Stuxnet
Stuxnet is a computer worm that was discovered in June 2010 and first described under the name RootkitTmphider . The malicious program was specially developed to attack a monitoring and control system ( SCADA system ) from Siemens - the Simatic S7 . Thereby intervention was made in the control of frequency converters from the manufacturers Vacon from Finland and Fararo Paya in Tehran . Frequency converters are used, for example, to control the speed of motors .
Such controls are widely used, for example in industrial plants such as waterworks , air conditioning or pipelines .
Since Iran owned the largest proportion of infected computers by the end of September 2010 and there were extraordinary disruptions in the Iranian nuclear program , it was obvious that Stuxnet was mainly created to disrupt the control technology of the uranium enrichment plant in Natanz or the Buschehr nuclear power plant .
The highly skilled programmer group and client are unknown. However, the US Department of Justice announced in June 2013 that it was investigating the former second-highest officer in the US and later Stuxnet project manager, General James E. Cartwright . The agency suspects that Cartwright disclosed details about Stuxnet to the New York Times in 2010 , which allegedly led to the exposure of the $ 50 million sabotage program.
Properties and special features
Due to its complexity and the aim of sabotaging control systems of industrial plants, Stuxnet is currently unique. The publicly available findings are based on the statements of IT professionals who analyzed executable files of the malware. The judgments are partly based on interpretations, since the source text of the author is not published.
Due to the complexity of Stuxnet, an extraordinarily high development effort is assumed for malware. With an existing test environment for hardware and software, the time required is estimated at at least six months, the personnel requirement at at least five to ten main developers and additional staff for quality assurance and management. In addition to the specialist knowledge for developing the software, knowledge of unknown security gaps and access to secret signatures of two companies had to be available. The companies with the earliest signs of Stuxnet infection were suppliers. Therefore, the malicious program was introduced indirectly via the partner network.
The uniqueness of Stuxnet at the time of its discovery is particularly evident in the way in which it is distributed
- Exploitation of several previously unknown security gaps in Microsoft operating systems from Windows 2000 to Windows 7 or Windows Server 2008 R2 ,
- Installation of a rootkit in these operating systems with the help of stolen digital signatures from the Taiwanese hardware manufacturers Realtek and JMicron Technology ,
- precise knowledge of the WinCC process visualization system for monitoring and controlling technical processes with Simatic S7 (ICS: Industrial Control System) and
- Installation of another rootkits in the control system ( PLC , engl PLC. Programmable Logic Controller) of such a PCS-7 system .
Route of infection
The Stuxnet worm was put into circulation by November 15, 2007 at the latest, and the associated command and control servers were registered on November 3, 2005. Stuxnet was identified for the first time in June 2010 by Sergej Ulasen from the Belarusian company VirusBlokAda following a tip from an Iranian customer. System crashes and other malfunctions occurred at a system there. Since then, the functionality of the malware has been discussed by manufacturers of security software . At the Virus Bulletin 2010 Conference , Symantec summarized the current state of knowledge in the W32.Stuxnet dossier , which will be updated as new findings become available. Accordingly, Stuxnet attacks Simatic S7 systems whose configuration has certain properties.
In general, Simatic systems are configured, commissioned and maintained with a special notebook , the "SIMATIC Field PG". In addition to the operating system, software for programming with STEP 7 and for process visualization with WinCC is preinstalled on such a programming device (PG) . Moreover, the device with Ethernet - USB and PROFIBUS - Interface fitted.
The project planning and development of the HMI software ( Human Machine Interface ) takes place within an internal network ( LAN ), the Internet access of which is protected by a firewall . There is at least one STEP 7 project folder on a Field PG . The coupling with a PLC is established on the software side by the software library of the WinCC-DLL ( Dynamic Link Library ). The field PG is connected to the actual control system for commissioning, diagnosis and maintenance. As a rule, this is rarely connected to a LAN or even directly to the Internet.
A possible attack scenario arises based on the technical properties of Stuxnet: After the initial infection in a company, Stuxnet tries to spread within the LAN in order to locate field PGs. All STEP7 project folders and the WinCC library are infected on these. As soon as an affected PG is connected to a suitable control system, Stuxnet tries to change its programming. This is done hidden from the operators: Stuxnet is also a PLC rootkit. The malware is unusually large for a computer worm. It carries all the code it needs to update itself with a peer-to-peer mechanism without the need for a permanent internet connection. In addition, there are functions to be able to give feedback to a command and control server , like in a botnet .
Operating system level
In order to achieve its goal, Stuxnet has to get to computers that are (probably) connected to the targeted system control. For this purpose, four Windows security gaps ( zero-day exploits ) that had not been published during the operation were misused. This affects the 32-bit operating systems Windows 2000 , Windows XP , Windows Server 2003 , Windows Vista , Windows Server 2008 , Windows 7 . Stuxnet tries to install itself on one of the systems mentioned as soon as a USB storage medium is connected. For this, the fault-tolerant is parsing the autorun.infexploited by Windows. This file contains the actual malicious code as well as valid autorun information at the end , according to which the file is an executable EXE file. Even if the autostart option has been switched off, an open function is available in the context menu that allows the malicious code to be executed manually.
At the beginning of the infection, Stuxnet first checks whether the computer is already infected and, if so, whether its saved configuration data is up to date. Then he checks for a suitable 32-bit system. Depending on the version of the operating system, he gives himself extended rights through two different zero-day exploits using privilege escalation . Up to version Windows XP SP2 , Stuxnet uses an error in the kernel mode driver for this purpose , with newer versions it uses a hole in the task scheduler . Stuxnet then tries to inject its malicious code into installed anti-virus and Windows system services . The actual installation leads Stuxnet then in a separate, from the compromised system as trustworthy classified process from. In addition to other files, the worm also uses the signed certificates to install two driver files and in the system that are intended to ensure that Stuxnet continues to spread even after a restart .
win32k.sys mrxcls.sysmrxnet.sys
After installing the Windows rootkit, Stuxnet has several options for spreading itself in a LAN in which only limited or no internet access is possible: RPC server and client programs are installed that enable the peer Allow to-peer communication between several infected computers. The various Stuxnet instances are thus able to update themselves to an existing newer version . Stuxnet also tries to install on other computers via the directory shares of all users of a computer and the domain .
The computer worm uses a security flaw in the management of the print spooler ("Print Spooler zero-day vulnerability") to write files to the %System%directory. In the meantime, it has been found that this vulnerability was described by the magazine Hakin9 in April 2009, but was exploited for the first time by Stuxnet in the wild . This loophole is only exploited if the system date is before June 1, 2011.
A buffer overflow in Windows Server Service (WSS) was already exploited by the Conficker alias Downadup worm . Stuxnet also uses this error to install itself on other computers via SMB . However, certain time frame conditions must be met for this:
- The current date is before January 1, 2030.
- The virus definition files were last updated before January 1, 2009.
- The time stamps from
kernel32.dllandnetapi32.dllbe later than 28 October 2008 ( Windows Patch Day ).
A version of Stuxnet that has been proven since March 2010 uses a vulnerability in the handling of LNK files in order to be able to spread the worm via newly connected USB drives without having to rely on a network connection. It is sufficient to display the directory content of the drive. Before an installation, Stuxnet checks whether three computers have already been infected by the drive. In this case, the files will be deleted from the drive. In addition, there will be no further distribution after June 24, 2012. By interfering with kernel32.dlland netapi32.dllthese processes remain hidden from the user.
WinCC software

The next important step for Stuxnet is to get stuck in STEP7 project files (S7P files). On the one hand, it uses the server that provides the WinCC database software. With the help of the password programmed into the software, Stuxnet uses SQL commands to write a copy of itself into the database. As soon as the local computer is infected, the entry is removed again, but at the same time a CAB file is written which can generate a new Stuxnet DLL . This modified DLL is then loaded, decrypted and installed through searches when loading the system libraries. This results in a new infection, which also compensates for a previous deletion of the Stuxnet files. On the other hand, he installs two hooks in the Simatic Manager for PCS 7 . Every project is infected that has been used or changed within approximately the last 3.5 years and that contains a folder wincprojwith a valid MCP file (this is typically generated by WinCC itself). Projects that are named according to the scheme \Step7\Examples\*are excluded from infection .
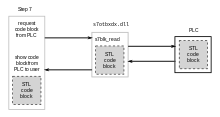
The file s7otbxdx.dllis the central library with which a PLC is linked to a Step7 application or a field PG. The original file is renamed by Stuxnet and supplemented by its own so that read and write access to the PLC can be monitored. In particular, this procedure enables you to include your own malicious code as an instruction list (STL) in the PLC and to protect this code from changes. Ultimately, the Stuxnet DLL, as a PLC rootkit, controls which programs are executed with which parameters in the connected PLC.
s7otbxsx.dlls7otbxdx.dll
Intervention in the programmable logic controller
The programs for a Simatic-S7 controller are divided into different modules with specific tasks:
- Organization blocks (OB) are processed cyclically by the PLC CPU in order to execute programs. OB1 as the central entry point for every program and OB35 as the standard watchdog timer are particularly important .
- System data blocks (SDB) store the specific structure of a specific system control. The configuration, e.g. number and type, of the connected devices is stored here.
- The data structures of the respective programs are stored in the data blocks (DB) .
- Function blocks (FB) contain the actual program code.
Before an infection, Stuxnet checks the PLC for various properties and behaves accordingly differently. Three different infection routines A, B and C were identified. Variants A and B are designed for the S7-300 with CPU type 315–2 and certain values defined in the SDBs. These two variants have since been examined more closely. Little was known about the much more complex variant C for the S7-400 with CPU type 417 until November 2010, because the program code is apparently deactivated or only "partially finished".
With the help of a Dutch Profibus expert, the functionality of variants A and B could be explained in more detail. An infection only occurs if the program block FB1869 is defined and at least one Profibus communication module CP-342-5 is entered in the SDB. Up to six of these modules each control 31 frequency converters that regulate the speed of rotation of electric motors. By implementing a finite machine with six states, Stuxnet changes the frequency to be set by the converters at irregular intervals of 13 days to three months. Using the identification number stored in the SDB, the Stuxnet variant A frequency converters were assigned to the company Vacon from Finland , and variant B to the manufacturer Fararo Paya in Tehran .
Updates and data retrieval
With every installation, Stuxnet collects information about the infected computer and saves it in a disguised configuration file. Among other things, the following is saved:
- the time of infection,
- the version numbers of the operating system and service pack ,
- the IP addresses of the network interfaces ,
- the names of the computer and the Windows workgroup or domain ,
- and the names of the infected Step7 projects.
With a get request via port 80 to www.windowsupdate.com and www.msn.com, Stuxnet checks whether an Internet connection is possible at all or whether it is prevented by a firewall . If successful, the collected data will be sent to the addresses www.mypremierfutbol.com and www.todaysfutbol.com by Get index.php?data=[DATA]. The servers for these domains were based in Denmark and Malaysia. It is possible for Stuxnet to update itself using these mechanisms in a similar way to a botnet , but this has not yet been observed.
distribution
The spread of Stuxnet on PCs is significantly greater than in the system controls . In the first case, the availability of the correct operating system is sufficient; in the other case, the function block FB1869 and the control of the frequency converter must be available. Stuxnet was thus detectable on a large number of PCs, while with other control systems the disturbances were probably unintentional. Since then, the worm has been analyzed by various anti-virus specialists. Unless otherwise stated, the following information from the chapter are timeline of W32.Stuxnet file from Symantec.
| date | event |
|---|---|
| Nov 20, 2008 | The Zlob Trojan is the first to exploit the LNK vulnerability (MS10-046), which will later be used by Stuxnet. |
| April 2009 | Hakin9 magazine publishes details on the MS10-061 print spooler exploit. |
| June 2009 | The first observed version of Stuxnet uses neither the LNK vulnerability MS10-046 nor signed driver certificates . |
| Jan 25, 2010 | The Stuxnet driver is signed with a certificate from Realtek . |
| April 2010 | A variant of Stuxnet uses remote code execution through the Windows shell for the first time (MS10-046). |
| June 17, 2010 | Virusblokada reports from Stuxnet as RootkitTmphider , which exploits the processing of shortcuts / LNK files for distribution. This LNK exploit is later named MS10-046. |
| July 13, 2010 | Symantec inserts a detection of the Trojan under the name W32.Temphid . |
| July 16, 2010 | Microsoft publishes the Security Advisory "Vulnerability in Windows Shell Could Allow Remote Code Execution (2286198)".
Verisign is revoking the Realtek certificate. |
| July 17, 2010 | ESET will find a Stuxnet version with a driver certificate from JMicron. |
| July 19, 2010 | Siemens reports on investigations into the infection of its SCADA systems.
Symantec renames the detection to W32.Stuxnet . |
| from July 20, 2010 | Symantec logs the data traffic with the command and control domains. |
| July 22, 2010 | VeriSign revokes the JMicron certificate . |
| Aug 2, 2010 | Microsoft released patch MS10-046 against the shortcut exploit. |
| Aug 6, 2010 | Symantec describes the function of Stuxnet as a PLC rootkit. |
| 22 Aug 2010 | Symantec can no longer discover newly infected IP addresses from Iran. |
| Sep 14 2010 | Microsoft has released print spooler patch MS10-061.
According to Siemens, 14 plants worldwide are to be affected. However, damage could not have been determined. |
| 26 Sep 2010 | Iran confirms attacks by Stuxnet. 30,000 computers are said to have been infected, but no "serious damage" occurred. However, this statement was revoked shortly afterwards by the Ministry of Foreign Affairs . In contrast, cyber propaganda is accused of “the West” . |
| Sep 30 2010 | The W32.Stuxnet dossier will be presented at the Virus Bulletin Conference 2010 .
The Xinhua news agency reports six million infected computers and almost a thousand affected system controls in China . |
| Oct 2, 2010 | To date, 15 infected systems have been reported to Siemens. Five of them are located in Germany, the rest in Western Europe, the USA and Asia. No damage should have occurred to any of the systems and the virus was successfully removed. |
| Oct 12, 2010 | With patch MS10-073, Microsoft closes a loophole for privilege escalation when loading keyboard layouts in the kernel. |
| Dec 14, 2010 | With patch MS10-092, Microsoft closes a gap in privilege escalation through the use of the task scheduler. |
| 11th Mar 2011 | So far, 24 Siemens customers have reported an infection. There was no impact on the facilities in any case. |
Assumptions about the originator and goals
Experts and engineers
IT security specialists assume that Stuxnet was specifically programmed to sabotage Iranian nuclear facilities. The work involved in the worm was enormous and expensive, and it only causes damage in certain systems, while others are apparently only infected without damage. The main distributor would be the Russian nuclear power export.
According to Wieland Simon ( Siemens ), experts and engineers from very different areas must have been involved in the development of the worm - in addition to Windows programmers, experts in automation technology and large industrial systems. Only such a team would be able to program a malware that successively overcomes several technically very different hurdles.
Because of the great amount of programming involved, Evgeni Kasperski , Liam O Murchu ( Symantec ) and other experts assume that the worm does not come from private individuals, but presumably from a government organization. The high development costs for the worm, which are estimated at a 7-digit dollar amount, speak for it.
To the client Israel
Several teams of experts found text modules in the worm code that suggest that the attackers called their project "Myrtus". The German IT security specialist Langner was the first to point out the possible allusion to the original Hebrew name of the Bible character Esther . Carol Newsom, Professor of the Old Testament at Emory University , confirmed the linguistic connection between the Hebrew words for "Myrtus" and "Esther" (Hebrew Hadassah ). The book of Esther in the Old Testament tells the story of a planned genocide by the Persians against the Jews, which the latter were able to prevent at Esther's initiative by destroying the enemy for their part.
In the media this speculation was taken as an indication of a possible authorship of Israel . According to the Süddeutsche Zeitung , however, most experts consider this thesis to be a conspiracy theory . It could also be a misleading trail. Shai Blitzblau, technical director and head of Maglan, an Israeli military IT security company, is convinced that Israel has nothing to do with Stuxnet. He suspects industrial espionage against Siemens or some kind of "academic experiment".
Yossi Melman , a journalist for the Israeli daily Haaretz , believed Israel was the likely originator in 2010. He stated that the contract of the director of the Israeli foreign intelligence service Mossad , Meir Dagan, was extended in 2009 because he was involved in important projects. In addition, Israel surprisingly postponed the estimated time by which Iran should have an atomic bomb to 2014.
According to a September 30, 2010 article in the New York Times , a former member of the United States Intelligence Community alleged that Israeli intelligence service Unit 8200 , comparable to the NSA , carried out the attack using Stuxnet. According to a later article dated January 15, 2011, the United States Department of Homeland Security and the Idaho National Laboratory examined the affected Siemens PCS-7 control system for vulnerabilities. The worm, which was developed on the basis of these findings, is then said to have been tested in the Israeli Negev nuclear research center ; there were gas centrifuge built Pakistani origin, which are also used in Iran. According to the New York Times report of January 15, 2011, there are “ Dimona ” centrifuges in Israel's nuclear weapons center , which are identical to the Iranian ones and could therefore have been used as a test for the worm.
The Israeli daily Haaretz reported on February 14, 2011 of a video in which the then Israeli chief of staff of the IDF Gabi Ashkenazi boasted that he was responsible for the successful Stuxnet attack in addition to the Israeli attacks on a Syrian nuclear reactor.
In July 2013, the former secret service employee and whistleblower Edward Snowden confirmed the suspicion that Stuxnet was a development of the NSA in cooperation with Israel.
To the client United States
The New York Times published an advance excerpt from Confront and Conceal: Obama's Secret Wars and Surprising Use of American Power by David E. Sanger on June 1, 2012 . He relies on interviews with those involved and concludes from this that a cyberattack with Stuxnet was started in the days of US President George W. Bush . Barack Obama had accelerated the secret operation code-named "Operation Olympic Games" (Olympic Games), and American and Israeli computer experts only managed to deal with the complex worm during his term in office. Obama oversaw the program and personally authorized every further step, writes Sanger.
US General James E. Cartwright , who was the second highest officer in the US armed forces from 2007 to 2011, was probably the initiator and head of the project . The US Justice Department announced in June 2013 announced that it had started investigations against the now retired Cartwright, as the authority suspected that he was as a project itself, the 2010 Information about the existence Stuxnets the year New York Times have passed which eventually led to the exposure of the program.
A joint effort by several states
The Iranian news agency Press TV referred in an article of January 16, 2011 to this same article in the New York Times of January 15, 2011. It is said that a US expert stated that Stuxnet is a product made by American, Israeli and British German cooperation. This position is also represented in an article in the Israeli daily Haaretz , in which there is talk of Siemens' active role in the programming of Stuxnet. Iranian officials are quoted as saying that Stuxnet did not pose a major threat to Iran because the virus was detected early and rendered harmless.
aims
An article in the time from November 26, 2010 suspected Sandro Gaycken that due to the high prevalence of the worm (including Germany and China) and the high cost of distribution (principal route is the targeted introduction of a USB disk) The worm's goals go beyond damaging Iranian facilities. Rather, he assumes that Stuxnet could be intended as “a test for future acts of sabotage in industrial plants”, including in “infrastructures such as electricity, water or gas”. One of the reasons he gives for this assumption is that the worm's widespread distribution and its ability to contact the attacker have dramatically increased the worm's probability of being detected. In the case of a targeted use to disrupt the Iranian uranium enrichment plant, however, it would have been more advantageous to remain undetected for a long time in order to be able to maintain the disruption as long as possible.
According to media reports, the Iranian uranium enrichment facility in Natanz may have been the target of the attack. According to secret documents that were brought to the public via the Internet platform WikiLeaks , there was a nuclear incident in Natanz in 2009 that reduced the plant's production capacity by 15 percent. It is assumed that the centrifuges of the plant are controlled by WinCC systems.
In late November 2010, Iranian President Mahmoud Ahmadinejad admitted that the worm had caused problems with the uranium centrifuges. Stuxnet had manipulated the speed of the centrifuges, which must be very precisely at 1064 revolutions per second. This damaged them. At the same time, Stuxnet disguised this. According to the Institute for Science and International Security (ISIS), this and the exact knowledge of the system speak for the authorship of Western intelligence services . The Stuxnet attack on Iranian nuclear and industrial plants is said to have infected around 16,000 computers, according to a high-ranking Iranian secret service employee.
Successor Duqu
In October 2011 the Laboratory of Cryptography and System Security (CrySyS) at the Budapest University of Technology and Economics in Hungary found a new piece of malware. The scientists wrote a 60-page report about it and named her Duqu after the prefix "~ DQ" which she prepended to the names of the files she created. Symantec published its report along with the CrySyS report. According to Symantec, Duqu was either developed by the same authors or the authors had access to the source code of Stuxnet. Above all, Duqu has espionage properties. Symantec suspects that this is to be used to collect information in order to prepare for future attacks.
Trivia
The Oscar -prämierte director Alex Gibney has with his documentary Zero Days filmed the history of Stuxnet and their dissemination and use.
literature
- David E. Sanger : Confront and Conceal. Obama's Secret Wars and Surprising Use of American Power . Random House, 2013, ISBN 0-307-71803-4
- Kim Zetter: Countdown to Zero Day. Stuxnet and the Launch of the World's First Digital Weapon . Crown, 2014, ISBN 0-7704-3617-X
- Lars Reppesgaard: Assault on the assembly line . In: Die Zeit , No. 34/2010
- Israel Tests on Worm Called Crucial in Iran Nuclear Delay . In: The New York Times , January 15, 2011
Web links
- Matthias Kremp: Port in the Persian Gulf: Iran confirms cyber attack on its oil industry. Spiegel Online , April 23, 2012, accessed on April 23, 2012 ( see Spyware, viruses, & security forum: New Deadly Virus / Worm discovered last night ).
- Matthias Kremp: Spectacular virus analysis: Stuxnet should disrupt Iran's uranium enrichment. Spiegel Online , November 16, 2010, accessed November 17, 2010 .
- Nicolas Falliere, Liam O Murchu, Eric Chien: W32.Stuxnet Dossier. (PDF; 4.1 MB) Version 1.4. Symantec , February 11, 2011, accessed July 4, 2011 .
- Ralph Langner: To Kill a Centrifuge. (PDF; 3.4 MB) A Technical Analysis of What Stuxnet's Creators Tried to Achieve. The Langner Group , November 2013, accessed January 20, 2014 .
- Frank Rieger: The digital first strike took place. FAZ.NET , September 22, 2010, accessed on November 10, 2010 .
- Frank Rieger: stuxnet: targeting the iranian enrichment centrifuges in Natanz? September 22, 2010, accessed December 28, 2010 .
- Topic page Stuxnet heise online
- Attack on Iran's nuclear program: Stuxnet could have destroyed a thousand uranium centrifuges . Spiegel Online , December 26, 2010
- Stuxnet: Israel is said to have built an Iranian nuclear facility . Spiegel Online , January 16, 2011
Remarks
Technical descriptions
The W32.Stuxnet dossier by Nicolas Falliere, Liam O Murchu and Eric Chien has so far been published at Symantec in the following versions:
- Version 1.0 on September 30, 2010
- Version 1.1 on October 12, 2010
- Version 1.2 on November 3, 2010
- Version 1.3 on November 12, 2010
- Version 1.4 on February 11, 2011
- ↑ a b c W32.Stuxnet Dossier, chapter Timeline
- ↑ a b c d e f W32.Stuxnet Dossier, Chapter Modifying PLCs
- ↑ a b W32.Stuxnet dossier, chapter Infection Statistics
- ↑ W32.Stuxnet Dossier, Chapter Executive Summary
- ↑ a b c W32.Stuxnet Dossier, Chapter Installation
- ↑ Costin Raiu: Stuxnet and stolen certificates. In: Securelist. Kaspersky Lab, July 20, 2010, accessed October 14, 2010 .
- ↑ W32.Stuxnet Dossier, Chapter Summary
- ↑ Industrial notebook SIMATIC Field PG. Siemens AG , accessed on November 9, 2010 .
-
↑ Photos from the Bushehr NPP:
- Mohammad Kheirkhah: Bushehr Nuclear Power Plant in Iran. UPI-Photo , February 25, 2009, accessed on November 14, 2010 (The photo illustrates how a Field-PG (the laptop in the foreground) is basically connected to a control system. A connection with the article Stuxnet is purely coincidental.): "Russian technicians work at Bushehr nuclear power plant in the Bushehr Port on the Persian Gulf, 1,000 kms south of Tehran, Iran on February 25, 2009. Iranian officials said the long-awaited project was expected to become operational last fall but its construction was plagued by several setbacks, including difficulties in procuring its remaining equipment and the necessary uranium fuel. "
- Mohammad Kheirkhah: Iran's Bushehr nuclear power plant in Bushehr Port. UPI-Photo , February 25, 2009, accessed on November 14, 2010 (This is the error message "WinCC Runtime License: Your software license has expired! Please obtain a valid license." A connection with the article Stuxnet is purely coincidental. ): "An error is seen on a computer screen of Bushehr nuclear power plant's map in the Bushehr Port on the Persian Gulf, 1,000 kms south of Tehran, Iran on February 25, 2009 ..."
- ↑ a b W32.Stuxnet Dossier, Chapter Attack Scenario
- ↑ W32.Stuxnet Dossier, Chapter Stuxnet Architecture
- ↑ Liam O. Murchu: Stuxnet Before the .lnk File Vulnerability. In: symantec.connect. Symantec Corporation, September 24, 2010, accessed November 10, 2010 .
- ↑ Windows Kernel-Mode Drivers Could Allow Elevation of Privilege. Microsoft Security Bulletin MS10-073, October 12, 2010, accessed November 18, 2010 .
-
↑
In Injection Technique, the dossier names Kaspersky KAV , McAfee , Avira AntiVir , Bitdefender , eTrust , F-Secure , two Symantec products , ESET , PC-Cillin from Trend Micro , as well as
lsass.exe,winlogon.exeandSvchost.exe. -
↑
In the W32.Stuxnet dossier is listed in Installation :
-
oem7a.pnfthe actual malicious program (main payload) -
%SystemDrive%\inf\mdmeric3.PNF(data file) -
%SystemDrive%\inf\mdmcpq3.PNF(configuration data) -
%SystemDrive%\inf\oem6C.PNF(log file)
-
- ↑ a b c d e W32, Stuxnet Dossier, Chapter Stuxnet Propagation Methods
-
↑ * CVE-2010-2729: Microsoft Windows Print Spooler Service Remote Code Execution Vulnerability. Symantec Connect, September 27, 2010; accessed November 19, 2010 .
- MS10-061: Vulnerability in Print Spooler Service Could Allow Remote Code Execution. Microsoft Security Bulletin, September 29, 2010; accessed November 19, 2010 .
-
↑ * CVE-2008-4250: Microsoft Windows Server Service RPC Handling Remote Code Execution Vulnerability. Symantec Connect, February 9, 2009, accessed November 19, 2010 .
- MS08-067: Vulnerability in Server Service Could Allow Remote Code Execution. Microsoft Security Bulletin, October 23, 2008, accessed November 19, 2010 .
-
↑ * CVE-2010-2568: Microsoft Windows Shortcut 'LNK / PIF' Files Automatic File Execution Vulnerability. Symantec Connect, August 11, 2010; accessed November 19, 2010 .
- Vulnerability in Windows Shell Could Allow Automatic File Execution. Multi-State Information Sharing and Analysis Center (MS-ISAC), July 17, 2010, accessed November 19, 2010 .
- MS10-046: Vulnerability in Windows Shell Could Allow Remote Code Execution (2286198). Microsoft Security Bulletin, August 2, 2010, accessed December 3, 2010 .
-
↑
The dossier lists in Windows Rootkit Functionality a . a. the following files:
-
%DriveLetter%\~WTR4132.tmp(Stuxnet's main DLL, approx. 500kB) -
%DriveLetter%\~WTR4141.tmp(Loader program for ~ WTR4132.tmp, approx. 25kB) %DriveLetter%\Copy of Shortcut to.lnk%DriveLetter%\Copy of Copy of Shortcut to.lnk%DriveLetter%\Copy of Copy of Copy of Shortcut to.lnk%DriveLetter%\Copy of Copy of Copy of Copy of Shortcut to.lnk
-
- ↑ Engineering system. Siemens AG, accessed on November 20, 2010 .
- ↑ S7-300 CPUs. (No longer available online.) Siemens AG, June 24, 2009, archived from the original on December 24, 2010 ; Retrieved December 1, 2010 . Info: The archive link was inserted automatically and has not yet been checked. Please check the original and archive link according to the instructions and then remove this notice.
- ↑ S7-400 CPUs. (No longer available online.) Siemens AG, archived from the original on October 18, 2010 ; Retrieved December 1, 2010 . Info: The archive link was inserted automatically and has not yet been checked. Please check the original and archive link according to the instructions and then remove this notice.
- ^ Stuxnet: A Breakthrough. Symantec Connect, November 12, 2010; accessed December 1, 2010 .
- ↑ cf. also Ident Numbers: What They Are, And How To Get One. Profibus & Profinet International , accessed December 1, 2010 .
- ↑ W32.Stuxnet Dossier, Chapter Command and Control
- ↑ W32.Stuxnet Dossier, Chapter Windows Rootkit Functionality
Individual evidence
- ↑ a b Attack on Iran's nuclear program - Stuxnet could have destroyed a thousand uranium centrifuges . Spiegel Online , December 26, 2010
- ↑ Iran Reports a Major Setback at a Nuclear Power Plant . nytimes.com, February 25, 2011
- ↑ a b Investigations by the US judiciary: four-star general is said to have betrayed Stuxnet program. spiegel.de, June 28, 2013, accessed June 28, 2013 .
- ↑ a b Andreas Wilkens: Stuxnet: Reports on further treason cases in the USA. heise.de, June 28, 2013, accessed on June 28, 2013 .
- ↑ Friedhelm Greis: Kaspersky identifies the first five Stuxnet victims. In: golem.de. Kaspersky Lab, November 11, 2014, accessed November 22, 2014 .
- ^ A b Paul Anton Krüger et al .: The worm and the balloon . In: Süddeutsche Zeitung . October 2, 2010.
- ^ Virus Bulletin in the English language Wikipedia
- ^ Vacon in the English language Wikipedia. Vacon is a leading supplier of variable speed AC drives. Vacon Plc, accessed December 1, 2010 .
- ↑ FararoPaya. Retrieved December 1, 2010 .
- ↑ Zlob trojan in the English language Wikipedia
- ^ Robert McMillan: Siemens: Stuxnet worm hit industrial systems. (No longer available online.) In: Computerworld. September 14, 2010, archived from the original on December 21, 2013 ; accessed on September 16, 2010 (English). Info: The archive link was inserted automatically and has not yet been checked. Please check the original and archive link according to the instructions and then remove this notice.
- ↑ Iran confirms cyber attack by Stuxnet. In: Heise online . December 9, 2010, accessed September 26, 2010 .
- ↑ Iran accuses the West of cyber propaganda. Spiegel Online, September 28, 2010, accessed December 9, 2010 .
- ↑ a b Stuxnet attacks in China. (No longer available online.) In: Kurier.at. October 1, 2010, archived from the original on October 4, 2010 ; Retrieved December 9, 2010 .
- ↑ a b Dangerous malware: Stuxnet computer virus hits German industry. In: sueddeutsche.de. October 2, 2010, accessed October 18, 2010 .
- ↑ SIMATIC WinCC / SIMATIC PCS 7: Information on malware / viruses / Trojans. Siemens AG , April 1, 2011, accessed on July 4, 2011 (Siemens Stuxnet Support, Entry ID: 43876783).
- ↑ Johannes Kuhn: Stuxnet sabotage virus - "Pandora's box is open". In: sueddeutsche.de. October 1, 2010, accessed October 14, 2010 .
- ↑ Andreas Hirstein: "Here was a team of experts at work" - Stuxnet, a dangerous computer worm. NZZ, September 26, 2010, accessed October 15, 2010 .
- ↑ The "Hack of the Century". "Stuxnet" virus paralyzes Iran. In: ORF.at. Österreichischer Rundfunk, September 26, 2010, accessed on September 30, 2010 .
- ^ Frank Rieger: Trojan "stuxnet" - the digital first strike has taken place. In: FAZ.NET . September 22, 2010, accessed September 30, 2010 .
- ↑ a b c Yvan Côté: Cyberguerre: les armes de demain. In: Télévision de Radio-Canada . February 21, 2012. Retrieved February 22, 2012 .
- ^ A b c Ethan Bronner, William J. Broad: In a Computer Worm, a Possible Biblical Clue. In: NYTimes. September 29, 2010, accessed October 2, 2010 .
- ^ John Markoff, Kevin O'Brien: A Silent Attack, but Not a Subtle One. In: New York Times online. September 30, 2010, accessed October 15, 2010 .
- ^ John Markoff, Kevin O'Brien: A Silent Attack, but Not a Subtle One. (No longer available online.) September 30, 2010, archived from the original on April 26, 2014 ; accessed on October 15, 2010 (English). Info: The archive link was inserted automatically and has not yet been checked. Please check the original and archive link according to the instructions and then remove this notice.
- ^ A b William J. Broad, John Markoff, David E. Sanger: Israel Tests on Worm Called Crucial in Iran Nuclear Delay. In: New York Times online. January 15, 2011, accessed October 4, 2015 .
- ↑ hairetz.co.il ( Memento of the original from February 17, 2011 in the Internet Archive ) Info: The archive link was inserted automatically and has not yet been checked. Please check the original and archive link according to the instructions and then remove this notice. Haaretz, January 14, 2011
- ^ Richard Silverstein: Ashkenazi Video Admits IDF Bombed Syrian Nuclear Reactor and Created Stuxnet . February 14, 2011
- ↑ Reuters / Thomas Peter: Snowden confirms NSA created Stuxnet with Israeli aid. July 9, 2013, accessed July 10, 2013 .
- ↑ David E. Sanger: Obama Order Sped Up Wave of Cyberattacks Against Iran. The New York Times, June 1, 2012, accessed June 19, 2012 .
- ^ Yossi Melman: Israel finally moving to define national policy on Iran. March 10, 2011, accessed March 5, 2012 .
- ↑ SF / HRF / MB: Stuxnet, US-Israeli bid against Iran. (No longer available online.) In: Press TV. January 16, 2011, archived from the original on February 12, 2015 ; accessed on January 16, 2011 . Info: The archive link was inserted automatically and has not yet been checked. Please check the original and archive link according to the instructions and then remove this notice.
- ↑ Sandro Gaycken: Who was it? And what for? In: Die Zeit , No. 48/2010
- ↑ a b Mark Clayton: Stuxnet worm mystery: What's the cyber weapon after? Yahoo News, February 25, 2009, accessed September 28, 2010 .
- ^ Serious nuclear accident may lay behind Iranian nuke chief's mystery resignation. (No longer available online.) Archived from the original on December 29, 2010 ; Retrieved October 3, 2010 . Info: The archive link was inserted automatically and has not yet been checked. Please check the original and archive link according to the instructions and then remove this notice.
- ↑ Iran Report , 03/2012 (PDF; 398 kB), accessed March 4, 2012
- ^ Laboratory of Cryptography and System Security (CrySyS) . Retrieved November 4, 2011.
- ↑ Duqu: A Stuxnet-like malware found in the wild, technical report (PDF; 1.5 MB) Laboratory of Cryptography of Systems Security (CrySyS). October 14, 2011. Retrieved May 31, 2012.
- ^ Statement on Duqu's initial analysis . Laboratory of Cryptography of Systems Security (CrySyS). October 21, 2011. Archived from the original on October 3, 2012. Info: The archive link was automatically inserted and has not yet been checked. Please check the original and archive link according to the instructions and then remove this notice. Retrieved October 25, 2011.
- ↑ W32.Duqu - The precursor to the next Stuxnet (PDF; 4.1 MB)
- ↑ Virus Duqu alerts IT security experts. In: Zeit Online . October 19, 2011, accessed October 19, 2011 .
- ↑ Zero Days - Stuxnet was just the beginning of a cyber war. In: 4You2Connect.com. Retrieved September 1, 2016 .