018, the mobile radio frequencies on E-UTRA band 8 will be reallocated in several steps (refarming).
DCS 1800 (GSM 1800) E-UTRA Volume 3


The information for E-UTRA Volume 3 corresponds to the allocation from 2020! By January 1, 2020, the mobile radio frequencies on E-UTRA Band 3 will be reallocated in several steps (refarming).
Situation in Switzerland
See mobile radio frequencies in Switzerland .
All public Swiss mobile network providers have announced the shutdown of their GSM mobile network:
Even today, the use of a cell phone that is only compatible with 2G / GSM can lead to cell phone reception problems.
GSM shutdown
It is expected that GSM will be replaced by successor standards in the long term. While the shutdown was already decided in 2017 in Australia and Singapore, z. For example, no shutdown date has yet been set for Germany and Austria, but in Switzerland there will probably no longer be a public GSM mobile network available from 2021.
Sunrise Switzerland plans to dismantle the 2G network and install 5G antennas. According to Huawei, this emulates 2G. This has the advantage that all "old" 2G telephones continue to work in Switzerland. There are still many applications that need 2G: traffic light controls, fire alarms, switches in the railway network, old built-in car telephones, etc.
See also
literature
- Siegmund M. Redl, Matthias K. Weber, Malcolm W. Oliphant: An Introduction to GSM , Artech House, March 1995, ISBN 978-0-89006-785-7
- Siegmund M. Redl, Matthias K. Weber, Malcolm W. Oliphant: GSM and Personal Communications Handbook , Artech House, May 1998, ISBN 978-0-89006-957-8
- Jon Agar: constant touch, a global history of the mobile phone. Icon Books, Cambridge 2003, ISBN 1-84046-541-7 .
- Jörg Eberspächer: GSM, Global System for Mobile Communication: switching, services and protocols in digital cellular networks . Teubner, Stuttgart 2001, ISBN 3-519-26192-8
- Hannes Federrath: Security of mobile communication: protection in GSM networks, mobility management and multi-sided security , Vieweg, 1999, ISBN 3-528-05695-9
- Michel Mouly, Marie-Bernadette Pautet: The GSM System for Mobile Communications. M. Mouly, Palaiseau 1992, ISBN 2-9507190-0-7
- Martin Sauter: Basic course in mobile communication systems. Vieweg, 2008, ISBN 978-3-8348-0397-9
- Jochen Schiller: Mobile communication. Pearson, Munich 2003, ISBN 3-8273-7060-4
- Peter Vary, Rainer Martin: Digital Speech Transmission - Enhancement, Coding and Error Concealment , Wiley 2006, ISBN 0-471-56018-9
- Bernhard Walke: Cellular networks and their protocols 1 , Stuttgart 2001, ISBN 3-519-26430-7
- Gerrit Boysen: Mobile communications - data transmission in industry , Rihn, Blomberg 2012, ISBN 978-3-00-037386-2
- Alex Glanz, Oliver Jung: Machine-to-Machine-Kommunikation , Campus, Frankfurt am Main / New York, NY 2010, ISBN 978-3-593-39224-0
Web links
- ITK-Steffens GSM-Sites (frequencies, bandwidths, details on the GSM extensions)
- Nobbis GSM pages (channel lists, monitor software, documentaries, images, electronic circuits, etc.)
- all GSM networks worldwide, network cards, partners
- Global mobile Suppliers Association with up-to-date counter for all GSM customers (English)
- GSM spectrum in Europe (June 2010, English)
- EMVU information regarding GSM
- CRE056 GSM Hacking Podcast with a focus on GSM security
- Security Research Labs: GSM Security Map
- Map showing the use of the different GSM frequency bands on earth
Individual evidence
- ↑ Tony Smith: 15 years ago: the first mass-produced GSM phone. In: theregister.co.uk. November 9, 2007, accessed July 5, 2016 .
- ↑ Through the country with the phone case. In: Focus Online . March 26, 2009, accessed July 5, 2016 .
- ^ A b H.-Peter Neitzke, Jürgen van Capelle, Katharina Depner, Kerstin Edler, Thomas Hanisch: Risk of electrosmog? Effects of electromagnetic fields on health and the environment , Birkhäuser Verlag (1994), ISBN 3-7643-5014-8 , p. 406
- ^ Mobile phone ( memento from July 14, 2014 in the Internet Archive ). Federal Office for Radiation Protection , accessed: June 11, 2014.
- ^ H.-Peter Neitzke, Jürgen van Capelle, Katharina Depner, Kerstin Edler, Thomas Hanisch: Risk of electrosmog? Effects of electromagnetic fields on health and the environment , Birkhäuser Verlag (1994), ISBN 3-7643-5014-8 , p. 405
- ↑ UMTS ( memento of July 14, 2014 in the Internet Archive ). Federal Office for Radiation Protection, accessed on June 11, 2014.
- ↑ Prof. Dr. Christian Lüders, Dipl.-Ing. (FH) Markus Quente: Capacity increase in current and future mobile radio systems, optimization by means of computer simulations , in Forschungsforum Paderborn 4-2001, (going to press December 2000), ISSN (print) 1435-3709, S: 80-85
- ↑ 3GPP TS 23.002: Network architecture; Cape. 4.3: The Mobile Station (MS). ( ZIP / DOC; 2.8 MB ).
- ↑ ETSI TS 100522 V7.1.0: Digital cellular telecommunications system (Phase 2+); Network architecture. ( ZIP / DOC; 135 kB ).
- ↑ 3GPP TS 24.008: Mobile radio interface Layer 3 specification; Core network protocols; Cape. 10.5.1.12.2 CS domain specific system information. (ZIP / DOC; 3.4 MB) September 28, 2009, accessed November 30, 2009 (English).
- ↑ a b GSM TS 03.20: Security-related network functions, Release 9.0.0. (ZIP / DOC; 476KB) January 16, 2001, accessed November 25, 2009 .
- ↑ heise Security: GSM hacking made easy
- ↑ Heise Security of December 28, 2010: 27C3: Eavesdropping on GSM cell phones further facilitated
- ↑ home.arcor-online.de: GSM technology ( memento from September 28, 2007 in the Internet Archive ) , accessed on May 6, 2011
- ↑ Telekom's mobile network largely equipped for HD telephony. on: teltarif.de May 5, 2011, accessed May 5, 2011
- ↑ Hannes Federrath: Security of Mobile Systems. Protection in GSM networks, mobility management and multilateral security 1st edition. Vieweg + Teubner, 1998, ISBN 978-3-528-05695-7
- ↑ IMSI-Catcher for 1500 Euro self-made. In: Heise online . August 1, 2010, archived from the original on August 2, 2010 ; Retrieved August 2, 2010 .
- ↑ Elad Barkan, Eli Biham, Nathan Keller: Instant Ciphertext-Only Cryptanalysis of GSM Encrypted Communication. (PDF; 240 kB) Journal of Cryptology, Volume 21 Issue 3, March 2008. Pages 392-429. January 10, 2003, accessed February 5, 2014 .
- ↑ Elad Barkan, Eli Biham, Nathan Keller: Instant Ciphertext-Only Cryptanalysis of GSM Encrypted Communication. (PDF; 351 kB) July 2006, accessed on February 5, 2014 (English).
- ^ A b Nico Golde, Kévin Redon, Jean-Pierre Seifert: Let Me Answer That for You. (PDF; 2.988 kB) Exploiting Broadcast Information in Cellular Networks. In: 22nd Usenix Security Symposium. August 14, 2013, accessed February 7, 2014 .
- ↑ a b Karsten Nohl, Luca Melette: GPRS Intercept. (PDF; 944 kB) Wardriving phone networks. August 10, 2011, accessed February 7, 2014 .
- ↑ Chris Paget, Karsten Nohl: GSM. (PDF; 664 kB) SRSLY? December 27, 2009, accessed February 7, 2014 .
- ↑ FAZ.NET: Chancellor bugged. It was Merkel's party cell phone. October 24, 2013, accessed August 7, 2014 .
- ↑ 3GPP TS 45.005: Radio Access Network; Radio transmission and reception (release 9); Cape. 2: Frequency bands and channel arrangement. (ZIP / DOC; 938 kB) October 1, 2009, accessed on November 25, 2009 (English).
- ↑ Practical mechanism to improve the compatibility between GSM-R and public mobile networks and guidance on practical coordination. (PDF; 1.1 MB) (No longer available online.) Formerly in the original ; accessed on January 24, 2010 (English). ( Page no longer available , search in web archives ) Info: The link was automatically marked as defective. Please check the link according to the instructions and then remove this notice.
- ↑ Final result of the frequency auction 2010 ( Memento of February 3, 2012 in the Internet Archive )
- ↑ GSM channels in Germany
- ↑ Federal Network Agency confirms auction for mobile radio frequencies. Retrieved June 26, 2013 .
- ↑ Federal Network Agency - Mobile Broadband - Project 2016. Accessed on November 6, 2015 .
- ↑ GSM channels ( Memento from September 14, 2011 in the Internet Archive )
- ↑ Telefónica improves LTE: 1800 MHz back on air. Telariff, September 22, 2016, accessed January 2, 2017 .
- ↑ RTR - overview of frequency ranges. Retrieved November 6, 2015 .
- ↑ https://www.swisscom.ch/de/about/medien/press-releases/2015/10/20151008-MM-Swisscom-ruestet-ihr-Mobilfunknetz-fuer-die-Zukunft.html Swisscom is equipping its mobile network for the future
- ↑ https://info.pcwebshop.ch/content/hinweise/MM_20170619_MM_2G_Shutdown__DE.pdf Sunrise press release June 19, 2017
- ↑ 5G: Effects, Significance, Facts - 33 answers on the 5G network. In: handelszeitung.ch . May 24, 2019, accessed May 27, 2019 .
- ↑ http://www.inside-it.ch/articles/47196 Inside-IT - Salt will also switch off 2G in 2020
- ↑ https://www.blick.ch/news/schweiz/der-langsame-tod-von-2g-wie-lange-funktioniert-mein-altes-handy-noch-id4368737.html Blick - The slow death of 2G
- ↑ GSM future in Germany, Austria and Switzerland is open. Retrieved February 26, 2017 .
- ↑ GSM twilight: networks in Australia and the USA at the end. Retrieved February 26, 2017 .